How AES Protects PHI in Cloud Systems
Post Summary
AES (Advanced Encryption Standard) is a critical tool for safeguarding Protected Health Information (PHI) in cloud environments. It converts sensitive data into an unreadable format, ensuring only authorized individuals with the correct key can access it. This encryption method is particularly important for healthcare organizations, as PHI is a prime target for cyberattacks like identity theft and ransomware. Here’s what you need to know:
- Why AES Matters: AES-256 encryption is the industry standard for protecting PHI in the U.S., offering robust security for data at rest and in transit. It also supports compliance with HIPAA and HITECH regulations, often qualifying encrypted data for "safe harbor" in breach incidents.
- Key Features: AES uses symmetric encryption, meaning the same key encrypts and decrypts data. Modes like AES-GCM provide both confidentiality and integrity, making them ideal for cloud-based PHI.
- Implementation: Effective encryption strategies include layered defenses, combining provider-managed encryption for storage with application-level encryption for sensitive fields. TLS with AES-GCM secures data in transit, while tools like Key Management Services (KMS) ensure proper key handling.
- Compliance Benefits: Proper AES encryption can reduce breach notification requirements under U.S. law, potentially saving millions in penalties and damages.
This guide explores how AES works, its role in healthcare compliance, and best practices for securing PHI in the cloud.
AES Basics for Cloud PHI Security
How AES Works: Key Sizes and Modes
AES is a symmetric encryption algorithm, meaning the same key is used for both encrypting and decrypting data. It supports three key sizes: 128-bit, 192-bit, and 256-bit. For U.S. healthcare organizations, AES-256 has become the standard for securing Protected Health Information (PHI) in cloud environments. For example, Google Cloud encrypts all customer data at rest using AES-256 by default, covering persistent disks, Cloud Storage, and internal backups.[2] The larger key size offers stronger security, and modern cloud systems are built to handle AES-256 efficiently, making it the go-to choice for PHI protection.
Another critical aspect of AES is the mode of operation, which defines how the algorithm processes data. AES-GCM (Galois/Counter Mode) is widely recommended for cloud-based PHI because it combines confidentiality and authentication into a single process - this is known as authenticated encryption with associated data (AEAD). AES-GCM is fast, supports parallel processing, and works well for encrypting databases, object storage, and data transmitted over TLS. For smaller, constrained environments, like certain IoT or medical devices, AES-CCM, another AEAD mode approved by NIST, is often used.[NIST SP 800-38C] Meanwhile, CBC (Cipher Block Chaining) mode, which requires an additional HMAC for authentication, is gradually being replaced by GCM due to its limitations. These choices in key size and mode are essential for meeting the rigorous security requirements in U.S. healthcare.
AES and U.S. Healthcare Standards
AES was officially adopted by the U.S. government through NIST FIPS 197 and is further supported by the NIST SP 800-series guidelines, which outline best practices for implementation. These guidelines are especially relevant for healthcare organizations aiming to comply with HIPAA's technical safeguards. While HIPAA treats encryption as an "addressable" requirement, using NIST-approved algorithms like AES is key to meeting the breach notification safe harbor under the HITECH Act. According to HIPAA Journal, if PHI is encrypted following NIST standards with strong algorithms and proper key management, a lost or stolen device generally does not require a breach report, as the data is considered unreadable.[3] This makes AES not just a security measure but also a critical tool for compliance and reducing liability for healthcare providers.
What AES Does and Doesn't Do
AES ensures confidentiality, making PHI unreadable to anyone without the correct decryption key. When used in authenticated modes like GCM, it also guarantees integrity and authenticity, ensuring that data hasn't been altered or tampered with. However, there are limits to what AES can achieve. It does not handle tasks like access control, audit logging, identity management, or network segmentation. For instance, AES won’t prevent an authorized user from misusing PHI, stop a misconfigured cloud storage bucket from being exposed, or detect unusual access patterns.
While AES is a critical layer for protecting PHI, it must be part of a broader security strategy. Complementary controls like access management, logging, and real-time monitoring are essential to build a comprehensive defense. Think of AES as the backbone of data protection - it’s vital, but it can’t do the job alone.
Designing AES Encryption for Cloud PHI
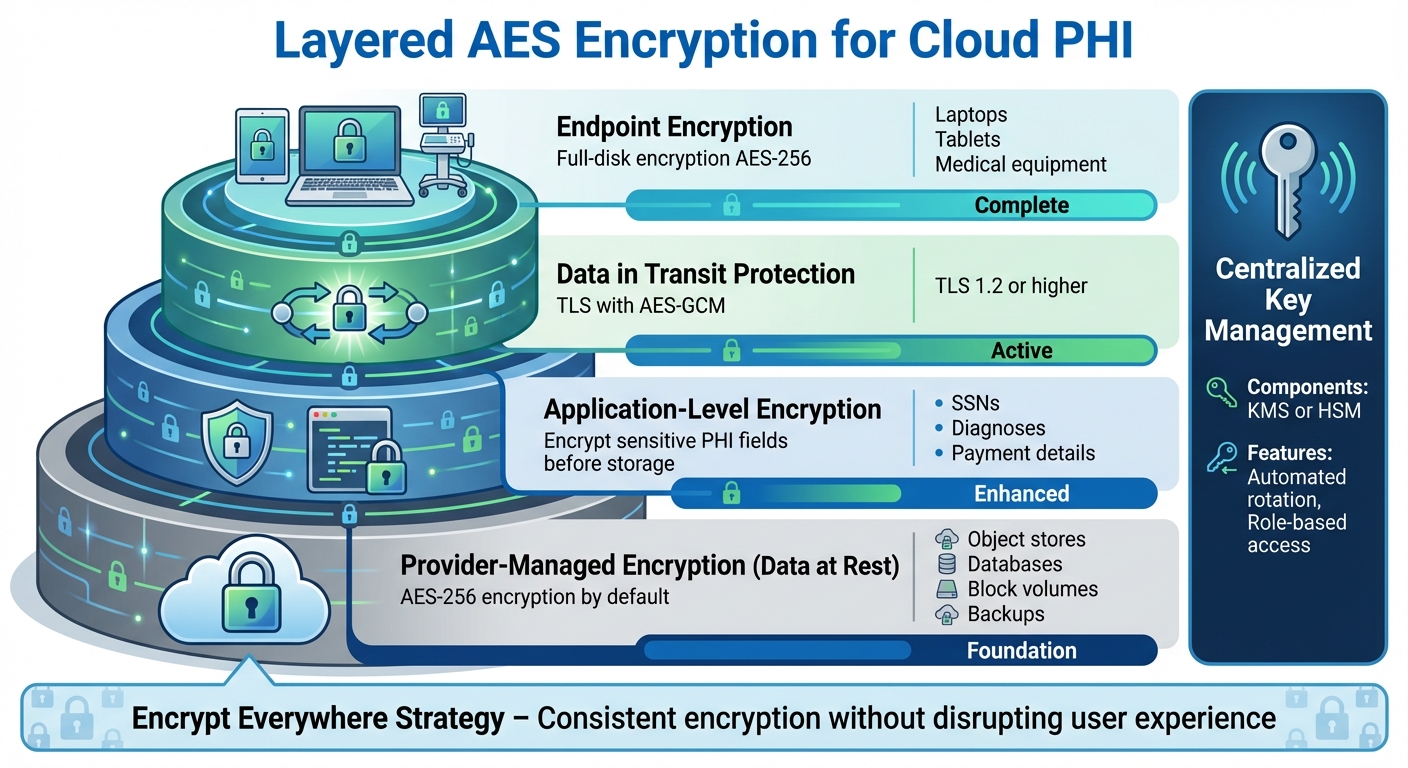
Layered AES Encryption Strategy for Cloud-Based PHI Protection
Layered Encryption for Cloud PHI
When it comes to protecting PHI (Protected Health Information) in the cloud, a well-thought-out design involves using AES encryption at multiple levels instead of relying on just one layer of defense. The first step is to implement provider-managed encryption for data at rest across all storage types - whether it's object stores, databases, block volumes, or backups. Most cloud providers offer built-in encryption, such as AES‑256, as a default for data at rest, which serves as a strong foundation [2].
On top of this, you can add application-level encryption for particularly sensitive PHI fields, like Social Security numbers, medical diagnoses, or payment details. This ensures that even if a database is compromised, the most critical data remains protected.
It’s equally important to secure endpoints and data in transit. Use TLS with AES‑GCM to encrypt data moving between services, and ensure that devices like laptops, tablets, or medical equipment storing PHI locally are equipped with full-disk encryption using AES‑256. AccountableHQ’s HIPAA cloud architecture guidance emphasizes an "encrypt everywhere" strategy, ensuring encryption is applied consistently without disrupting user experience [6]. This layered approach creates a strong foundation for evaluating encryption strategies at both the provider and application levels.
Provider‑Managed vs. Application‑Level Encryption
Deciding between provider-managed and application-level AES encryption comes down to your specific risks and operational requirements. Provider-managed encryption is typically easier to implement and faster to set up. The cloud provider handles encryption and key rotation, offering protection against external breaches, lost devices, and certain configuration errors. However, it’s worth noting that cloud administrators might still have access to plaintext data in some situations.
On the other hand, application-level encryption gives you more control. Sensitive PHI fields are encrypted at the application level before they even reach the database, meaning the cloud provider never has access to the encryption keys. This approach is particularly effective against insider threats and aligns with "zero knowledge" architecture requirements. That said, it does come with added complexity. You’ll need to integrate encryption logic directly into your application code, carefully manage keys (often via an external Key Management Service or Hardware Security Module), and deal with limitations like the inability to index or search encrypted fields easily.
For most healthcare organizations, a hybrid approach works best. Start with provider-managed encryption as your baseline, then add application-level encryption for the most sensitive data. Beyond the technical setup, compliance with regulations plays a significant role in shaping your encryption strategy.
U.S.-Specific Considerations for PHI Encryption
When designing AES encryption for U.S. healthcare, it’s crucial to align with the HIPAA Security Rule and HITECH breach notification requirements. These regulations mandate that encryption practices meet specific standards to minimize breach liabilities [3]. For example, if PHI is encrypted using NIST-approved algorithms like AES‑256 and the encryption keys remain secure, losing a device typically doesn’t trigger a breach under HITECH. This can save organizations from costly breach notifications and liability.
Encryption design must also account for U.S. requirements around backup retention and disaster recovery. Backups should be encrypted and stored within U.S. jurisdictions to comply with business associate agreements and state laws. Additionally, documenting encryption measures thoroughly is essential for audits and risk assessments. Tools like Censinet RiskOps™ can help ensure that your AES-based encryption controls are correctly configured across both vendor platforms and internal systems. These steps not only support compliance but also strengthen your overall encryption and key management practices, which are critical for protecting PHI in the cloud.
Implementing AES Encryption for PHI
Classifying PHI Data Flows
Start by mapping out where PHI (Protected Health Information) is located and how it moves through your cloud environment. This includes every stage - creation, use, storage, sharing, archival, and destruction. Be thorough in documenting which applications interact with PHI, whether they create, store, transmit, or share it.
Why is this important? Because over 90% of large healthcare data breaches involve unencrypted electronic PHI (ePHI) [3]. To minimize risks, clearly distinguish sensitive PHI fields, like Social Security numbers or medical diagnoses, from non-PHI data. For each PHI data flow, identify whether the data is at rest, in transit, or in use, and note the cloud services involved - such as databases, object storage, or message queues. Once you’ve created this map, apply AES encryption to secure PHI at every point where it’s stored or transmitted.
Enabling AES for Data at Rest
After classifying your PHI, ensure all storage layers are encrypted with server-side AES‑256 encryption. This includes relational databases (like RDS or Cloud SQL), object storage (such as S3 or Azure Blob), block storage volumes attached to virtual machines, and all backup snapshots. Most cloud platforms make this straightforward with toggles or policy settings to enforce encryption.
For especially sensitive PHI - like Social Security numbers or payment details - go a step further. Use application-level AES encryption in addition to provider-managed encryption. This involves encrypting specific database columns or JSON fields before storing them, using encryption keys you manage through a Key Management Service (KMS) or a Hardware Security Module (HSM).
Why take these extra steps? Strong encryption can reduce breach-notification obligations under HIPAA [3] [4]. If encrypted PHI is lost or stolen, it may not count as a reportable breach. Considering the average cost of a healthcare data breach in the U.S. exceeds $10 million per incident [3], investing in these encryption measures can save significant costs in the long run. Once your data at rest is secure, turn your attention to safeguarding data in motion.
Securing Data in Transit with AES
When PHI is in transit, enforce encryption by using TLS with AES-based cipher suites. Configure your web servers, APIs, and load balancers to require TLS 1.2 or higher, and use strong cipher suites like TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384. Completely disable outdated protocols like SSL and older versions of TLS (1.0/1.1) to align with NIST recommendations and HIPAA requirements.
For service-to-service communication or partner integrations involving PHI, implement mutual TLS (mTLS) [6]. This ensures both endpoints are authenticated while encrypting the connection with AES. Make sure your load balancers and API gateways enforce HTTPS, and regularly validate your TLS configuration with tools like SSL Labs or cloud-native security scanners. Additionally, log all access to encrypted PHI and track key-management activities to support compliance audits and continuous monitoring.
sbb-itb-535baee
Key Management and Compliance Validation
Managing encryption keys properly is just as important as encryption itself when it comes to protecting PHI in cloud environments.
Best Practices for Key Management
Never store AES keys in code, configuration files, or databases. Instead, rely on a cloud-based Key Management Service (KMS) or a Hardware Security Module (HSM) to handle key generation, storage, and access control. Major cloud providers offer KMS solutions backed by HSMs that adhere to HIPAA standards. These services centralize key management, integrate with identity and access management systems, and automate key rotation processes [2][6].
For most healthcare applications, a cloud KMS with HSM support is sufficient. However, for high-risk systems like core EHR databases or multi-tenant PHI platforms, dedicated HSMs are recommended [2][6]. Implement envelope encryption, where a master key encrypts individual dataset, volume, or tenant-specific keys. This approach allows for easy key rotation or revocation without needing to re-encrypt all stored data [6].
Separate key management responsibilities from system administration. For example, database administrators with access to data stores shouldn't automatically have the ability to decrypt encryption keys. Enforce strict KMS key usage policies by assigning specific roles for decryption and automating key rotation at regular intervals. Additionally, maintain a clear, documented process for key revocation and data re-encryption in the event of a security breach [6].
Documenting and Validating AES Encryption
HIPAA regulations treat encryption and key management as interconnected technical safeguards [3][4]. For every PHI system, document your encryption methods, key management policies, risk assessments, and periodic reviews. This includes specifying whether data at rest is encrypted and detailing how keys are created, stored, rotated, and destroyed [3][4].
Perform regular technical and administrative evaluations of your encryption and key management practices, as mandated by HIPAA §164.308(a)(8). Keep records of these evaluations for auditors [3][4]. Log all key-related activities - such as generation, rotation, access, and deletion - and feed these logs into your SIEM system for real-time monitoring. Proper encryption following NIST standards can exempt organizations from breach notification requirements if encrypted data is lost or stolen [3][4]. This makes thorough key management a critical component of compliance and risk reduction.
Using Censinet RiskOps™ for Risk Management

Censinet RiskOps™ simplifies the process of assessing and validating your AES encryption and key management strategies. The platform allows healthcare organizations to compare their encryption practices with industry benchmarks and identify vulnerabilities in their PHI protection [1]. Terry Grogan, CISO at Tower Health, shared that Censinet RiskOps enabled them to conduct "a lot more risk assessments" with just two full-time employees, freeing up three others for different tasks [1].
"Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters." - Brian Sterud, CIO, Faith Regional Health [1]
With Censinet RiskOps™, you can centralize documentation of encryption settings, key management policies, and audit results. The platform connects you to a network of over 50,000 vendors, simplifying the process of addressing encryption gaps in your supply chain. By continuously monitoring risks tied to patient data and medical records, Censinet RiskOps™ helps demonstrate HIPAA compliance during OCR reviews, payer audits, and business associate evaluations.
Conclusion
AES encryption plays a key role in safeguarding PHI within cloud-based healthcare systems. When implemented correctly, it reduces the likelihood of breach notifications, cutting down on regulatory challenges and financial risks [3][5]. To ensure comprehensive protection, use both storage-level and field-specific encryption.
A layered encryption strategy requires strong key management practices. Keys should be stored in HSM-backed KMS solutions, with access separated from data administration. Automate key rotation, enforce role-based access controls, and conduct regular audits to verify encryption protocols and key management processes.
Every flow of PHI - whether in backups, logs, archives, or medical devices - must be carefully mapped and secured. Identify where AES encryption is in use, where it’s missing, and where stronger modes like AES-GCM are necessary. Conduct risk assessments focused on PHI and document all encryption methods, key policies, rotation schedules, and reviews to meet HIPAA compliance standards. This continuous focus on encryption best practices and risk evaluation forms the backbone of a strong cybersecurity strategy in healthcare.
Platforms like Censinet RiskOps™ can simplify scaling these practices. They centralize documentation, benchmark encryption strategies against industry standards, and connect healthcare organizations with a network of over 50,000 vendors. This ensures your AES encryption approach evolves alongside new threats and regulatory changes [1]. As Matt Christensen, Sr. Director GRC at Intermountain Health, explains:
"Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare" [1].
Balancing security, efficiency, and cost is crucial. Leading cloud providers like Google Cloud already encrypt all data at rest with AES-256 by default, making advanced encryption available without added complexity [2]. Ultimately, the focus should remain on protecting patient data, meeting compliance requirements, and developing a cybersecurity program capable of growing with your organization.
FAQs
What makes AES encryption eligible for HIPAA safe harbor during a data breach?
When it comes to meeting HIPAA's safe harbor requirements, AES encryption stands out - especially when using AES-256, a widely trusted standard. This encryption ensures that protected health information (PHI) becomes unreadable and unusable without the proper decryption key, offering a strong layer of security. However, for AES encryption to fully comply with HIPAA, it must follow NIST guidelines, which include critical practices like proper key management.
By sticking to these standards, healthcare organizations can show they’ve taken the necessary steps to protect PHI, even if a breach occurs. This approach not only helps safeguard sensitive patient information but also reduces the risk of facing penalties for non-compliance.
What’s the difference between provider-managed AES encryption and application-level AES encryption?
When a cloud provider manages AES encryption, it operates at the storage or hardware level. This setup offers extensive data protection but limits user control over encryption keys and the overall encryption process.
On the other hand, application-level AES encryption is handled directly within the application. This method puts users in charge of managing encryption keys and tailoring security measures. It’s particularly useful for safeguarding sensitive data, such as Protected Health Information (PHI), as it allows for more targeted control and customization.
Why is AES-GCM commonly used to secure PHI in cloud-based healthcare systems?
AES-GCM is a popular choice for securing Protected Health Information (PHI) in cloud systems. It pairs powerful encryption with built-in data integrity checks, ensuring sensitive information stays confidential while confirming it hasn’t been modified during transmission or storage.
This encryption method is both fast and reliable, making it ideal for cloud environments where performance and security are top priorities. By offering authenticated encryption, AES-GCM helps healthcare organizations safeguard patient data and comply with regulatory standards in today’s digital age.


