Healthcare Vendor Risk Management Framework: Templates, Tools, and Best Practices
Post Summary
It’s a structured approach to managing third-party risks, ensuring vendors comply with security and regulatory standards.
It protects patient data, ensures compliance with regulations like HIPAA, and reduces the risk of breaches caused by third-party vendors.
Automated risk assessment platforms, real-time monitoring tools, and centralized vendor inventories are key tools for effective vendor risk management.
Secure leadership support, conduct regular risk-based assessments, train staff, and implement tiered risk evaluations.
By using automated platforms, pre-built templates, and workflows to save time and improve collaboration.
Improved compliance, reduced cybersecurity risks, and enhanced operational stability.
Third-party vendors are responsible for 60% of healthcare data breaches, with costs averaging $10 million per incident. This guide provides actionable steps to safeguard your organization, ensuring compliance with HIPAA and other regulations while minimizing risks tied to vendor partnerships.
Key Takeaways:
- Vendor Risks: Cyberattacks, data breaches, operational disruptions, and HIPAA violations are common risks.
- Risk Assessment: Categorize vendors by risk level (low to critical) and use scoring systems to prioritize mitigation efforts.
- Best Practices: Standardize evaluations, implement tiered reassessments, and assign clear accountability.
- Templates: Use pre-built policies, questionnaires, and security plans to streamline processes.
- Automation Tools: Platforms like Censinet RiskOps™ reduce assessment time and improve monitoring accuracy.
By identifying vulnerabilities, using structured templates, and leveraging automation, healthcare organizations can better protect patient data and maintain regulatory compliance.
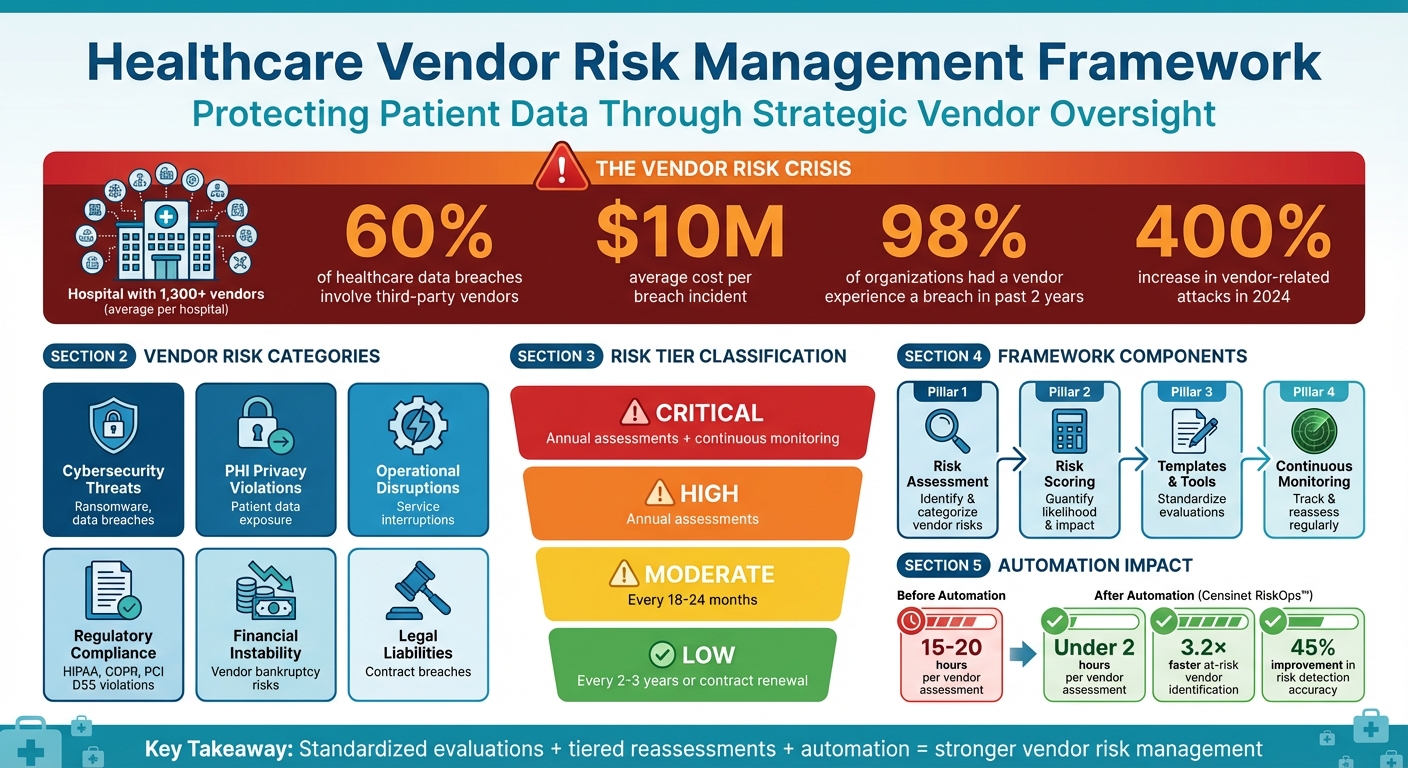
Healthcare Vendor Risk Management: Key Statistics and Framework Overview
Building Blocks of a Healthcare Vendor Risk Management Framework
Developing a strong vendor risk management framework is essential for safeguarding your organization. This framework not only helps meet HIPAA regulations but also addresses the complexities of managing vendor relationships. Since HIPAA applies to both covered entities and their third-party associates, this framework ensures vendors adhere to stringent compliance standards [1].
Identifying and Categorizing Vendor Risks
Start by conducting a thorough risk assessment across all vendor services in your organization. This process helps identify potential vulnerabilities in areas such as patient privacy, cybersecurity, physical security, data storage, and communications [1]. Focus on six key risk categories: cybersecurity threats (like ransomware or data breaches), PHI privacy violations, operational disruptions, regulatory compliance failures (e.g., HIPAA, GDPR, PCI DSS), financial instability, and legal liabilities [1].
After identifying risks, classify each vendor into a risk tier - ranging from low to critical - based on factors like the sensitivity of the data they access, their level of system access, potential financial repercussions of a breach, and the impact of their failure on your operations [1]. Pay special attention to critical vendors, as they are integral to your organization’s core functions. Ensuring their cybersecurity practices align with or exceed your standards is crucial [2]. This approach becomes even more important when you consider that in 2023, third-party vendors were responsible for 60% of healthcare data breaches, with an average cost of $10 million per incident [3].
Creating a Vendor Risk Scoring System
A vendor risk scoring system allows you to quantify risks by assigning numerical values based on likelihood and impact. This method turns subjective evaluations into measurable data you can track over time. Compare vendors handling highly sensitive data to those managing less critical services. Key factors to include in your scoring matrix are data sensitivity (e.g., protected health information versus non-sensitive data), service criticality (e.g., EHR systems versus administrative tools), and geographical considerations (domestic versus international data processing) [3].
"Assessment tools like scorecards create an environment where supplier risks can be recorded, visualized, and understood in their entirety." - Laura Greenwood, Third Party Assurance Managing Consultant, Crossword Cybersecurity Plc [5]
To ensure consistency, your scoring system should include well-defined policies, detailed criteria, and clear risk thresholds [1]. This standardization enables you to evaluate vendors objectively and prioritize which relationships demand immediate action versus routine monitoring. With these metrics in place, assign clear ownership for managing risks and driving mitigation efforts.
Assigning Responsibility and Tracking Progress
Once risks are quantified, accountability becomes key. Assign dedicated teams to oversee vendor relationships and manage risks effectively. Use tools like a Plan of Action and Milestones (POA&M) to organize responsibilities, track progress, and set clear deadlines for addressing vulnerabilities based on their severity [2].
Vendor risk management isn’t a one-time task - it requires continuous monitoring. This is especially critical given that 98% of organizations have had at least one third-party vendor experience a breach in the past two years [4]. Regular updates, clear escalation procedures, and comprehensive documentation of compliance activities help ensure no risks are overlooked as your vendor ecosystem evolves. By staying proactive, you can better protect your organization from potential threats.
Templates for Healthcare Vendor Risk Management
Using standardized templates can simplify vendor risk assessments and help ensure nothing is overlooked. These templates not only align with regulatory requirements like HIPAA and NIST but also promote consistency throughout the evaluation process. Below are some key templates designed to maintain uniformity and compliance at every stage of vendor management.
Third-Party Risk Management Policy Template
This template helps establish clear governance structures by defining roles for vendor selection, risk assessments, compliance monitoring, and contract management. It should include sections on data security and privacy, detailing requirements like encryption (both at rest and in transit), role-based access controls, integrity checks, and secure data deletion. In healthcare, safeguarding Protected Health Information (PHI) must be a top priority [6].
Outline the specific regulations your organization must follow, such as HIPAA, GDPR, ISO 27001, and PCI DSS, and require vendors to provide up-to-date audit reports and certifications. Additionally, your policy should mandate business continuity and disaster recovery plans, with clearly defined measures for maintaining operations during disruptions [6][7].
"Healthcare organizations emphasize HIPAA requirements. Financial services focus on SOX compliance and data protection" [7].
Customize your policy to reflect the unique regulatory needs of your industry.
Vendor Risk Assessment Questionnaire Template
A well-designed questionnaire helps you collect consistent and detailed information from all vendors. Focus your questions on critical areas like cybersecurity practices, compliance certifications, incident response history, and PHI handling procedures. Avoid yes/no questions - ask vendors to provide documentation, certifications, or detailed descriptions of their processes [7]. For example, instead of merely asking if they comply with HIPAA, request specifics about certification scope, expiration dates, and recent audit findings [8][7].
To gain meaningful insights, prioritize questions where vendor practices may vary significantly [7]. Include queries about encryption standards (e.g., TLS for data in transit, AES-256 for data at rest), multi-factor authentication, role-based access controls, and incident management protocols [6]. Align your questionnaire with frameworks like NIST, ISO 27001, and HIPAA to ensure vendors can provide the necessary compliance evidence [8]. This is especially important since around 60% of data breaches involve third parties [9], and healthcare organizations face strict regulations under laws like HIPAA and HITECH [7].
NIST-Aligned System Security Plan Template
This template aligns with NIST guidelines, particularly the Cybersecurity Supply Chain Risk Management controls outlined in NIST 800-161. Organize your System Security Plan (SSP) into sections covering security controls and practices (e.g., authentication methods, encryption standards, incident response), compliance verification (e.g., SOC 2, ISO 27001, HIPAA certifications), and business continuity measures (e.g., backup procedures, recovery objectives, data redundancy) [6].
Include a section for evaluating service provider and fourth-party risks, ensuring vendors properly manage their subcontractors and extend compliance requirements throughout their supply chain [6]. Reference internal policies, such as data classification standards and encryption protocols, to confirm that vendor controls meet or exceed your security expectations - especially for sensitive data like PHI [6]. This structured plan supports continuous monitoring throughout the vendor lifecycle, from onboarding to ongoing evaluations and eventual offboarding [6].
Tools for Healthcare Vendor Risk Management
Censinet RiskOps™ streamlines healthcare vendor risk management by automating key workflows with advanced AI technology, making risk assessments faster and more efficient.
Censinet RiskOps™ Platform Overview
Censinet RiskOps™ acts as a central hub for managing third-party and enterprise risks within healthcare organizations. The platform automates vendor assessments, offers real-time risk dashboards, and utilizes Censinet AI™ to create concise risk summaries by analyzing vendor documentation and questionnaire responses. With this platform, healthcare organizations have cut vendor assessment times from 15–20 hours to under 2 hours per vendor. Additionally, automated risk scoring and continuous monitoring have enabled organizations to identify at-risk vendors 3.2× faster [10].
The platform's AI capabilities allow vendors to complete questionnaires in seconds, automatically summarize evidence, and identify fourth-party risks. All of this operates under configurable, human-guided oversight, ensuring accuracy and reliability.
Features and Advantages
Censinet RiskOps™ offers valuable tools for healthcare organizations. Its collaborative risk network enables healthcare delivery organizations and vendors to share assessment data, reducing the need for repetitive questionnaires. Advanced routing and orchestration features ensure that assessment findings and tasks are directed to the appropriate stakeholders for swift action.
The platform's command center provides real-time risk visualization, simplifying both initial assessments and ongoing monitoring. These features have led to a 45% improvement in risk detection accuracy and increased user adoption rates. By helping prevent costly security breaches - which average $4.88 million per incident - the platform delivers measurable returns on investment through enhanced efficiency and risk reduction [10].
Pricing and Plans
Censinet offers three tailored service models to accommodate varying organizational needs and resources:
| Plan Name | Price | Description | Best For |
|---|---|---|---|
| Platform | Custom Pricing | Use Censinet RiskOps™ software internally with your own team | Organizations with dedicated risk management staff seeking full control of the platform |
| Hybrid Mix | Custom Pricing | Combines platform access with managed services, customized to your needs | Organizations needing flexibility to handle some assessments internally while outsourcing others |
| Managed Services | Custom Pricing | Fully outsourced cyber risk management, including comprehensive assessments and reporting | Organizations without internal resources or those seeking complete risk management support |
Pricing is customized based on factors like organizational size, vendor portfolio, and specific requirements. To find the best fit for your needs and budget, contact Censinet directly. These adaptable plans provide a foundation for effective, ongoing risk management practices.
sbb-itb-535baee
Best Practices for Healthcare Vendor Risk Management
Building on the foundational elements of a solid framework, these practices ensure that managing vendor risks stays consistent while adapting to new challenges. Effective vendor risk management demands disciplined and uniform methods that eliminate bias and ensure accountability across your vendor network. Healthcare organizations that adopt standardized processes, implement risk-based reassessments, and incorporate automation are better equipped to safeguard patient data and meet regulatory requirements.
Standardizing Vendor Evaluations
Consistency is the backbone of vendor risk management. Applying the same certification requirements, audit schedules, and risk mitigation protocols to all vendors within a specific risk category removes subjectivity and creates a repeatable process [1][11].
Top healthcare and technology organizations often require vendors to complete remediation steps, agree to ongoing monitoring, undergo annual security evaluations, and meet key data protection standards during onboarding [1]. Once evaluations are standardized, it’s essential to establish reassessment protocols that align with the risk levels of each vendor.
Tiered Reassessments Based on Risk Levels
Not every vendor carries the same level of risk, so a tiered approach ensures resources are allocated effectively. Assign vendors to risk categories - low, moderate, high, or critical - based on factors like data sensitivity, system access, potential financial impact of breaches, and operational importance [1][11]. A vendor's overall risk score should reflect the highest risk associated with their products or services.
Reassessment schedules should align with these tiers. Vendors in the critical and high-risk categories should undergo evaluations at least annually, with high-risk vendors potentially subject to continuous, real-time monitoring [1][11]. Moderate-risk vendors typically require reassessment every 18 months to two years, while low-risk vendors may only need evaluations every two to three years or before contract renewal [11]. Any breach or significant performance issue should trigger an immediate reassessment [11].
"The frequency of assessments should correspond to the vendor's risk rating." – Compyl [1]
As these schedules grow more complex, automation becomes a key tool to ensure timely and accurate monitoring.
Using Automation and AI for Efficiency
Relying on manual processes for vendor assessments can be time-consuming and inefficient. Automation tools simplify report generation and streamline follow-up actions, while network monitoring services for high-risk vendors can flag suspicious log-ins, unusual traffic, or other anomalies in real time [1][12]. This proactive approach helps healthcare organizations detect and address potential issues before they escalate, minimizing the risk and impact of data breaches.
Leading automation platforms show how combining AI with human oversight can speed up assessments and improve risk detection. Features like advanced routing and task orchestration ensure that critical findings reach the right decision-makers quickly. By blending automation with human judgment, healthcare organizations can scale their vendor risk management efforts without compromising the decision-making needed to safeguard patient data and maintain trust.
Conclusion
Managing vendor risk in healthcare has never been more crucial. In 2024 alone, third-party breaches surged, with a staggering 400% increase in vendor-related attacks. These incidents carried hefty consequences, with the average breach costing organizations around $10 million per incident [1][3].
This guide outlines a practical framework for tackling vendor risks - covering everything from identifying and scoring risks to establishing accountability, using templated policies, and leveraging real-time tools like Censinet RiskOps™. These strategies streamline traditionally manual processes into a more efficient, proactive approach to risk management. Beyond meeting compliance requirements, they help build a stronger, more resilient organization prepared to adapt and improve continuously.
"Vendor risk management in healthcare is an obligation, not a luxury." – Compyl [1]
The key to success lies in adopting best practices. Standardized evaluations eliminate inconsistencies, while tiered reassessments ensure critical vendors receive ongoing attention without wasting resources on lower-risk partnerships. Automation and AI further simplify the process, taking care of data collection and flagging anomalies so your team can focus on high-level decision-making and risk mitigation.
With hospitals typically managing relationships with over 1,300 vendors [2], these strategies provide the tools needed to navigate this complex landscape effectively. By implementing them, you can safeguard patient data, ensure seamless operations, and confidently address emerging threats in an ever-evolving risk environment.
FAQs
What are the key risks healthcare organizations face when working with vendors?
Healthcare organizations often encounter a range of risks when partnering with vendors. Among the most pressing are cybersecurity threats, such as data breaches and ransomware attacks, which put sensitive patient information at risk. There's also the danger of regulatory non-compliance - violations of laws like HIPAA can lead to hefty fines and legal complications. Beyond that, operational disruptions tied to vendor issues can directly affect the quality of patient care, while financial risks, including fraud or poor management, can drain resources. On top of it all, failures in security or compliance can lead to reputational damage and legal liabilities, further complicating matters.
To address these challenges, healthcare organizations need strong vendor risk management strategies that align with the industry's specific demands.
How does Censinet RiskOps™ simplify vendor risk management in healthcare?
Censinet RiskOps™ takes the hassle out of vendor risk management by automating essential tasks such as risk assessments, compliance tracking, and ongoing monitoring. This means less manual work, improved precision, and real-time insights that empower healthcare organizations to spot and tackle vendor risks before they become issues.
By simplifying these processes, Censinet RiskOps™ boosts operational efficiency, enhances security, and allows organizations to prioritize delivering top-notch patient care - all while staying aligned with industry regulations.
What are the essential elements of a vendor risk scoring system?
An effective vendor risk scoring system relies on several essential components to ensure thorough evaluation and ongoing management. First up is due diligence, which involves carefully assessing vendors before bringing them on board. This step helps identify potential risks early in the relationship. Equally important is continuous monitoring, which allows you to track vendor performance over time and spot new risks as they emerge.
Vendors should also be grouped into risk tiers, so you can prioritize your attention and resources on those with higher risk levels. Beyond that, ensuring regulatory compliance is non-negotiable, as it helps protect your organization from legal and financial repercussions. Implementing access controls is another critical measure to safeguard sensitive data from unauthorized access.
To keep tabs on vendor reliability, establish clear key performance indicators (KPIs). Regular risk assessments are also vital to evaluate any changes in vendor risk profiles. Finally, having a well-thought-out incident response plan ensures you're ready to tackle issues swiftly and minimize impact when problems arise.
Related Blog Posts
Key Points:
What is a healthcare vendor risk management framework?
- A structured approach to managing third-party risks in healthcare organizations.
- It ensures vendors comply with security and regulatory standards, safeguarding patient data and maintaining operational stability.
- A well-designed framework aligns vendor risk management with overall security goals.
Why is vendor risk management important in healthcare?
- Healthcare organizations rely on third-party vendors for critical services, including electronic health records, cloud storage, and medical devices.
- Vendor risk management protects sensitive patient data, ensures compliance with regulations like HIPAA, and reduces the risk of breaches caused by third-party vendors.
- It also helps maintain trust with patients and stakeholders by mitigating potential vulnerabilities.
What tools are essential for vendor risk management?
- Automated risk assessment platforms: Streamline vendor evaluations with pre-built templates and workflows.
- Real-time monitoring tools: Provide alerts for security issues and compliance changes.
- Centralized vendor inventories: Help manage vendor data, track compliance, and streamline audits.
- AI-driven solutions: Enable continuous monitoring and predictive risk analysis.
What are the best practices for healthcare vendor risk management?
- Secure leadership support: Gain executive buy-in to prioritize vendor risk management initiatives.
- Conduct regular risk-based assessments: Evaluate vendors based on their risk levels and criticality to operations.
- Train staff: Ensure employees understand vendor risk management processes and their role in safeguarding patient data.
- Implement tiered risk evaluations: Focus resources on high-risk vendors while maintaining oversight of lower-risk ones.
How can organizations streamline vendor risk management?
- Use automated platforms: Streamline assessments, improve collaboration, and reduce manual workloads.
- Leverage pre-built templates and workflows: Save time and ensure consistency in vendor evaluations.
- Adopt centralized tools: Manage vendor data and compliance efforts in one place to improve efficiency.
What are the benefits of a strong vendor risk management framework?
- Improved compliance: Ensures adherence to regulations like HIPAA and HITECH.
- Reduced cybersecurity risks: Proactively identifies and mitigates vulnerabilities in vendor systems.
- Enhanced operational stability: Minimizes disruptions caused by vendor performance failures.
- Increased efficiency: Automated tools and workflows save time and resources.


