How Multi-Cloud Key Management Secures PHI
Post Summary
Protecting Protected Health Information (PHI) in multi-cloud environments is a critical challenge for healthcare organizations. PHI includes sensitive data like medical records, Social Security numbers, and IP addresses, which must be secured to comply with regulations like HIPAA and HITECH. Encryption and key management are essential for safeguarding this data, but managing encryption keys across multiple cloud providers adds complexity.
Here’s what you need to know:
- PHI Security Challenges: Multi-cloud setups often lead to inconsistent encryption and key management practices, increasing the risk of breaches.
- Regulatory Requirements: HIPAA mandates encryption at rest and in transit, along with strict access controls, audit logs, and regular key rotation.
- Key Management Strategies: Organizations must map where PHI and encryption keys are stored, standardize encryption policies across providers, and enforce role-based access controls.
- Implementation Tips: Use tools like AWS KMS, Azure Key Vault, and Google Cloud KMS for encryption, and automate configurations with infrastructure-as-code to prevent misconfigurations.
- Ongoing Maintenance: Regular training, risk assessments, and incident response testing are vital to ensure compliance and security.
Key takeaway: Centralized and consistent key management across cloud platforms is essential to protect PHI, reduce risks, and avoid costly penalties under U.S. healthcare regulations.
Understanding Multi-Cloud Key Management Risks and Requirements
When planning multi-cloud key management, it's crucial to first identify where Protected Health Information (PHI) resides, how it moves across systems, and what encryption key compliance standards apply. This initial step helps uncover vulnerabilities that may put patient data at risk and allows you to prioritize fixes effectively. Below, we break these tasks into actionable steps.
Mapping PHI Across Cloud Platforms
Start by cataloging every location where PHI is stored, processed, or transmitted within your cloud environments. This includes clinical databases, backup systems, analytics platforms, and even temporary staging areas. Document how PHI moves between cloud environments and identify where encryption is applied - or where it might break down. Special attention should be given to cross-cloud transfers, as these can momentarily expose sensitive data if encryption keys aren't properly synchronized or if encryption lapses occur during the transfer.
In addition, map out all locations where encryption keys are created, stored, or used. This includes native cloud key management services (KMS), hardware security modules (HSMs), and application-level encryption libraries. Configuration inconsistencies across cloud providers can lead to heightened risks of PHI breaches. Without a complete map of where keys exist and how they're managed, enforcing consistent security policies or identifying mismanagement becomes nearly impossible.
Key Management Compliance Considerations
Determine whether your encryption keys are cloud-managed, customer-managed, or hosted externally, and clearly document who has administrative access to them. Under HIPAA, organizations must implement both administrative and technical safeguards for PHI. This means tightly controlling who has the authority to create, rotate, disable, or export encryption keys. Additionally, ensure that Business Associate Agreements (BAAs) clearly outline the responsibilities of cloud providers versus those of your organization.
Although HIPAA does not prescribe specific technologies, frameworks like NIST emphasize the importance of regular key rotation - either on a set schedule (e.g., annually or more frequently for high-risk scenarios) or immediately after a suspected compromise. In a multi-cloud setup, this requires aligning key rotation schedules across all providers, ensuring that services relying on PHI can seamlessly adopt new keys without downtime, and maintaining detailed rotation records for audits.
The stakes are high: under HITECH, civil penalties for PHI breaches can reach up to $1.5 million per year per violation category. This makes effective key management not just a technical necessity but also a financial safeguard.
Evaluating Current Key Management Practices
Once compliance standards are defined, assess your current key management practices to identify and address any vulnerabilities. Begin by reviewing your tools and processes for gaps. Common issues in multi-cloud healthcare environments include open storage buckets, expired access keys, missing encryption, and inconsistent identity management rules - all of which can expose PHI.
Verify that separation of duties is enforced, ensuring that key administrators, security teams, and application owners have distinct roles. This minimizes the risk of unauthorized access or misuse of encryption keys. Additionally, confirm that role-based access control (RBAC) is in place, so only designated roles - like security key administrators or approved services - can perform sensitive operations such as creating, rotating, or disabling keys.
Automate compliance monitoring by implementing configuration baselines and continuous checks. These should verify that all PHI storage has encryption enabled, no storage buckets are publicly accessible, and strong key policies are consistently applied. Tools like Censinet RiskOps™ can enhance these efforts by offering structured risk assessments, benchmarks, and collaborative management for PHI, clinical applications, and medical devices. Such platforms help healthcare organizations evaluate vendor practices, track remediation progress, and maintain strong encryption and key management policies across their multi-cloud environments.
Building a Multi-Cloud Key Management Architecture
Once you've mapped PHI and reviewed your current practices, the next step is to design an architecture that ensures consistent security and compliance across all cloud environments. This involves deciding on key ownership, standardizing policies, and integrating identity management. One of the biggest challenges in multi-cloud environments is configuration drift - where one cloud may have stronger encryption or access controls than another. This inconsistency can lead to data leaks. A well-thought-out architecture eliminates these gaps from the outset, strengthening the risk mitigation strategies discussed earlier. Let’s dive into ownership models, policy standardization, and identity integration.
Selecting the Right Key Ownership Model
Choosing the right key ownership model is a critical decision. You can opt for provider-managed keys, customer-managed keys (CMK), or externally hosted keys (like hardware security modules or third-party key management services). Each has its pros and cons.
- Provider-managed keys simplify lifecycle management but limit visibility into key events. This can make it harder to demonstrate separation of duties, which may raise concerns during audits or regulatory reviews regarding access to PHI encryption keys.
- Customer-managed keys (CMKs) offer more control and compliance flexibility. With CMKs, you manage key policies, access permissions, rotation schedules, and deletion timelines within each cloud provider's key management service (KMS). These keys also generate detailed audit logs and integrate seamlessly with native identity and access management (IAM) tools. However, this approach requires more effort to ensure consistent configurations across multiple clouds.
- Externally hosted keys provide the highest level of control. Using hardware security modules (HSMs) or third-party key platforms allows you to centralize key management, enforce uniform policies, and maintain strong separation of duties. Cloud administrators won’t have access to these keys, which can be crucial for meeting strict regulatory requirements. The trade-offs? Integration complexity, potential latency, and higher vendor costs. For organizations handling highly sensitive PHI or operating under stringent governance rules, the added control often outweighs these challenges.
Once you’ve chosen a model, the next step is to ensure encryption and key policies are consistent across all cloud platforms.
Standardizing Encryption and Key Policies Across Clouds
Consistency is essential when securing PHI across multiple clouds. Start by defining approved cryptographic standards - such as AES-256 for data at rest and TLS 1.2 or higher for data in transit - and enforce these standards across every cloud environment. Document these requirements in a multi-cloud key governance policy that aligns with HIPAA, HITECH, and NIST guidelines.
Set an enterprise-wide key rotation schedule. For instance, rotate keys every 12 months for most PHI workloads, with more frequent rotations for keys protecting high-risk systems or internet-facing services. Align this schedule with each cloud provider's KMS capabilities and ensure applications can handle key versioning without disruptions.
Your policies should also define clear key lifecycle states: active, deprecated (used only for decryption), and disabled or destroyed. Establish detailed procedures for transitioning keys between these states. For example, if a key is compromised or an employee with access leaves, you need to quickly disable the affected key, re-encrypt the PHI using a new key, and update configurations across all environments using infrastructure-as-code pipelines. Log every key rotation, revocation, and lifecycle change for audit purposes, and regularly test your procedures to ensure they work as intended.
With encryption and key policies standardized, the next focus is on limiting access through robust identity management.
Integrating Identity and Access Management with Key Security
To enforce your key policies, implement strict role-based access control (RBAC). Only specific roles - like security key administrators or designated application service accounts - should have permissions to create, rotate, disable, or delete keys. Application roles, for instance, should only have permissions for operations they require, such as "encrypt" and "decrypt", without broader key management privileges.
Design detailed KMS policies to restrict key usage to specific operations and resources. For example, a clinical analytics application should only access the encryption key assigned to its database, not keys protecting other PHI storage. This limits the potential for lateral movement if a compromise occurs. Additionally, enforce separation of duties by ensuring roles like key administrators, security teams, and application owners have distinct responsibilities. No single individual should have full control over both key creation and access to PHI.
Centralize identity management by federating authentication across all clouds using a single identity provider. Apply consistent multi-factor authentication (MFA) policies and conduct regular permission audits to identify and revoke unnecessary access. Automate compliance by scheduling configuration scans to verify encryption is enabled on all PHI storage, public access to storage buckets is disabled, and robust key policies are consistently applied.
Platforms like Censinet RiskOps™ can streamline this process by offering structured risk assessments and tools for monitoring PHI-related systems. These platforms help track vendor practices, oversee remediation efforts, and maintain strong encryption and key management policies across multi-cloud environments.
Implementing Multi-Cloud Key Management
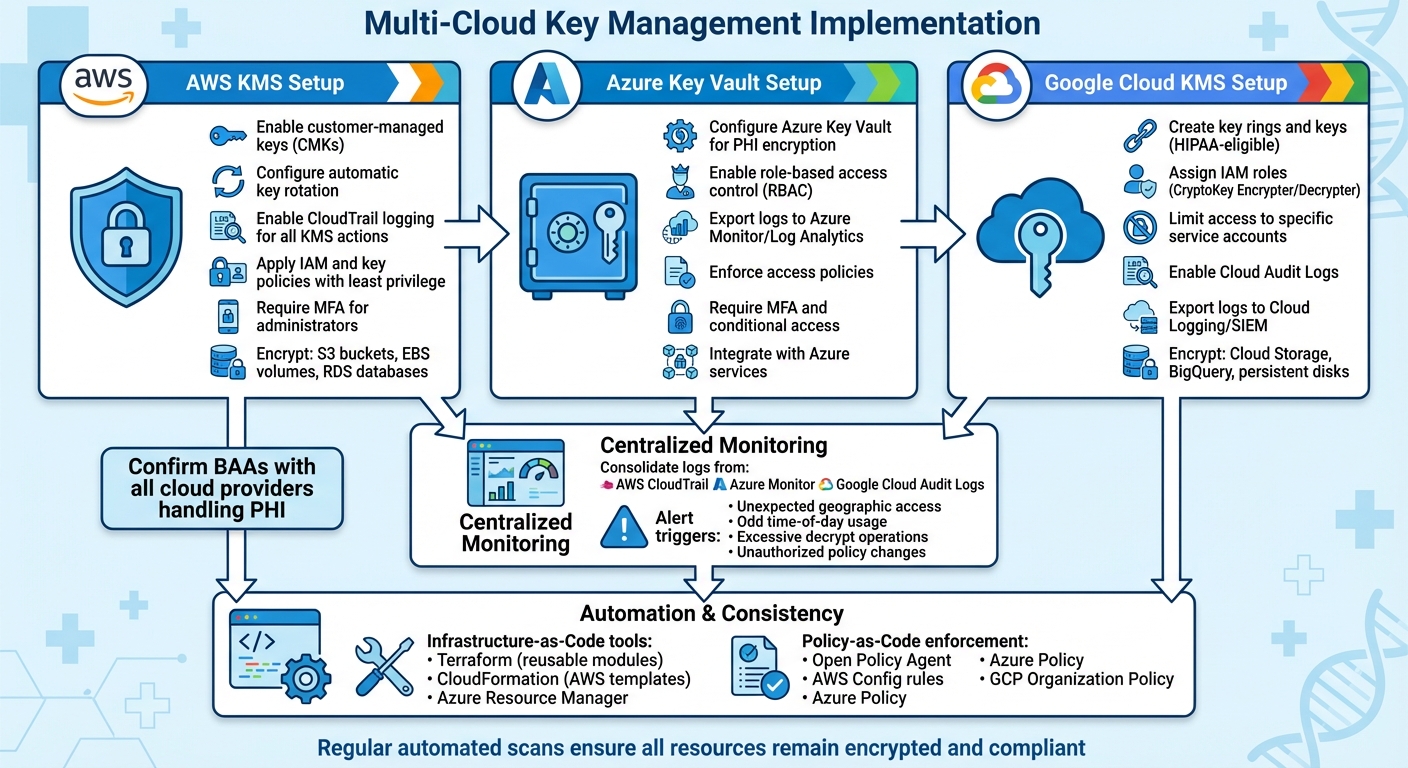
Multi-Cloud Key Management Implementation Steps for Healthcare PHI Security
Rolling out key management across AWS, Azure, and Google Cloud requires careful setup for each provider's key management service. This includes centralized logging for full visibility and automation to minimize misconfigurations. Make sure to confirm BAAs (Business Associate Agreements) with all cloud providers handling PHI [1][5].
Step-by-Step Deployment Across Cloud Providers
These configurations ensure your cloud environments meet enterprise PHI security standards.
AWS KMS
Leverage AWS KMS with customer-managed keys (CMKs) for better control and detailed auditing [1][4][5]. Enable automatic key rotation according to policy and log all KMS actions using CloudTrail [1][4][5]. Apply least privilege principles through IAM and key policies, and require multi-factor authentication (MFA) for administrators and sensitive operations. Use these keys to encrypt PHI stored in S3 buckets, EBS volumes, RDS databases, and other AWS services [1][4][5].
Azure Key Vault
For PHI encryption, Azure Key Vault integrates logging and uses role-based access control (RBAC) [1][4]. Export logs to Azure Monitor, Log Analytics, or your SIEM for auditing and anomaly detection. Enforce access controls with Azure RBAC and access policies, and require MFA and conditional access for administrators to enhance security [1][4].
Google Cloud KMS
Use Google Cloud KMS to manage encryption keys for Cloud Storage, BigQuery, and persistent disks [1][4][5]. When operated in a compliant environment, Google Cloud KMS is HIPAA-eligible. Assign appropriate IAM roles (e.g., Cloud KMS CryptoKey Encrypter/Decrypter) when setting up key rings and keys, and limit access to specific service accounts. Enable Cloud Audit Logs for KMS and export them to Cloud Logging or your SIEM to meet HIPAA record-keeping requirements [1][4][5].
Centralizing Key Monitoring and Logging
Once deployed, consolidate logs from AWS CloudTrail, Azure Monitor, and Google Cloud Audit Logs into a single SIEM or log platform. This unified approach simplifies anomaly detection across all cloud environments. Set up alerts for unusual key activities, such as unexpected geographic access, odd time-of-day usage, excessive decrypt operations, or unauthorized changes to key policies and IAM roles. For example, if a service account decrypts PHI keys at 3:00 AM from an unfamiliar IP address, your team should be notified immediately. Regular log reviews and automated anomaly detection can help identify misconfigurations or potential breaches early [1][3][4].
Platforms like Censinet RiskOps™ can assist by centralizing risk assessments for third-party and cloud vendors. They also help track PHI-related risks tied to multi-cloud key management, maintain a record of remediation actions, and support collaboration between security, compliance, and clinical teams when changes impact PHI systems.
Preventing Misconfigurations and Ensuring Consistency
To keep deployments secure, use infrastructure-as-code (IaC) tools like Terraform, CloudFormation, or Azure Resource Manager to enforce consistent encryption and key policies [1][6][7]. For instance, Terraform can create reusable modules for AWS KMS keys (including standard policies, key rotation, and CloudTrail integration), Azure Key Vault instances (with access policies and diagnostics), and Google Cloud KMS key rings (with keys, IAM bindings, and logging sinks). Similarly, CloudFormation templates can automate the configuration of encryption settings for resources like S3, EBS, and RDS, while enforcing tagging and logging standards [1][6][7].
Integrate IaC pipelines into CI/CD workflows to automatically apply encryption and key policies. Use policy-as-code tools like Open Policy Agent, AWS Config rules, Azure Policy, or GCP Organization Policy to prevent non-compliant configurations and address drift quickly. Regular automated configuration scans and security audits are essential to ensure all resources remain encrypted with approved keys and comply with organizational policies. Misconfigurations, such as open storage buckets or missing encryption, are among the most common causes of PHI exposure in multi-cloud healthcare environments [1].
sbb-itb-535baee
Maintaining and Optimizing Key Management Processes
Once your multi-cloud key management system is up and running, the work doesn’t stop there. Keeping it secure and compliant requires constant monitoring and adjustments. Configurations change, keys expire, and access controls can drift - any of these can lead to the exposure of sensitive patient data, such as PHI (Protected Health Information) [1]. To stay ahead, it’s crucial to conduct regular training, testing, and risk assessments. These efforts help maintain a strong defense as new threats emerge and regulations evolve, ensuring your system operates securely over time.
Training Teams and Formalizing Roles
Annual, role-specific training is a must for security, compliance, and IT teams. This training should focus on HIPAA, HITECH, and NIST guidelines, ensuring everyone understands their responsibilities [1][3]. Include practical, hands-on labs that cover the use of AWS, Azure, and Google Cloud KMS services. Simulate real-world incidents, like key compromises, and teach teams how to interpret centralized monitoring dashboards and SIEM alerts [4][6]. For U.S. healthcare organizations, it’s equally important to train staff on Business Associate Agreement (BAA) requirements, breach notification timelines, and the documentation standards expected during audits [1][4].
Clear role definitions are essential. Document responsibilities for cloud architects, security teams, compliance officers, and operations staff to prevent gaps or overlaps that could lead to vulnerabilities [6]. Establish a cloud governance committee that includes representatives from IT, security, compliance, and clinical teams. This group should oversee multi-cloud key policies and ensure PHI protections are upheld [3][6]. Tabletop exercises using realistic scenarios - like lost keys or misconfigured storage buckets - can help reinforce incident response protocols and ensure teams are ready to act when needed.
Testing for Resilience and Disaster Recovery
Even with a strong deployment, testing is critical to ensure your key management processes can handle stress. Schedule regular disaster recovery and continuity tests to evaluate how well your systems perform under challenging conditions. Scenarios might include the loss or compromise of a root key, outages in a cloud provider’s KMS or region, or restoring backup keys and HSM clusters while verifying their integrity. Additionally, test your incident response and breach notification workflows to ensure they comply with HIPAA/HITECH timelines and documentation standards [1][3].
It’s also vital to confirm recovery point objectives (RPO) and recovery time objectives (RTO) for critical healthcare systems like EHR, PACS, and lab platforms that rely on specific keys and regions. The HHS Healthcare Sector Cybersecurity Implementation Guide underscores that managing cyber risks is a continuous process - not a one-and-done project [3].
Continuous Risk Assessment and Optimization
Consistency in key management requires the same level of vigilance applied during the initial setup. Regular risk assessments should cover key lifecycle controls - such as creation, rotation, revocation, and destruction - as well as multi-cloud IAM practices, including SSO, MFA, RBAC, and just-in-time access [1]. Conduct periodic audits to identify unencrypted storage containing PHI, encryption gaps in transit between clouds, and issues like orphaned keys or over-privileged roles [1].
Common mistakes in multi-cloud environments include stale access keys, open storage buckets, missing encryption settings, and weak identity rules. To stay compliant with HIPAA and minimize breach risks, hospitals should review encryption standards, identity controls, and monitoring tools annually across all cloud platforms [1].
Tools like Censinet RiskOps™ can simplify ongoing risk management. This platform conducts standardized third-party risk assessments for EHR vendors, cloud providers, and security tools that interact with PHI or encryption keys. It helps track and address issues related to key management, IAM, and encryption, while benchmarking your cybersecurity posture and documenting controls for audits. By integrating continuous risk data - such as vulnerability scans and misconfiguration findings - into a centralized risk register, healthcare organizations can maintain a proactive approach to managing PHI and key security.
Conclusion
Safeguarding Protected Health Information (PHI) in a multi-cloud setup isn’t optional - it’s a necessity for meeting regulatory requirements and maintaining operational security. PHI must be encrypted consistently, both at rest and in transit, across all cloud environments. This requires the use of strong, industry-standard encryption algorithms that align with HIPAA and HITECH guidelines [1]. A centralized approach to multi-cloud key management helps eliminate fragmented controls and visibility gaps, which are common vulnerabilities that can jeopardize patient data [4]. By unifying key management practices, organizations not only ensure compliance but also reduce overall risk.
The stakes are high. HITECH has raised civil monetary penalties for mishandling PHI to as much as $1.5 million per violation category annually. Meanwhile, the U.S. Department of Health and Human Services has identified hacking and IT incidents as the leading causes of large-scale healthcare data breaches, compromising hundreds of millions of records [1][3]. Strong key management practices mitigate these risks by enabling swift key rotations, coordinated incident responses, and tamper-evident audits across all cloud environments [4][2].
Effective protection doesn’t stop at deployment. Long-term success depends on ongoing governance. This includes training staff, defining clear roles, conducting regular audits, and implementing formal risk management practices. Organizations can measure their progress by tracking metrics such as the speed of key rotations, the percentage of keys secured with multi-factor authentication (MFA) and role-based access control, and audit results under HIPAA [4]. Tools like Censinet RiskOps™ can simplify third-party risk assessments and provide continuous monitoring across cloud and vendor ecosystems, complementing the technical key management efforts described here.
Evaluate whether your centralized key management platform or HSM-backed solution integrates seamlessly with all cloud providers in use [2]. Train your teams - including engineering, security, and clinical staff - on their updated responsibilities and processes. Enforce unified controls to defend PHI against evolving threats. With a cohesive strategy, healthcare organizations can maintain control over their keys, enhance audit readiness, and establish a resilient defense against shifting regulatory demands.
FAQs
How does multi-cloud key management help protect PHI?
Managing encryption keys across multiple cloud platforms is a game-changer for protecting Protected Health Information (PHI). By centralizing control, healthcare organizations can ensure PHI stays encrypted whether it's stored or being transmitted, making it much harder for unauthorized individuals to access or compromise sensitive data.
This approach also simplifies compliance with stringent regulations. Features like secure key rotation, detailed access auditing, and easier encryption management help healthcare providers meet legal requirements while maintaining high security standards. In tackling the challenges of multi-cloud setups, this strategy creates a strong safeguard for patient information.
How can healthcare organizations ensure HIPAA compliance in multi-cloud environments?
To maintain HIPAA compliance in multi-cloud environments, healthcare organizations need to prioritize several key practices. Start by enforcing strict access controls to ensure only authorized personnel can access sensitive data. Additionally, encrypt all Protected Health Information (PHI) - both when it’s stored and while it’s being transmitted. Regularly monitor and audit cloud activity to identify and address potential risks before they escalate.
A solid risk management framework is also critical. Make sure it’s designed to identify vulnerabilities and includes measures to mitigate them effectively. Don’t overlook third-party vendors - verify that they meet all HIPAA requirements to avoid compliance gaps.
Solutions like Censinet RiskOps™ can simplify this process. These tools assist in streamlining risk assessments, enhancing cybersecurity benchmarks, and fostering collaborative risk management. By using such purpose-designed platforms, organizations can better safeguard patient data while staying aligned with healthcare regulations.
What should healthcare organizations consider when choosing a key ownership model for PHI encryption?
When deciding on a key ownership model for encrypting Protected Health Information (PHI), healthcare organizations need to consider control, compliance, and operational priorities. Retaining encryption key ownership allows for tighter control and can make it easier to meet regulatory requirements like HIPAA. On the other hand, relying on cloud providers for key management might bring convenience and reduce the complexity of operations.
It's crucial to assess how each model fits within your organization's overall risk management strategy. The chosen approach should support strong security measures, offer scalability, and ensure reliable data recovery. Focus on solutions that not only safeguard sensitive patient information but also align with healthcare regulations effectively.


