HIPAA-Compliant Wireless Network Setup Guide
Post Summary
If your Wi-Fi network handles electronic protected health information (ePHI), ensuring compliance with the HIPAA Security Rule is non-negotiable. Wireless networks are particularly vulnerable to breaches due to their reliance on radio frequencies. A misstep, such as using outdated encryption or failing to monitor access points, can lead to data exposure, regulatory fines, and damaged trust.
What does a HIPAA-compliant wireless network require?
- Strong encryption: Use WPA2 or WPA3 Enterprise with 802.1X authentication.
- Network segmentation: Separate clinical, administrative, and guest traffic.
- Role-based access controls: Restrict ePHI access to authorized users.
- Continuous monitoring: Detect rogue devices and configuration issues.
Key safeguards include encrypting data during transmission, conducting regular risk assessments, and using tools like RADIUS servers for authentication. Proper planning, technical controls, and administrative policies ensure your wireless setup aligns with HIPAA standards while maintaining secure access for clinicians and devices.
Actionable Steps:
- Perform a risk assessment to identify vulnerabilities.
- Deploy WPA3 Enterprise encryption and segment networks by role (e.g., clinical, guest).
- Monitor access points and logs for anomalies.
- Train staff on secure device use and incident reporting.
This guide dives deeper into designing, securing, and managing a HIPAA-compliant wireless network to protect patient data while supporting healthcare operations.
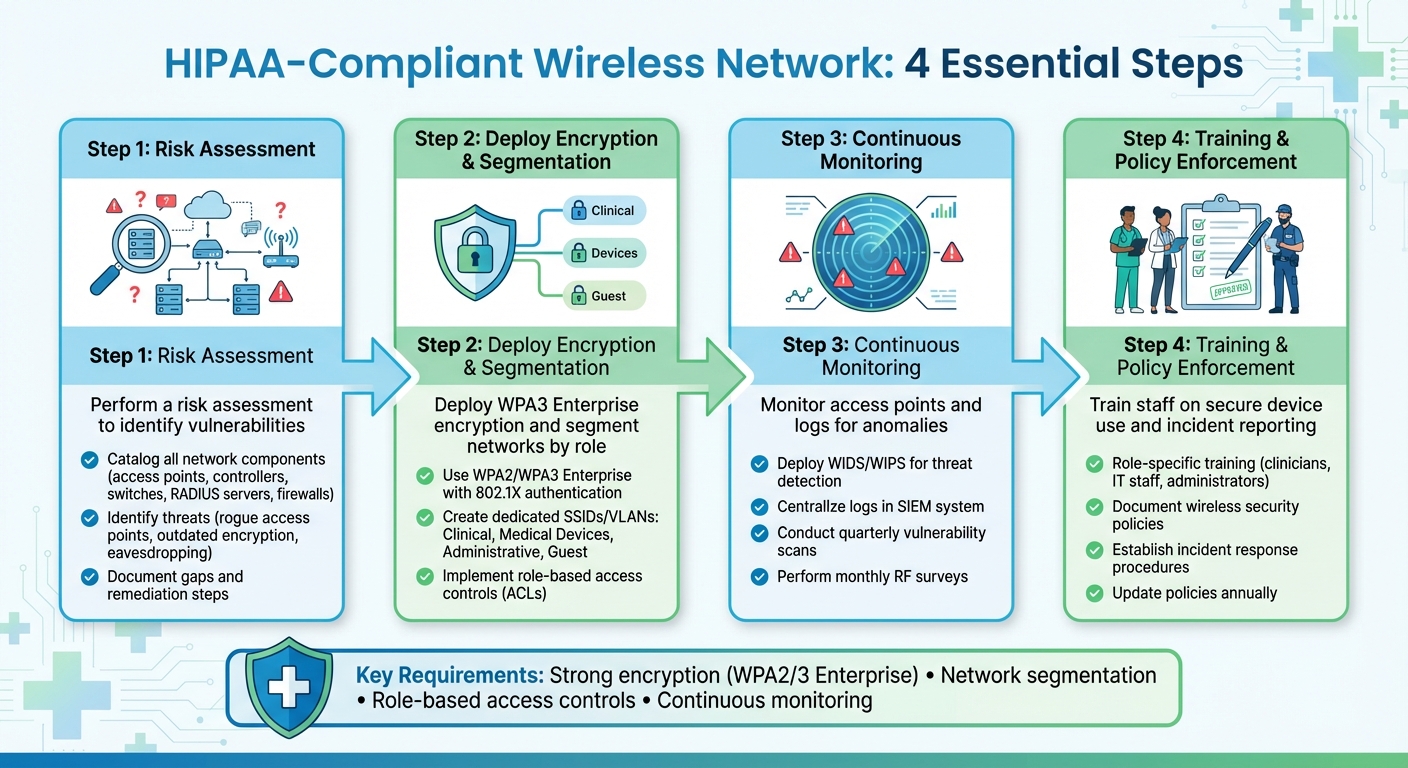
4-Step HIPAA-Compliant Wireless Network Implementation Process
Planning a Secure Wireless Network Architecture
Before setting up access points, it's essential to create a detailed blueprint that aligns your wireless infrastructure with HIPAA safeguards. This design must carefully balance the confidentiality, integrity, and availability of ePHI while ensuring it supports clinical workflows seamlessly. This planning phase sets the groundwork for the technical configurations we'll discuss later. Key areas to focus on include risk assessment, network segmentation, and authentication practices to secure your wireless network.
Conducting a Wireless Risk Assessment
Start by cataloging every component in your network - access points, controllers, switches, RADIUS servers, firewalls, and any critical devices. Map out where ePHI is generated, accessed, or transmitted across your network. Then, identify potential wireless threats, such as rogue or unauthorized access points, outdated encryption protocols like WEP, shared passwords, misconfigured guest networks, eavesdropping, man-in-the-middle attacks, and denial-of-service attempts. Assess each threat based on its likelihood and potential impact. For instance, an open SSID in a public waiting area carries a much higher risk compared to a misconfigured access point in a locked server room.
Next, evaluate your current controls against these risks. Are you using WPA2 or WPA3 Enterprise with 802.1X authentication? Do you have centralized management and logging for all access points? Is there a wireless intrusion detection system in place, or do you regularly scan for rogue devices? Document any gaps and outline remediation steps, such as adopting WPA2-Enterprise, enforcing network access control, or assigning medical devices to dedicated VLANs. Prioritize these actions based on their clinical impact and compliance needs. Tools like Censinet RiskOps™ can help formalize this process by tracking third-party wireless vendors, cloud-hosted controllers, and medical device ecosystems as part of your overall risk management strategy.
Network Segmentation and Zoning
Segmenting your wireless network is critical. Assign dedicated SSIDs and VLANs for different purposes - clinical, medical devices, administrative, and guest use. For example:
- A clinical SSID could support devices accessing EHR, PACS, and lab systems.
- A medical device SSID would handle IoT equipment like monitors and pumps, with strict rules limiting communication to specific application servers.
- An administrative SSID might serve billing and back-office systems.
- A guest SSID should be isolated on its own VLAN, offering internet-only access with no routes to internal networks.
Firewalls at the distribution or core layer should enforce default-deny policies between these zones, with explicit allow rules for documented workflows. For instance, radiology carts may need access to imaging servers but not pharmacy systems. Role-based access control lists (ACLs) can further restrict access based on user or device roles, minimizing the damage if a device or account is compromised. This zoning approach not only supports HIPAA's access control and transmission security requirements but also ensures clinicians have the connectivity they need without compromising security.
Authentication and Device Onboarding
Ditch shared Wi‑Fi passwords in favor of WPA2-Enterprise or WPA3-Enterprise with 802.1X authentication and a RADIUS server. When a user or device connects to a secure SSID, the access point forwards credentials or certificates to the RADIUS server. The server validates these credentials and provides per-session encryption keys and VLAN assignments. This setup ensures each user or device has unique credentials, robust AES-encrypted sessions, and role-based access control through RADIUS attributes that assign specific VLANs or downloadable ACLs.
With your network segmented, focus on robust authentication to control device access. Tailor onboarding processes based on device type. For corporate-managed laptops and tablets, use an MDM solution to push Wi‑Fi profiles automatically and enforce device health checks (e.g., OS patch levels, antivirus status) before granting access to clinical VLANs. For clinician smartphones or BYOD devices, if permitted, use an SSID with network access control and a captive portal for onboarding. This portal can install certificates or enrollment profiles, then segment BYOD devices into a restricted VLAN with access limited to approved applications. This approach meets HIPAA's requirements for unique user identification, access control, and authentication, while also protecting against eavesdropping and unauthorized wireless access.
Implementing Technical Controls for HIPAA Compliance
Once your network is designed and segmented, the next step is to secure your wireless infrastructure by applying HIPAA technical safeguards. These include access control, integrity, authentication, and secure transmission measures. These safeguards are critical for protecting electronic Protected Health Information (ePHI) as it moves across your wireless network, ensuring that only authorized users and devices can connect. Below, we’ll dive into specific configurations to strengthen your wireless environment.
Configuring Wireless Access Points and Controllers
Begin by changing default SSIDs and admin credentials on all access points and controllers. Use strong, unique passwords and store them securely in a password manager. Instead of sharing a single login, create role-based admin accounts for better accountability. Disable outdated management protocols like Telnet and HTTP, and restrict access to more secure options like SSH and HTTPS. Additionally, limit access to management interfaces by allowing connections only from specific admin subnets, keeping them isolated from clinical or guest VLANs. Make it a habit to update firmware regularly to address any emerging vulnerabilities.
Position access points away from exterior walls and adjust their transmit power to minimize signal leakage, reducing the risk of unauthorized access from outside the facility. For SSIDs that connect to systems handling ePHI, configure WPA2-Enterprise or WPA3-Enterprise with 802.1X authentication. This ensures that only authorized users and devices can connect. Lastly, log all administrative actions on access points and controllers to maintain an audit trail, which is essential for compliance reviews.
Encryption and Secure Data Transmission
Encryption is a cornerstone of protecting ePHI. Use WPA2/3 Enterprise with AES-CCMP for Wi-Fi encryption, and enforce TLS 1.2 or higher at the application layer to secure all data transmissions. Confirm that your EHR, patient portal, and telehealth tools use strong encryption protocols and disable outdated ones.
When ePHI needs to travel over untrusted networks - such as when clinicians work remotely using public Wi-Fi or when facilities connect via third-party links - require VPN tunnels (IPsec or SSL VPN). These tunnels encrypt all traffic end-to-end and ensure that access is tied to individual identities. Policies should explicitly prohibit ePHI from being transmitted over open or guest Wi-Fi unless an encrypted VPN tunnel is in use. Additionally, any new wireless application should undergo a review to confirm it complies with approved encryption standards. These steps ensure that every wireless data transmission aligns with HIPAA requirements.
Identity and Access Management
Encryption alone isn’t enough; robust identity management ensures that only the right users and devices gain access. Implement 802.1X authentication with a RADIUS server tied to your directory service, such as Active Directory. When a device connects to a secure SSID, the access point sends credentials or certificates to the RADIUS server, which verifies them and assigns the device to the appropriate VLAN with the correct access policies. For clinical devices owned by the organization, certificate-based EAP-TLS is ideal. It eliminates the need for user-entered passwords and allows centralized management of certificates, including their revocation if a device is lost or retired.
For user laptops and mobile devices, enforce authentication using domain credentials or managed certificates tied to specific roles. This enables role-based network access control - for instance, clinicians can access the EHR and medication systems, while billing staff are restricted to administrative servers. Add an extra layer of security by implementing multi-factor authentication (MFA) for remote access, such as VPNs or cloud-based EHR portals, and for privileged access to network management consoles.
For guest users, create SSIDs that use captive portals with short-lived tokens or vouchers. Avoid sharing corporate credentials on guest networks, and apply strict firewall rules to block access to internal systems. Finally, log RADIUS accounting data in a central SIEM system. This provides detailed records of who accessed the network, when they connected, from which device, and what resources they interacted with - critical information for audits and compliance checks.
Operational Policies, Monitoring, and Incident Response
Technical safeguards alone aren't enough to secure your wireless network. They need to be backed by well-documented policies, active monitoring, and a clear incident response plan. Together, these measures help your team understand expectations, detect threats early, and quickly contain any breaches before they spiral out of control.
Setting Wireless Network Policies and Procedures
Start with a comprehensive wireless security policy. This policy should define what’s allowed, which devices are approved, and the security configurations required for networks handling electronic protected health information (ePHI). Explicitly ban unauthorized access points, requiring all devices to be IT-approved and centrally managed. Specify standards for SSID use - such as avoiding default SSIDs - and ensure ePHI is never transmitted over open networks. Mandate WPA2 or WPA3-Enterprise encryption for clinical wireless networks.
Lay out clear access control rules for staff, clinicians, contractors, and vendors. If remote access is necessary, require secure methods like VPNs. For personal devices (BYOD), outline which devices are permitted, set minimum security requirements, and include conditions for remote wiping lost or unapproved devices. Clinical and IoT devices should operate on dedicated VLANs with restricted internet access, avoiding any direct connection to guest networks. For guest Wi‑Fi, make it clear - whether through terms of use or captive portals - that it’s isolated from production networks and cannot be used to access clinical records.
Standardize the configuration of all access points and controllers. Disable unnecessary services, enforce secure management protocols (like HTTPS/SSH), and restrict management access to designated admin networks. Document pre-deployment testing and use a formal change-management system to track updates. Keep configuration baselines stored centrally and conduct periodic checks to ensure devices stay aligned with approved settings.
Once these policies are in place, continuous monitoring will help reinforce your security measures.
Continuous Monitoring and Wireless Intrusion Detection
Effective monitoring starts with consolidating logs from access points, controllers, RADIUS systems, and firewalls into a centralized Security Information and Event Management (SIEM) system. Track key events such as connection attempts, authentication failures, configuration changes, rogue access point detections, and policy violations. Retain these logs for at least six years to meet HIPAA documentation requirements, and set up dashboards for routine reviews. Escalate any anomalies immediately.
Deploy a Wireless Intrusion Detection and Prevention System (WIDS/WIPS) to identify threats like rogue access points, evil twin networks, and deauthentication attacks. Choose a system that supports 802.11 threat signatures, integrates with your WLAN controllers and SIEM tools, and offers automated or semi-automated responses. Ensure sensors cover critical areas like patient rooms and nursing stations, while minimizing RF bleed into less secure spaces like parking lots. Define clear criteria for identifying rogue access points and validate alerts before taking action. Regularly tune the system - at least quarterly - to reduce false positives and avoid unnecessary disruptions.
Conduct regular RF surveys and rogue access point scans, ideally every month or quarter, and after significant network changes. Use both integrated WLAN tools and independent scanners for these checks. Perform vulnerability scans on your wireless infrastructure and schedule penetration tests annually or biennially to confirm the effectiveness of your network segmentation and other controls. Feed these findings into your risk management plans, overseen by your security governance team.
Wireless Incident Response and Remediation
Even with strong policies and monitoring, incidents can happen. That’s where a well-defined response plan comes into play. Develop a wireless incident response playbook that covers preparation, identification, containment, eradication, recovery, and lessons learned. For rogue or evil twin access points, the playbook should guide you through confirming the threat using WIDS alerts and on-site validation. Document key details like SSID, MAC address, location, and connected clients, then isolate affected segments or disable compromised SSIDs. If credentials are compromised, enforce password resets or revoke certificates, disable affected accounts, and check logs for signs of data breaches.
Every incident should trigger an evaluation of its impact on ePHI, including breach notification requirements. Use these findings to update your wireless policies, training materials, or technical configurations. Log incidents in your enterprise risk register, assigning risk scores based on their likelihood and potential impact on ePHI confidentiality, integrity, and availability. Map your wireless controls and responses to HIPAA Security Rule standards, addressing any gaps with updates to administrative, technical, or physical safeguards. Centralized platforms like Censinet RiskOps™ can streamline this process.
Finally, educate your team. Train clinicians and staff to avoid using guest or public Wi‑Fi for accessing electronic health records. Teach them to recognize suspicious SSIDs - such as fake hospital networks in public areas - and secure mobile devices with screen locks. Stress the importance of reporting lost devices immediately. IT and biomedical engineering teams should receive in-depth training on wireless policies, WIDS/WIPS operation, and incident response. Regular refresher courses and reminders will help maintain awareness and keep everyone prepared.
sbb-itb-535baee
Validating Compliance and Continuous Improvement
Maintaining a secure wireless network isn't a one-and-done task. It requires ongoing risk assessments, regular vulnerability testing, and updated policies to keep pace with changing HIPAA requirements. Treating compliance as a fixed goal can leave organizations vulnerable as new devices, attack techniques, and regulations arise. Instead, aim for a dynamic approach - one that combines technical evaluations, administrative reviews, focused training, and centralized tracking. This ensures your wireless environment stays aligned with HIPAA standards while complementing the safeguards discussed earlier.
Periodic Technical and Administrative Assessments
Regular evaluations are crucial for ensuring your network remains HIPAA-compliant. From a technical perspective, conduct quarterly vulnerability scans, annual penetration tests, and routine configuration reviews to verify encryption, segmentation, and authentication protocols. These checks help identify risks like unpatched systems, outdated encryption methods, or configuration drift. After significant changes to the network, schedule penetration tests to ensure defenses can withstand real-world threats, such as rogue access points or stolen credentials. Additionally, wireless spectrum scans should be performed periodically to detect unauthorized access points or devices extending coverage into unsecured areas.
On the administrative side, update your risk analysis annually to reflect changes in policies and controls. Review and revise procedures for wireless use, guest access, BYOD (Bring Your Own Device), access point deployment, and incident response to ensure they align with HIPAA requirements. Verify that agreements with vendors providing Wi‑Fi services, cloud controllers, or security tools explicitly address ePHI protection, breach notification, and audit rights. Document findings, assign risk levels, and track remediation efforts to completion.
Training and Awareness Programs
Even the best technical defenses can falter if your workforce isn’t educated on security best practices. Tailor training to specific roles: clinicians should learn to securely use devices, recognize risky networks, and differentiate between clinical and guest SSIDs. IT staff need advanced training on secure configurations, monitoring, and incident response, while administrators should understand oversight responsibilities and budget planning for security measures. Reinforce critical habits like using strong authentication, avoiding unencrypted public Wi‑Fi, not sharing credentials, and securing devices when unattended.
Incorporate scenarios addressing mobile and BYOD security, such as encrypting local storage, enabling remote wipe features, and following guidelines for connecting personal devices. Use tools like micro-learning modules, clear signage, and simulated threat exercises to keep awareness high. Track training participation and analyze incident trends to fine-tune your program and ensure it addresses evolving risks effectively.
Using Risk Management Platforms
Managing compliance manually can be a logistical nightmare. A centralized risk management platform can simplify the process, serving as a single source for compliance documentation, assessment schedules, remediation tasks, and vendor evaluations. These platforms streamline workflows, provide version-controlled document management, track issues with deadlines, and generate reports aligned with HIPAA’s Security Rule.
Healthcare-focused platforms like Censinet RiskOps™ go a step further by offering solutions tailored to the industry. They support risk assessments, cybersecurity benchmarking, and collaborative remediation for ePHI, clinical applications, medical devices, and supply chains. For example, Terry Grogan, CISO at Tower Health, shared how Censinet RiskOps enabled their team to conduct "a lot more risk assessments with only 2 FTEs required", freeing up resources for other priorities. Similarly, James Case, VP & CISO at Baptist Health, highlighted the benefits of moving away from spreadsheets:
Not only did we get rid of spreadsheets, but we have that larger community [of hospitals] to partner and work with.
Conclusion
Creating a HIPAA-compliant wireless network is not a one-and-done task - it’s an ongoing effort to safeguard patient data while supporting clinical operations. The process begins with a formal risk assessment to trace how ePHI flows through your Wi‑Fi network. From there, implement segmented networks with robust encryption like WPA2/WPA3 Enterprise, enforce role-based authentication and access controls, and establish continuous monitoring to detect rogue devices and unusual activity.
While technical measures such as encryption, segmentation, secure access point configurations, and thorough logging are essential, they must be paired with administrative safeguards. These include updated policies, vendor agreements that address ePHI security, and well-defined incident response plans. Don’t overlook the importance of physical protections either - secure your access points and controllers in locked, controlled spaces. Together, these layers address HIPAA’s Security Rule requirements for transmission security, integrity controls, and access management.
As your organization integrates more medical IoT devices, telehealth platforms, and cloud-based EHR systems, manual tracking becomes unmanageable. Platforms like Censinet RiskOps™ can simplify compliance by centralizing documentation and standardizing risk assessments. These tools help streamline remediation efforts and maintain enterprise-wide consistency.
Immediate action is critical. IT teams should inventory all wireless infrastructure, close gaps in encryption and segmentation, and establish baseline monitoring within 60–90 days. Compliance officers need to update the formal risk analysis to include Wi‑Fi and align wireless controls with HIPAA policies. Executives must ensure sufficient resources - both budget and staffing - are allocated for secure wireless operations, training, and the adoption of risk management platforms if internal capacity is limited.
A HIPAA-compliant wireless network is a cornerstone of secure, patient-focused care. By treating compliance as an ongoing program that integrates technical, administrative, and physical safeguards, your organization can confidently protect ePHI, support mobility, and stay ahead of evolving threats and technologies.
FAQs
How can I set up a HIPAA-compliant wireless network?
To establish a wireless network that complies with HIPAA regulations, start by enabling strong encryption protocols like WPA3. This ensures data transmissions remain secure. Set up access controls to restrict network access to authorized personnel only. It's also essential to keep your router's firmware up to date to patch security vulnerabilities and monitor network activity closely to detect any unauthorized access.
Perform regular risk assessments to uncover potential threats and maintain compliance standards. Securely manage all connected devices, ensuring they meet HIPAA requirements. Utilizing healthcare-focused cybersecurity tools can simplify these tasks and help protect sensitive patient data and Protected Health Information (PHI) from potential breaches.
What role does network segmentation play in achieving HIPAA compliance?
Network segmentation plays a key role in meeting HIPAA compliance standards. By breaking a network into smaller, isolated sections, it becomes easier to protect sensitive patient information. This setup limits unauthorized access, reduces the chances of data breaches, and helps contain security incidents to specific parts of the network.
When systems handling protected health information (PHI) are isolated, healthcare organizations can more effectively align with HIPAA's strict security and privacy rules. This strategy not only protects patient data but also bolsters the security of the entire network.
Why is continuous monitoring important for keeping wireless networks HIPAA-compliant?
Continuous monitoring plays a key role in keeping wireless networks aligned with HIPAA standards. It enables healthcare organizations to spot security threats, vulnerabilities, and unauthorized access as they happen. By catching potential risks early, they can act quickly to prevent breaches and protect sensitive patient information (PHI).
This kind of vigilance not only ensures compliance with HIPAA regulations but also helps protect essential systems and data. In turn, it reinforces trust and keeps organizations prepared in an ever-changing security environment.


