HIPAA Compliance and Key Management in Healthcare Clouds
Post Summary
When healthcare data moves to the cloud, encryption is critical - but key management is just as important. Without properly managing encryption keys, even encrypted data can be exposed. Under HIPAA’s shared responsibility model, cloud providers secure the infrastructure, but healthcare organizations must safeguard keys and control access. Poor key practices, like storing keys with encrypted data or neglecting key rotation, can lead to breaches and regulatory penalties.
Key points:
- HIPAA’s Security Rule requires encryption and robust key management to protect ePHI.
- Shared responsibility: Cloud providers manage infrastructure; healthcare entities handle keys and access.
- Breach impact: Proper key management can exempt encrypted data from breach notifications.
- Three key management models: Customer-Managed Keys (CMK), Provider-Managed Keys (PMK), and hybrid approaches like Bring Your Own Key (BYOK).
- NIST guidelines recommend strong encryption, key rotation, and secure storage in hardware or dedicated systems.
Effective key management reduces breach risks and supports HIPAA compliance. Choose the right strategy - CMK for control, PMK for simplicity, or hybrid for flexibility - and integrate it into risk assessments and vendor agreements.
HIPAA Security Rule and Cloud Encryption Requirements
Technical Safeguards for ePHI Protection
The HIPAA Security Rule outlines five essential technical safeguards that healthcare organizations must implement to protect electronic protected health information (ePHI). These include:
- Access controls: Measures like unique user IDs, emergency access procedures, automatic logoff, and encryption.
- Audit controls: Systems to record and review all activity related to ePHI.
- Integrity protections: Tools like checksums and digital signatures to prevent unauthorized changes.
- Person or entity authentication: Methods such as multi-factor authentication or digital certificates to verify access.
- Transmission security: TLS-based encryption to safeguard ePHI during network transmission.
Encryption has become a critical standard for securing ePHI in cloud environments. This is especially important since hacking incidents have been responsible for more than 70% of large healthcare data breaches in recent years [4].
Cloud Service Provider Responsibilities Under HIPAA
When a cloud service provider (CSP) handles ePHI - whether by creating, receiving, maintaining, or transmitting it - it is classified as a Business Associate under HIPAA. Even if the CSP stores encrypted ePHI without access to the decryption keys, it is still bound by HIPAA regulations and must sign a Business Associate Agreement (BAA) with the covered healthcare entity.
A well-constructed BAA is crucial. It should clearly define responsibilities for encryption and key management, specifying whether encryption keys are managed by the customer, the provider, or an external party. It must also outline timelines for incident response and breach notifications, particularly in the event of key compromises. While CSPs provide the infrastructure for encryption at rest and in transit, the responsibility for properly configuring these services - including securing encryption keys - falls on the healthcare organization. This division of duties is key to maintaining compliance and managing breach protocols effectively.
Encryption Requirements and Breach Notification Rules
Encryption practices play a pivotal role in determining breach reporting obligations under HIPAA. According to the HIPAA Breach Notification Rule, there is a "safe harbor" provision for properly encrypted data. If ePHI is encrypted following guidelines from the Department of Health and Human Services (HHS) and the National Institute of Standards and Technology (NIST), and the encryption keys remain secure, an incident may not qualify as a reportable breach. This reduces both notification requirements and potential legal exposure.
However, maintaining this safe harbor status hinges on effective key management. Practices such as storing encryption keys alongside encrypted data, neglecting regular key rotation, or allowing unauthorized access can void the safe harbor. This could trigger full breach notification requirements, impacting millions of patient records and potentially leading to costly settlements or mandated corrective actions. Proper key management is not just a best practice - it’s essential for reducing risk and ensuring compliance.
Research Findings on Encryption and Key Management
How Encryption Reduces PHI Breach Impact
Studies reveal that modern encryption paired with separate key management significantly reduces the risk and impact of PHI breaches. By encrypting ePHI in cloud systems using robust algorithms like AES-256 and storing encryption keys separately from the data, encrypted PHI remains unreadable without access to the keys. This approach ensures such incidents aren't categorized as reportable breaches under the HIPAA Breach Notification Rule [7].
Healthcare organizations that implement encryption for both data at rest and in transit - along with stringent access controls and key monitoring - see fewer large-scale data exfiltration events and lower costs per breached record. Encryption renders the data unusable and indecipherable without the associated keys [11][3]. Cloud providers offering built-in encryption solutions with centralized key management and HSM-backed services, such as AWS KMS, Azure Key Vault, or GCP CMEK, report that healthcare clients utilizing these tools are better equipped to meet HIPAA Security Rule requirements. This also helps reduce the scale and severity of security incidents involving ePHI [3][5].
These findings make it clear why poor key management can dramatically increase breach risks.
Common Key Management Security Weaknesses
Inadequate key management undermines the benefits of encryption and can turn minor security incidents into reportable breaches under HIPAA. Analyses of breaches show that poor key management often leads to reportable PHI breaches, especially when attackers gain access to both encrypted ePHI and the associated keys or credentials. In such cases, the regulatory safe harbor provided by encryption is lost, triggering breach notifications and potential OCR investigations [7].
Frequent vulnerabilities include stolen API keys or IAM roles that enable decryption, as well as private keys or secrets accidentally exposed in public code repositories used by healthcare applications connecting to cloud databases [3][4]. Additionally, common HIPAA violations in cloud environments - such as weak encryption, missing audit logs, and insufficient backup practices - are often linked to immature key management processes [8]. Embedding keys in code or templates is a critical misstep. Instead, keys should be retrieved securely at runtime using services like KMS or HSM.
These recurring issues underscore the importance of adhering to robust standards like those outlined in NIST guidelines.
NIST Guidelines for Key Management

NIST SP 800-57 provides essential recommendations for safeguarding sensitive data, including ePHI, in cloud environments. According to the standard, symmetric keys should be generated using validated cryptographic modules with approved random number generators, meeting minimum strength requirements such as 128-bit or 256-bit keys for AES [7].
NIST also highlights the importance of limiting a key's cryptoperiod (its active lifespan) based on its usage and sensitivity. Shorter lifespans and frequent key rotations, especially for high-value or widely used keys, reduce the potential damage if a key is compromised [7]. In cloud settings, this means leveraging provider key-management services that support automatic key rotation, strong random number generation, and FIPS 140-validated modules for key generation and storage [4][5].
The guidelines stress that keys must be stored in secure cryptographic modules or services that enforce access controls, prevent unauthorized access, and resist tampering. Keys should never be stored in plaintext in general-purpose storage [7]. Secure backup procedures are equally critical - keys should be encrypted under a separate master key, stored in geographically dispersed secure locations, and access to backup media should be tightly controlled [7].
Key Management Approaches for Healthcare Cloud Systems
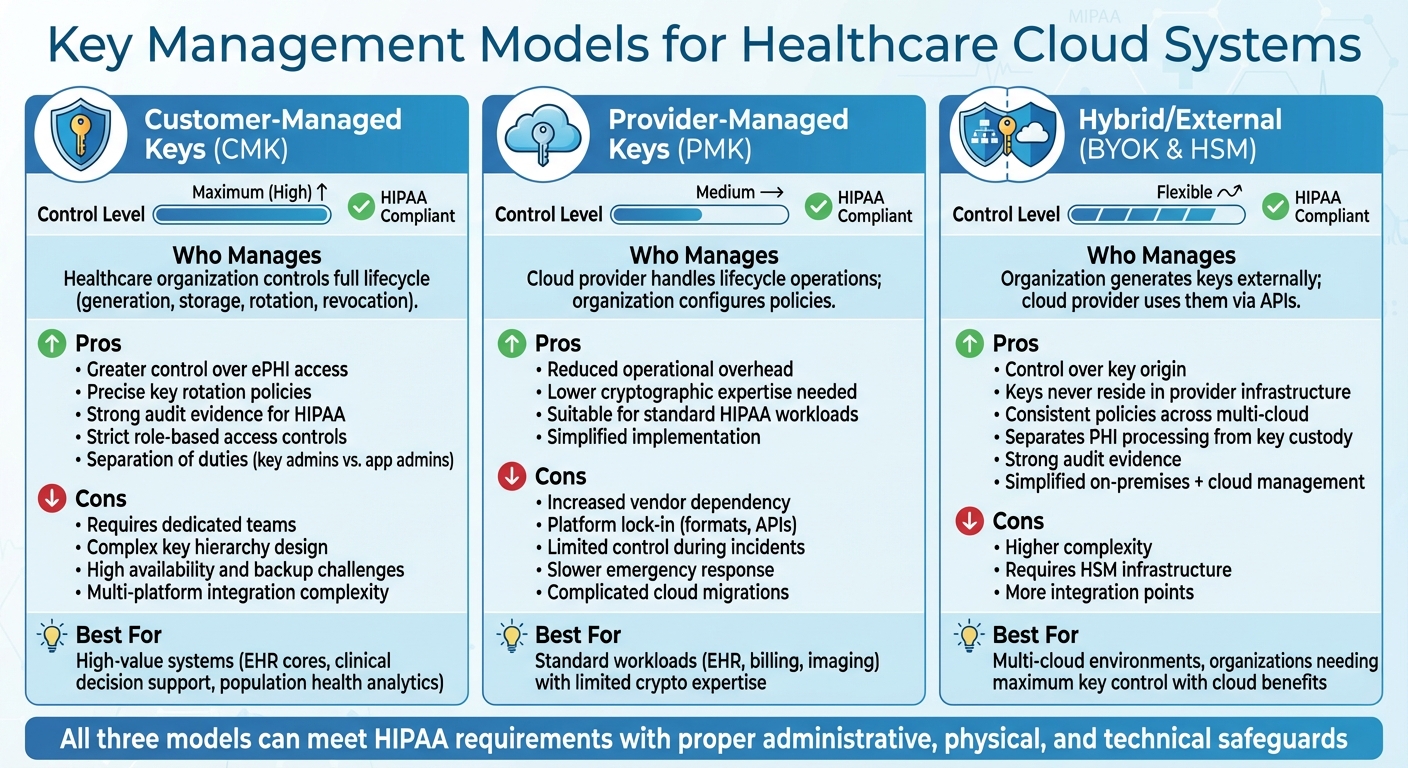
Three Key Management Models for HIPAA-Compliant Healthcare Cloud Systems
When healthcare organizations move electronic protected health information (ePHI) to the cloud, one critical decision looms: who manages the encryption keys? While HIPAA doesn't specify a particular key management model, it does demand that encryption keys are properly safeguarded, access-controlled, and managed throughout their lifecycle [6][10]. This responsibility falls on healthcare organizations, which must clearly define key management roles within a shared-responsibility framework [6][9].
There are three main approaches to key management: Customer-Managed Keys (CMK), Provider-Managed Keys (PMK), and hybrid or external key management models (such as Bring Your Own Key or external HSM integration). Each comes with its own set of pros and cons in terms of control, complexity, and HIPAA compliance risks [3][4][5]. Choosing the right model depends on a risk-based evaluation tailored to specific workloads, documented in the organization’s HIPAA risk analysis, and aligned with technical safeguard requirements. Here’s a closer look at each model.
Customer-Managed Keys (CMK)
With CMK, the healthcare organization takes full control of the key lifecycle, including generation, storage, rotation, and revocation, often using industry-standard key management services [3][5]. This approach provides greater control over access to ePHI, allowing for more precise key rotation policies and robust evidence for HIPAA audits [5][9]. Organizations can enforce strict role-based access controls, separate key administrators from application or database administrators to uphold least privilege principles, and log every key operation for audit purposes [4][10].
However, managing keys independently comes with challenges. Organizations need dedicated teams to design key hierarchies, ensure high availability and backups, and integrate key management across multiple cloud platforms and SaaS services [3][4]. Missteps, such as failing to rotate keys or misconfiguring IAM roles, can undermine the security benefits and expose ePHI. CMK is often the go-to choice for high-value systems like EHR cores, clinical decision support tools, or population health analytics, where demonstrating clear separation of duties and least privilege is crucial for audits or OCR reviews [2][6].
Provider-Managed Keys (PMK)
In the PMK model, the cloud provider handles most key lifecycle operations - such as generation, storage, and rotation - while the healthcare organization configures access and usage policies [3][5]. This setup reduces operational overhead, making it a practical choice for organizations with limited cryptographic expertise but still requiring HIPAA-grade encryption for workloads like EHR, billing, or imaging [4][5].
The trade-off? Increased dependency on the cloud provider. Key formats, APIs, and lifecycle processes are closely tied to the provider’s platform, complicating cloud-to-cloud migrations or partial exit strategies. In the event of a security incident, the organization may have limited control over key revocation or emergency access restrictions, which could slow response efforts [2][4][5][6]. To maintain compliance, organizations must still implement access controls, perform risk assessments, and monitor activity. PMK doesn’t eliminate HIPAA obligations - it simply shifts certain responsibilities to the provider under the shared-responsibility model [2][6]. It’s essential to confirm through the Business Associate Agreement and supporting documentation that the provider’s key management service includes audit logs, strong administrative controls, and multi-factor authentication [4][5].
Hybrid and External Key Management Options
Hybrid models, such as Bring Your Own Key (BYOK) and external HSM integration, address some of the limitations of CMK and PMK by offering greater control over key material while still leveraging cloud-native encryption [4][5]. In a BYOK setup, the organization generates encryption keys in an on-premises HSM or another trusted external system, then securely transfers them to the cloud provider’s key management service. This allows the organization to retain control over key origin and some policy decisions [3][5]. External HSM integration takes this a step further, with cryptographic operations or master key storage happening entirely in customer-controlled HSMs. The cloud environment interacts with these keys via APIs or connectors, ensuring the most sensitive keys never reside in the provider’s infrastructure [3][4].
For HIPAA compliance, these hybrid approaches provide added flexibility and assurance. They allow organizations to separate PHI-processing workloads in the cloud from key custody, which can be maintained in healthcare-controlled or certified third-party environments [2][6][7]. Hybrid models also simplify managing PHI across on-premises systems (like PACS or lab systems) and multiple public clouds, enabling consistent key policies. Additionally, they strengthen evidence of due diligence and layered safeguards in risk assessments, which can be critical during audits or OCR reviews [2][6][7]. Organizations using hybrid models should document their architectures in HIPAA risk assessments and technical documentation, including detailed data-flow diagrams that outline where keys are stored and how they’re used [6][10].
Key Takeaways
All three models - CMK, PMK, and hybrid - can meet HIPAA requirements if configured with the proper administrative, physical, and technical safeguards. The differences lie in how granular the audit capabilities are, the level of vendor dependency, and the clarity with which roles and responsibilities are defined in the shared-responsibility model [2][6]. Tools like Censinet RiskOps™ can help healthcare organizations monitor key-related risks across PHI systems, providing insights into key rotation schedules, failed access attempts, and encrypted asset coverage during HIPAA risk assessments and safeguard reviews [4].
sbb-itb-535baee
Key Management Effects on HIPAA Compliance and Breach Risk
Encryption plays a major role in reducing risks, but how encryption keys are managed can significantly impact breach outcomes and compliance efforts. For healthcare organizations, the way encryption keys are handled directly affects breach reporting and potential regulatory penalties. When encryption keys are properly secured, electronic protected health information (ePHI) remains protected, often exempting incidents from notification requirements. However, if those keys are compromised, this exemption no longer applies. This gap in key protection is a common focus of enforcement actions by the Office for Civil Rights (OCR).
OCR Enforcement Actions Related to Key Management
OCR frequently highlights failures in risk analysis, risk management, and technical safeguards in its enforcement actions. Settlements and fines often point to inadequate encryption and related controls as contributing factors[6]. In cloud environments, healthcare organizations are often cited for violations such as weak encryption, insufficient access controls, poor audit logging, and inadequate cloud risk assessments[8]. Even when encryption is implemented, poorly managed keys - such as shared administrative access, storing keys alongside encrypted data, or failing to log key usage - can negate the safe harbor protections. This can trigger breach notification requirements and lead to penalties for violating the Security Rule[6][8].
Evidence of Breach Reduction Through Proper Key Management
Organizations that adopt strong encryption and robust key management practices report fewer and less severe breaches. Addressing common compliance gaps - like separating keys from encrypted data, using dedicated key management systems or hardware security modules (HSMs), and enforcing least-privilege access - can significantly reduce the risk of successful attacks and lessen regulatory consequences[6][4]. Proper key management also allows for rapid responses, such as revoking compromised keys or rotating credentials, and provides clear documentation for OCR reviews. These practices align with recommendations from the Department of Health and Human Services (HHS) and OCR.
HHS and OCR Guidance on Key Management Practices
HHS and OCR stress that covered entities and business associates must conduct thorough risk analyses, especially for cloud-hosted ePHI, and implement encryption as a critical technical safeguard whenever it is reasonable and appropriate[6][7]. Their guidance on cloud computing highlights the shared responsibility between healthcare organizations and cloud service providers in protecting ePHI. This includes managing encryption keys through strong access controls, audit trails, and integrity protections[6].
OCR also directs organizations to follow best practices outlined in NIST publications. These include using strong encryption algorithms, securing keys in hardware or dedicated services, enforcing least-privilege access, and documenting the entire key lifecycle - from generation and distribution to storage, rotation, and destruction[6][7]. By aligning with these standards and thoroughly documenting key management strategies in risk assessments, organizations can better demonstrate compliance during audits and OCR evaluations.
Implementing Key Management in Healthcare Risk Programs
Integrating effective key management into healthcare risk programs is essential for maintaining HIPAA compliance and safeguarding sensitive data. To achieve this, organizations should embed key management practices into risk assessments, vendor agreements, and governance documents. Start by cataloging all cloud systems that handle ePHI - such as SaaS, IaaS, and medical device platforms - and document their encryption status, key ownership, and lifecycle processes. This method ensures that key management becomes a standard part of risk analysis rather than an afterthought.
Adding Key Management to Risk Assessments
Encryption and key management must be explicitly addressed in third-party risk assessments and Business Associate Agreements (BAAs). Security questionnaires should evaluate encryption algorithms, key lengths, storage methods (e.g., hardware security modules or cloud-based key management), rotation frequency, and separation of roles between application and key administrators. BAAs should clearly define responsibilities for key generation, storage, backup, rotation, and destruction. They should also include notification procedures for potential key compromises and specify audit log requirements that align with HIPAA documentation standards.
Internal policies should outline the roles of key stakeholders - like the CISO, security engineering teams, and cloud operations - and establish documented processes for key rotation, recovery, and emergency access (commonly referred to as "break-glass" access). These well-defined protocols lay the groundwork for automated and centralized risk monitoring.
Using Centralized Risk Management Platforms
Specialized platforms can simplify the assessment and monitoring of encryption and key management practices across multiple cloud providers and vendors. For instance, Censinet RiskOps™ allows healthcare organizations to evaluate key management during third-party risk assessments and continuously monitor cloud security controls. A real-world example: Tower Health reduced its risk assessment team from five full-time employees to just two after implementing Censinet RiskOps [1].
Improving Team Collaboration and Compliance Tracking
Centralized platforms replace manual processes - like spreadsheets - with a unified system where teams from security, compliance, IT, and procurement can collaborate on key management decisions. For example, Baptist Health eliminated spreadsheets entirely and improved cybersecurity collaboration, as highlighted by VP & CISO James Case [1]. These platforms also enable continuous monitoring by setting up alerts for critical events, such as disabled encryption on storage resources, failed key rotations, or unusual activity in key management services. Additionally, conducting regular tabletop exercises to simulate key compromise scenarios helps test incident-response plans and strengthens cross-functional collaboration.
Conclusion
Encryption and key management play a crucial role in safeguarding healthcare organizations that store or process ePHI in cloud environments. While encryption is labeled as "addressable" under HIPAA's Security Rule, both HHS and OCR strongly encourage its implementation whenever it is reasonable and appropriate. However, encryption alone isn't enough - effective key management is equally vital. Poorly managed keys can compromise encrypted data, turning what could have been a non-reportable incident into a full-scale breach requiring notification.
In the shared-responsibility model, cloud providers handle infrastructure security, while healthcare organizations are responsible for managing encryption keys and access controls. This division of responsibilities needs to be clearly outlined in Business Associate Agreements, security policies, and risk assessments. OCR enforcement actions have shown that organizations with weak encryption and key management controls are more likely to face reportable breaches and penalties. On the other hand, those with well-implemented controls can significantly reduce the impact of incidents.
Selecting the right key management strategy - whether customer-managed (CMK), provider-managed (PMK), or a hybrid approach - depends on factors like risk tolerance, technical expertise, and the sensitivity of workloads. For high-risk PHI, CMK offers greater control and independent lifecycle management. PMK may be a better fit for lower-risk workloads, provided the cloud provider’s key management service aligns with HIPAA requirements and is covered under the BAA. Hybrid or external key management solutions allow organizations to maintain control over master keys while benefiting from the scalability of cloud services.
To integrate key management into HIPAA compliance efforts, organizations should adopt NIST-aligned practices. These include generating strong keys, enforcing strict access controls, rotating keys regularly, maintaining secure backups, and keeping detailed audit logs. Such measures strengthen compliance monitoring and reduce risk, as underscored by the risk management findings. Tools like Censinet RiskOps™ can further streamline this process by helping organizations monitor encryption status, track key ownership, and manage vendor responsibilities across risk assessments. This centralized approach simplifies evidence collection for audits and improves collaboration across security, compliance, IT, and procurement teams.
Encryption and key management are ongoing responsibilities rather than one-time tasks. By embedding these practices into risk assessments, vendor agreements, continuous monitoring, and incident response plans, healthcare organizations can reduce the likelihood of breaches, minimize regulatory exposure, and better protect patient data in today’s cloud-reliant world.
FAQs
What’s the difference between customer-managed and provider-managed encryption keys in healthcare cloud systems?
Customer-managed keys (CMKs) allow healthcare organizations to take the reins when it comes to encryption. With CMKs, you have full control over your encryption keys, meaning you can directly manage access and security. This setup offers stronger protection for sensitive information like Protected Health Information (PHI), but it does come with added responsibility - it requires more time, effort, and expertise to maintain effectively.
On the flip side, provider-managed keys (PMKs) shift the responsibility to the cloud provider. This option streamlines key management, reducing the operational workload for your team. However, the trade-off is less direct control over encryption processes, which may not meet the needs of every organization.
Deciding between CMKs and PMKs boils down to your organization's specific compliance requirements and how much risk you're willing to accept. If maintaining tight control over sensitive healthcare data is a top priority, CMKs are often the go-to choice.
How does effective key management support HIPAA breach notification compliance?
Effective key management is essential for keeping healthcare organizations in line with HIPAA breach notification rules. By securely handling encryption keys, they can protect the confidentiality and integrity of protected health information (PHI), minimizing the chances of unauthorized access to sensitive data.
When a security incident occurs, having a solid key management strategy allows for quicker detection, response, and resolution. This ensures compliance with HIPAA's strict timelines for breach notifications. Beyond meeting regulatory requirements, this approach safeguards patient privacy, shields organizations from potential fines, and helps maintain their reputation.
How do Business Associate Agreements (BAAs) support HIPAA compliance for cloud encryption and key management?
Business Associate Agreements (BAAs) play a key role in maintaining HIPAA compliance when working with cloud services. These agreements clearly spell out the responsibilities of cloud service providers to safeguard protected health information (PHI) and adhere to HIPAA regulations.
By specifying security requirements, BAAs ensure that critical measures like encryption and key management align with the standards needed to protect patient data. This applies to both storing and transmitting information in the cloud, enabling healthcare organizations to handle sensitive data securely while staying compliant.


