Lifecycle Management for Third-Party Access in Healthcare
Post Summary
It is the process of managing third-party access to healthcare systems and data, from onboarding to offboarding, to ensure security and compliance.
It protects sensitive patient data, ensures compliance with regulations like HIPAA, and mitigates risks from third-party vendors.
The key phases include onboarding, ongoing monitoring, and offboarding, each with specific activities to manage risks and ensure compliance.
Challenges include ensuring compliance, managing complex vendor relationships, and addressing risks from temporary or high-privilege access.
Best practices include conducting risk assessments, implementing least privilege access, continuous monitoring, and secure offboarding processes.
Organizations can streamline processes by using automated tools like IAM solutions, centralizing documentation, and enforcing strict access controls.
Healthcare organizations face significant challenges with third-party access to critical systems, especially as breaches involving Protected Health Information (PHI) can lead to regulatory penalties, patient safety risks, and reputational damage. Mismanagement of access - such as failing to revoke permissions after contracts end - creates vulnerabilities, particularly in cloud environments where traditional controls often fall short.
Key takeaways:
Adopting structured frameworks like ILM, combined with tools like Censinet RiskOps™, helps healthcare organizations streamline third-party access processes, safeguard PHI, and meet regulatory requirements effectively.
Research Overview: Third-Party Access Management Challenges
Third-Party Data Breaches in Healthcare
Recent industry analyses reveal that third parties and business associates are responsible for a large portion of healthcare data breaches, often involving millions of compromised patient records [4][5]. In some cases, a single vendor-related incident has exposed vast amounts of sensitive information, driving breach costs into the multi-million-dollar range. These costs typically include forensic investigations, legal fees, regulatory penalties, patient notifications, and remediation efforts [4][5].
But the damage isn’t just financial. When a vendor’s systems are breached or rendered inoperable, the ripple effects can directly disrupt patient care. These incidents often draw scrutiny from the Department of Health and Human Services (HHS) and can lead to litigation, further amplifying both financial and reputational harm [4][5]. The underlying issue often stems from fragmented risk management programs, a topic explored further in this research.
Common Weaknesses in Third-Party Risk Programs
A VPAM survey conducted across industries highlighted several recurring challenges in managing third-party access risks. These include weak governance, complex regulatory requirements, insufficient budgets, and a heavy reliance on manual processes [3]. Often, the lack of clear ownership between departments like IT, Legal, and HR leads to inconsistent controls and oversight gaps [3].
Manual processes exacerbate these problems. Many organizations still manage non-employee access using outdated tools like spreadsheets and email workflows. This approach is prone to errors, delays in provisioning access, and the persistence of orphaned accounts long after contracts have ended [2][3][4]. With the HHS placing greater emphasis on business associates’ compliance with HIPAA, having a well-structured third-party risk program is no longer optional - it’s now a regulatory expectation [4].
Identity Lifecycle Management Frameworks
To tackle these challenges, Identity Lifecycle Management (ILM) frameworks have emerged as an effective solution. These frameworks provide a systematic way to manage third-party access, covering every stage from onboarding to deprovisioning. They’re especially critical in healthcare, where the number of non-employee identities - such as contractors, affiliated clinicians, students, temporary staff, and vendor personnel - continues to grow [2]. The rise of external roles like telehealth providers, remote medical coders, biomedical technicians, and cloud support teams has further expanded the attack surface and added complexity to access management [6].
Research indicates that automating lifecycle management processes can significantly reduce the risk of unauthorized access and data breaches [2]. Effective ILM frameworks often incorporate key strategies like role-based access control, zero-trust principles, and continuous monitoring to ensure that third parties only have access to what they need for their specific roles. Additionally, successful implementation relies on centralized governance, with clear roles assigned to IT, Security, Compliance, Procurement, and Clinical leadership [2][3][4].
The 5 Phases of Third-Party Access Lifecycle
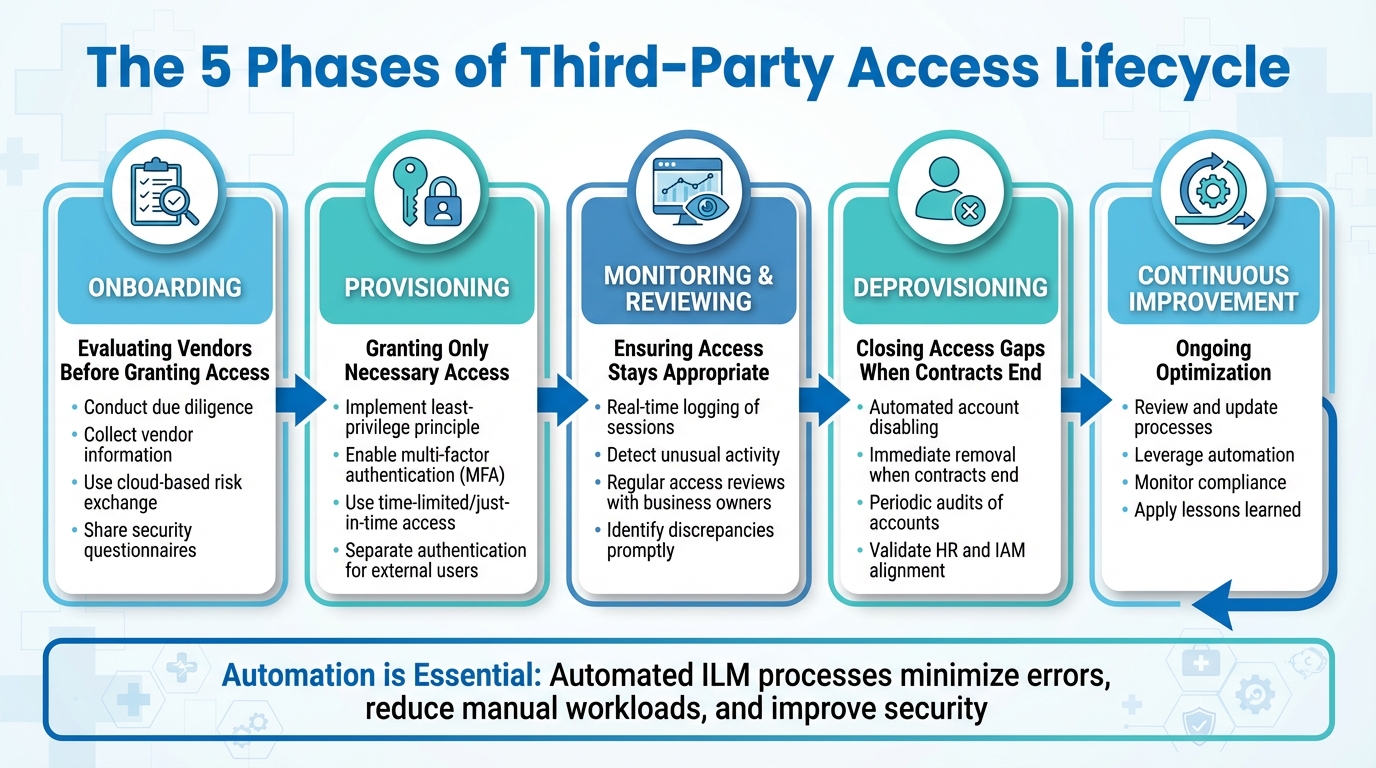
5 Phases of Third-Party Access Lifecycle Management in Healthcare
Managing third-party access in healthcare demands a well-organized process that spans the entire relationship. These phases put the Identity Lifecycle Management (ILM) framework into action, addressing potential vulnerabilities in managing third-party access. When organizations automate lifecycle management for non-employees, they can achieve better security, ensure compliance, and improve operational workflows [2]. The process is divided into five phases, each with its own set of controls and responsibilities.
Onboarding: Evaluating Vendors Before Granting Access
Before granting access to systems or protected health information (PHI), healthcare organizations must thoroughly evaluate third-party vendors. This begins with collecting detailed information and conducting due diligence. Gathering key data upfront allows for smoother automation and better lifecycle management later on [2]. Using a cloud-based risk exchange can simplify this step by enabling vendors to share completed security questionnaires and relevant documentation early in the process [1].
Provisioning: Granting Only Necessary Access
After vetting a vendor, the focus shifts to granting only the minimum access required. Over-permissioning is a common issue, often making third parties attractive targets for cyberattacks. These attackers exploit the challenges of tracking non-employee access and enforcing least-privilege principles [3]. To address this, organizations should implement multi-factor authentication (MFA) and, where necessary, separate authentication systems for external users [3]. For high-risk activities like remote device maintenance or database management, time-limited or just-in-time access should be used, automatically expiring once the task is complete [3]. With proper access levels in place, ongoing monitoring becomes essential.
Monitoring and Reviewing: Ensuring Access Stays Appropriate
Once access is granted, continuous monitoring ensures it remains appropriate over time. Real-time logging of third-party sessions, especially those with elevated privileges, helps detect unusual activity or policy violations before they escalate into major issues [3]. Tower Health, for example, saw significant improvements after adopting Censinet RiskOps™. They increased their risk assessment capacity while reducing the required staff from five full-time employees (FTEs) to just two.
"Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required." – Terry Grogan, CISO, Tower Health
Regular access reviews should involve business owners who can confirm whether third parties still need their current permissions. These reviews also help identify and address any discrepancies promptly [2]. This ongoing oversight naturally leads to timely deprovisioning when contracts end.
Deprovisioning: Closing Access Gaps When Contracts End
The final phase often poses the greatest risk. Without proper controls, manual processes can leave behind orphaned accounts once contracts end, creating significant security vulnerabilities [2]. Automated workflows are essential for disabling vendor accounts immediately when a contract concludes, a statement of work changes, or specific vendor personnel leave or change roles [2]. Clear triggers and controls should guide this process, and periodic audits should validate that HR, contractor, and vendor records align with identity and access management (IAM) systems [2]. Without automation, delays in removing access can leave systems exposed to unauthorized activity.
Managing Third-Party Access in Cloud Environments
Cloud Adoption Trends in Healthcare
Healthcare organizations are increasingly shifting their core systems to the cloud. Major EHR providers like Epic and Cerner/Oracle now offer cloud-hosted platforms, accelerating the transition away from on-premises data centers. Beyond electronic health records, healthcare providers depend on cloud services for telehealth, remote monitoring, medical imaging, and analytics. According to a 2023 HIMSS Analytics study, 88% of healthcare organizations are already using or planning to use cloud services for clinical or business purposes.
This shift has dramatically altered how third-party access is managed. Access now flows primarily through APIs, web portals, and other internet-based services. Research from Saviynt indicates that 40–60% of access identities in healthcare systems are external, including vendors, contractors, affiliates, and students [6]. Each of these connections represents a potential vulnerability, especially when organizations struggle to monitor and manage non-employee access across multiple cloud platforms. This migration to the cloud has fundamentally reshaped the way third-party risks must be addressed.
Cloud-Specific Access Risks
Cloud environments come with their own set of vulnerabilities that differ from traditional on-premises systems. Common issues include misconfigured IAM policies, public storage buckets, over-privileged accounts, weak API security, and insufficient segmentation between tenants [6]. A 2022 study by Ponemon and the Cloud Security Alliance found that 63% of healthcare organizations had experienced at least one security incident involving a cloud service in the prior year, with 45% attributing the incidents to misconfigured cloud storage or IAM policies.
The financial impact of these breaches is staggering. IBM's 2023 Cost of a Data Breach Report revealed that healthcare breaches cost an average of $10.93 million, with 82% involving cloud data. Breaches tied to third-party partners averaged $4.76 million. Additionally, the HIPAA Journal reported that in 2023, 73% of large healthcare data breaches (affecting 500 or more records) involved business associates or third parties, many of which were linked to cloud or hosting providers.
APIs, in particular, present significant risks. Insecure FHIR APIs can expose sensitive patient health information (PHI), while poorly authenticated integrations between EHR systems and vendor portals create opportunities for unauthorized access. Remote support connections, often left active for vendor troubleshooting, can bypass regular security measures. Shared credentials or overly broad permissions further compound the problem, as a single compromised account can provide access to critical clinical systems and patient data across multiple cloud environments. These risks highlight the need for robust, cloud-specific security measures.
Cloud Security Controls for Third-Party Users
To address these risks, healthcare organizations must adopt identity-focused security measures. Federated identity management using SAML or OIDC, combined with multi-factor authentication (MFA) and conditional access, is essential. Just-in-time provisioning, which automatically expires access after a set period, ensures that third-party users don’t retain unnecessary permissions [6]. These practices align with the Zero Trust Architecture principles outlined in NIST SP 800-207, where every session is treated as untrusted and requires continuous verification.
Implementing least-privilege access is critical. Time-bound, just-in-time provisioning, along with OAuth 2.0 configured with proper scopes, mutual TLS, and API gateways, can secure integrations. Cloud Security Posture Management (CSPM) tools are invaluable for identifying misconfigurations, public storage buckets, and overly broad IAM policies before they result in breaches. Continuous monitoring of cloud-native logs, such as AWS CloudTrail and Azure AD logs, enables real-time detection of suspicious third-party activity. Additionally, micro-segmentation can limit lateral movement within the network if credentials are compromised, adding another layer of protection.
sbb-itb-535baee
Regulatory Requirements and Framework Guidance
HIPAA and HITECH Rules for Third-Party Access
Healthcare organizations must navigate strict regulatory requirements when managing third-party access, with HIPAA setting the groundwork. Under HIPAA, organizations are required to establish Business Associate Agreements (BAAs) with vendors who handle protected health information (PHI). These agreements legally bind vendors to protect PHI and limit its use to the purposes outlined in the contract. According to the HIPAA Privacy Rule, business associates include a wide range of entities like cloud service providers, billing companies, IT vendors, and consultants. Before granting access, every vendor relationship must be documented with a signed BAA.
Organizations must also adhere to the "minimum necessary" standard, ensuring that PHI access is limited strictly to what is needed for the task at hand. On top of that, the HIPAA Security Rule requires technical safeguards such as unique user IDs, automatic logoff, encryption, strict access controls, and audit trails. These measures apply to both employees and third-party users.
The HITECH Act expanded HIPAA's reach, making many Security Rule provisions directly applicable to business associates. It also introduced a breach notification rule, which mandates that covered entities and business associates notify affected individuals, the Department of Health and Human Services (HHS), and, in certain cases, the media, following specific PHI breaches. Notably, third-party vendors remain a leading cause of HIPAA-reportable breaches. The consequences of failing to enforce proper BAAs and access controls are evident in cases like the 2019 Touchstone Medical Imaging settlement ($3M) and the 2018 Anthem resolution ($16M).
NIST and HITRUST Framework Recommendations

In addition to HIPAA and HITECH, industry standards from NIST and HITRUST provide further guidance. NIST's publications - such as SP 800-53, 800-66, and 800-161 - outline key controls, including access enforcement (AC-3), least privilege (AC-6), and account management (AC-2). These controls also cover supply chain risk management, ensuring that third-party access is monitored throughout its lifecycle. NIST SP 800-66 Rev. 2 maps HIPAA Security Rule requirements directly to NIST controls, addressing issues like contract clauses, oversight of business associates, shared responsibility models for cloud services, and continuous monitoring.
The HITRUST Common Security Framework (CSF) combines HIPAA, NIST, ISO, and other standards into a certifiable framework widely used in U.S. healthcare. It emphasizes third-party risk management, requiring organizations to conduct due diligence on business associates, enforce access controls, maintain detailed logging, and oversee vendor lifecycles. HITRUST-certified vendors can simplify compliance efforts, as organizations may inherit certain controls - provided they maintain proper governance and monitoring practices. Additionally, NIST SP 800-161 Rev. 1 highlights the importance of managing supply chain and third-party risks throughout the system development lifecycle, particularly for cloud and external service providers.
Governance Models for Access Management
Ensuring compliance with these regulations and frameworks requires robust governance models. Research and industry recommendations stress the importance of centralized governance for managing third-party and non-employee access. Many organizations rely on identity governance and administration (IGA) systems or dedicated third-party risk offices. These governance structures typically involve collaboration across multiple departments, including IT, security, compliance, procurement, HR, and clinical leadership. However, a 2024 study revealed that over 60% of organizations lacked clear roles for managing third-party access, exposing significant governance gaps.
Lifecycle-based governance is a recognized best practice, encompassing onboarding, access modifications, periodic reviews, and deprovisioning. By integrating lifecycle management with procurement and contract controls, organizations can minimize the risk of unauthorized or lingering access. James Case, VP & CISO at Baptist Health, highlighted the value of collaboration in this process:
"Not only did we eliminate spreadsheets, but we also gained a community of hospitals to collaborate with."
This shared approach demonstrates how healthcare organizations can pool resources and insights to strengthen their third-party risk management strategies.
Implementing Research Findings with Censinet RiskOps™

Censinet RiskOps™ transforms research insights and regulatory guidance into actionable strategies, streamlining lifecycle management with targeted tools and features.
Key Features for Effective Risk Management Platforms
Research highlights that manual processes, fragmented controls, and limited resources often undermine third-party risk management. To tackle these issues, an effective risk management platform must offer automated workflows, centralized dashboards, and continuous risk monitoring to stay ahead of potential challenges.[2][3]
How Censinet RiskOps™ Simplifies Lifecycle Management
Censinet RiskOps™ addresses the complexities of third-party access lifecycle management with its cloud-based risk exchange, connecting over 50,000 vendors and products within the healthcare sector. Here's how it works across each phase:
"Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare." – Matt Christensen, Sr. Director GRC, Intermountain Health
Leveraging AI and Automation for Better Access Management
Censinet AI™ enhances third-party risk assessments by speeding up processes like security questionnaires, summarizing evidence, and generating risk reports. This blend of automation and human oversight ensures that critical decisions remain in the hands of skilled teams, while operations scale efficiently.
Think of the platform's AI as "air traffic control" for governance and risk management - it routes key findings and tasks to the right stakeholders for review and approval. Real-time data is displayed on an intuitive dashboard, centralizing all AI-driven risk management activities in one place.
"Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters." – Brian Sterud, CIO, Faith Regional Health
Conclusion
Managing the lifecycle of third-party access in healthcare is not just a technical necessity - it’s a strategic challenge requiring well-researched approaches, teamwork across departments, and tools designed specifically for the job. When done right, structured lifecycle management can strengthen security, ensure HIPAA compliance, and improve overall efficiency.[2]
However, many organizations still struggle with outdated manual processes and fragmented controls. These inefficiencies can leave the door open to unauthorized access and compliance risks, even when vendor risk tools are in place.[3] To truly address these challenges, third-party access lifecycle management must be treated as an organization-wide initiative, backed by leadership across security, compliance, and clinical teams.
Platforms like Censinet RiskOps™ bring these strategies to life by offering healthcare-specific solutions tailored to the industry’s unique demands. From safeguarding PHI to integrating with clinical systems, Censinet RiskOps™ simplifies complex processes. For example, Tower Health demonstrated the platform’s impact: it enabled three employees to return to their primary roles while increasing the number of risk assessments conducted - all with fewer full-time resources.[1]
Looking ahead, U.S. healthcare leaders need to adopt a structured approach to lifecycle management. This includes key phases like risk-based onboarding, least-privilege provisioning, continuous monitoring, and timely deprovisioning. Scalable automation and expert oversight are essential to making this approach work. Tools like Censinet AI™ enhance these efforts by streamlining processes while keeping expert risk teams in control, ensuring findings are routed to the right stakeholders for review and action. By combining research-driven strategies with practical tools, healthcare organizations can turn third-party access management into a powerful strategic asset.
FAQs
How does managing the lifecycle of third-party access improve security in healthcare?
Effective management of third-party access throughout its lifecycle plays a critical role in boosting security within healthcare. By keeping a close eye on access permissions - regularly updating them and promptly revoking them when they're no longer necessary - organizations can significantly lower the chances of outdated or excessive access leading to data breaches or compliance issues.
Streamlining risk assessments and automating essential processes makes this approach even more effective. It helps healthcare providers stay aligned with security standards, reduce potential vulnerabilities, and safeguard sensitive patient information, such as PHI and clinical data. At the same time, it strengthens overall security measures and eases the administrative workload.
What are the key challenges of managing third-party access in cloud-based healthcare systems?
Managing third-party access in cloud-based healthcare systems is no small task. It involves tackling several hurdles, such as maintaining consistent security and compliance, keeping a clear view of third-party activities, and handling ever-changing access permissions as roles and needs evolve.
Healthcare organizations also have distinct concerns to address. These include safeguarding sensitive patient information and Protected Health Information (PHI), weaving risk assessments seamlessly into everyday workflows, and staying aligned with the latest cloud security standards. Successfully navigating these challenges is essential to protecting operational stability and maintaining the trust of patients.
Why is automation essential for managing third-party access in healthcare?
Automation plays a key role in managing third-party access in healthcare, ensuring that updates to user access are handled with both precision and speed. By cutting down on manual tasks, automation reduces the likelihood of errors while bolstering security measures and compliance efforts.
With automation, healthcare organizations can swiftly modify or revoke access as needed, making sure that only authorized individuals can access sensitive patient information, clinical applications, and other vital systems. This approach not only lowers potential risks but also helps meet stringent regulatory standards.
Related Blog Posts
- Remote Access Vulnerabilities: Why 48% of 2024 Data Breaches Came Through Third-party Connections
- Beyond Vetting: Continuous Monitoring Strategies for Third-party Risk Management Excellence
- Third-Party IAM Challenges in Healthcare
- TPRM Technology Stack for Healthcare: Tools, Platforms, and Integration Strategies
{"@context":"https://schema.org","@type":"FAQPage","mainEntity":[{"@type":"Question","name":"How does managing the lifecycle of third-party access improve security in healthcare?","acceptedAnswer":{"@type":"Answer","text":"<p>Effective management of third-party access throughout its lifecycle plays a critical role in boosting security within healthcare. By keeping a close eye on access permissions - regularly updating them and promptly revoking them when they're no longer necessary - organizations can significantly lower the chances of outdated or excessive access leading to data breaches or compliance issues.</p> <p>Streamlining risk assessments and automating essential processes makes this approach even more effective. It helps healthcare providers stay aligned with security standards, reduce potential vulnerabilities, and safeguard sensitive patient information, such as PHI and clinical data. At the same time, it strengthens overall security measures and eases the administrative workload.</p>"}},{"@type":"Question","name":"What are the key challenges of managing third-party access in cloud-based healthcare systems?","acceptedAnswer":{"@type":"Answer","text":"<p>Managing third-party access in cloud-based healthcare systems is no small task. It involves tackling several hurdles, such as maintaining <strong>consistent security and compliance</strong>, keeping a clear view of third-party activities, and handling ever-changing access permissions as roles and needs evolve.</p> <p>Healthcare organizations also have distinct concerns to address. These include safeguarding sensitive patient information and Protected Health Information (PHI), weaving risk assessments seamlessly into everyday workflows, and staying aligned with the latest cloud security standards. Successfully navigating these challenges is essential to protecting operational stability and maintaining the trust of patients.</p>"}},{"@type":"Question","name":"Why is automation essential for managing third-party access in healthcare?","acceptedAnswer":{"@type":"Answer","text":"<p>Automation plays a key role in managing third-party access in healthcare, ensuring that updates to user access are handled with both precision and speed. By cutting down on manual tasks, automation reduces the likelihood of errors while bolstering security measures and compliance efforts.</p> <p>With automation, healthcare organizations can swiftly modify or revoke access as needed, making sure that only authorized individuals can access sensitive patient information, clinical applications, and other vital systems. This approach not only lowers potential risks but also helps meet stringent regulatory standards.</p>"}}]}
Key Points:
What is third-party access lifecycle management in healthcare?
Definition: Third-party access lifecycle management refers to the structured process of managing how external vendors, contractors, and business associates access healthcare systems and sensitive data. It encompasses onboarding, monitoring, and offboarding to ensure security, compliance, and operational efficiency.
Why is third-party access management important in healthcare?
Importance:
- Protects sensitive patient data, including PHI, from unauthorized access and breaches.
- Ensures compliance with regulations like HIPAA, which mandate secure third-party relationships.
- Mitigates risks associated with third-party vendors, such as insider threats and cyberattacks.
- Maintains operational continuity by ensuring vendors meet security and performance standards.
What are the key phases of third-party access lifecycle management?
Phases:
- Onboarding: Includes risk assessments, due diligence, and secure credentialing to establish a foundation for the vendor relationship.
- Ongoing Monitoring: Involves continuous risk assessments, performance monitoring, and compliance checks to address evolving risks.
- Offboarding: Ensures secure termination of access, retrieval or destruction of sensitive data, and proper documentation of the relationship's closure.
What are the challenges of managing third-party access in healthcare?
Challenges:
- Compliance Complexity: Ensuring vendors meet HIPAA and other regulatory requirements.
- High-Privilege Access Risks: Managing temporary or privileged access without compromising security.
- Vendor Oversight: Monitoring multiple vendors with varying risk profiles and access needs.
- Data Breach Risks: Addressing vulnerabilities introduced by third-party systems or personnel.
What are the best practices for third-party access lifecycle management?
Best Practices:
- Conduct comprehensive risk assessments during onboarding to identify potential vulnerabilities.
- Implement least privilege access to limit vendor access to only what is necessary.
- Use continuous monitoring tools to track vendor activity and detect anomalies.
- Develop clear contractual agreements that outline security responsibilities and breach notification protocols.
- Ensure secure offboarding processes to revoke access and retrieve or destroy sensitive data.
How can healthcare organizations streamline third-party access management?
Streamlining Strategies:
- Use Identity and Access Management (IAM) solutions to automate onboarding, monitoring, and offboarding.
- Centralize documentation, including contracts, risk assessments, and access logs, for easier management.
- Train staff on third-party risk management best practices and compliance requirements.
- Leverage tools like Censinet RiskOps™ to simplify vendor risk assessments and lifecycle management.


