HIPAA vs. HITRUST: Cloud Certification Differences
Post Summary
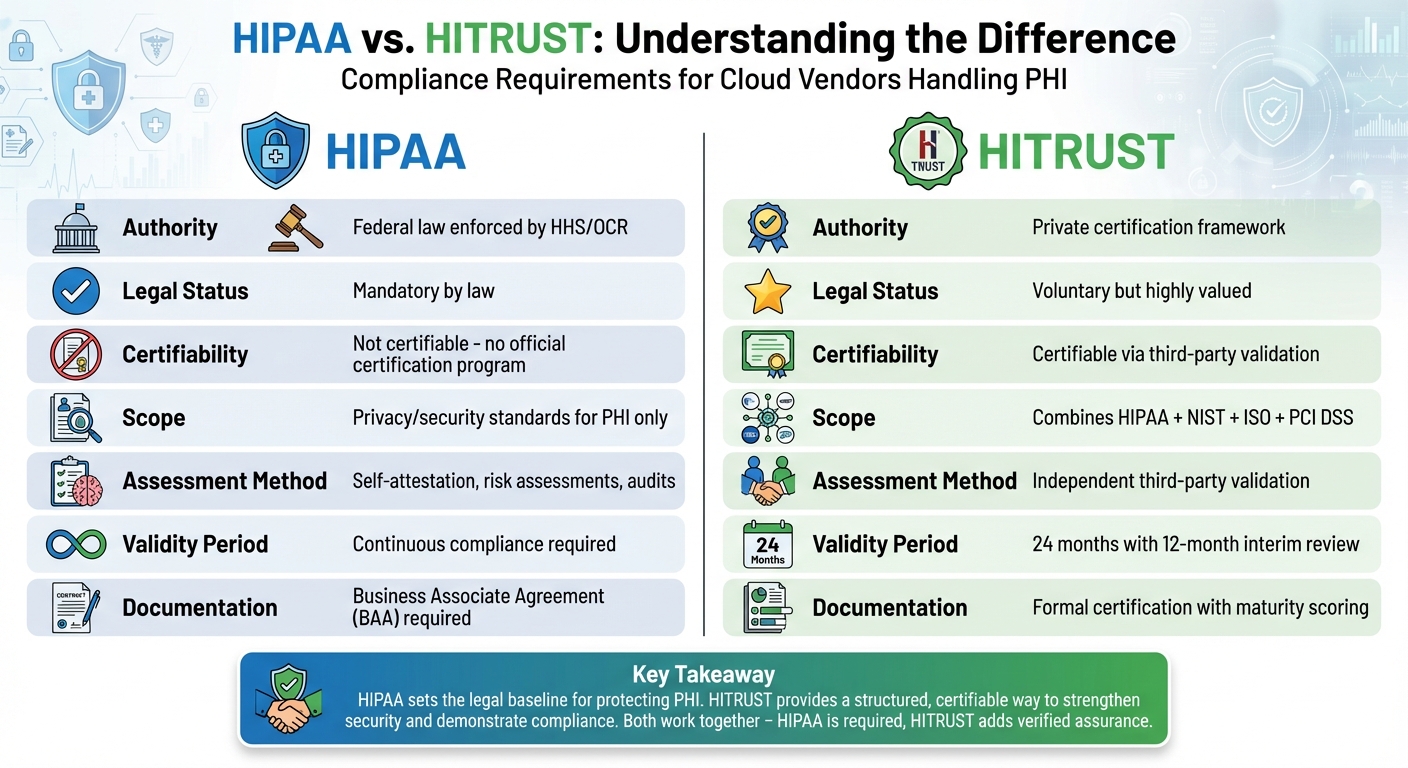
HIPAA and HITRUST are often mentioned when cloud vendors handle protected health information (PHI) in the U.S., but they serve different purposes. Here's the key distinction:
- HIPAA is a federal law that sets privacy and security standards for PHI. Compliance is mandatory but doesn't include an official certification process. It's risk-based, requiring organizations to implement safeguards they determine as "reasonable and appropriate."
- HITRUST is a private, certifiable framework that integrates HIPAA with other standards like NIST and ISO. It provides detailed guidance, independent validation, and certification, which is optional but highly valued by healthcare organizations.
Key Points:
- HIPAA compliance is required by law, while HITRUST certification is voluntary but offers added assurance.
- HIPAA lacks an official certification; organizations demonstrate compliance through audits, risk assessments, and agreements.
- HITRUST certification involves third-party assessments, a maturity model, and a two-year validity period with interim reviews.
- Healthcare providers increasingly prefer HITRUST-certified vendors due to its rigorous validation process.
Quick Comparison
| Aspect | HIPAA | HITRUST |
|---|---|---|
| Authority | Federal law (HHS/OCR) | Private certification framework |
| Certifiability | Not certifiable | Certifiable via third-party |
| Scope | Privacy/security for PHI | Combines HIPAA, NIST, ISO, etc. |
| Assessment Rigor | Self-attestation, audits | Independent validation |
| Validity Period | Continuous compliance | 24 months, with interim review |
Bottom Line: HIPAA sets the legal baseline for protecting PHI, while HITRUST provides a structured, certifiable way to strengthen security. Combining both ensures compliance and builds trust.
HIPAA vs HITRUST Compliance Framework Comparison Chart
HIPAA Requirements for Cloud Vendors
HIPAA's Core Rules for Cloud Services
When a cloud provider handles electronic Protected Health Information (ePHI), it automatically becomes a HIPAA business associate. This designation brings specific responsibilities under the Privacy, Security, and Breach Notification Rules. Here's a quick breakdown:
- The Privacy Rule sets strict limits on how Protected Health Information (PHI) can be used and shared. It ensures that cloud vendors respect patient rights and apply the "minimum necessary" standard when accessing data.
- The Security Rule focuses on safeguarding ePHI through administrative, physical, and technical measures. These safeguards aim to protect the confidentiality, integrity, and availability of sensitive data.
- The Breach Notification Rule requires cloud vendors to notify healthcare entities of any breach involving unsecured PHI as quickly as possible, and no later than 60 days after discovery. This allows healthcare organizations to inform affected individuals, the Department of Health and Human Services (HHS), and, in some cases, the media.
These requirements apply even if the cloud provider only stores encrypted ePHI without holding the decryption key. According to HHS guidance, such providers are still considered business associates and must sign a Business Associate Agreement (BAA) while adhering to HIPAA safeguards. These rules form the basis for the risk management practices cloud vendors must implement, which are further addressed in independent certification frameworks.
Why HIPAA Has No Certification
Unlike some regulatory frameworks, HIPAA doesn't offer an official certification program. The HHS Office for Civil Rights has made it clear that no third-party certification guarantees HIPAA compliance. Why? Because HIPAA is risk-based, not tied to specific technologies or configurations. Instead of prescribing exact solutions, it requires cloud vendors to:
- Continuously analyze risks to ePHI.
- Implement tailored risk management processes.
- Document "reasonable and appropriate" safeguards based on their unique risk assessments.
For example, a 2023 OCR enforcement summary highlighted common compliance failures, including lack of risk analysis, poor audit controls, and weak access management. These findings underline the importance of maintaining thorough documentation of security policies, risk assessments, and implemented safeguards. However, it's worth noting that no HHS-approved "stamp of compliance" exists.
How Cloud Vendors Show HIPAA Compliance
Since there's no formal certification, cloud vendors rely on contractual agreements and independent assessments to demonstrate their compliance. The cornerstone of this process is the Business Associate Agreement (BAA). Every healthcare client requires a signed BAA, which outlines:
- Permitted uses of PHI.
- Security responsibilities.
- Breach reporting timelines.
- Obligations for subcontractors.
Between 2009 and 2023, the HHS Breach Portal recorded 5,887 large breaches impacting over 523 million individuals. Many of these incidents stemmed from inadequate oversight of business associates or the absence of BAAs, highlighting the importance of these agreements.[1]
In addition to BAAs, cloud vendors must implement and demonstrate technical safeguards like:
- Encryption (both in transit and at rest).
- Access controls, including multi-factor authentication.
- Audit logs for tracking data access and changes.
- Backup and disaster recovery plans.
- Workforce training on HIPAA requirements.
- Incident response plans to handle potential breaches.
To bolster trust, many vendors undergo third-party assessments such as SOC 2 Type II or HITRUST certification. While these assessments provide useful evidence of security controls, they don't replace the need for HIPAA compliance.
Platforms like Censinet RiskOps™ help healthcare organizations streamline compliance efforts. These tools allow healthcare providers to maintain a centralized inventory of BAAs, security reports, and risk assessments. They also enable cloud vendors to efficiently respond to security questionnaires, share audit findings, and collaborate on risk mitigation strategies. This approach not only reduces the administrative burden but also ensures transparency in managing HIPAA compliance across applications, clinical systems, and supply chain services. However, it's important to remember that frameworks like HITRUST, while helpful, are complementary - not replacements for HIPAA's requirements.
HITRUST Certification for Cloud Vendors

How HITRUST Certification Works
The HITRUST CSF certification program simplifies compliance by combining multiple security standards - like HIPAA, NIST, ISO, and PCI DSS - into a single, unified framework. With 19 control categories, this structure helps cloud vendors streamline their efforts, eliminating the need to juggle different requirements for various healthcare clients.
Certification is tailored to the vendor’s size, regulatory needs, and risk level, with independent assessors evaluating controls for a certification period of two years. What sets HITRUST apart is its maturity model and scoring system. Instead of a straightforward pass/fail, the framework examines how well controls are implemented over time, pinpointing areas that need improvement. This approach allows vendors to demonstrate ongoing progress in security, rather than merely meeting baseline requirements. As a result, cloud vendors can continuously refine their security measures while maintaining compliance.
HITRUST's Application to Cloud Security
For cloud vendors, one standout feature of HITRUST is its control inheritance model. This allows vendors to inherit certain security controls from HITRUST-certified infrastructure providers. Essentially, if a vendor builds on a certified platform, they can leverage those foundational controls and focus on their unique requirements. This not only reduces duplication but also speeds up the certification process.
Another advantage is the ability to define a precise certification scope. Vendors can choose whether their certification applies to specific applications, data centers, or services. This flexibility is particularly helpful for cloud providers catering to multiple healthcare organizations. Each defined scope undergoes thorough validation to ensure robust protection of electronic protected health information (ePHI) across administrative, physical, and technical domains.
Benefits of HITRUST Certification
HITRUST certification offers several clear benefits. One of the most significant is the independent third-party validation it provides, which is widely trusted in audits and assessments. Studies indicate that HITRUST certification can reduce the burden of security questionnaires by 99% and speed up sales cycles, as healthcare buyers view it as a gold standard for assurance.
Cloud vendors also gain a competitive edge. Certification can lead to lower cyber insurance premiums and help differentiate them in the market due to the rigorous controls they implement. For smaller companies and startups, HITRUST offers programs designed to lower certification costs while still providing the credentials needed to compete in the healthcare space.
The framework’s focus on continuous improvement ensures vendors maintain a strong security posture. Through maturity assessments and ongoing evaluations, they can adapt and strengthen their defenses over time. Additionally, when cloud vendors require their subcontractors to be HITRUST-certified, it extends compliance across the entire supply chain. This gives healthcare organizations confidence that protected health information (PHI) is secure at every level of their technology stack.
HIPAA vs. HITRUST: Key Differences
Side-by-Side Comparison
Understanding the differences between HIPAA and HITRUST is crucial for cloud vendors and healthcare organizations looking to make informed compliance decisions. Here's a breakdown of how they compare:
| Aspect | HIPAA | HITRUST |
|---|---|---|
| Authority | Federal law enforced by HHS/OCR | Private certification framework |
| Scope | Sets minimum security and privacy requirements | Combines multiple standards (HIPAA, NIST, ISO, PCI DSS) into one framework |
| Certifiability | Not certifiable | Certifiable through third-party validation |
| Cloud-Specific Guidance | General requirements with limited technical details | Detailed controls tailored to cloud security needs |
| Assessment Rigor | Relies on client-led audits and self-attestation[1] | Requires independent third-party validation[1][3] |
| Validity Period | Continuous compliance required | Certification valid for 24 months, with a 12-month interim assessment[3] |
HIPAA focuses on self-attestation and agreements like BAAs, while HITRUST emphasizes independent third-party validation. These differences play a significant role in how healthcare organizations evaluate vendor security.
What This Means for Healthcare Organizations
These distinctions directly impact how healthcare organizations approach vendor assessments. With the rise in HIPAA-related breaches, the risks tied to self-attestation have become evident. HITRUST certification, on the other hand, reduces reliance on self-attestation by providing third-party validation.
For healthcare organizations, working with HITRUST-certified vendors simplifies vendor risk management. This certification can reduce the need for security questionnaires by up to 99% and speed up sales processes[1]. It also provides verifiable assurance that vendors have implemented robust controls, reducing the risk of breaches - especially when handling PHI in complex supply chains.
For cloud vendors, HITRUST certification is a strategic advantage. It not only enhances marketability but also lowers cybersecurity insurance premiums and minimizes breach risks through stringent controls[1]. As more healthcare organizations prioritize HITRUST certification, it’s becoming an essential factor for staying competitive.
Clearing Up Confusion
To integrate both frameworks effectively, healthcare organizations should view HIPAA as the legal foundation and HITRUST as a way to build and verify a stronger security posture. HIPAA sets the baseline requirements that all covered entities and business associates must meet. Meanwhile, HITRUST provides a structured and certifiable approach to demonstrating compliance with those requirements.
Think of HIPAA as the essential starting point, while HITRUST acts as the advanced layer that confirms an organization has implemented comprehensive, validated security measures. Even with HITRUST certification, vendors must still comply with HIPAA and establish BAAs. However, the certification offers healthcare organizations confidence that vendors adhere to independently verified controls. Together, these frameworks create a robust approach to safeguarding PHI in cloud environments.
sbb-itb-535baee
How to Evaluate Cloud Vendor Compliance
For Healthcare Organizations
When evaluating cloud vendors, start by categorizing vendors based on the level of risk they pose. Vendors that handle sensitive data like Protected Health Information (PHI), integrate with Electronic Health Records (EHRs), or are critical to patient care require more thorough scrutiny compared to those managing non-sensitive data. For these high-risk vendors, request essential security documents, such as penetration test summaries, vulnerability and incident reports, business continuity and disaster recovery plans, and audit logs.
Don’t rely solely on a vendor’s claim of HIPAA compliance. Instead, ask for documentation of their risk assessments, a signed business associate agreement (BAA), and proof of security measures like encryption and access controls for PHI. Since HIPAA compliance isn’t officially certifiable, it’s important to conduct regular reviews to ensure the vendor remains compliant over time.
If the vendor holds a HITRUST certification, verify its scope and expiration date. Ensure the certification applies to the specific services you plan to use and confirm it’s still valid. HITRUST certifications last for 24 months, with a required 12-month interim assessment, so make sure the vendor maintains their certification status.
Taking these steps helps healthcare organizations thoroughly evaluate vendor security before implementing broader cloud vendor practices.
"Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare." - Matt Christensen, Sr. Director GRC, Intermountain Health
For Cloud Vendors
If you’re a cloud vendor targeting healthcare clients, it’s crucial to simplify your compliance process. Consider pursuing HITRUST certification, especially if you handle high-risk PHI or want to stand out in a competitive market. HITRUST combines HIPAA with other standards like NIST, ISO, and PCI DSS, which can reduce sales scrutiny by up to 99% and even lower insurance premiums.
Before engaging a HITRUST assessor, conduct an internal readiness review. This involves documenting your policies, addressing gaps in controls (such as access management, encryption, vulnerability management, and incident response), and building a thorough evidence library with items like network diagrams, configurations, and test reports. Being prepared ensures you’re ready to address healthcare-specific concerns.
It’s also important to align with your clients’ expectations. Share your certification roadmap and timelines, publish a security and privacy overview, and provide regular updates on your progress. Keep in mind that while HITRUST certification is valuable, it doesn’t replace the mandatory requirements of HIPAA.
Using Censinet RiskOps™ for Compliance Management

Managing these evaluation steps can be complex, but advanced platforms make the process much more efficient. For example, Censinet RiskOps™ streamlines vendor risk assessments by automating evidence collection and benchmarking against HIPAA and HITRUST standards. This allows healthcare organizations to evaluate hundreds of vendors annually through automated workflows, saving time while maintaining high standards.
Terry Grogan, CISO of Tower Health, shared that adopting Censinet RiskOps reduced the number of staff needed for risk assessments from three to two, while increasing the number of assessments completed. Similarly, James Case, VP & CISO at Baptist Health, highlighted that the platform eliminated the need for spreadsheets and fostered collaboration within a broader network of hospitals.
For cloud vendors, Censinet Connect™ accelerates the sales process by allowing you to share completed security questionnaires and supporting evidence early on. The platform enables secure data sharing across a network of healthcare organizations and over 50,000 vendors, helping you demonstrate compliance and meet client expectations more effectively.
Conclusion
HIPAA sets the legal foundation for protecting PHI but doesn’t dictate specific methods for achieving that protection. On the other hand, HITRUST provides a certifiable framework that guides organizations on how to implement, test, and maintain those safeguards effectively.
HIPAA defines the rules; HITRUST offers a practical path to compliance. While all cloud vendors handling PHI must comply with HIPAA, HITRUST certification is becoming increasingly critical. Many major health systems and payers now include HITRUST certification as a requirement in vendor agreements, making it an industry standard - even though it’s technically voluntary[2][4].
Given these distinctions, healthcare organizations can’t simply rely on vendor assurances of HIPAA compliance. Since HIPAA doesn’t have an official certification program, you need structured ways to validate vendor security. This can include HITRUST certification, thorough risk assessments, or tools like Censinet RiskOps™, which centralize vendor evaluations and compare controls against both HIPAA and HITRUST standards. These measures help mitigate risk across your cloud supply chain and avoid costly penalties for HIPAA violations, which can climb into the millions[2].
For cloud vendors, meeting basic compliance isn’t enough. Aligning your security strategy with HITRUST’s maturity model shows healthcare clients that you’re committed to building and maintaining strong, verifiable protections for their sensitive data. This not only strengthens trust but also reduces potential sales barriers[2].
In short, combining HIPAA’s legal requirements with HITRUST’s operational controls creates a streamlined approach to managing risk. Use HIPAA as the legal framework and HITRUST as the practical guide - together, they support compliance and operational excellence in healthcare cloud environments.
FAQs
What’s the difference between HIPAA compliance and HITRUST certification for cloud vendors?
HIPAA compliance establishes the federal standards necessary to safeguard protected health information (PHI). It ensures that patient data is managed with both security and privacy in mind, serving as the foundational requirements for organizations handling sensitive healthcare information.
HITRUST certification takes things a step further. It offers a broad, risk-based framework that integrates HIPAA requirements with additional industry regulations and best practices. This certification enables cloud vendors and healthcare organizations to showcase a more advanced level of security and compliance, all within a structured and certifiable framework.
Why isn’t there an official certification for HIPAA compliance?
HIPAA doesn’t offer an official certification because it’s a framework of federal regulations, not a certifiable standard. Instead of earning a formal certification, compliance is measured by how effectively an organization implements the required safeguards and adheres to the rules.
Organizations must take charge of conducting risk assessments, addressing potential vulnerabilities, and maintaining compliance over time to safeguard sensitive health information. This adaptable approach allows HIPAA to be applied across various healthcare providers, entities, and vendors.
What are the benefits of HITRUST certification for cloud vendors in healthcare?
HITRUST certification is a game-changer for cloud vendors working in the healthcare industry. It offers a well-structured framework to manage security and compliance, ensuring vendors align with strict healthcare data protection standards.
Earning HITRUST certification allows cloud vendors to show their dedication to protecting sensitive patient information and adhering to regulations like HIPAA. This commitment not only strengthens trust with healthcare providers but also simplifies risk assessments and certification workflows, paving the way for smoother partnerships within the healthcare sector.


