How to Meet 60-Day Breach Notification Requirements
Post Summary
When a healthcare organization discovers a breach involving Protected Health Information (PHI), the clock starts ticking. Under the HIPAA Breach Notification Rule, you must notify affected individuals within 60 calendar days of discovering the breach. Here’s what you need to know:
- What qualifies as a breach? Any unauthorized access, use, or disclosure of unsecured PHI that compromises its security or privacy.
- When does the 60-day clock start? From the date the breach is discovered - or should have been discovered through reasonable diligence.
- What happens if you miss the deadline? Penalties range from $137 to $68,928 per violation, with potential fines reaching millions for systemic failures.
To stay compliant:
- Act quickly to assess and contain the breach.
- Conduct a risk assessment to determine if notification is necessary.
- Notify individuals, HHS, and possibly the media if 500+ people are affected.
Preparation is key. Assign clear roles, create a response plan, and use centralized tools to track deadlines and streamline notifications. Remember, waiting until day 60 can still result in violations if delays are deemed unnecessary.
Steps to Meet the 60-Day Notification Deadline
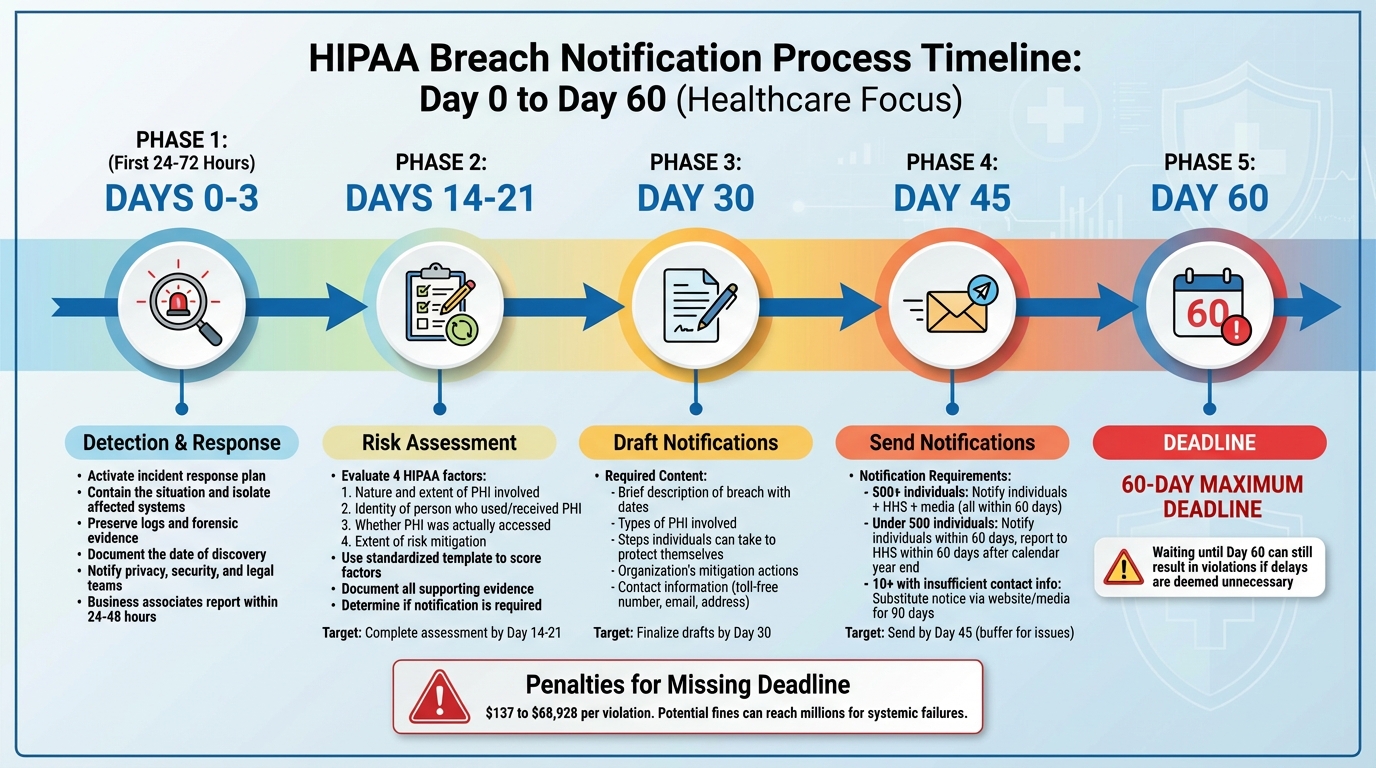
60-Day HIPAA Breach Notification Timeline and Process
Meeting the 60-day deadline for notifications requires a well-organized approach from the moment an incident is detected. It's important to act promptly - HIPAA’s requirement to notify "without unreasonable delay" means that unnecessary holdups, even within the 60-day timeframe, could lead to compliance issues [4]. Below is a breakdown of the essential steps to follow, from initial detection to sending out notifications.
Detecting and Responding to the Incident
The first 24 to 72 hours after detecting a potential incident are crucial. As soon as you identify an issue - whether through internal monitoring, an employee report, or a vendor alert - activate your incident response plan [6][11]. The immediate focus should be on containing the situation: isolate affected systems to prevent further damage, preserve logs and forensic evidence, and notify your privacy, security, and legal teams. At this stage, it’s equally important to document the date of discovery. This involves recording the initial alert, the source of the report, the individuals involved in the initial triage, and when management confirmed the incident [5][6].
If business associates are involved, they often have contractual obligations to report incidents quickly - typically within 24 to 48 hours [2][6][8].
Performing a Breach Risk Assessment
Once the incident is contained and initial data is gathered, the next step is to assess whether notification is required. HIPAA outlines four key factors to evaluate:
- The nature and extent of the PHI involved, including the likelihood of re-identification.
- The identity of the person who used or received the PHI.
- Whether the PHI was actually accessed or acquired.
- The extent to which any risks have been mitigated [6].
Using a standardized template can help you score these factors consistently. Document all supporting evidence, such as access logs, encryption status, or proof that a misdirected message was recovered and destroyed. If your analysis shows a low probability of compromise, notification may not be necessary. However, if the findings suggest otherwise, the incident is presumed to be a reportable breach, triggering the 60-day notification requirement [1][6].
For example, a misdirected fax sent to a known healthcare provider who immediately confirms destruction of the document might not require notification. On the other hand, a ransomware attack involving unauthorized access to a database containing PHI is likely reportable, requiring notifications to individuals, the Department of Health and Human Services (HHS), and possibly the media within 60 days [1][6][8]. Similarly, a lost laptop that is encrypted and password-protected may not meet the criteria for a breach of unsecured PHI [6].
If the breach is deemed reportable, the focus should shift to preparing notifications without delay.
Preparing and Sending Required Notifications
Drafting notifications should begin as soon as possible, even as the investigation continues. Individual notices must be clear and straightforward, including:
- A brief description of the breach, with dates of occurrence and discovery.
- The types of PHI involved.
- Steps individuals can take to protect themselves.
- Details on what your organization is doing to investigate and mitigate harm.
- Clear contact information, such as a toll-free number, email, and mailing address [2][6][9].
The notification process varies depending on the number of individuals affected:
- Breaches involving 500 or more individuals: Notify affected individuals, submit a report to HHS via its online breach portal, and inform prominent media outlets serving the impacted area - all within 60 days of discovery [1][2][6].
- Breaches involving fewer than 500 individuals: Notify affected individuals within 60 days, log these events, and report them to HHS no later than 60 days after the end of the calendar year in which they were discovered [1][2][5].
- Insufficient contact information: If you don’t have valid contact information for 10 or more individuals, you’ll need to provide substitute notice. This can include posting on your website or using major print or broadcast media for at least 90 days, along with a toll-free number [2][9].
To streamline the process, use pre-approved templates with editable fields for incident-specific details and credit monitoring offers. Route drafts efficiently through privacy, security, and legal teams for review [1][2]. Establish internal milestones to avoid delays - aim for a risk assessment by days 14–21, finalize drafts by day 30, and send notifications by day 45, leaving a buffer for unforeseen issues [1][5][8].
How to Streamline Your Breach Notification Process
Healthcare organizations often face challenges with fragmented and inconsistent processes that slow down breach notifications. The Department of Health and Human Services (HHS) requires prompt reporting, and waiting until day 60 is not acceptable if details are available earlier [4]. Streamlining your breach notification process involves minimizing the time between detection, assessment, and notification. To address these delays, having clearly defined roles and a well-prepared playbook is crucial.
Assign Clear Roles and Create Response Playbooks
Appoint a Breach Response Lead - typically the Privacy Officer or Chief Information Security Officer - who oversees timelines and ensures quick decision-making [6]. Assign specific responsibilities to key teams:
- IT and Security: Handle containment, forensics, and document the discovery date.
- Compliance and Privacy: Lead the HIPAA risk assessment and track deadlines for notifying individuals, HHS, and media.
- Legal: Interpret overlapping state and federal laws and review notification language.
- Communications: Draft and coordinate individual notices, media statements, and website updates [1][2][7].
Document these roles in a policy, including backup personnel for each position, to reduce confusion and speed up decisions during an incident.
Your breach notification playbook should outline every step from detection to final regulatory reporting. Set internal deadlines well ahead of the 60-day limit, such as completing risk assessments within 10–15 days and sending notices by day 45 [1][4]. Include decision trees to determine whether an incident is reportable, along with templates for individual letters and media notices that meet 45 C.F.R. § 164.404 requirements. The playbook should also specify escalation criteria for involving executives, the board, cyber insurance, and law enforcement [4][7][9]. Address scenarios like business associate breaches, lost devices, ransomware attacks, and misdirected communications [1][8].
Use Automation and Centralized Tracking Tools
Relying on spreadsheets and email chains for tracking can lead to missed deadlines, version control problems, and incomplete documentation. This makes it harder to prove "reasonable diligence" if the HHS Office for Civil Rights (OCR) reviews your response [1][4][8]. Centralized platforms provide a single system of record for incident details, including discovery dates, affected systems, and key decisions about breach determination and notifications.
Tools like Censinet RiskOps™ - designed specifically for healthcare cybersecurity - can centralize incident and third-party risk data across clinical applications, medical devices, and vendors. These platforms help organizations quickly determine whether PHI was involved and identify impacted covered entities or business associates.
Automation can further streamline the process by generating time-based tasks and alerts, such as reminders at 15, 30, and 45 days post-discovery, ensuring timely notifications [2][5][6]. These tools can also maintain rule sets for HIPAA and state breach laws, guiding users through required timelines, audiences (individuals, HHS, state Attorneys General, media), and content elements. For organizations managing multiple business associates, platforms like Censinet RiskOps™ help centralize third-party risk management. They catalog business associates, their systems, and data flows, enabling quick mapping of incidents to affected partners and patients. Automated alerts can flag delays in business associate notifications that could jeopardize the covered entity's 60-day deadline [1][6].
Test and Improve Your Response Plan
Regular testing of your breach response plan is essential. Use realistic, time-sensitive scenarios common in healthcare, such as ransomware attacks on EHR systems, misdirected lab results, or third-party breaches affecting multiple states [1][8]. Each exercise should track the "date of discovery" and require participants to make critical decisions, such as when to engage forensics, when to begin notifications, and whether the incident qualifies as a reportable breach under HIPAA's risk assessment standards [4][5][7].
Incorporate challenges like incomplete contact information (triggering substitute notices), state law deadlines shorter than HIPAA's 60 days, and law enforcement requests to delay notifications [1][2][4]. After each incident or exercise, review timelines, identify bottlenecks (e.g., gathering system logs or legal review delays), and ensure documentation meets OCR standards. Update your playbook, contact lists, and training materials based on lessons learned [4][5][7].
This continuous improvement process helps organizations shift from reactive to structured incident responses, reducing the risk of timing violations that could result in enforcement actions and penalties [1][4][8].
sbb-itb-535baee
Managing State and Federal Notification Requirements
When it comes to HIPAA's 60-day breach notification deadline, that’s just one piece of the puzzle. Things get trickier when state laws come into play. Many states have their own data breach laws with tighter deadlines - often between 30 and 45 days - and these laws can cover a wider range of data than HIPAA. If a breach impacts patients across multiple states, compliance teams need to focus on the strictest timeline to ensure they meet all their obligations [1].
Key Differences Between Federal and State Laws
State laws add another layer of complexity to breach notifications. For one, they often demand quicker action - notifications are typically required within 30 to 45 days and may start from the moment a breach is determined, not just when it’s discovered [1]. Beyond timing, states may require notifications to be sent to attorneys general, consumer protection agencies, or credit bureaus, depending on specific thresholds.
State laws also tend to cast a wider net when it comes to protected data. They often include Social Security numbers, driver’s license details, and financial account information, even if the breach doesn’t involve PHI. Additionally, some states mandate extra steps, like offering credit monitoring services or including specific contact information in notifications. Penalties for non-compliance vary by state and can differ significantly from HIPAA’s enforcement framework [3].
Build a Notification Timeline Matrix
To manage overlapping requirements effectively, creating a notification timeline matrix can be a game-changer. This tool helps map out critical details such as:
- Types of data involved (e.g., PHI, personal information, health app data)
- Definitions of trigger events (e.g., date of discovery vs. determination)
- Deadlines for notifying individuals, regulators, or the media
- Content requirements and notification methods
- Penalties and enforcement rules
Using this matrix, teams can log incidents and quickly determine which state or federal rules apply based on the location of affected individuals and the type of data involved. For example, if a ransomware attack compromises data for 5,000 individuals across several states with different deadlines, the organization can anchor its response to the most stringent timeline [1].
Use Technology to Track Legal Requirements
Once state-specific differences are identified and timelines are mapped, technology can simplify compliance. Platforms like Censinet RiskOps™ offer centralized tools to stay on top of federal and state regulations. These systems can automatically identify impacted jurisdictions based on individuals’ addresses and create task timelines aligned with the shortest legal deadlines.
Conclusion
Why Preparation Matters
The 60-day notification deadline is non-negotiable, and staying prepared is essential. Much of this timeframe is consumed by tasks like forensic investigations, assessing the scope of affected data, coordinating with vendors, legal reviews, and compiling accurate contact lists. Organizations that delay building their response capabilities until a breach occurs often find themselves scrambling to meet the deadline. Regulators have also emphasized that waiting until day 60 can still result in violations if sufficient information to notify was available earlier [4].
Preparation involves assigning roles and creating documented playbooks for the critical first 24–72 hours. It also requires keeping up-to-date inventories of PHI, linked to system owners and vendors, to quickly assess the breach's scope.
Terry Grogan, CISO at Tower Health, shared, "Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required." [10]
Regular tabletop exercises can help identify bottlenecks, such as delayed vendor responses or unclear approval processes, allowing organizations to address these issues before an actual breach. Many healthcare providers find that testing at least once a year enables them to complete full notifications in under 30 days, creating a critical buffer for managing complex or multi-jurisdiction incidents [4][8]. This proactive approach not only enhances response efficiency but also lays the groundwork for leveraging technology-driven solutions.
How Censinet RiskOps™ Supports Compliance

Technology plays a key role in bridging the gap between preparation and execution. Censinet RiskOps™ is designed specifically for healthcare, offering a centralized platform to manage third-party and enterprise cyber risks - common sources of PHI breaches. By organizing structured risk and vendor assessment data, the platform helps organizations quickly identify which systems, business associates, and data flows are impacted, significantly reducing the time required for scoping and risk assessment.
The platform also streamlines workflows and task management, ensuring coordinated breach investigations and notifications.
James Case, VP & CISO at Baptist Health, remarked, "Not only did we get rid of spreadsheets, but we have that larger community [of hospitals] to partner and work with." [10]
Switching to a centralized system like Censinet RiskOps™ creates a single source of truth for incident status, deadlines, and documentation. This reduces the risk of errors caused by missed emails or outdated spreadsheets, which could lead to timing failures.
Censinet RiskOps™ addresses healthcare-specific concerns, including PHI breaches, EHR integrations, and medical device connectivity. It empowers organizations to build repeatable, auditable processes that align with HIPAA's "without unreasonable delay" standard, minimizing the risk of missing deadlines. By combining thorough preparation with tools like Censinet RiskOps™, healthcare organizations can reliably meet breach notification deadlines and maintain patient trust.
FAQs
What should I do right after discovering a PHI breach?
The instant you suspect a breach involving protected health information (PHI), it's crucial to act fast to limit the damage. Begin by containing the breach to stop any further exposure and carefully record all the details, such as when and how the incident occurred.
Inform the individuals affected as quickly as possible, offering a clear explanation of the situation and any actions they should take to safeguard themselves. It's also essential to report the breach to the Department of Health and Human Services (HHS) within the mandatory 60-day window to stay compliant with HIPAA regulations.
What steps can healthcare organizations take to comply with federal and state breach notification laws?
Healthcare organizations can meet federal and state breach notification laws by creating well-defined processes for identifying, reporting, and resolving breaches. It's essential to stay aware of HIPAA's 60-day notification rule as well as varying state-specific deadlines.
To simplify compliance efforts, organizations should conduct regular risk assessments, keep policies current, and use tools that enable prompt reporting. Utilizing platforms tailored for healthcare risk management can help meet legal obligations while safeguarding patient data and other sensitive information.
How does technology help simplify the 60-day HIPAA breach notification process?
Technology significantly aids in making the HIPAA breach notification process more efficient by enabling quicker detection, automated alerts, and smoother data management. These tools are essential for ensuring that breaches are reported within the mandated 60-day timeframe.
For instance, AI-driven risk management platforms empower healthcare organizations to keep a constant eye on potential risks, automate complex workflows, and stay compliant with HIPAA rules. By cutting down on manual tasks and boosting operational efficiency, these technologies help safeguard sensitive patient information and ensure that breach notifications are handled with precision and care.


