Long-Term Care Facility Vendor Risk Management: Resident Safety and Regulatory Compliance
Post Summary
Vendor risk management (VRM) is critical for long-term care facilities to protect resident safety and meet regulatory requirements. It ensures that third-party vendors like IT providers, medical suppliers, and staffing agencies comply with HIPAA and CMS guidelines while safeguarding sensitive data and critical systems. Neglecting vendor oversight can lead to legal penalties, compromised care, and reputational damage.
Key Takeaways:
- Risks to Resident Safety: Cybersecurity breaches, flawed data, and service disruptions can directly harm residents.
- Regulations: HIPAA and CMS rules require facilities to monitor vendor compliance with data security, care standards, and emergency preparedness.
- Risk Categories: Focus on cybersecurity, privacy, clinical quality, and business continuity when assessing vendors.
- Consequences: Data breaches and poor oversight can cost millions, trigger CMS citations, and erode trust.
- Action Steps: Establish governance, maintain a vendor inventory, conduct risk assessments, and enforce strong contracts and SLAs.
By embedding VRM into daily operations, using tools like automation for efficiency, and regularly evaluating vendors, facilities can mitigate risks, protect residents, and maintain compliance.
Regulations and Risk Areas for Vendor Management in Long-Term Care
Vendor Risk Management Statistics: Data Breaches and Compliance in Long-Term Care Facilities
U.S. Regulations That Govern Vendor Risk Management
Long-term care facilities operate under a web of federal and state regulations when it comes to managing vendor relationships. One key regulation is HIPAA, which mandates that third-party business associates adhere to the same stringent data protection standards as the facilities they serve. This means your facility must actively ensure that vendors are meeting compliance requirements [1].
Another critical regulation is outlined in the CMS Conditions of Participation (42 CFR Part 483). These rules require facilities to oversee third-party services that impact resident rights, quality of care, infection control, emergency preparedness, and overall compliance. On top of that, state health departments may enforce additional location-specific rules [3][1]. Knowing and understanding these regulatory frameworks is essential for identifying and addressing vendor risks effectively.
Critical Risk Categories for LTCF Vendors
Regulatory compliance is just the starting point. To truly safeguard resident care, facilities need to dive deeper into vendor risk assessments. Vendors should be evaluated across four main risk categories: cybersecurity, privacy, clinical quality, and business continuity.
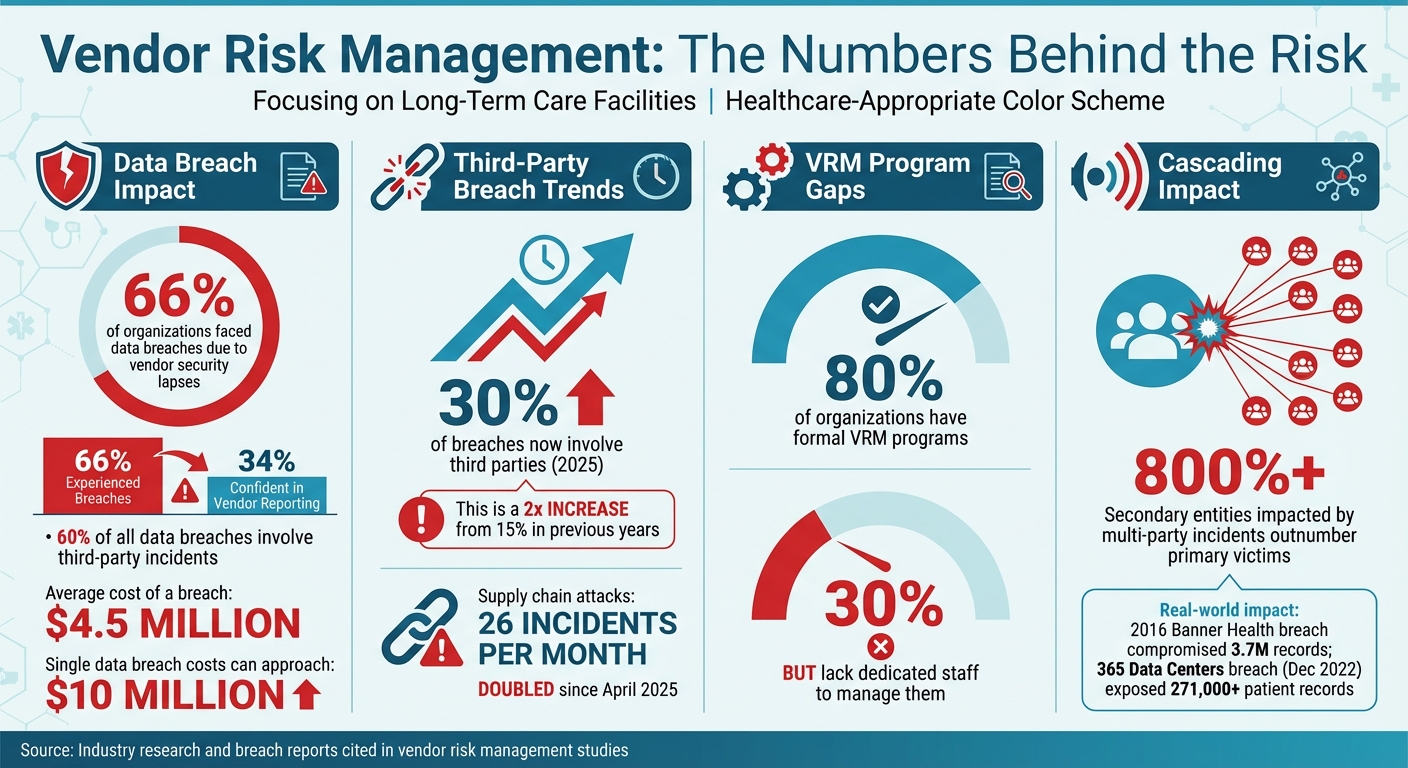
- Cybersecurity Risks: These are top-of-mind for most facilities. Consider this: 66% of organizations have faced data breaches due to vendor security lapses, yet only 34% were confident that vendors would report breaches promptly [4]. This gap highlights the importance of vetting vendor security measures.
- Privacy Risks: Vendors that handle Protected Health Information (PHI) must have robust safeguards in place. Any mishandling of sensitive data could lead to serious compliance issues.
- Clinical Quality Risks: Vendors providing services that directly affect resident care - such as consultant pharmacists, medical equipment suppliers, or electronic health record (EHR) systems - introduce unique risks. For example, flawed data from these sources could lead to poor clinical decisions, putting residents at risk.
- Business Continuity Risks: Can your facility continue operations if a vendor faces disruptions? This is a crucial question, especially when system outages or service interruptions could severely impact resident care [1].
To manage these risks, facilities should assign vendors to specific risk tiers. Factors like the type of data accessed, the level of system access, the financial impact of potential breaches, and the overall effect on operations should guide this process. For instance, the risks posed by a dietary services vendor differ significantly from those of an EHR provider, and your oversight should reflect these differences.
Penalties and Consequences of Poor Vendor Oversight
Failing to properly oversee vendors can lead to severe consequences - not just for operations but also for compliance and reputation. The financial fallout of a single data breach can be staggering, with costs approaching $10 million. This doesn’t even account for legal actions or the lasting damage to your facility’s reputation. A real-world example is the 2016 Banner Health breach, where a third-party payment processor’s failure compromised 3.7 million records, resulting in a costly settlement [1].
Beyond financial penalties, facilities risk citations from CMS. These range from standard deficiencies to Immediate Jeopardy - the most severe category, issued when residents face serious harm, injury, or even death. Vendor-related failures, such as inadequate medication monitoring or missed follow-up labs, have triggered Immediate Jeopardy citations in the past [5]. Such citations can lead to termination from Medicare and Medicaid programs, effectively shutting down a facility.
The damage doesn’t stop there. Poor vendor oversight erodes trust among residents and their families, tarnishes your facility’s reputation within the community, and invites heightened scrutiny from regulators. The stakes couldn’t be higher, making robust vendor management a non-negotiable priority.
How to Build a Vendor Risk Management Program
Setting Up Governance and Vendor Inventory
Start by establishing clear governance across departments. Assign roles to key areas such as executive leadership, legal, compliance, IT, and procurement to oversee vendor risk management (VRM) [1]. This collaborative approach ensures all potential risk areas are accounted for.
Once governance is in place, create a detailed vendor inventory. While nearly 80% of organizations have formal VRM programs, 30% still lack dedicated staff to manage them [7]. Your inventory should include every vendor with access to your facility - this means not just major partners like EHR providers and medical equipment suppliers, but also smaller contractors like cleaning services, document shredding companies, landscapers, and caterers [7]. Even vendors that seem low-risk can pose threats if they have access to sensitive data, files, or physical spaces.
Next, conduct a facility-wide risk assessment to identify high-risk areas across all departments. Pay special attention to risks related to patient privacy, cybersecurity, physical security, data storage, and communication systems [1]. This comprehensive understanding will help you prioritize which vendor relationships require the most attention.
With governance established and a complete vendor list in hand, you can move on to performing risk assessments and due diligence.
Conducting Due Diligence and Risk Assessments
Effective due diligence involves evaluating both the vendor as an organization and the specific products or services they provide [7]. Establish clear evaluation criteria to assess and score risks, using scales like low/medium/high or numerical rankings [7]. You may want to weigh certain categories more heavily depending on your facility's priorities. For example, if your organization handles sensitive patient data, privacy risks should take precedence over operational risks.
Use prior risk assessments to classify vendors into tiers based on factors like data sensitivity, access levels, and operational impact [1]. This tiering system will guide the depth of due diligence needed. For instance, a low-risk vendor might only require a basic financial review, while a high-risk vendor may need extensive background checks and security audits [7].
Form a diverse risk assessment team with members from Compliance, Finance, Security, IT, Legal, and ESG [7]. Their combined expertise ensures a thorough evaluation, uncovering risks that might otherwise go unnoticed. During onboarding, request and verify key documentation such as cybersecurity certifications, insurance policies, credit reports, and operational details [1]. The December 2022 breach at 365 Data Centers, which exposed medical information for over 271,000 patients of Avem Health Partners, underscores the importance of vetting vendor security practices [7].
For each approved vendor, develop a tailored risk management plan. This plan should outline potential risk scenarios, assign specific tasks and responsibilities, and detail mitigation strategies like regular monitoring or annual in-depth reviews [7]. Keep in mind that secondary entities impacted by multi-party incidents often outnumber primary victims by more than 800% [7], so it’s crucial to assess risks posed by your vendors' subcontractors as well.
Once the due diligence process is complete, incorporate these standards into vendor contracts and service-level agreements (SLAs).
Creating Contracts, SLAs, and Security Requirements
Vendor contracts should include clear security and compliance requirements to safeguard resident care. These agreements must outline accountability standards, policies, and procedures for vendors [8]. Address data security and patient privacy explicitly, and include confidentiality clauses to prevent the sharing of trade secrets [8].
For vendors handling Protected Health Information (PHI), HIPAA requires Business Associate Agreements. Contracts should also specify the necessary documentation, such as proof of licensing, equipment certifications, and staff qualifications [8]. Include oversight mechanisms to monitor vendor performance, disciplinary measures for non-compliance, and clear termination clauses [8]. Additionally, contracts should detail how vendors will identify and address security breaches, ensuring alignment with your facility’s compliance and ethics program [3].
Service Level Agreements (SLAs) should define performance expectations and metrics for all services, guaranteeing they meet the standards required for resident safety and regulatory compliance. For subcontractors, standardize agreements to include minimum liability coverage, bonding thresholds, risk management protocols, and safety procedures [6]. Always have legal counsel review all vendor management documents and contracts to ensure your facility is adequately protected [8].
Managing Cybersecurity Risks with Vendors
Assessing Vendor Cybersecurity Practices
When working with vendors, it's essential to evaluate how they protect your data and systems. Key areas to assess include data encryption (both for stored and transmitted information), access controls like multi-factor authentication, and vulnerability management processes - covering everything from system patching to security testing and addressing weaknesses.
Ask vendors to provide cybersecurity certifications and SOC reports, especially those handling sensitive data like Protected Health Information (PHI). It's worth noting that third-party incidents account for about 60% of all data breaches, with the average cost of a breach nearing $4.5 million [9]. According to the 2025 Verizon Data Breach Investigations Report, 30% of breaches now involve third parties, a sharp increase from 15% in previous years [10].
Also, consider the growing reliance on third-party and open-source code in vendor software. Supply chain attacks have doubled since April 2025, now averaging 26 incidents per month [10]. To mitigate these risks, request a Software Bill of Materials (SBOM) from vendors. This document helps you track all the software components they use, including any fourth-party dependencies that might introduce hidden vulnerabilities. Such evaluations are critical for preparing collaborative incident response plans with vendors.
Coordinating Incident Response with Vendors
Even if a breach originates within a vendor's system, your organization is ultimately responsible for the fallout. As AP Healthcare emphasizes, "The facility, not the vendor, is ultimately responsible for breaches" [2]. This underscores the need for close collaboration with vendors when planning for incident response, as quick action is vital to safeguarding resident safety.
Incorporate vendors into your incident response plans with clear protocols for breach notifications, communication channels, and recovery procedures. Review each vendor's Incident Response Plan to understand their communication workflows, responsibilities, and available resources for addressing security incidents [9].
Additionally, work with your insurance and risk management teams to ensure your cyber liability coverage aligns with potential risks. This includes revisiting contractual agreements with vendors, especially when adopting new technologies or services [2]. Assign a specific team member to manage vendor relationships during incidents, ensuring consistent communication and accountability [9]. After a security event, conduct a thorough review with the vendor to identify lessons learned and confirm that vulnerabilities have been addressed. Coordinated response protocols are crucial for maintaining operations and supporting broader business continuity objectives.
Ensuring Business Continuity and Disaster Recovery
Vendor disruptions pose a direct risk to resident safety and the delivery of care. During your due diligence process, request and evaluate vendors' business continuity and disaster recovery (BC/DR) plans [11]. Prioritize vendors by their importance to your operations - Tier 1 vendors, being the most critical, should undergo the most rigorous review of their BC/DR capabilities [9][11].
Service Level Agreements (SLAs) should clearly define uptime, availability standards, and incident response times, reflecting the vendor's commitment to ensuring continuity [9]. Confirm that vendors maintain system redundancy, perform regular backups, and have tested recovery processes in place.
Keep a close eye on your entire vendor supply chain to track all entities with access to sensitive data [9]. This comprehensive oversight helps you identify dependencies that could lead to cascading service interruptions, potentially impacting resident care. Regularly test vendors' recovery capabilities to ensure they can restore critical services within timelines that protect both resident safety and regulatory compliance. Strong continuity planning is essential for maintaining seamless care delivery and achieving broader risk management goals.
sbb-itb-535baee
Implementing Vendor Risk Management in Daily Operations
Integrating VRM Into Facility Workflows
Vendor risk management works best when it’s built into your everyday processes rather than treated as a standalone task. Start by embedding vendor assessments into your procurement workflow. For example, require vendors to complete security questionnaires and provide necessary documentation before signing any contracts. This proactive step ensures that only vetted vendors gain access to your systems and sensitive resident data.
Keep all vendor documents and risk assessments in a centralized repository. This shared access keeps everyone - from IT to procurement - on the same page about vendor status and potential risks. Transparency like this helps teams collaborate more effectively.
Assign clear responsibilities for managing vendor relationships across departments. For instance, your IT team might focus on technical evaluations, while procurement handles contract negotiations and compliance checks. Regular cross-department meetings are essential for clarifying roles and addressing any issues quickly.
By integrating vendor risk management into your workflows, you create a foundation for ongoing performance tracking and program improvements. The next step? Measuring your program’s effectiveness and refining it as you go.
Tracking Performance and Improving Your Program
To gauge how well your vendor risk management program is working, focus on measurable metrics. Track things like how many vendor assessments are completed, how long it takes to onboard new vendors, and the percentage of vendors meeting your security standards. Additionally, monitor incidents or breaches involving vendors and how quickly your team resolves them. These insights can highlight strengths and pinpoint areas for improvement.
Conduct quarterly reviews of your vendor portfolio to reassess risk levels, especially for vendors handling sensitive data or supporting critical care systems. Annual audits are also crucial - they help identify gaps in your processes and ensure you’re staying aligned with changing regulations. Regular reviews and audits not only enhance compliance but also reinforce resident safety.
When vendor-related incidents or near-misses occur, use them as learning opportunities. Update your policies based on these experiences and gather input from staff who work closely with vendors. Their feedback can help refine your selection criteria and monitoring practices.
As you work to improve your program, consider tools that can make these processes more efficient.
Using Automation and AI Tools Safely
Manually managing vendor risk assessments with spreadsheets can be overwhelming and difficult to scale. Automation can take over repetitive tasks like assessments, document reviews, and compliance tracking, freeing your team to focus on strategic decisions.
Platforms like Censinet RiskOps™ simplify third-party risk assessments while maintaining high safety standards. Similarly, Censinet AITM™ speeds up the entire assessment process. It allows vendors to complete security questionnaires in seconds, summarizes evidence and documentation automatically, captures details about product integrations and fourth-party risks, and generates comprehensive risk reports.
Even with automation, human oversight is essential. Tools like Censinet AITM use a human-guided approach, where risk teams set rules and review critical findings. For example, significant risks or tasks can be routed to an AI governance committee for further review. This structured process ensures automation supports decision-making rather than replacing it. Think of it as an "air traffic control" system, helping your facility scale vendor risk management while protecting resident safety and care delivery integrity.
Conclusion
Managing vendor risks is a crucial part of ensuring the safety of residents and meeting regulatory requirements. According to 42 CFR Part 483, skilled nursing facilities are required to maintain a compliance and ethics program capable of identifying and addressing criminal, civil, and administrative violations[3]. This responsibility extends to all vendor relationships, whether they involve food services, IT systems, or other essential services.
The stakes are high. Data shows that inadequate vendor oversight can lead to serious consequences, including deficiencies during CMS surveys, disruptions in operations that jeopardize care delivery, and, most importantly, harm to residents. Failing to properly manage vendor risks not only exposes facilities to regulatory penalties but also compromises the safety and well-being of those in their care.
To address these challenges, facilities need robust risk management strategies. This means fostering a culture of accountability throughout the organization. Strong governance, detailed due diligence, and a focus on cybersecurity are key components. Incorporating vendor oversight into everyday operations - supported by scalable automation and thoughtful human review - helps ensure risks are managed effectively.
The most successful facilities view vendor risk management as an ongoing effort. Regular evaluations, continuous monitoring, and open communication with vendors form the backbone of a strong risk management framework. By committing to this process, facilities can safeguard residents, maintain compliance, and ensure the consistent delivery of high-quality care.
FAQs
What are the best ways for long-term care facilities to assess vendor cybersecurity risks?
Long-term care facilities can tackle vendor cybersecurity risks by using a strategic, proactive approach that emphasizes safety and compliance. A good starting point is conducting regular risk assessments with established frameworks like NIST or HITRUST. These provide clear, structured guidelines to help identify and evaluate potential vulnerabilities in vendor practices.
Incorporating automated monitoring tools is another smart move. These tools continuously track security activities, catching issues in real time, which minimizes manual errors and allows for quicker responses to threats. Beyond that, independently verifying the information vendors provide ensures its accuracy and strengthens confidence in their cybersecurity efforts.
By weaving these practices into your vendor risk management program, you can safeguard sensitive data, protect residents, and stay aligned with healthcare regulations.
What are the risks of not properly managing vendors in long-term care facilities?
Failing to effectively manage vendors in long-term care facilities can lead to some serious problems. These include risks to resident safety, potential violations of healthcare regulations, and even data breaches. Such issues can bring about legal troubles, hefty fines, and disruptions to daily operations - all of which can tarnish your facility's reputation.
Ignoring vendor risk management also opens the door to heightened third-party risks, like falling short of industry standards or weak cybersecurity measures. Taking a proactive approach to these challenges is essential for maintaining trust, keeping operations running smoothly, and protecting the residents' well-being.
How do automation tools enhance vendor risk management in healthcare facilities?
Automation tools play a key role in simplifying vendor risk management within healthcare. They cut down on tedious manual tasks and help reduce the likelihood of mistakes. These tools also make it easier to validate vendor responses, keep an eye on potential risks continuously, and facilitate faster collaboration with vendors.
By making these processes more efficient, automation enhances precision, improves workflow efficiency, and enables real-time risk identification and response. This not only supports regulatory compliance but also helps ensure the safety of patients and residents.


