5 Steps to Launch Phishing Simulations in Hospitals
Post Summary
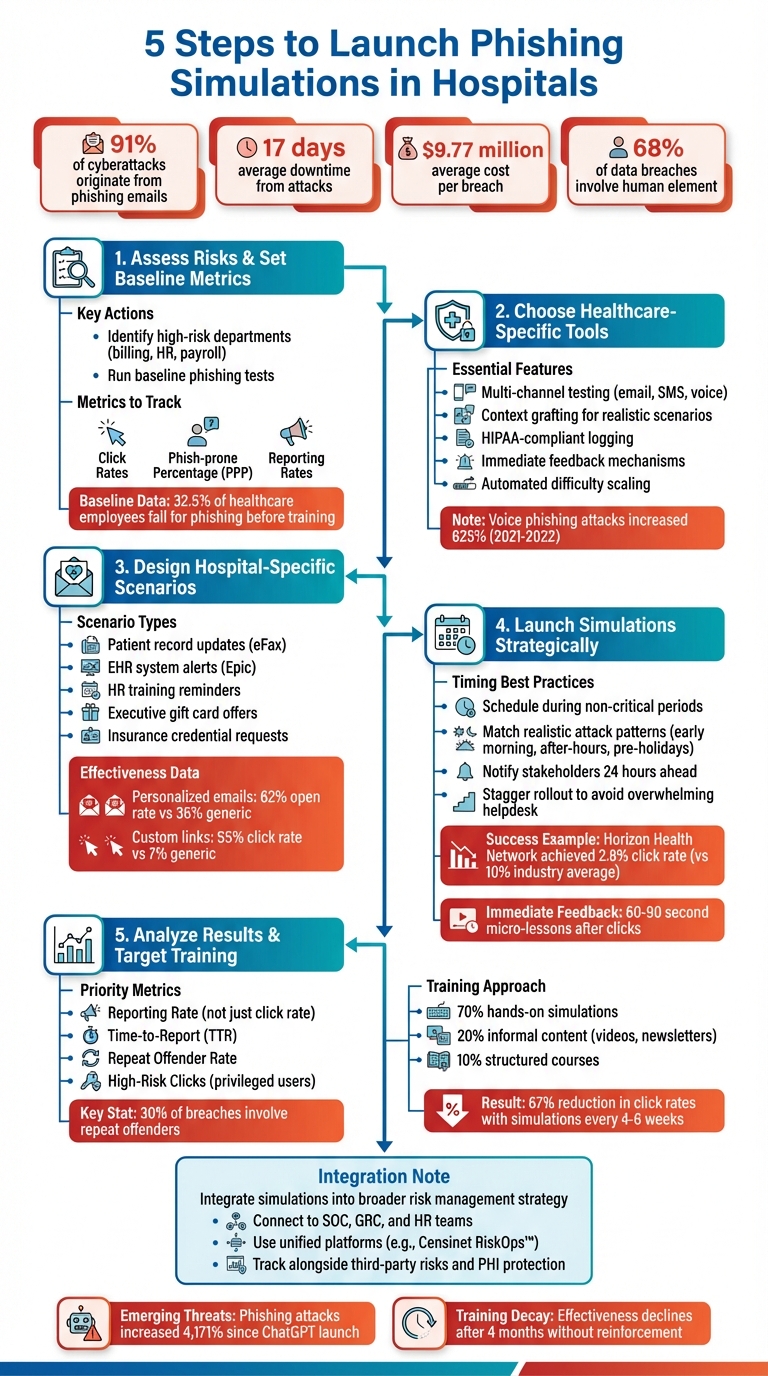
Phishing is a major cybersecurity threat for hospitals, with 91% of all cyberattacks originating from phishing emails. These attacks disrupt patient care, cause significant downtime (averaging 17 days), and lead to breaches costing $9.77 million per incident. Simulations can help hospitals reduce these risks by training staff to recognize and respond to phishing attempts. Here’s a quick overview of the five steps to implement phishing simulations effectively:
-
Assess Risks & Set Baseline Metrics
Identify high-risk departments (e.g., billing, HR) and evaluate current vulnerabilities. Run baseline phishing tests to measure metrics like click rates and reporting rates. -
Choose Healthcare-Specific Tools
Select simulation platforms tailored for hospitals, with features like multi-channel testing, realistic scenarios, and compliance with HIPAA standards. -
Create Hospital-Specific Scenarios
Design phishing emails that mimic real situations, such as fake patient record updates or HR notifications, while avoiding unethical tactics. -
Launch Simulations Strategically
Schedule phishing tests during non-critical periods and align them with realistic attack patterns. Provide immediate feedback to staff after simulations. -
Analyze Results & Target Training
Focus on metrics like reporting rates and time-to-report. Offer personalized training for repeat offenders and reward proactive reporting.
Phishing simulations are most effective when integrated into a hospital’s broader risk management strategy, helping to reduce human error and improve overall security resilience.
5 Steps to Launch Phishing Simulations in Hospitals
How to Automate Better Phishing Simulations with AI
sbb-itb-535baee
Step 1: Assess Current Risks and Set Baseline Metrics
Start by evaluating your hospital's cybersecurity vulnerabilities and measuring what matters for cybersecurity in healthcare. This foundational step helps identify weak points and provides a clear starting point for improvement.
Conduct Vulnerability Assessments
Take a close look at cybersecurity risks across different departments. Teams like billing, HR, payroll, and finance often face higher risks because they manage sensitive financial data and are frequent targets for phishing attacks [10]. Clinical staff, on the other hand, are more likely to encounter phishing attempts that mimic clinical scenarios, leveraging their access to confidential patient records.
The HIPAA Security Rule mandates security awareness training based on a thorough risk assessment [10]. This evaluation should cover both technical gaps - such as phishing emails slipping past spam filters - and human factors like fatigue or heavy workloads, which can compromise adherence to security protocols [8].
"Phishing is versatile, requiring little technical knowledge and most of all use vulnerabilities that are very difficult to patch – those of human behaviour." - Fabio Rizzoni et al., Fondazione Policlinico Gemelli [8]
Once you've identified these vulnerabilities, you can move on to gathering concrete data through baseline testing.
Run Baseline Tests
Next, conduct a phishing simulation in the high-risk areas identified during your assessment. This test will help you gather essential baseline metrics like Phish-prone Percentage (PPP), Click Rates, and Reporting Rates [7]. These metrics offer a snapshot of your hospital's current level of vulnerability to phishing attacks.
Studies show that before training, 32.5% of healthcare employees fell for phishing simulations [10], while around 10% were caught off guard during their first test [9]. Additionally, email filters tend to let through 7% to 10% of phishing emails [7]. These initial metrics are crucial for designing effective training programs and refining your approach in the next stages.
Step 2: Choose Healthcare-Specific Simulation Tools
After establishing your baseline metrics, the next step is selecting a simulation platform tailored to healthcare's unique challenges. Generic phishing tools simply won't suffice. You need a solution designed specifically for healthcare environments, capable of meeting rigorous regulatory standards.
Identify Key Features
A strong platform does more than just email simulations. Look for tools offering multi-channel capabilities - covering SMS, messaging apps, and even voice phishing. These channels are crucial, especially when you consider that voice phishing attacks surged by 625% between early 2021 and mid-2022 [11].
Another must-have is context grafting, which allows the platform to incorporate realistic, hospital-specific details like internal project names, vendor systems, or departmental jargon [12]. This level of realism is vital, as 68% of data breaches involve a human element, such as social engineering or credential theft [12]. Platforms that provide immediate feedback mechanisms - like short training modules triggered right after a failed simulation - turn mistakes into learning opportunities [12][4].
Integration is another key factor. A built-in "Report Phishing" button within your email client can help track Time-to-Report (TTR) metrics and encourage proactive defense behaviors [11][12].
"Phishing testing is a key exercise which strengthens your 'human firewall.'" - Sherri Davidoff, Founder of LMG Security [11]
Advanced platforms often include automated difficulty scaling powered by machine learning. This feature adjusts the complexity of simulations based on individual performance, enabling users to tackle more challenging scenarios as their skills improve [13]. These capabilities not only simulate real-world threats but also prepare your organization to meet compliance standards, setting the stage for the next step.
Ensure Regulatory Compliance
Regulatory compliance is non-negotiable when choosing a simulation tool. Ensure the platform supports HIPAA-compliant logging and encryption to track staff performance and training completion [3]. The HHS Office for Civil Rights (OCR) recognizes phishing simulations and training as "recognized security practices", which can influence their decisions during breach investigations [5].
Your chosen tool should provide features like end-to-end encryption, granular role-based access, and tamper-proof audit logs that are exportable for regulatory reviews. Before finalizing your decision, conduct common healthcare third-party risk assessment questions as part of a thorough vendor security assessment. Request penetration testing results and certifications such as ISO 27001 to confirm the provider adheres to the same high standards you're striving to maintain.
Step 3: Design Hospital-Specific Scenarios
Once you have a healthcare-focused simulation tool in place, the next step is creating scenarios tailored to your hospital's unique environment. These scenarios should mirror the real threats your staff encounters daily. Customization plays a key role here. For instance, a study at Fondazione Policlinico Gemelli, a major Italian hospital with over 6,000 employees, revealed that personalized phishing emails had a 62% open rate compared to 36% for generic ones. Similarly, 55% of employees clicked on custom phishing links, while only 7% fell for standard ones [8].
Create Scenarios Based on Hospital Context
Your simulations should align closely with the workflows and routines of your staff. For example, design emails that appear to be about patient records sent via eFax, urgent updates to the Electronic Health Record (EHR) system (like Epic), or mandatory HR training reminders. These scenarios feel authentic because they reflect the daily operations of a hospital.
"The effectiveness of the message is dependent on the personalization of the message to current, local events"
- Fabio Rizzoni, Data Protection Office, Fondazione Policlinico Gemelli [8]
You can also include scenarios that mimic high-level attacks, like whaling. For instance, simulate emails from executives offering gift cards or health insurers requesting credential verification [3]. Add spoofed login pages to test whether employees verify URLs before entering passwords, and incorporate lessons on the "hover-to-check" technique to inspect links [14].
However, tread carefully with your approach. Ethical boundaries matter. In December 2019, an Italian hospital faced backlash for using a "Christmas bonus" email as bait, which upset staff and had to be stopped. Avoid scenarios that rely on false promises or threats, as these can harm morale and lead to organizational pushback.
"Successful, ethical phishing simulations require coordination across the organization, precise timing and lack of staff awareness"
- Fabio Rizzoni, Data Protection Office, Fondazione Policlinico Gemelli [8]
Once you’ve established these foundational scenarios, broaden your strategy to include simulations that test various phishing channels.
Include Multiple Phishing Types
Modern threats come in many forms, so it’s essential to diversify your simulations. Go beyond email and incorporate smishing (phishing via SMS) and spear phishing, which targets specific individuals or departments with tailored messages. Test your staff's response to malicious attachments that could deliver ransomware, fake login pages designed to harvest credentials, and communications from commonly impersonated entities like parcel delivery services or local restaurants [3][5].
Step 4: Launch Simulations with Proper Timing
After setting up your baseline metrics and selecting the right tools, timing becomes the next critical element. Launching phishing simulations at the wrong moment can disrupt hospital operations, strain helpdesk resources, and even interfere with patient care. But with strategic scheduling, you can ensure your simulations closely mimic real-world threats while respecting the unique workflows of a healthcare environment.
Schedule Simulations Carefully
Timing matters. Avoid launching campaigns during sensitive periods like layoffs, organizational changes, or major crises - times when psychological safety is already under pressure. Work with your Security Operations Center (SOC) to steer clear of peak hours when IT teams are busy managing active threats.
Match simulations to realistic attack patterns. Phishing attempts often happen at specific times, like early mornings, after-hours, or just before holidays. Plan your simulations during these windows but steer clear of critical clinical periods. For instance, you might target finance staff during end-of-quarter cycles or general staff after their shifts. Staggering the rollout of simulations, instead of sending them all at once, can also help avoid overwhelming helpdesk teams and detection systems.
Here’s a real-world example: Horizon Health Network in New Brunswick, which operates 12 hospitals and employs over 14,000 staff and physicians, achieved a phishing click rate of just 2.8% in 2023 - well below the Canadian industry average of over 10% [1]. Their success came from running monthly phishing simulations with predictable timing, minimizing downtime while preparing staff for real threats.
Keep stakeholders informed. Notify department managers and helpdesk teams at least 24 hours before launching a simulation. This heads-up helps them prepare for any spikes in reports or questions. Additionally, ensure that link-scanners and URL rewriters are pre-approved to prevent security tools from auto-clicking links, which could skew your results.
Once your timing is locked in, the next step is delivering feedback that makes an impact.
Provide Immediate Feedback
When someone clicks on a simulated phishing link, it’s a perfect moment to teach. Immediate feedback helps turn a mistake into a learning opportunity while the incident is still fresh in their mind. Redirect users to a landing page that outlines what they missed - like suspicious URLs, urgent language, or unusual requests.
Follow up with a short 60–90-second lesson to reinforce key takeaways. These quick, supportive sessions are highly effective for knowledge retention and help staff recognize similar tactics in the future. For employees who correctly report phishing emails, send instant "thank you" messages or small digital rewards to encourage the behavior.
"Click rate never goes down to zero… and focusing on click rates means we focus on failure. That can be really damaging to psychological safety - people become afraid to report mistakes."
Instead of obsessing over reducing click rates, shift your focus toward encouraging active reporting. Make it easy for employees to report suspicious emails with a simple "Report Phish" button in their email toolbar. Send immediate confirmation when they use it. This kind of real-time feedback is essential, especially since around 30% of data breaches involve repeat offenders within an organization [7].
Step 5: Analyze Results and Provide Targeted Training
Once your simulations are live, the next step is turning all that raw data into meaningful insights. This isn't just about counting who clicked on what - it's about identifying who needs support, which behaviors need improvement, and how fast your team can detect and respond to threats. The ultimate goal? To create a workplace where reporting suspicious emails is second nature, not an environment where people fear making mistakes.
Track Key Metrics
Focus on metrics that encourage active defense rather than those that discourage participation. While click rates are often tracked, they can be misleading - and focusing too much on them might make employees hesitant to report actual errors. Instead, prioritize metrics like:
- Reporting Rate: This shows how many employees are flagging potentially malicious emails. A higher rate indicates a more vigilant team.
- Time-to-Report (TTR): This measures how quickly employees report suspicious emails. Faster reporting limits the time attackers have to exploit vulnerabilities, reducing the risk of breaches.
Consider this: 68% of data breaches involve a human element [12], and email filters miss threats 7–10% of the time [7]. Monitoring repeat offenders is also critical. Employees who fail multiple simulations need personalized coaching rather than public reprimands. Another key metric to track is High-Risk Clicks, particularly among employees with privileged access to sensitive systems like EMRs or pharmacy platforms. These clicks pose the greatest threat to your organization.
To ensure fair evaluations, use tools like the NIST Phish Scale, which adjusts for the difficulty of phishing simulations. For example, failing a sophisticated spear-phishing test isn’t the same as falling for an obvious scam. Segmenting metrics by job roles also helps refine training - what’s a threat to your Finance team might not be relevant to IT admins. This level of detail ensures your training is laser-focused on real-world risks.
Deliver Remediation Training
Once you’ve analyzed the data, it’s time to act. Tailor your training to address specific gaps and turn mistakes into learning opportunities. For instance, if someone clicks on a phishing simulation, provide a 60–90-second micro-lesson immediately. Use landing pages that highlight the exact email they interacted with, complete with annotations showing red flags like suspicious links, urgent requests, or unfamiliar senders.
For employees who repeatedly fail, offer one-on-one coaching sessions. This is especially important because 30% of data breaches involve repeat offenders within the same organization [7]. Personalized support can significantly reduce this risk. To keep training engaging, rotate topics regularly - cover credential theft one month, QR code scams the next, and then move on to voice phishing or attachment safety. Incorporate the 70:20:10 learning model: 70% through hands-on simulations, 20% through informal content like videos and newsletters, and 10% through structured courses [7].
Shift your messaging to encourage reporting rather than focusing solely on avoiding clicks. For example, reward employees who successfully flag phishing attempts with digital badges, thank-you notes, or recognition as "Top Phish Hunters." Positive reinforcement not only builds confidence but also fosters a proactive team culture where employees actively look for threats instead of hiding mistakes.
Integrate Simulations into Your Risk Management Program
Phishing simulations work best when they’re part of your hospital’s larger cybersecurity strategy. Treating them as standalone exercises misses the mark - after all, human error contributes to 68% of data breaches. Instead, connect simulation results to key areas like third-party risk, incident response, and regulatory compliance to maximize their value.
Connect Simulations to Broader Risk Strategies
Tie your phishing simulation results directly into your hospital’s existing risk management processes to strengthen your defenses. Start by aligning your program with teams like the Security Operations Center (SOC), Governance, Risk, and Compliance (GRC), and even HR. This collaboration ensures simulation data feeds into the metrics your leadership already tracks. For example, you can link Time-to-Report (TTR) data with real incident response logs to show how faster reporting by employees can cut down attacker dwell time [6].
Rather than organizing simulation data by department, focus on risk profiles. Different roles face different threats - finance teams managing wire transfers are exposed to risks that differ from those faced by IT administrators handling sensitive medical records. By identifying high-risk roles and tailoring your simulations, you could see a 40% drop in high-risk clicks among privileged users after just two campaigns [12]. Plus, simulation data can support regulatory audits for frameworks like SOC 2, ISO 27001, or HIPAA, proving that your organization is actively working to fortify its “human firewall.”
"Effective programs don't just test awareness. They mirror the complexity of authentic phishing attacks to strengthen the organization's overall human risk posture and build a culture of active defense."
- Adaptive Team, Adaptive Security
Centralizing these insights is key to streamlining risk management and making your efforts more effective.
Use Risk Management Platforms
To simplify and enhance your risk management efforts, consider using a unified platform. Tools like Censinet RiskOps™ bring phishing simulation data together with third-party risk assessments, cybersecurity benchmarks, and other enterprise risk activities. This integration helps you see how human vulnerabilities intersect with risks tied to vendors, devices, and supply chains - all on one dashboard [16]. This visibility is crucial given the economic impact of third-party breaches in the healthcare sector. Instead of juggling multiple tools, you can monitor metrics like Incident Reporting Rate (IRR) and Repeat Offender Rate (ROR) alongside clinical application risks and PHI protection [16].
Take it a step further by deploying a "Report Phishing" button across all devices. This feeds data directly into your SOC, speeding up response times while reinforcing training efforts [6]. Automate follow-ups with micro-training triggered immediately after a failed simulation, turning every mistake into a learning opportunity [6]. This approach transforms simulations from a one-off activity into a continuous, adaptive defense mechanism - ready to tackle emerging threats like AI-driven spear-phishing and deepfake impersonations [12].
Conclusion
Phishing simulations play a key role in safeguarding patient data and ensuring hospital operations remain uninterrupted. With healthcare data breaches projected to cost an average of $9.77 million per incident by 2025 and phishing attacks in the sector rising by 32% [2], these simulations must be treated as an ongoing process rather than a one-time training exercise.
For long-term effectiveness, the focus needs to shift from punitive responses to fostering resilience. Research shows that training effectiveness declines after just four months without reinforcement [18]. Conducting simulations every 4–6 weeks can reduce phishing click rates by as much as 67% [19]. Instead of solely tracking click-through rates, it’s more impactful to measure metrics like Reporting Rate and Time-to-Report. These metrics encourage a security-first mindset where employees feel empowered to report potential threats without fear [2][18]. As phishing tactics evolve, training must adapt to counter new methods and reduce human error.
The threat landscape has grown exponentially, with phishing attacks skyrocketing by 4,171% since the launch of ChatGPT. Attackers now employ advanced techniques like deepfakes, smishing (SMS phishing), and quishing (QR code phishing) to bypass traditional email-focused training [2][17].
To maximize the value of phishing simulations, integrate the insights they provide into your broader risk management strategies. Tools like Censinet RiskOps™ can help connect simulation data with third-party risks, medical device security, and the protection of PHI, while also supporting HIPAA compliance [2]. Aligning simulation results with your SOC and GRC teams ensures these tests contribute actionable intelligence. This approach not only strengthens your organization’s defenses against phishing attacks but also enhances your overall cybersecurity and risk management framework, creating a more resilient and secure environment.
FAQs
How can hospitals run phishing simulations that meet HIPAA requirements?
Hospitals aiming to align phishing simulations with HIPAA guidelines should prioritize staff education through consistent security awareness training. This type of training equips employees to identify phishing attempts and fulfills HIPAA’s mandate for workforce training to safeguard sensitive information like Protected Health Information (PHI).
Simulated phishing exercises should mimic tactics commonly used by attackers. By exposing staff to realistic scenarios, they can practice spotting suspicious emails, misleading links, or urgent requests. These hands-on exercises sharpen detection skills, reducing the likelihood of falling victim to real phishing attacks.
To strengthen compliance, hospitals can leverage tools that automate risk assessments, track vulnerabilities, and document both training sessions and phishing simulations. Maintaining detailed records not only showcases compliance during audits but also helps refine security measures over time.
What are the best practices for designing realistic phishing simulations in hospitals?
To craft effective phishing simulations in hospitals, it's crucial to design scenarios that closely resemble potential cyberattacks without crossing ethical boundaries. Start by using personalized emails that align with staff responsibilities or current hospital events. Including elements like urgency or a sense of trust can help mimic tactics commonly used by attackers. This tailored approach not only captures attention but also creates meaningful learning experiences.
Expand the realism by adopting a multi-channel strategy, such as sending fake emails that appear to come from colleagues or trusted vendors. This helps simulate the variety of methods attackers might use. Keep scenarios fresh by regularly updating them to reflect new and emerging threats, ensuring they remain relevant to the hospital's specific environment.
After each simulation, provide immediate and constructive feedback to participants. This helps staff identify phishing attempts more effectively and reinforces good security practices. These simulations should be integrated into a larger, continuous cybersecurity awareness program to better prepare staff and reduce risks.
How can hospitals evaluate the success of their phishing simulation programs?
Hospitals can measure the effectiveness of their phishing simulation programs by closely monitoring key performance indicators (KPIs) that reflect employee behavior and awareness. These include metrics like the click-through rate on simulated phishing emails, the percentage of employees who report suspicious messages, and how much these numbers improve over time. Tracking these trends can provide valuable insights into how well the program is working.
Other critical factors to evaluate are response times, the accuracy with which phishing attempts are identified, and the percentage of successful reporting. By comparing these results to industry benchmarks, hospitals can pinpoint both strengths and areas needing attention. Regular analysis of these metrics helps ensure the program is building a workforce that’s more alert to security threats and better equipped to minimize the risks of real phishing attacks.


