Joint Commission Vendor Risk Requirements: What Healthcare Organizations Must Know
Post Summary
Managing vendor risks is mandatory for healthcare organizations to ensure patient safety, protect sensitive data, and maintain regulatory compliance. The Joint Commission has set specific standards to help organizations monitor and assess third-party vendors, especially those with access to facilities, systems, or patient information. Non-compliance can lead to severe financial penalties, data breaches, and disruptions to patient care.
Key Takeaways:
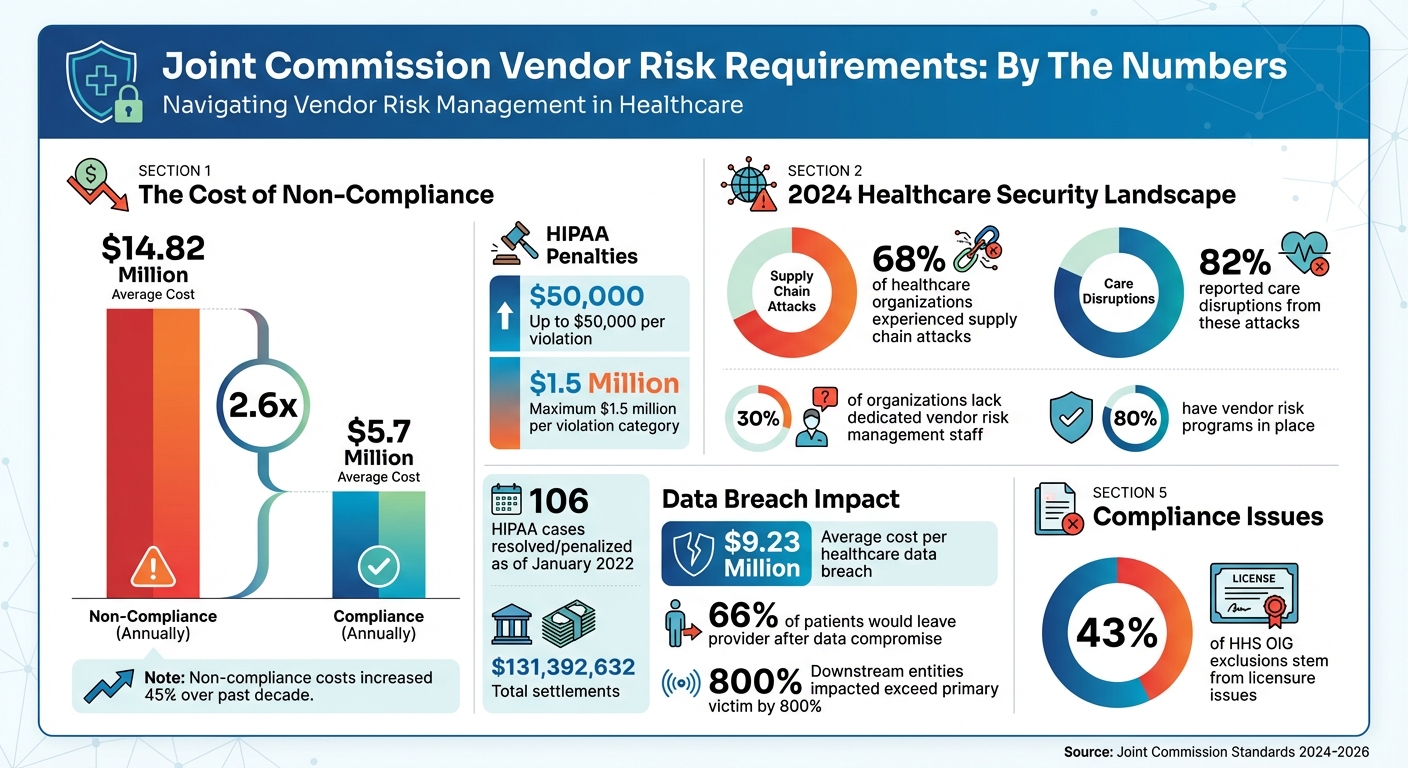
- Why It Matters: In 2024, 68% of healthcare organizations experienced supply chain attacks, with 82% reporting care disruptions. Non-compliance costs averaged $14.82 million annually, compared to $5.7 million for compliant organizations.
- Core Standards: Requirements include tracking vendor access (EC.02.01.01), verifying qualifications (HR.01.0.01), safeguarding patient rights (RI.01.01.01), and ensuring infection control (IC.02.01.01).
- 2025-2026 Changes: New National Performance Goals (NPGs) will replace the National Patient Safety Goals, emphasizing continuous improvement in vendor risk management starting January 1, 2026.
- Best Practices: Conduct regular risk assessments, prioritize high-risk vendors, verify compliance with privacy and cybersecurity standards, and use digital tools for monitoring and reporting.
Bottom Line: Healthcare organizations must implement structured vendor risk management to avoid costly penalties, protect accreditation, and ensure quality care.
Joint Commission Vendor Risk Management Statistics and Compliance Costs 2024
Joint Commission Vendor Risk Standards and Recent Changes

The Joint Commission works closely with healthcare professionals, experts, consumers, and the Centers for Medicare & Medicaid Services (CMS) to develop its standards. This collaborative process ensures the requirements align with operational realities while upholding strict safety and quality expectations [4]. Understanding these standards is crucial because Joint Commission surveys are unannounced and occur every 18 to 36 months, meaning healthcare organizations must always stay prepared [1][9].
Key Elements of Vendor Risk Assessments
Vendor risk assessments need to cover various compliance and safety aspects. Healthcare organizations must confirm that vendors meet background verification standards, including checks for exclusions from federal healthcare programs. Notably, 43% of exclusions by the Department of Health and Human Services (HHS) Office of Inspector General (OIG) stem from licensure issues, such as revocations or disciplinary actions [9]. This makes primary source verification critical, both during initial credentialing and ongoing monitoring.
Another essential component is data and privacy protection. Vendors managing protected health information (PHI) are required to sign Business Associate Agreements (BAAs) and Data Processing Agreements (DPAs). They must also demonstrate compliance with standards like PCI when applicable. Required safeguards include antivirus software, firewalls, and encryption for data at rest and in transit, in line with NIST guidelines. Additionally, vendors must follow recognized cybersecurity frameworks and report any security breaches or violations immediately [3].
Specific standards further define vendor management expectations:
- EC.02.01.01 mandates systems to track and monitor vendor access, purpose, and compliance.
- RI.01.01.01 and IM.02.01.01 focus on protecting patient rights and privacy.
- IC.02.01.01 addresses infection control protocols.
- HR.01.0.01, HR.01.06.01, and HR.01.07.01 require verification of vendor qualifications, competency, and performance [1].
Together, these requirements create a robust framework for managing vendors, extending well beyond basic access control. These standards also lay the groundwork for upcoming changes that will reshape vendor risk management.
2025-2026 Standard Updates
In June 2025, the Joint Commission will introduce Accreditation 360, a new framework that shifts key compliance measures. These changes will take full effect on January 1, 2026, for hospital and critical access hospital accreditation programs [5][6][7][8]. This marks a major shift in how healthcare organizations approach compliance and performance evaluation.
One significant update is the replacement of the National Patient Safety Goals (NPSGs) chapter with the new National Performance Goals (NPGs) chapter [4][10]. This change broadens the focus to include measurable and actionable topics that go beyond traditional safety metrics. For vendor risk management, the new standards emphasize continuous improvement, requiring organizations to enhance how they assess and manage third-party risks. By aligning these updates with CMS Conditions of Participation, the Joint Commission strengthens the link between accreditation and federal healthcare program participation, making vendor compliance even more critical for maintaining Medicare and Medicaid eligibility.
How to Conduct Vendor Risk Assessments
Carrying out vendor risk assessments that align with Joint Commission standards requires a well-organized approach that balances thorough evaluation with operational efficiency. As previously mentioned, supply chain attacks and non-compliance can pose serious threats. Regular assessments are essential to maintain adherence to these standards, as discussed earlier. Below, we’ll break down how to identify and assess vendors effectively.
How to Identify and Prioritize High-Risk Vendors
The first step is to categorize vendors based on their potential impact on critical areas like patient safety, data privacy, system security, and regulatory compliance. Vendors who handle Protected Health Information (PHI) or Personally Identifiable Information (PII), have direct access to IT systems, are involved in patient care, or participate in federal healthcare programs should be treated as high-priority.
The Joint Commission emphasizes the importance of knowing who is entering your facility, their purpose, and their activities - right down to individual representatives. This means your prioritization framework must address both physical access and digital interactions. For example, vendors involved in installing medical equipment, supplying medications, or managing clinical systems demand immediate attention due to the direct impact their actions can have on patient outcomes.
To streamline this process, establish standardized credentialing policies for vendor approvals. These policies should include requirements for documentation, background checks, training certifications, and compliance with relevant regulations. Responsibilities for primary source verification, credential reviews, and renewal timelines should be clearly defined. Digital credentialing tools can simplify this by flagging inconsistencies, tracking expiration dates, and sending reminders for re-verifications.
Performing Vendor Due Diligence
Once vendors are categorized, the next step is conducting comprehensive compliance checks. This goes beyond basic credential reviews to include full-scale compliance assessments. For vendors paid through federal healthcare programs, ensure their personnel have not been involved in fraud, embezzlement, theft, bribery, or other criminal activities. Also, confirm they are not debarred or suspended.
Vendors handling PHI must sign Business Associate Agreements (BAAs) and Data Processing Agreements. They should also demonstrate compliance with PCI standards for credit card transactions and have identity theft prevention measures in place for PII. Security controls such as antivirus software, firewalls, encryption that meets NIST standards, strict access protocols, timely software updates, secure data storage, and intrusion detection systems are essential.
Additionally, vendors should adhere to recognized cybersecurity frameworks and provide evidence of compliance through certifications like Hitrust CSF or ISO 27001, or third-party audits like SSAE18 Type II or SOC2 Type II. Any subcontractors they use must meet the same security and compliance standards, as outlined in their contracts. Vendors should also disclose any conflicts of interest, such as personal or financial ties to your organization.
Scheduling Regular Reviews and Updates
Maintaining compliance is an ongoing process. This requires consistent monitoring, testing, and conducting annual risk assessments. Set up a system to regularly audit vendor licenses and certifications to ensure they remain up to date. Include regular training sessions for vendors on patient privacy, security protocols, and regulatory updates.
Create a clear workflow for vendor document submission, verification, and approval. After onboarding, offer orientation programs to familiarize vendors with your hospital’s policies and procedures. This ensures they align with your patient safety objectives. For high-risk vendors, schedule formal reviews at least once a year, with more frequent check-ins for those handling critical services or sensitive data.
Using technology can significantly reduce administrative tasks and the risk of human error. Tools powered by AI and machine learning can provide real-time updates on document status, flag compliance issues, and send alerts when certifications are nearing expiration. This proactive approach keeps your organization audit-ready at all times.
Common Compliance Gaps and Their Consequences
Frequent Vendor Risk Management Failures
When it comes to vendor risk management, falling short of Joint Commission standards can have serious repercussions - not just for patient safety but also for an organization's accreditation. While nearly 80% of healthcare organizations have vendor risk programs in place, a striking 30% lack dedicated staff to manage them. This staffing gap often leads to incomplete evaluations, leaving organizations exposed to unnecessary risks [11].
One major issue is the failure to conduct thorough assessments for all vendors, regardless of their size or the services they provide. Many organizations rely on a one-time evaluation rather than performing annual reviews or ongoing audits [11]. Another common shortfall is the inability to keep up with new regulations that impact vendor operations. For instance, healthcare organizations often struggle to provide data on who enters their facilities, why they’re there, and what activities they’re performing - a critical requirement under EC.02.01.01 [1][11]. These gaps in oversight and outdated practices significantly raise the stakes.
"Without thorough evaluation, unqualified vendors can compromise patient care and regulatory compliance."
- Amy Andersen, Chief Customer Officer, Verisys Corporation [2]
Other frequent compliance failures include weak protections for patient rights (RI.01.01.01, IM.02.01.01), poor infection control measures (IC.02.01.01), and inadequate verification of staff qualifications (HR.01.0.01, HR.01.06.01, HR.01.07.01) [1]. These lapses don’t just pose risks to patient safety - they also open the door to significant financial and operational setbacks.
Penalties and Risks of Non-Compliance
The financial toll of non-compliance is staggering. On average, healthcare organizations face costs of $14.82 million for non-compliance - a figure that has jumped over 45% in the past decade [2]. By comparison, the cost of maintaining compliance is far lower, averaging $5.7 million [2]. Violations of HIPAA alone carry civil monetary penalties of up to $50,000 per violation, with a maximum fine of $1.5 million per violation category [12][13]. As of January 2022, the Office for Civil Rights had resolved or penalized 106 HIPAA cases, amounting to a total of $131,392,632 in settlements [12].
Real-world cases highlight the severity of these risks. For example, in 2021, Excellus Health Plan faced a $5.1 million penalty after a 2015 data breach exposed the information of 9.3 million patients. The breach stemmed from failures in conducting proper risk analyses and addressing vulnerabilities in electronic protected health information [12]. Similarly, in 2013, North Memorial Healthcare paid $1.55 million after a stolen laptop from a business associate compromised unencrypted patient data for 290,000 individuals [12].
The consequences extend beyond financial penalties. Non-compliance can jeopardize accreditation, which is crucial for Medicare and Medicaid reimbursements. Data breaches in healthcare cost an average of $9.23 million per incident, factoring in lost revenue, legal fees, settlements, forensic investigations, and breach notifications [12]. Moreover, trust is at stake - 66% of patients say they would leave their healthcare provider if their personal or payment information were compromised [12].
The risks don’t stop there. In 2024, 68% of healthcare organizations reported experiencing supply chain attacks, with 82% acknowledging disruptions in patient care as a result [2]. These ripple effects can be devastating; the number of entities impacted by a single attack can exceed the primary victim by over 800% [11].
"Failing to identify risky vendors can cost you money, customers, and your company's reputation."
sbb-itb-535baee
Using Censinet RiskOps™ for Vendor Risk Management

Managing vendor risks in healthcare has become increasingly challenging, with rising non-compliance costs and ever-evolving Joint Commission standards. To tackle these complexities, Censinet RiskOps™ provides a centralized platform designed to simplify third-party risk management. This all-in-one solution integrates seamlessly with monitoring and reporting processes, making vendor risk management more efficient. Let’s take a closer look at how its key features help streamline the process.
Automated Risk Assessments with Censinet RiskOps™
One of the standout features of Censinet RiskOps™ is its ability to automate vendor risk assessments. By automating workflows, the platform significantly reduces manual effort, making the entire evaluation process faster and more efficient. It also integrates cybersecurity benchmarking and compliance checks into a single interface, ensuring that assessments are not only thorough but also easy to manage from one central location.
Vendor Collaboration Through Censinet Connect™
Censinet Connect™ facilitates smoother communication between healthcare organizations and their vendors. This tool creates a direct channel for sharing documents, updating security details, and maintaining ongoing discussions about risk management. By making collaboration more transparent and efficient, healthcare organizations and vendors can stay aligned on shared objectives, ensuring that risk management efforts are continuously updated and effective.
Faster Assessments with Censinet AI™

Censinet AI™ takes automation to the next level by speeding up the assessment process even further. It automates tasks like completing and reviewing questionnaires, generating concise risk reports in record time. The platform also balances automation with human oversight, allowing for configurable reviews to ensure accuracy and reliability. This combination of speed and precision enables healthcare organizations to conduct faster, more detailed evaluations without compromising on quality.
Maintaining Compliance Through Monitoring and Reporting
After conducting thorough risk assessments, the next step to meet Joint Commission standards is consistent monitoring and accurate reporting. These processes are essential to avoid compliance issues that could lead to significant costs. Recent findings highlight just how important it is to have systems in place that provide real-time insights. By identifying potential gaps early, organizations can act before those gaps turn into expensive problems.
Adding Vendor Metrics to Performance Improvement Programs
Incorporating vendor performance data into your quality improvement efforts can enhance accountability and lead to better results. Sharing vendor risk assessment findings with multidisciplinary teams - such as Safety, Environment of Care, or Infection Control Committees - helps ensure that risk mitigation strategies are implemented effectively. These teams can use data from system failures and proactive assessments to improve safety across the board.
Key metrics to track include credentialing status, completion of background checks, compliance with infection control protocols, and adherence to patient privacy standards. Additionally, organizations should monitor vendor identification metrics and conduct annual risk assessments at a minimum. For vendors considered high-risk, more frequent reviews are advisable. Staying updated on regulatory changes and addressing vendor non-compliance promptly - whether through scheduled calls or, if necessary, ending partnerships - helps maintain high standards[11]. Feeding these metrics into dashboard systems provides instant insights into vendor compliance, streamlining the review process.
Tracking Vendor Risks with Centralized Dashboards
Centralized dashboards revolutionize how organizations monitor and respond to vendor risks. These systems automatically log vendor activities, offering instant access to real-time compliance data that surveyors can easily review. For example, a credential dashboard provides details on each vendor representative’s access level, required credentials, and the current status of those credentials.
With intuitive filters for sorting data by date, department, or access purpose, these dashboards make reviews faster and more effective. They also allow organizations to spot trends and identify high-risk areas, enabling targeted preventive measures where they’re needed most. Considering the financial risks tied to non-compliance, centralized dashboards are not just convenient - they’re crucial for safeguarding both patient safety and organizational resources.
Conclusion
Managing vendor risks is a cornerstone of ensuring patient safety and maintaining operational stability in healthcare. The stakes are high - failing to oversee vendors effectively can lead to financial losses and jeopardize compliance, far outweighing the cost of implementing a structured risk management program.
The Joint Commission provides healthcare organizations with some flexibility in conducting risk assessments, but the fundamental requirements are non-negotiable. These include knowing who enters your facility, verifying the qualifications and performance of non-employees involved in patient care, safeguarding health information, and adhering to infection control standards [1]. While these criteria set a clear foundation, they also allow organizations to tailor risk assessments based on their unique needs.
"Compliance in healthcare is a lot like driving - you're not just responsible for your actions, but also for staying alert to others on the road. A vendor's carelessness can set you back by thousands of dollars and cost you a reputation that's taken years to build." - Amy Andersen, Chief Customer Officer, Verisys Corporation [2]
A well-structured vendor risk program does more than check boxes - it actively protects patient safety, secures sensitive data, and preserves your organization’s reputation. This requires ongoing monitoring, regular evaluations, and tools that provide visibility across your vendor network. With incidents involving downstream entities outnumbering primary victims by over 800% [11], it’s clear that effective vendor oversight must go beyond initial assessments to include continuous evaluation. This disparity highlights the importance of a proactive approach to risk management.
Moving forward, the key lies in combining clear policies, consistent procedures, and technology that supports real-time compliance tracking. By using automated assessments and centralized monitoring, healthcare organizations can not only meet Joint Commission standards but also strengthen their defenses against emerging risks. A strong vendor risk management program is essential for safeguarding patient data, maintaining compliance, and upholding the commitment to delivering quality care.
FAQs
What are the Joint Commission's key standards for managing vendor risks in healthcare?
The Joint Commission has set forth key standards to guide healthcare organizations in managing vendor risks effectively. For instance, EC.02.01.01 emphasizes the importance of verifying vendor credentials to confirm they meet the required qualifications. Meanwhile, EC.02.06.01 calls for conducting risk assessments for high-risk processes at least once every 18 months.
Beyond these standards, healthcare organizations are expected to keep thorough documentation, closely monitor vendor compliance, and ensure that vendors adhere to critical safety, privacy, and infection control protocols. These practices play a crucial role in protecting patient data and staying compliant with regulations while addressing the challenges of third-party risk management.
What steps can healthcare organizations take to identify and prioritize high-risk vendors?
Healthcare organizations can better manage high-risk vendors by conducting detailed risk assessments. These assessments should focus on factors like the vendor's access to sensitive data, their involvement with critical systems, and how their services could affect patient safety. It's also essential to evaluate their compliance history, security measures, and the specific nature of their work.
Leveraging automated vendor risk management tools can make this process more efficient. These tools offer real-time updates on credentialing, compliance status, and possible vulnerabilities. To ensure vendors remain compliant and risks are minimized, organizations should implement regular audits, continuous monitoring, and enforce clear policies around credentialing and training.
What happens if a healthcare organization doesn’t meet the Joint Commission’s vendor risk requirements?
Failing to meet the Joint Commission's vendor risk requirements can lead to serious repercussions for healthcare organizations. These include regulatory fines, loss of accreditation, and greater legal and financial exposure. Beyond these tangible risks, non-compliance can damage the organization’s reputation and put patient safety at risk by increasing the likelihood of sensitive data breaches.
When healthcare providers don't follow these standards, they compromise their ability to deliver safe, quality care and may face major operational challenges. Staying compliant not only safeguards patient information but also reinforces trust and accountability within the healthcare system.


