HIPAA Compliance for Healthcare Vendors: Your Complete Third-Party Risk Checklist
Post Summary
Healthcare organizations rely on third-party vendors to handle sensitive patient data, but these partnerships come with risks. Non-compliance with HIPAA can result in severe penalties, operational disruptions, and reputational damage. Here's how to manage vendor risks effectively:
- Create a vendor inventory: Identify all vendors handling Protected Health Information (PHI) and classify them by risk level.
- Sign Business Associate Agreements (BAAs): Establish legally required contracts to define data handling responsibilities.
- Conduct risk assessments: Evaluate vendor safeguards for administrative, technical, and physical security measures.
- Monitor vendors continuously: Track security incidents, access logs, and updates to vendor practices.
- Document everything: Maintain organized records of risk assessments, BAAs, and compliance actions to prepare for audits.
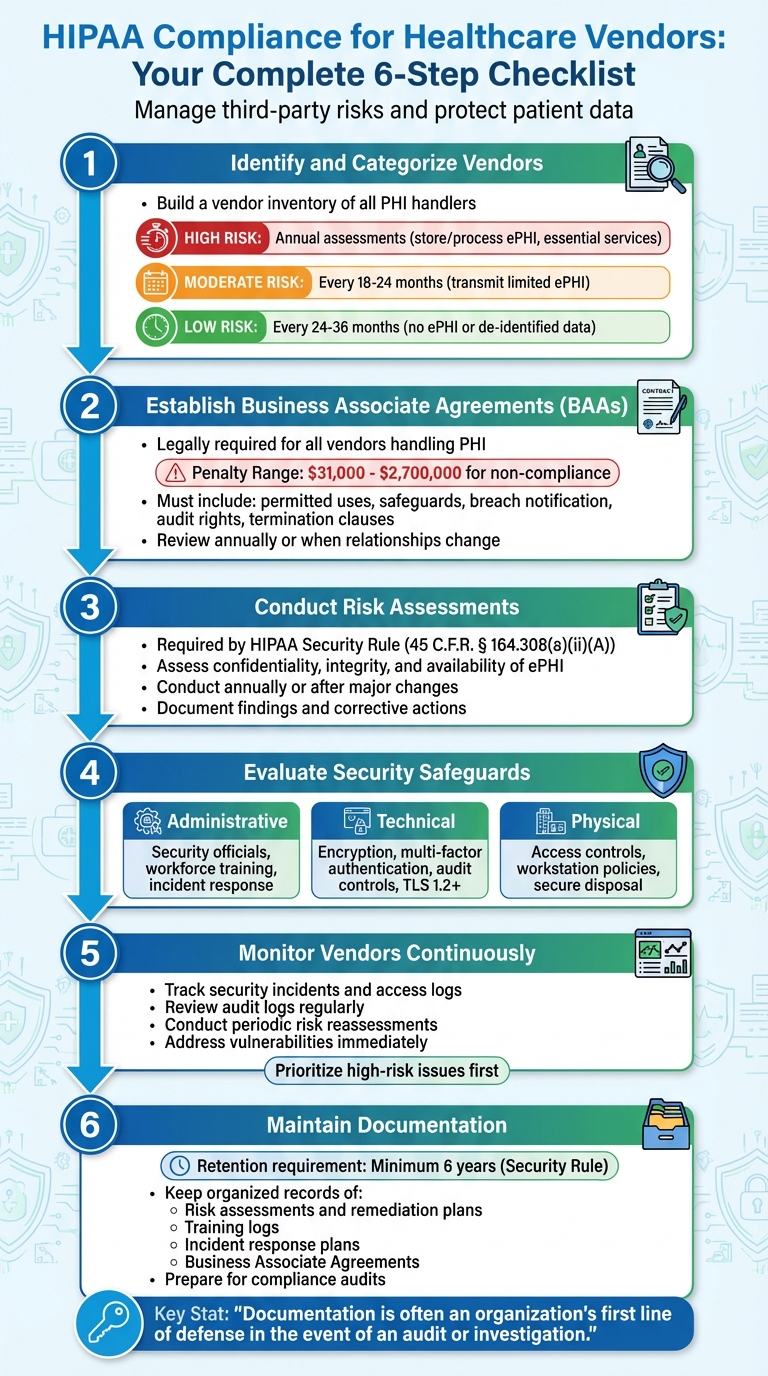
6-Step HIPAA Vendor Compliance Checklist for Healthcare Organizations
Step 1: Identify and Categorize Your Vendors
Build a Vendor Inventory
Start by mapping out every location where electronic PHI (Protected Health Information) flows. This includes both physical assets like servers and workstations and virtual environments such as cloud storage platforms. The HHS Office for Civil Rights emphasizes this step:
"Identify the PHI that your organization creates, receives, stores, and transmits – including PHI shared with consultants, vendors, and Business Associates." [2]
To ensure you capture all relevant third parties - consultants, vendors, and business associates - review project records, interview key stakeholders, and analyze contracts and data access agreements. For added support, use the SRA Tool [3][4], which can streamline your focus on asset and vendor management.
Once this information is gathered, establish a centralized repository to store all vendor-related documentation. This should include contracts, service agreements, and any compliance evidence [7].
Categorize Vendors by Risk Level
After building your vendor inventory, classify each vendor based on their risk level. This depends on the sensitivity of the data they handle and the criticality of their services. Here's a general breakdown:
- High-risk vendors: These vendors store or process ePHI and provide essential services. They require annual assessments.
- Moderate-risk vendors: These vendors may transmit limited ePHI and often have safeguards in place. Assessments are needed every 18–24 months.
- Low-risk vendors: These vendors handle no ePHI or only de-identified data with minimal access. Assessments can be scheduled every 24–36 months [8].
The categorization process starts with scoring the inherent risk (before controls are applied). Then, assess the residual risk after accounting for the vendor’s safeguards [8]. Be sure to document important details for each vendor, such as how they handle ePHI, data flow specifics, storage locations, and access permissions. Don’t overlook subcontractors during this step [8][5].
This tiered system helps prioritize your risk assessments and allocate resources effectively [7].
Step 2: Establish Business Associate Agreements (BAAs)
Required Elements of a BAA
After identifying your vendors, the next step is securing Business Associate Agreements (BAAs) to ensure compliance with HIPAA standards. A BAA is a legally required contract between your healthcare organization (the covered entity) and any vendor that works with Protected Health Information (PHI) [9][10]. Without this agreement, both parties are exposed to significant liability and enforcement risks [9].
The penalties for non-compliance are steep, ranging from $31,000 to $2,700,000. For example, Oregon Health & Science University faced a $2,700,000 fine, while North Memorial Health Care in Minnesota was penalized $1,550,000 between 2016 and 2018 [12].
A comprehensive BAA should include the following key components:
- Permitted and required uses and disclosures of PHI
- Administrative, physical, and technical safeguards
- Breach notification timelines
- Obligations for subcontractors
- Audit rights
- Provisions for patient rights
- Termination clauses
- Procedures for securely returning or destroying PHI
According to HHS regulations (45 CFR §§ 164.502(e) and 164.504(e)), business associates are prohibited from using or disclosing PHI in ways not authorized by the contract or applicable laws [9][10][11][13].
Track and Manage BAA Documentation
Keeping your BAAs organized is just as important as creating them. Use a centralized system to store all agreements, tracking signatures, renewal dates, and any amendments [7][15][16]. Regularly review and update BAAs - annually at a minimum or whenever there are changes in regulations, technology, or vendor relationships [9][11][12]. Tailor each BAA to reflect the specific services and data handling practices of the vendor.
If a vendor refuses to sign a BAA, document the refusal and look for an alternative provider [14][15][16][17]. It's crucial to note that being unaware of HIPAA requirements won't shield you from enforcement actions [2].
To stay on top of compliance, set calendar reminders for BAA renewals and routinely review vendor classifications. If a vendor's risk level changes, update the agreement terms accordingly. This proactive approach helps mitigate risks and ensures ongoing adherence to HIPAA standards.
Step 3: Conduct Risk Assessments and Due Diligence
Perform Initial and Recurring Vendor Assessments
Risk assessments are a key requirement under the HIPAA Security Rule (45 C.F.R. § 164.308(a)(ii)(A))[4] for both covered entities and business associates. The goal? To identify and evaluate potential risks to the confidentiality, integrity, and availability of all electronic Protected Health Information (ePHI) your vendors handle.
Start by defining the scope of your assessment. Pinpoint every location where ePHI is stored or processed - whether on servers, workstations, cloud platforms, backups, or mobile devices. Look for vulnerabilities in vendor security, which could range from outdated encryption protocols to a lack of clear policies.
Examine your vendor's administrative, physical, and technical safeguards. Assess how likely it is for identified threats to be exploited and the potential consequences, such as financial losses, legal penalties, reputational damage, or operational setbacks. Document your findings, assign risk levels, and outline corrective actions to ensure continuous improvement.
Make it a point to conduct these assessments at least once a year or whenever major changes occur - like adopting new technologies, experiencing security incidents, or undergoing operational shifts. Regular evaluations like these set the stage for a more streamlined and effective risk management process.
Use Tools to Streamline Risk Assessments
Manually conducting risk assessments can be a slow and tedious process. Platforms like Censinet Connect™ simplify this by automating vendor onboarding and offboarding while keeping an eye on changes in a vendor's cybersecurity, business, and financial risk profiles. The platform provides real-time insights into system activity, audit logs, and incident reports, eliminating the need for cumbersome spreadsheets and lengthy email threads.
Automated workflows ensure that assessment results reach the right stakeholders for review and approval, boosting accountability within your Governance, Risk, and Compliance teams. With centralized documentation and visual dashboards, you can quickly spot high-risk vendors and focus your mitigation efforts. What used to take weeks can now be completed in just a few days.
Step 4: Evaluate Vendor Security Safeguards
After conducting risk assessments, the next step is to ensure your vendors have effective security measures in place.
Review Administrative Safeguards
Administrative safeguards are the backbone of HIPAA Security Rule compliance. These policies and procedures outline how vendors handle workforce access, respond to security incidents, and maintain ongoing protection of sensitive data. Under HIPAA, Business Associates (your vendors) must adhere to the Security Rule, Breach Notification Rule, and specific Privacy Rule provisions outlined in your Business Associate Agreement (BAA) [2][7].
Start by confirming that your vendor has designated a security official responsible for creating and monitoring security policies. Ensure they conduct mandatory workforce training on managing protected health information (PHI), including access protocols and incident response procedures. Ask for documentation showing how often training occurs and how completion is tracked.
Examine their incident response plan. It should include steps for rapid detection, escalation, containment, and a thorough post-incident analysis. Request evidence of past incidents to evaluate how effectively they handled those situations.
Verify Technical and Physical Safeguards
Beyond administrative measures, technical and physical safeguards are vital for protecting electronic PHI (ePHI).
Technical Safeguards: These involve technology controls to secure ePHI. Under the Security Rule (45 C.F.R. § 164.302–318), vendors must limit ePHI access to authorized users only [18][19]. Confirm the use of unique user IDs, automatic logoff features, and encryption for both stored and transmitted ePHI.
Check if the vendor has audit controls that track system activity. These logs should detail who accessed data, when, and what actions were taken. Inquire about their log retention policies and how often they review logs for suspicious activity.
Ensure multi-factor authentication is in place for accessing systems. Additionally, verify that secure protocols, such as TLS 1.2 (or higher) and VPNs, are used to protect ePHI during network transfers.
Physical Safeguards: These address the security of facilities and equipment that store or process PHI. Vendors should have access controls, such as badge systems, biometric scanners, or on-site security, to restrict entry to sensitive areas [2][16]. Confirm that they have policies governing workstation use, specifying where devices accessing PHI can be used.
Review their procedures for managing devices and media. Vendors should securely dispose of hardware and media containing ePHI through methods like data wiping or shredding. They should also maintain an inventory of devices used to access PHI. Ask to review disposal logs to ensure they follow proper data sanitization practices.
sbb-itb-535baee
Step 5: Monitor Vendors and Mitigate Risks
After completing your initial assessments, the real work begins. Keeping an eye on vendors continuously is essential for staying HIPAA compliant. A one-time risk assessment is just the starting point - ongoing monitoring and reporting are crucial parts of an effective Third-Party Risk Management (TPRM) program for HIPAA compliance [20]. Vendors' environments are constantly changing due to new features, ownership changes, or security incidents. This dynamic nature demands a well-structured approach to monitoring.
Establish Continuous Monitoring Practices
Set up systems to keep tabs on third-party performance, security incidents, and any changes that could impact vendor risk [20]. This includes reviewing audit logs, tracking access reports, and monitoring security incidents [2][7]. Regular check-ins with vendors are also important, especially when they roll out new features or undergo technical changes [1].
Stay informed about external risks as well. Monitor cybersecurity intelligence, reputational updates, and financial indicators that might signal shifts in a vendor’s risk profile [20]. For instance, using audit control software to log events and track activity on systems containing electronic protected health information (ePHI) can show who accessed your data, when they did, and what actions they took [2].
Periodic risk reassessments are key to ensuring that past remediation efforts are still effective and to spotting new risks [20][1]. Risk analysis isn’t a one-and-done activity - it’s an ongoing process [4]. Plan for annual reassessments, and conduct additional reviews if your organization experiences major changes or security incidents.
Resolve Identified Risks Quickly
When monitoring uncovers potential risks, swift action is essential. Develop a process to address vulnerabilities as soon as they’re identified [20]. Focus on high-risk issues first, creating a remediation plan with clear tasks, assigned responsibilities, timelines, and measurable goals [1].
Tools like Censinet RiskOps™ can make this process smoother by automating corrective actions, attaching evidence, and providing real-time updates through alerts and dashboards [1]. This reduces the workload of manually tracking multiple vendors and keeps you updated on compliance status [5][16]. The platform’s command center also offers a clear view of vendor risks, helping you quickly prioritize which issues need immediate attention and ensuring remediation efforts stay on track.
Step 6: Maintain Documentation and Reporting
Keeping thorough documentation is essential for demonstrating compliance during audits. HIPAA mandates that organizations maintain written records - whether on paper or electronically - of their policies, procedures, actions, activities, and assessments.
"Documentation is often an organization's first line of defense in the event of an audit or investigation." – Cynomi [16]
The Security Rule requires organizations to retain risk analysis documentation for at least six years [2]. This includes risk assessments, the reasoning behind security measures, policy documents, and records of remediation efforts. When incidents occur or audits take place, organizations must provide evidence of their policies, identified risks, and the controls they’ve implemented [7]. Without proper or up-to-date documentation, audits can become challenging, as auditors rely heavily on written records, policies, procedures, and access logs to evaluate compliance.
Organize Vendor Evidence and Records
Once risk assessments and monitoring are complete, organizing your documentation becomes critical. Centralizing Business Associate records simplifies compliance management [7]. Your records should include:
- HIPAA risk assessments and remediation plans
- Training logs (with details like training type, date, and certifications)
- Incident response plans and post-incident reviews
- Business Associate Agreements (BAAs)
To ensure consistency, establish a standardized risk assessment process. This could include using checklists to evaluate vendors, ensuring all third-party relationships meet the same compliance standards [6]. Automated systems that generate audit reports for unauthorized access can help trace breaches and demonstrate accountability. Platforms like Censinet RiskOps™ can centralize vendor documentation, making it easier to manage contracts, assessment reports, security policies, and compliance evidence in one place.
Prepare for Compliance Audits
Well-organized documentation not only helps with day-to-day compliance but also strengthens audit readiness. Ensure your records are comprehensive and easy to access. This approach not only speeds up the audit process but also reflects your organization’s commitment to compliance [16]. Policies should be reviewed at least annually [2], and any completed activity should have accompanying documentation as proof [7].
Regularly report your progress to leadership using executive summaries, dashboards, or board updates. Highlight resolved risks, improvements in compliance practices, and ongoing challenges. These reports help maintain leadership support and demonstrate your dedication to protecting patient information. Incorporate lessons from assessments into policy updates, security training, and procedural improvements to ensure compliance remains an ongoing effort.
Conclusion
Key Takeaways for Healthcare Organizations
Following the six-step checklist is essential for healthcare organizations aiming to strengthen their HIPAA compliance strategy. Each step plays a crucial role in safeguarding patient data and managing vendor relationships effectively.
Managing third-party risk under HIPAA isn’t optional - it’s a requirement, and the consequences for non-compliance can be severe. Recent breaches highlight just how important vendor risk management is [16]. By implementing this six-step framework, organizations can better protect patient information while improving overall vendor oversight. Here’s a quick summary of the steps:
- Build a detailed vendor inventory and assess risks.
- Establish and monitor Business Associate Agreements for all vendors handling PHI.
- Conduct thorough, recurring risk assessments.
- Evaluate security measures across administrative, technical, and physical controls.
- Implement continuous monitoring systems.
- Maintain clear, up-to-date documentation for compliance and audit readiness.
A comprehensive HIPAA risk assessment not only helps with vendor management but also addresses multiple areas of HIPAA compliance [2]. Effective vendor risk management strengthens your overall compliance posture, and integrating technology can make this process even more seamless.
How Technology Simplifies Compliance
Technology brings efficiency and scalability to the compliance process. By centralizing documentation and automating risk assessments, healthcare organizations can manage their vendor relationships more effectively without sacrificing thoroughness.
For example, tools like Censinet AITM™ allow vendors to quickly complete security questionnaires while the platform automatically compiles evidence, captures integration details, and generates detailed risk reports. These automated processes, combined with human oversight, ensure that compliance tasks are handled efficiently and accurately. With the right tools, healthcare organizations can reduce risk faster and make compliance a manageable, ongoing effort instead of an overwhelming challenge.
FAQs
What should be included in a Business Associate Agreement (BAA) to ensure HIPAA compliance?
A Business Associate Agreement (BAA) plays a critical role in ensuring HIPAA compliance by outlining the responsibilities and expectations for handling Protected Health Information (PHI). A well-constructed BAA should address the following key elements:
- Permitted uses and disclosures: Specify how PHI can be used or shared, strictly within the boundaries of HIPAA regulations.
- Safeguards: Detail the measures that must be in place to protect PHI from unauthorized access or breaches.
- Incident reporting: Require prompt notification of any security incidents or breaches involving PHI.
- Subcontractor compliance: Ensure that any subcontractors handling PHI also adhere to HIPAA standards.
- PHI disposal or return: Outline the process for securely returning or destroying PHI once the agreement concludes.
By addressing these areas, healthcare organizations can better manage risks and maintain HIPAA-compliant relationships with their vendors.
How often should healthcare organizations assess vendor risks based on their risk level?
For vendors classified as high-risk, it's advisable to perform risk assessments at least once a year. However, if the data or services they handle are particularly sensitive, you might need to conduct these assessments more often - think quarterly or following major events like a system upgrade or a data breach.
Vendors with moderate or low risk don't require assessments as frequently, but regular reviews are still crucial. These periodic checks help ensure compliance and address any new risks that may arise. Adjusting the assessment schedule based on a vendor's risk level is a smart way to stay ahead in protecting data and meeting HIPAA requirements.
What tools can help simplify and automate HIPAA compliance for healthcare vendors?
Automating HIPAA compliance can make the process faster and help minimize mistakes. Tools like the HIPAA Security Risk Assessment (SRA) Tool and platforms such as Censinet RiskOps™ are built to streamline the work involved. These tools provide features like guided risk assessments, ongoing monitoring, and real-time tracking of vendor security measures.
With these solutions, healthcare organizations can take a proactive approach to managing third-party risks while staying aligned with HIPAA regulations. This not only simplifies compliance but also strengthens the protection of sensitive patient information.


