ISO 27001 vs HIPAA: Compliance in Healthcare
Post Summary
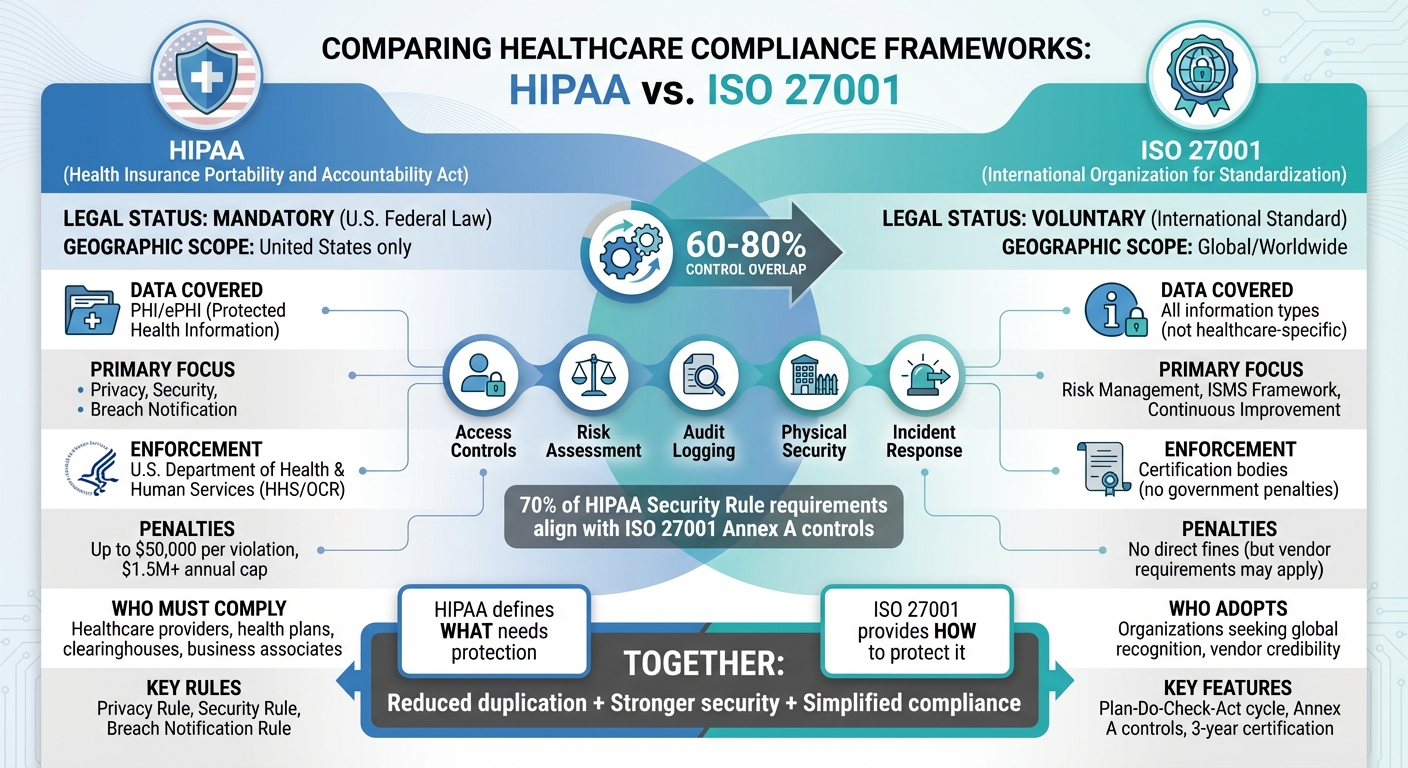
Healthcare organizations in the U.S. must protect patient data while meeting strict regulations. HIPAA is a federal law requiring safeguards for Protected Health Information (PHI), while ISO 27001 is a voluntary international standard for managing information security. Both frameworks share overlapping controls but serve different purposes:
- HIPAA: Mandatory for U.S. healthcare entities and business associates handling PHI. Focuses on privacy, security, and breach notification.
- ISO 27001: Voluntary, global framework covering all types of information, not limited to healthcare. Offers a structured system for risk management and continuous improvement.
Key takeaway: HIPAA defines what needs protection, while ISO 27001 provides a roadmap for how to protect it. Aligning both reduces duplication, strengthens security, and simplifies compliance.
Quick Comparison
| Criteria | HIPAA | ISO 27001 |
|---|---|---|
| Scope | U.S. healthcare, PHI/ePHI only | Global, all information types |
| Legal Status | Mandatory (U.S. law) | Voluntary (international standard) |
| Focus | Privacy, security, breach rules | Risk management, ISMS framework |
| Enforcement | U.S. Dept. of Health & Human Services (HHS) | Certification bodies |
| Penalties | Fines up to $1.5M+ per year | No direct penalties |
ISO 27001 vs HIPAA Compliance Framework Comparison
HIPAA Compliance: A U.S. Federal Requirement
HIPAA places strict legal obligations on healthcare organizations and their partners. As a federal law, it mandates compliance from any entity that handles patient data. This includes not only healthcare providers but also their business associates. The Department of Health and Human Services Office for Civil Rights (OCR) enforces these rules, making HIPAA compliance non-negotiable for anyone creating, receiving, maintaining, or transmitting protected health information (PHI).
Core HIPAA Rules
HIPAA compliance revolves around three main rules:
- Privacy Rule: This rule dictates how PHI can be used and shared, while also granting patients rights to access and amend their medical records.
- Security Rule: Focused on electronic PHI (ePHI), this rule requires organizations to implement safeguards - administrative, physical, and technical. Examples include conducting risk analyses, using encryption, managing access controls, and providing workforce training.
- Breach Notification Rule: In the event of a breach involving unsecured PHI, this rule requires timely notifications to affected individuals and to the Department of Health and Human Services (HHS).
Who Must Comply with HIPAA?
HIPAA applies to two main groups:
- Covered entities: These are healthcare providers, health plans, and clearinghouses that handle electronic health information during standard transactions like billing. This group includes hospitals, clinics, telehealth providers, and insurers.
- Business associates: Vendors working with covered entities, such as EHR providers, billing companies, cloud hosting services, data analytics firms, and telemedicine platforms, also fall under HIPAA. They must sign Business Associate Agreements (BAAs) and adopt the same level of safeguards required under HIPAA.
Subcontractors working for business associates - like infrastructure providers supporting EHR systems - must also comply. These downstream entities inherit HIPAA obligations through agreements, ensuring consistent standards for PHI protection, risk management, and reporting breaches. Failing to meet these requirements can lead to severe consequences.
Penalties for Non-Compliance
HIPAA violations can result in steep penalties. Civil fines can reach $50,000 per violation, with annual caps exceeding $1.5 million (adjusted for inflation). Criminal penalties, enforced by the Department of Justice, apply to those who knowingly misuse PHI, with fines and potential jail time depending on the severity of the offense.
When determining penalties, OCR considers factors like the scope of the violation, the number of individuals affected, the harm caused, and whether the organization acted negligently or took corrective action. Resolutions often include Corrective Action Plans (CAPs), which may involve multi-year monitoring, policy revisions, independent audits, employee retraining, and regular compliance reporting.
Beyond financial penalties, public exposure can lead to reputational damage. OCR publishes enforcement actions on its "Wall of Shame", and media coverage of significant breaches can erode patient trust. These consequences highlight the importance of strict adherence to HIPAA requirements, underscoring the need for both mandatory compliance and proactive best practices.
ISO 27001: A Global Standard for Information Security
While HIPAA is a U.S. law specifically designed to protect patient data, ISO 27001 provides a global framework for safeguarding various types of information assets, going far beyond just healthcare data. This standard covers everything from Protected Health Information (PHI) to financial and research data, making it an attractive option for healthcare organizations that need to secure both clinical and operational systems. By adopting ISO 27001, these organizations can protect their entire enterprise under a unified security framework.
At its core, ISO 27001 establishes an Information Security Management System (ISMS). This structured program helps organizations identify risks, implement controls, and continuously improve their security practices. While HIPAA focuses on defining what data needs protection, ISO 27001 provides a roadmap for building and maintaining a security program that evolves with time and emerging threats.
Key Features of ISO 27001
ISO 27001 stands out for its comprehensive approach to security. One of its central features is a risk-based methodology, which requires organizations to identify their information assets, evaluate potential threats and vulnerabilities, and apply appropriate controls to address those risks. The standard includes Annex A, a detailed catalog of controls that cover areas like governance, physical security, technology, and personnel. These controls address critical aspects such as access management, system configuration, vendor oversight, encryption, and business continuity - going beyond HIPAA's more focused requirements.
The framework also incorporates the Plan-Do-Check-Act (PDCA) cycle, which promotes continuous improvement. Through this cycle, organizations:
- Plan: Define the scope and assess risks.
- Do: Implement controls and policies.
- Check: Monitor performance and conduct audits.
- Act: Address gaps and update risk assessments.
This iterative process ensures that security measures remain effective as technology and threats evolve. For healthcare providers managing complex systems like imaging platforms or telehealth, the PDCA cycle complements HIPAA's risk analysis requirements, transforming security from a one-time task into an ongoing commitment.
Another key aspect of ISO 27001 is its emphasis on governance and accountability. Organizations are required to assign security responsibilities across clinical, IT, and business units. This often involves appointing a Chief Information Security Officer (CISO), forming risk committees, and designating control owners. By integrating security into daily operations - such as how patient records are accessed or how vendors are evaluated - ISO 27001 ensures that security becomes part of the organization's culture, not just an IT concern.
Certification and Audits
Achieving ISO 27001 certification involves a structured process carried out by certification bodies. The journey typically begins with a gap analysis to identify areas where the organization's practices fall short of the standard. After addressing these gaps, the formal audit process begins, which includes two key stages:
- Stage 1 Audit: A review of ISMS documentation, including policies, risk methodologies, and the Statement of Applicability, which outlines implemented controls and their rationale.
- Stage 2 Audit: A deeper dive into the actual implementation of controls. Auditors interview staff, examine evidence, and test controls across different departments.
Upon meeting all requirements, the organization receives an ISO 27001 certificate valid for three years. During this period, annual or semiannual surveillance audits are conducted to ensure ongoing compliance. At the end of the three years, a full recertification audit is required. This rigorous process provides external validation that the ISMS is not only functioning but also improving over time.
Why U.S. Healthcare Organizations Adopt ISO 27001
Many healthcare organizations and digital health vendors in the U.S. are adopting ISO 27001 alongside HIPAA compliance, and for good reason. This dual approach not only satisfies federal requirements but also supports a more comprehensive cybersecurity strategy. Here’s why ISO 27001 is gaining traction:
- Global Recognition: Unlike HIPAA, which is limited to the U.S., ISO 27001 is recognized worldwide. This makes it a valuable credential for organizations working with international partners, payers, or regulators. In fact, many large health systems now view ISO 27001 certification as a requirement for vendors handling PHI or integrating with their systems.
- Demonstrating Good Faith: Certification can serve as evidence of a proactive approach to security, potentially reducing penalties in the event of a data breach if a robust ISMS was in place.
- Streamlined Compliance: With ISO 27001, organizations can adopt a "one and done" approach, implementing controls that align with multiple frameworks like HIPAA and SOC 2. This reduces audit fatigue and lowers long-term compliance costs.
- Operational Efficiency and Vendor Oversight: The standard’s structured approach to third-party risk management ensures better oversight of vendors like cloud providers, EHR platforms, and medical device suppliers. Additionally, its focus on business continuity and incident response helps healthcare organizations stay resilient against challenges like ransomware attacks, system outages, and supply chain disruptions.
ISO 27001 vs HIPAA: Key Differences and Overlaps
At a glance, HIPAA and ISO 27001 share a common goal: protecting healthcare information. However, their differences are crucial for understanding how to achieve compliance effectively. HIPAA is a U.S. federal law, while ISO 27001 is an international standard that organizations can voluntarily adopt. Where their requirements intersect, healthcare providers can align efforts to simplify compliance. Where they differ, each fills specific gaps left by the other. This comparison helps highlight how to manage overlapping controls while addressing unique requirements.
Purpose and Legal Status
HIPAA is mandatory for entities like healthcare providers, insurers, and their business associates that handle protected health information (PHI) or electronic PHI in the United States. Enforced by the Department of Health and Human Services (HHS) Office for Civil Rights (OCR), HIPAA violations can lead to investigations, corrective action plans, and penalties ranging from hundreds of thousands to several million dollars per case[4].
ISO 27001, on the other hand, is voluntary. Organizations choose to adopt the standard and can pursue certification through accredited auditors. While no federal agency enforces ISO 27001 or imposes fines for non-adoption, many healthcare systems and insurers require their vendors to be ISO 27001 certified if they handle PHI. Additionally, ISO 27001 certification can serve as a mitigating factor during OCR investigations[3].
Scope of Data and Protection
HIPAA focuses specifically on PHI and electronic PHI - essentially, identifiable health information managed by covered entities or their business associates[4]. It does not extend to other sensitive data, like employee records, intellectual property, or general corporate information.
ISO 27001, however, covers "any and all types of information", as noted by BSI. This broader scope makes it suitable for protecting not just patient data but also clinical systems, financial records, operational technology, and supply chain information. For healthcare organizations, ISO 27001 offers a unified framework for safeguarding enterprise-wide information.
Risk Management Approach
HIPAA requires covered entities to conduct a risk analysis and implement "reasonable and appropriate" safeguards, but it provides limited guidance on how to approach this process. The Security Rule is largely prescriptive, listing specific administrative, physical, and technical safeguards, but it doesn’t emphasize ongoing refinement.
ISO 27001 takes a more dynamic approach, using a risk-based, continuous improvement model built around the Plan-Do-Check-Act (PDCA) cycle. Organizations assess information assets, evaluate threats and vulnerabilities, implement appropriate controls, and regularly review their security measures. Notably, around 70% of HIPAA Security Rule requirements align with ISO 27001 Annex A controls, including areas like access control, audit logging, incident response, and physical security[5].
sbb-itb-535baee
Aligning ISO 27001 and HIPAA for Unified Compliance
Healthcare organizations often face the challenge of juggling multiple compliance frameworks like ISO 27001 and HIPAA. Instead of treating these as separate tracks, they can build a single, integrated information security management system (ISMS) to cover both. This unified approach minimizes duplicate efforts, reduces audit stress, and strengthens overall security. In fact, 60–80% of controls, policies, and processes can overlap between the two frameworks[1][6]. A key step in this process is mapping controls to bridge the gap between ISO 27001 and HIPAA.
Mapping Controls Between ISO 27001 and HIPAA
The process begins with a control mapping matrix that links HIPAA Security Rule safeguards to ISO 27001 Annex A controls. For instance:
- HIPAA’s workforce security and security awareness safeguards align with ISO 27001’s human resource security and training controls[2][6].
- Access controls for electronic PHI connect directly to ISO 27001’s identity management, authentication, and access rights controls[2][5].
- HIPAA’s physical safeguards for facilities and devices correspond to ISO 27001’s physical and environmental security measures[2][5].
Organizations centralize this mapping in a control repository, tying each control to unified policies, procedures, and technical configurations. This allows them to gather a single set of evidence that supports both HIPAA assessments and ISO 27001 audits simultaneously[8][6]. For example, access management controls - covering unique user IDs, automatic logoffs, and access authorization - can address multiple HIPAA requirements when explicitly mapped out[1][5][7].
Building a Unified Risk Management Program
A practical unified approach starts with one integrated risk assessment. Using ISO 27001’s structured methodology, organizations can ensure all HIPAA-required elements are included. From there, they create a combined Statement of Applicability that references ISO 27001 controls while indicating which ones address HIPAA safeguards[5][10].
Policies can then be consolidated to enforce a single set of protocols for security, access, incident response, and vendor management that meet both frameworks’ requirements[2][4]. Assigning control owners across IT, clinical, and compliance teams ensures HIPAA oversight is fully integrated into the ISMS[9][3]. Internal audits and monitoring processes can test both control effectiveness and HIPAA compliance, feeding results into management reviews for continuous improvement[8][3].
For example, a single enterprise access policy could enforce role-based controls, least privilege, periodic reviews, and specific HIPAA provisions for ePHI[2][5][6]. Similarly, a unified incident management process could handle triage, containment, and lessons learned per ISO 27001, while also incorporating HIPAA-specific breach assessment, notification timelines, and documentation requirements for unsecured PHI[8][3].
How Censinet Supports Compliance
Censinet RiskOps™ simplifies dual compliance by providing a centralized platform for managing third-party and enterprise risks. This platform addresses overlapping requirements for vendors, patient data, medical devices, and supply chains under both ISO 27001 and HIPAA.
With cybersecurity benchmarking, healthcare organizations can compare their security programs against industry standards, identifying gaps across both frameworks. Brian Sterud, CIO of Faith Regional Health, shared:
"Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters."
Censinet’s collaborative risk network also allows healthcare providers and vendors to securely share cybersecurity and risk data, streamlining assessments. Terry Grogan, CISO at Tower Health, noted that after implementing Censinet RiskOps™, the organization reallocated three full-time employees while increasing the volume of risk assessments. Now, only two FTEs are needed to manage the process, demonstrating how efficiency can improve when handling overlapping ISO 27001 and HIPAA requirements.
Conclusion
HIPAA establishes the legal foundation for safeguarding patient data in the U.S., while ISO 27001 provides a structured, auditable framework for managing information security. In essence, HIPAA specifies what needs protection, and ISO 27001 offers guidance on how to ensure that protection remains consistent and effective over time [1][4].
By aligning these two frameworks, healthcare organizations can unlock operational efficiencies. Since many controls, policies, and processes overlap between HIPAA and ISO 27001, organizations can create a single, streamlined information security management system (ISMS). This approach reduces redundant efforts, simplifies compliance, and cuts down on audit fatigue. A unified ISMS not only strengthens patient data protection but also showcases a higher level of process maturity to global stakeholders - such as payers, partners, and collaborators in life sciences - who increasingly expect ISO 27001 certification alongside HIPAA compliance [4][3][7].
The benefits of integrating these frameworks are clear: more efficient risk assessments, consolidated policies, cost savings, and stronger cybersecurity. With healthcare being one of the most frequently targeted industries for cyberattacks - and U.S. breach reports often involving millions of patient records annually [3][6] - treating HIPAA as merely a baseline is no longer enough. Adopting ISO 27001 helps organizations build a more mature security program, better equipped to handle evolving cybersecurity threats while meeting regulatory requirements.
Censinet RiskOps™ simplifies this integration by centralizing control mapping and risk evidence. The platform enables healthcare organizations to manage enterprise and third-party risks for protected health information (PHI), clinical systems, medical devices, and supply chains in a unified, scalable program. By moving beyond fragmented, manual processes and benchmarking against industry standards, organizations can develop the robust cybersecurity measures that patient safety demands.
Combining HIPAA and ISO 27001 isn’t just about meeting compliance - it’s about advancing cybersecurity to protect patients, satisfy regulatory expectations, and thrive in today’s interconnected healthcare environment.
FAQs
How do HIPAA and ISO 27001 work together to improve healthcare cybersecurity?
HIPAA and ISO 27001 work hand in hand, addressing distinct yet interconnected elements of cybersecurity in healthcare. HIPAA zeroes in on safeguarding patient privacy and protecting protected health information (PHI), ensuring adherence to U.S. regulations. Meanwhile, ISO 27001 offers a globally recognized framework for establishing and managing an information security management system (ISMS) to tackle risks and improve security measures.
Together, these standards empower healthcare organizations to not only comply with regulatory demands but also implement industry best practices for managing risks effectively. This combination boosts data protection, minimizes vulnerabilities, and strengthens the organization's overall cybersecurity defenses.
Why would a healthcare organization in the U.S. adopt ISO 27001 if HIPAA compliance is required?
While HIPAA compliance is a legal requirement for U.S. healthcare organizations, incorporating ISO 27001 can offer additional layers of protection. ISO 27001 provides a globally accepted framework for managing information security risks, helping organizations bolster their cybersecurity defenses.
By aligning with ISO 27001, healthcare providers can show their dedication to thorough risk management, enhance trust with global partners, and simplify compliance when operating internationally. This combination not only strengthens the safeguarding of sensitive patient information but also supports the organization's ability to adapt and thrive over time.
What are the key advantages of combining HIPAA and ISO 27001 into a single compliance approach?
Combining HIPAA and ISO 27001 into a single compliance strategy allows healthcare organizations to simplify their processes, avoid redundant efforts, and strengthen their cybersecurity measures. By aligning these frameworks, organizations can better protect sensitive patient information, meet regulatory standards, and build a more robust defense against cyberattacks.
This unified approach also boosts efficiency by streamlining risk management and encouraging a consistent security mindset across teams. For healthcare providers, this translates to smarter use of resources and stronger protection for critical systems and patient data.


