Integrating ISO 27001 Risk Management with Operations
Post Summary
ISO 27001 offers a structured way to manage risks in healthcare, ensuring patient safety and uninterrupted clinical workflows. In the U.S., healthcare breaches exposed over 133 million records in 2023, highlighting the need for better risk management. By embedding ISO 27001 into daily operations, healthcare organizations can address threats like ransomware, medical device vulnerabilities, and vendor risks while staying compliant with HIPAA and other regulations.
Key Points:
- ISO 27001 Framework: Focuses on continuous risk management through an Information Security Management System (ISMS).
- Sector-Specific Risks: Includes patient data breaches, EHR outages, and compromised medical devices.
- Core Clauses: Risk assessment (Clause 6), organizational context (Clause 4), and actionable controls (Annex A).
- Integration: Risk assessments should align with clinical workflows, vendor processes, and new technology implementations.
- Automation Tools: Platforms like Censinet RiskOps™ streamline vendor assessments and monitoring.
By shifting from reactive to proactive risk management, healthcare providers can enhance security, minimize disruptions, and ensure patient care remains the top priority.
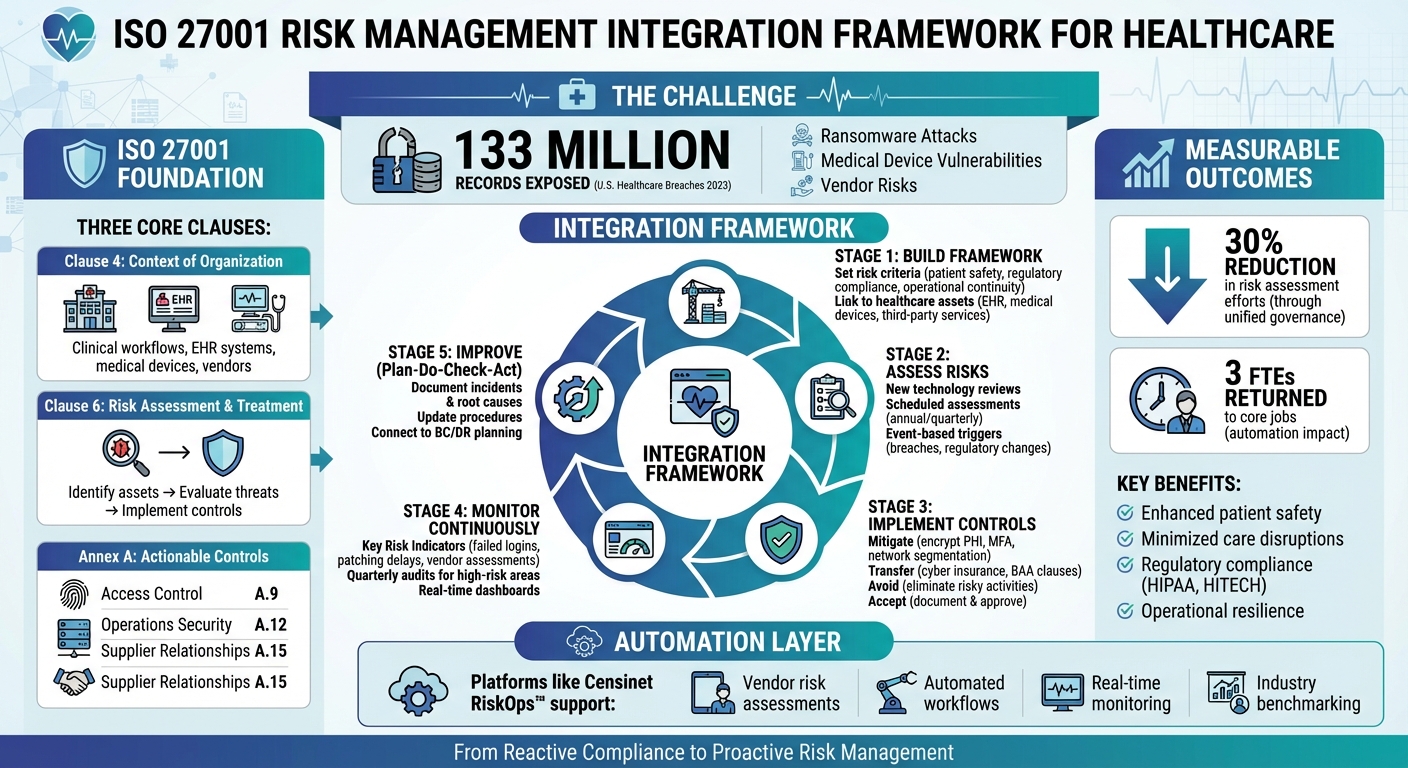
ISO 27001 Risk Management Integration Framework for Healthcare Operations
ISO 27001 Risk Management Fundamentals for Healthcare
ISO 27001 provides a structured framework to weave security practices into the daily operations of healthcare organizations, addressing their unique challenges.
At its core, ISO 27001 introduces an Information Security Management System (ISMS), emphasizing that security is not a one-time task but an ongoing process. For U.S. healthcare providers, this means continuously managing risks to patient data, clinical systems, and overall operations. Its risk-based approach aligns seamlessly with healthcare's focus on patient safety - both require identifying threats, implementing safeguards, and monitoring results.
ISO 27001 Clauses and Controls for Healthcare Organizations
Clause 4 (Context of the Organization) emphasizes understanding the specific environment in which a healthcare provider operates. This includes clinical workflows, connected medical devices, electronic health record (EHR) systems, and third-party vendors. To effectively address these areas, input from clinical leaders, compliance officers, and operational staff is essential - they know the ins and outs of patient care processes.
Clause 6 (Risk Assessment and Treatment) forms the backbone of the risk management process. Healthcare organizations must identify critical assets like patient records, imaging systems, and lab interfaces; evaluate threats such as ransomware attacks, insider misuse, or vendor vulnerabilities; and determine appropriate responses - whether implementing controls, accepting risks, or transferring them. This clause mandates thorough documentation of risk criteria, ownership, and treatment plans, ensuring both clinical and business leaders are actively involved in decision-making[2][4].
Annex A controls provide actionable safeguards tailored to healthcare needs. For example:
- Access control (A.9) ensures only authorized individuals - like clinicians, nurses, and administrative staff - can view or modify patient records.
- Operations security (A.12) covers critical areas like change management for clinical systems, malware protection on workstations, and reliable backup processes for essential systems.
- Supplier relationships (A.15) focuses on managing risks tied to third-party vendors, particularly when they handle protected health information (PHI) or maintain medical devices.
Risk Factors Specific to Healthcare Environments
Healthcare organizations face distinct risks, amplified by regulatory and operational pressures.
HIPAA and HITECH enforcement can result in steep civil monetary penalties and mandatory corrective action plans for privacy or security breaches[3][4]. Adding to this complexity, state breach notification laws often require faster reporting and more detailed disclosures than HIPAA mandates[3][4].
The stakes are even higher when it comes to care disruption risks. For instance, an EHR system outage can force clinicians to revert to paper workflows, delaying critical decisions and increasing the likelihood of medication errors. Similarly, a hacked medical device - like an infusion pump or imaging machine - can directly endanger patient outcomes. ISO 27001 risk criteria must account for these scenarios, with minimal tolerance for risks that jeopardize patient safety or lead to willful HIPAA violations[2][3][4]. Healthcare organizations should clearly define their risk appetite in areas like patient harm, regulatory breaches, system downtime, and data loss.
By addressing these sector-specific challenges, healthcare providers can move beyond compliance checklists to adopt a proactive, continuous approach to risk management.
Moving from Compliance Projects to Continuous Risk Management
A common pitfall for healthcare organizations is treating ISO 27001 as a one-time certification exercise. For example, risk assessments are often conducted only when launching a new telehealth platform or when a vendor relationship changes.
However, organizations that integrate ISO 27001 with broader risk frameworks - such as ISO 31000 - report tangible benefits. One such case demonstrated a 30% reduction in risk assessment efforts by unifying governance, risk taxonomy, and control management across the organization[2]. Achieving this shift requires strong leadership, not just from the Chief Information Security Officer (CISO), but also from clinical executives and board members. Their commitment ensures that risk management becomes a core element of operational resilience and patient safety, influencing every decision across the organization.
Building a Risk Framework for Healthcare Operations
Creating an ISO 27001-compliant risk framework tailored for healthcare goes far beyond using generic IT security templates. Healthcare's unique landscape - ranging from protecting patient data and securing medical devices to safeguarding research systems and supply chains - requires a customized approach. This framework must address the intricacies of clinical workflows, regulatory compliance, and patient safety, laying a foundation for seamlessly integrating risk assessments into daily healthcare operations.
Setting Risk Criteria for Healthcare Organizations
When defining risk criteria, focus on the core areas of patient safety, regulatory compliance, and operational continuity. Patient safety is paramount - any risk that could impact clinical decisions or care delivery must be addressed immediately. Regulatory compliance includes exposure to HIPAA violations, which can lead to financial penalties and mandatory corrective actions. Operational downtime also needs clear quantification, differentiating between minor disruptions and prolonged outages that could jeopardize critical services.
Likelihood criteria should be tailored to the specific threats healthcare organizations face. For example, consider the prevalence of ransomware attacks on healthcare systems, data breaches involving third-party vendors, and vulnerabilities in outdated medical devices. Use these patterns to calibrate the likelihood of potential risks, ensuring they align with the realities of healthcare operations.
Finally, connect these criteria directly to the organization’s assets and workflows for a targeted risk management approach.
Connecting Risks to Healthcare Assets and Processes
To effectively manage risks, link them to essential healthcare assets such as electronic health record (EHR) systems, medical devices, and third-party services. For EHR systems, assess access controls, backup reliability, and integration points. Medical devices require evaluations of their network exposure, patch management, and the clinical consequences of potential compromise. Third-party services - whether handling protected health information (PHI), billing data, or clinical applications - should be scrutinized for data protection measures, business continuity plans, and contractual safeguards.
Beyond technology, it’s critical to assess core business functions like patient registration, clinical documentation, medication administration, laboratory results delivery, and billing. Identify their dependencies on information systems, potential failure points, and recovery priorities. This detailed mapping strengthens the ongoing risk management process, ensuring it stays aligned with operational priorities.
To further embed these frameworks into daily operations, specialized platforms can play a pivotal role.
Using Platforms to Deploy Risk Frameworks
Specialized platforms simplify risk assessments and automate workflows, fostering collaboration across departments and vendor networks. For instance, Censinet RiskOps™ offers a comprehensive solution for healthcare risk management, addressing vendors, patient data, medical records, research, medical devices, and supply chains - all within a single platform [1].
Terry Grogan, CISO at Tower Health, highlighted the efficiency gained through such tools:
"Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required." [1]
These platforms also facilitate benchmarking against industry standards, enabling healthcare leaders to set appropriate risk criteria and secure necessary resources. Brian Sterud, CIO at Faith Regional Health, shared:
"Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters." [1]
Integrating Risk Assessment into Daily Operations
Incorporating ISO 27001 risk assessments into the daily routines of healthcare organizations shifts risk management from a once-a-year task to an ongoing safeguard. By embedding these assessments into everyday workflows, healthcare providers can proactively identify and mitigate risks before they disrupt patient care or operations. Instead of handling risk assessments as standalone projects, they should be seamlessly integrated into processes like technology rollouts, clinical workflows, and vendor management. This approach ties strategic planning directly to operational execution, ensuring a more robust and dynamic risk management system.
Risk Assessments for New Technology and Changes
Every new technology or system update brings potential risks that need to be addressed before implementation. To stay ahead, healthcare organizations should make risk reviews a mandatory step during IT change approvals and capital purchases. For example, when adopting cloud-based EHR modules or clinical SaaS tools, it’s crucial to evaluate factors like data flows, access controls, integration with current systems, and backup mechanisms. Similarly, deploying medical devices requires scrutiny of network vulnerabilities, patching capabilities, and the potential clinical impact if a device is compromised.
These pre-implementation assessments should involve key stakeholders across departments. By documenting risk treatments and collaborating with decision-makers early on, organizations can avoid expensive fixes and protect patient safety from the outset.
Scheduled and Event-Based Risk Assessments
To maintain a proactive stance, healthcare organizations should combine regular, scheduled risk reviews with event-triggered assessments. For high-risk systems, periodic reviews not only support ISO 27001 and HIPAA Security Risk Analysis compliance but also keep teams prepared for emerging threats. For instance, critical systems like EHR platforms, patient portals, and laboratory information systems should undergo annual assessments, while systems handling highly sensitive or life-critical data may require quarterly reviews.
Event-based assessments, on the other hand, respond to specific triggers, such as security breaches, regulatory updates, or significant vendor changes. For example, if a ransomware attack hits the industry or a vendor is involved in a data breach or merger, it’s essential to reassess your organization’s exposure. This ensures that the risk management strategy evolves alongside external conditions.
Adding Risk Management to Clinical and Vendor Processes
Risk management can be woven into clinical workflows without disrupting patient care. For example, clinical staff should be trained to report deviations like shared logins, informal texting of PHI, or bypassing authentication processes. These reported issues can reveal risks that traditional assessments might overlook, feeding valuable insights into the ISO 27001 framework.
Vendor processes also need a risk-focused approach. Risk management should be part of onboarding, negotiating business associate agreements (BAAs), and periodic reviews. Tools like Censinet RiskOps™ streamline this process by enabling early vendor risk disclosures and automating workflows [1].
Automation tools replace manual methods like spreadsheets and email-based questionnaires with efficient digital workflows. These systems can tailor question sets based on the vendor or system type, pre-fill known data, and route findings to relevant stakeholders - whether in security, compliance, or clinical roles. This automation not only scales risk management efforts but also ensures healthcare organizations can meet growing demands without overburdening staff. By embedding risk management into daily operations, healthcare providers enhance their resilience and align closely with established risk frameworks.
sbb-itb-535baee
Implementing Risk Treatment, Controls, and Monitoring
To effectively integrate ISO 27001 into clinical workflows, organizations must focus on risk treatment, implementing controls, and ongoing monitoring. Once risks are identified, these insights need to translate into safeguards that protect patient care while meeting ISO 27001 requirements. This involves selecting the right treatment strategies, embedding controls into daily operations, and defining performance metrics to ensure continuous improvement.
Selecting Risk Treatment Approaches
ISO 27001 provides four main approaches to handling risks:
- Mitigate: Reduce risk by implementing controls.
- Transfer: Shift risk to a third party.
- Avoid: Eliminate the activity causing the risk.
- Accept: Acknowledge the risk when treatment costs outweigh the potential impact.
When deciding on these strategies, healthcare organizations must weigh regulatory requirements, patient safety, and operational priorities. For high-severity risks, mitigation is often the best choice. Examples include encrypting protected health information (PHI) during storage and transmission, implementing multi-factor authentication for electronic health records (EHRs), and using network segmentation to isolate devices.
Transferring risk, on the other hand, might involve purchasing cyber insurance or including indemnification clauses in agreements with business associates. However, these measures do not absolve the organization of its ultimate responsibility for compliance.
Risk acceptance requires thorough documentation and executive approval. For instance, a rural hospital might choose to continue using an outdated radiology system due to prohibitive replacement costs. In such cases, compensating controls like network isolation and enhanced monitoring can minimize exposure. These decisions should be revisited periodically or when circumstances change to ensure they remain appropriate and do not create hidden vulnerabilities.
Once treatment strategies are defined, the next step is to integrate ISO 27001 controls into everyday operations.
Applying ISO 27001 Controls in Healthcare Operations
ISO 27001 Annex A provides a detailed list of controls that should become part of routine healthcare workflows, rather than standalone initiatives. For example, access management controls should align with HR processes. If a nurse changes roles, their permissions should update automatically. Similarly, when a physician leaves, all credentials must be promptly revoked to prevent insider threats.
Change management is another critical area. Before updating EHR systems or adding new applications, risk assessments should evaluate potential impacts on data integrity, availability, and patient safety. Coordinating system downtimes with clinical teams and testing rollback procedures can help prevent disruptions during critical care.
Vendor management controls are equally important, given the extensive use of third-party services in healthcare. Before onboarding a vendor that handles PHI, organizations should evaluate the vendor’s security practices, negotiate business associate agreements, and define clear incident response requirements. Specialized tools can streamline these processes by automating control implementation and sharing vendor risk data.
"Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare." - Matt Christensen, Sr. Director GRC, Intermountain Health [1]
To prioritize effectively, organizations should first address controls that directly impact patient safety and compliance, such as EHR access restrictions and PHI encryption. Lower-priority systems can follow in subsequent phases. This staggered approach prevents staff from becoming overwhelmed and allows processes to be fine-tuned based on early results.
Ongoing Monitoring and Performance Metrics
Integrating controls is just the beginning. Continuous monitoring ensures these measures remain effective as threats evolve and operations change. Key risk indicators (KRIs) like failed login attempts, patching delays, overdue vendor assessments, and response times for incidents can serve as early warning signals of potential issues.
High-risk areas should undergo quarterly audits, while lower-risk domains can be reviewed annually. These audits help identify control gaps or inefficiencies, giving organizations a chance to make adjustments before minor problems escalate into major incidents.
Purpose-built platforms can enhance monitoring by providing real-time visibility into risks across the organization and its vendors. For example, one healthcare organization reduced its full-time employee (FTE) needs for risk assessments by automating processes with Censinet RiskOps™ [1].
Benchmarking against industry standards is another valuable tool. It helps organizations gauge their performance relative to peers and identify areas for improvement. As Brian Sterud, CIO at Faith Regional Health, explained, benchmarking can justify resource allocation and ensure the organization remains a leader in key cybersecurity areas [1]. This external perspective complements internal efforts, helping to identify blind spots and align investments with broader industry priorities.
A healthcare provider that integrated ISO 27001 with ISO 31000 reported a 30% reduction in risk assessment efforts. This was achieved by unifying risk processes and control mapping, leading to better visibility of interconnected risks and more efficient audits [2]. This example shows how thoughtful integration of risk frameworks and monitoring tools can enhance security while delivering tangible operational benefits.
Maintaining Continuous Improvement and Operational Resilience
ISO 27001 emphasizes the Plan–Do–Check–Act cycle, a structured approach that transforms incidents, audits, and near-misses into actionable improvements. For healthcare organizations, this means documenting every breach, downtime, or control gap in a risk register and promptly updating procedures. Without this feedback loop, risk management can stagnate, leaving organizations vulnerable to evolving threats. By keeping this cycle active, healthcare providers can strengthen both operational resilience and ongoing risk management efforts.
Incorporating Lessons from Incidents and Audits
Each security incident or service disruption offers a learning opportunity. Healthcare organizations should carefully document root causes, contributing factors, and control failures. To ensure alignment with ISO 27001, connect these root causes to specific clauses and Annex A controls. For instance, if a ransomware attack occurs due to delayed patching, corrective actions might include shortening patch management timelines and setting up automated alerts for overdue updates.
Audits - whether internal or external - shouldn't be treated as mere compliance exercises. Instead, they can highlight systemic weaknesses. For example, repeated findings like incomplete vendor risk assessments suggest a need for workflow revisions or automation. Incorporating real-world incidents and audit findings into staff training helps employees understand the importance of specific controls. These lessons serve as a critical link between incident analysis and effective business continuity planning.
Connecting Risk Management with Business Continuity
To build stronger operational resilience, risk management must align closely with business continuity and disaster recovery (BC/DR) planning. This starts with conducting business impact analyses (BIAs) that focus on high-impact risks, such as ransomware affecting electronic health records (EHRs), PACS outages, or interruptions in clinical cloud services. Continuity plans should include tested procedures to ensure the swift restoration of critical functions.
Scenario-based exercises - like simulating a regional data center outage or a cloud vendor breach - are essential for testing BC/DR plans and incident response strategies. The insights gained from these simulations should feed back into the continuous improvement cycle of the ISMS, resulting in updated risk assessments and controls. For example, during a major supply chain disruption, one healthcare organization with well-integrated response teams demonstrated strong resilience by coordinating effectively[2].
Scaling Risk Management Through Automation
As healthcare organizations grow and their vendor ecosystems expand, managing risks manually becomes increasingly impractical. Automation offers scalability while maintaining human oversight for critical decisions. Tools like Censinet RiskOps™ can handle routine tasks such as tracking vendor assessments, monitoring key risk indicators, and routing critical findings to the appropriate teams. Many healthcare organizations report that automation not only lightens staffing workloads but also increases their capacity to conduct assessments.
Automation is particularly effective for repetitive, data-driven tasks like aggregating risk scores, scheduling assessments, and flagging overdue actions. However, decisions involving patient safety, clinical judgment, or complex trade-offs should always remain in human hands. To measure the effectiveness of risk management and operational resilience, organizations can track metrics such as the time taken to detect and respond to incidents, the percentage of critical vendors with up-to-date assessments, and the closure rate of audit findings. Regular management reviews of these metrics ensure that continuous improvement stays front and center.
Conclusion
Bringing ISO 27001 risk management into healthcare isn't just about ticking compliance boxes - it’s about strengthening the foundation of information security and operational resilience. The process starts with grasping the basics of ISO 27001 and identifying risks unique to healthcare. From there, organizations can build a framework that ties risk criteria directly to assets and patient care. Risk assessments then become part of everyday workflows, whether evaluating new technologies, vendors, or clinical processes. By implementing controls, monitoring through metrics and dashboards, and applying the Plan–Do–Check–Act cycle, healthcare providers can create a system of continuous improvement. The result? Better patient safety, stronger protection of sensitive health information, and more resilient operations.
Some U.S. healthcare organizations worry that adopting ISO 27001 might slow down clinicians or add layers of bureaucracy. However, integrated risk management can actually streamline operations. By eliminating redundant efforts and aligning risk management with broader operational priorities - like minimizing EHR downtime or addressing supply chain disruptions - organizations can reduce resource demands. Research shows that unifying risk management efforts, such as using an integrated risk register and joint governance committee, significantly cuts down on inefficiencies while improving decision-making [2].
Tools like Censinet RiskOps™ make this integration more practical by automating repetitive tasks, managing vendor assessments, and ensuring critical issues reach the appropriate teams. This kind of automation and consistency is essential in the fast-paced, high-stakes environment of U.S. healthcare, where organizations must juggle HIPAA compliance, OCR oversight, and the constant demands of 24/7 patient care. By embedding ISO 27001 into daily operations, healthcare providers can achieve the resilience needed to navigate these challenges effectively.
FAQs
What are the key benefits of ISO 27001 for healthcare organizations in managing risks?
ISO 27001 offers healthcare organizations a clear framework to identify, assess, and address risks tied to sensitive patient information, clinical systems, and medical devices. By adopting this standard, healthcare providers can strengthen their security measures, meet regulatory requirements, and improve day-to-day processes.
Additionally, it promotes a proactive approach to managing risks, safeguarding crucial assets like protected health information (PHI) and supply chain operations. This not only secures vital resources but also builds confidence among patients and partners.
How does ISO 27001 differ from ISO 31000 in risk management?
ISO 27001 is tailored for information security management, offering a structured framework to protect sensitive data, like patient records, through an information security management system (ISMS). Its focus is on implementing risk-based controls that address cybersecurity challenges.
On the other hand, ISO 31000 provides a broad framework for managing risks across various industries. It outlines principles and processes for handling all types of risks but doesn’t specifically target information security like ISO 27001 does. For healthcare organizations, ISO 27001 stands out because of its detailed approach to safeguarding sensitive information and ensuring compliance with strict data security standards.
How does Censinet RiskOps™ simplify risk management for healthcare organizations?
Censinet RiskOps™ transforms how healthcare organizations handle risk management by leveraging AI-powered automation to identify, assess, and address risks continuously. This approach minimizes the need for manual effort, boosts the precision of risk evaluations, and provides real-time monitoring to help organizations react swiftly to emerging threats.
By automating intricate processes and streamlining workflows, Censinet RiskOps™ improves operational efficiency while safeguarding critical assets like patient information, clinical systems, and medical devices. This enables healthcare providers to prioritize delivering quality care without compromising on strong risk management protocols.


