Network Segmentation for HIPAA Compliance
Post Summary
Protecting patient data is non-negotiable. Network segmentation is a proven way to secure ePHI (electronic protected health information) while managing vendor access. By dividing networks into isolated zones, healthcare organizations can limit access, prevent lateral movement by attackers, and align with HIPAA's technical safeguards.
Here’s what you need to know:
- Flat networks are risky: They allow attackers to move freely, exposing critical systems like EHRs and medical devices.
- Segmentation is now required: The 2025 HIPAA Security Rule mandates risk-based segmentation to protect ePHI.
- Vendor access needs control: Shared accounts, weak authentication, and broad access create vulnerabilities.
- Key safeguards: Segmentation enforces access control, audit logging, and transmission security, reducing breach risks and costs.
Start by mapping your network, classifying risks, and implementing vendor-specific zones. Tools like Censinet RiskOps™ can simplify this process and ensure compliance while safeguarding patient data.
Problems with Flat Networks and Vendor Access
How Flat Networks Expose ePHI
Flat networks bring together critical systems - like electronic health record (EHR) systems, imaging equipment, medical devices, billing platforms, guest Wi‑Fi, and vendor systems - into a single network segment that's broadly accessible. This setup makes it easy for attackers to exploit. Once they breach one entry point, such as a workstation or peripheral device, they can move freely across systems storing electronic protected health information (ePHI). This happens because unrestricted internal traffic bypasses firewalls and VLAN controls. Without internal firewalls or detailed access restrictions, lateral movement within the network goes unchecked. This lack of control not only makes it hard to enforce the "minimum necessary" access principle but also limits the ability to contain malware or ransomware.
The proposed 2025 HIPAA Security Rule highlights the risks of attackers pivoting from vulnerable peripheral systems into EHRs when network segmentation is absent [10]. When one system is breached, the lack of network boundaries exposes multiple others, violating HIPAA's confidentiality and integrity requirements. It also complicates efforts to ensure that only authorized users can access and monitor ePHI. These vulnerabilities become even more concerning when vendors access the network.
Risks from Vendor and Third-Party Access
Vendor access practices on flat networks add another layer of risk. Shared vendor accounts, weak or missing multi-factor authentication, always-on VPN connections, and network-wide access granted for convenience expose critical systems like EHRs, financial platforms, and medical devices. Such practices make it nearly impossible to enforce least-privilege access controls or track which specific individual accessed ePHI.
Shared vendor accounts, in particular, make it harder to trace user activity and can delay breach containment [4]. When excessive permissions are granted, a compromised vendor account can quickly access multiple systems. On top of that, insufficient logging of vendor sessions - such as missing session recordings or command logs - makes it difficult to determine exactly which ePHI was accessed or stolen [5].
Financial and Operational Consequences
The technical flaws of flat networks directly translate into financial and operational risks. Healthcare data breaches in the U.S. can cost organizations millions of dollars, factoring in expenses like incident response, forensic investigations, breach notifications, credit monitoring, legal settlements, and fines from the Office for Civil Rights [6]. Studies show that extensive lateral movement and unchecked third-party access not only increase the number of compromised records but also lead to higher breach costs and potential class-action lawsuits.
Regulatory fines can also be severe. The Office for Civil Rights may impose multimillion-dollar penalties for "willful neglect", especially when investigations reveal a lack of basic safeguards like network segmentation and vendor access controls [5]. Ransomware campaigns exploiting third-party remote access pathways often take advantage of flat networks, encrypting multiple systems in the process. These incidents drain IT resources, drive up cyber insurance premiums, and damage an organization’s reputation [10]. Recent analyses suggest that many breaches "could have been prevented or contained" if proper segmentation had been in place to limit attackers' lateral movement [10].
Building a Risk-Based Network Segmentation Strategy
Core Principles for HIPAA-Compliant Segmentation
The 2025 HIPAA Security Rule emphasizes the importance of risk-based network segmentation, as outlined in 45 CFR 164.312(a)(2)(vi), replacing the older "addressable versus required" approach [2][8].
To implement effective segmentation, three key principles come into play: Zero Trust, least privilege, and defense-in-depth. Zero Trust requires verification of every connection. Least privilege ensures that users and systems only have access to what is absolutely necessary. Defense-in-depth involves layering measures like strong identity management, encryption, and continuous monitoring. Together, these strategies limit lateral movement within the network and prevent attackers from accessing sensitive electronic health record (EHR) systems through unrelated systems, such as compromised point-of-sale devices or building control systems.
Static IP or subnet rules should give way to identity-aware policies, and encryption must be used to safeguard ePHI traffic, particularly when it crosses network segment boundaries or exits the organization.
Aligning Segmentation with HIPAA Safeguards
Network segmentation plays a vital role in meeting HIPAA's technical safeguards, offering measurable benefits:
- Access Controls (45 CFR 164.312(a)): Segmentation enforces role-based, least-privilege access by creating distinct zones for different departments, functions, and risk levels. Access rules are tied to user and system identity, making it easier to document who has access to ePHI and why.
- Audit Controls (45 CFR 164.312(b)): Clear segmentation ensures that all traffic flows through defined zones, where every connection is logged and monitored. This improves anomaly detection and simplifies compliance during audits.
- Transmission Security (45 CFR 164.312(e)): Segmentation limits and monitors the pathways for ePHI, ensuring encryption and secure remote access methods are in place for traffic between segments or across external boundaries.
To stay compliant, organizations must document, test, and continuously monitor their segmentation strategies. Up-to-date network and data flow diagrams should clearly outline segments, trust boundaries, and vendor connections, aligning with HIPAA's documentation standards. This approach sets the foundation for a detailed risk assessment and governance framework.
Risk Assessment and Governance for Segmentation
Before implementing segmentation, healthcare organizations need to conduct a comprehensive HIPAA risk analysis. This involves categorizing assets - such as EHR systems, medical devices, billing platforms, imaging equipment, vendor-managed systems, and guest networks - and designing segments based on risk levels, prioritizing the protection of ePHI.
Governance is essential to maintaining effective segmentation. This includes establishing clear change control processes, structured vendor onboarding, and regular validation. Testing methods such as penetration tests, red-team exercises, and tabletop scenarios should be used to ensure lateral movement toward ePHI systems is blocked. Continuous monitoring tools can help detect policy drift and confirm the ongoing effectiveness of segmentation.
Solutions like Censinet RiskOps™ simplify third-party risk assessments and vendor access management for healthcare organizations. Terry Grogan, CISO at Tower Health, shared:
"Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required" [1].
This collaborative approach is instrumental in designing segmentation strategies, especially when determining which vendors need access to ePHI systems and under what conditions. Once risk assessment and governance are in place, the focus shifts to implementing practical vendor access controls based on these strategies.
How to Implement Network Segmentation for Vendor Access
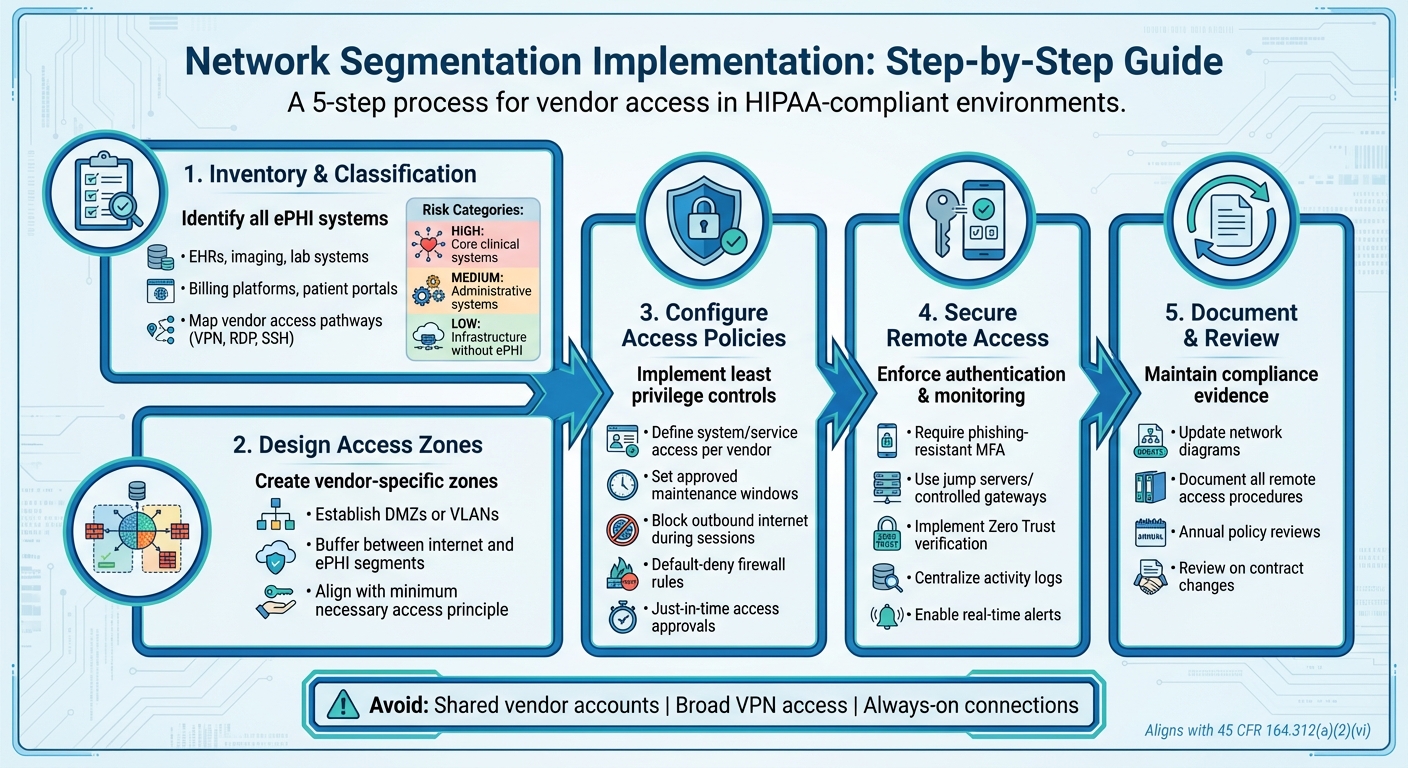
5-Step Network Segmentation Implementation Process for HIPAA Compliance
Identifying Systems and Vendor Access Points
Start by creating an inventory of all systems that handle electronic protected health information (ePHI). These might include electronic health records (EHRs), imaging systems, lab systems, billing platforms, patient portals, and backups. Then, map out every vendor access pathway - this could mean VPN, RDP, SSH, web portals, or cloud integration points. Once you’ve done this, classify the systems into risk categories:
- High risk: Core clinical systems.
- Medium risk: Administrative systems that occasionally handle ePHI.
- Low risk: Infrastructure systems without ePHI.
This classification will guide you in designing secure access zones tailored for vendors [3][4].
Setting Up Vendor Access Zones and Policies
Establish vendor access zones, such as DMZs or VLANs, to create a buffer between the internet and your internal ePHI segments [2][3]. Develop access policies that align with the principles of minimum necessary access and least privilege. These policies should clearly outline which systems and services vendors can access, as well as approved maintenance windows [4][5].
To strengthen security, block outbound internet access during vendor sessions to prevent potential exploitation, such as command-and-control attacks [3][4]. Avoid shared vendor accounts or granting broad VPN access, as these practices compromise both the principle of least privilege and the integrity of audit trails [2][4].
Further, enforce strict firewall rules with a default-deny approach, implement just-in-time access approvals, and ensure all rules are reviewed annually or whenever contracts change [2][3][4][8]. These steps will help secure vendor access and ensure their activity remains under control.
Securing Remote Access and Monitoring Vendor Activity
For remote vendor access, require multi-factor authentication (MFA) using phishing-resistant methods [6][10]. Direct vendor sessions through controlled gateways, like jump servers, to limit lateral movement within your network. Incorporate zero trust solutions to verify both identity and device security before granting access [2][3][7].
Centralize and record all vendor activity logs to enable real-time alerts and comprehensive audit reporting [2][3]. Ensure that your HIPAA policies document all remote access procedures, covering vendor obligations like using MFA and maintaining strong endpoint security [4][8].
For healthcare organizations, platforms like Censinet RiskOps™ can simplify the vendor assessment and access management process. By streamlining third-party risk evaluations, this solution helps determine which vendors require access to ePHI systems and under what conditions. This approach supports the foundation of effective segmentation strategies, ensuring a more secure and manageable vendor access framework.
sbb-itb-535baee
Benefits of Network Segmentation for HIPAA Compliance
Reduced Risk and Better Security
Network segmentation acts like a security barrier, keeping breaches contained within a specific zone. If an attack occurs - say, through compromised vendor credentials - it won’t grant access to your entire network. Instead, critical systems like EHRs, imaging tools, and patient portals remain shielded. This containment drastically reduces the potential impact of an incident and helps safeguard electronic protected health information (ePHI) from widespread exposure [2].
The updated 2025 HIPAA Security Rule emphasizes network segmentation as a core safeguard [2][8][9]. Specifically, the proposed rule at 45 CFR 164.312(a)(2)(vi) aims to prevent attackers from moving between systems, such as jumping from a point-of-sale terminal to clinical systems like EHRs [2]. By isolating vendor-connected systems, segmentation ensures that even if one system is compromised, your primary ePHI infrastructure remains secure. This approach not only strengthens your defenses but also simplifies compliance management.
Improved HIPAA Audit Readiness
Network segmentation provides clear, actionable audit evidence, including network diagrams, access policies, firewall configurations, and monitoring logs. These align directly with HIPAA's technical safeguards, such as access control, integrity protections, transmission security, and audit controls [2][3][5]. Having these artifacts readily available makes it easier to demonstrate "reasonable and appropriate" safeguards during investigations by the Office for Civil Rights (OCR) or state attorneys general [4][8].
Organizations with robust segmentation practices benefit from increased visibility into where ePHI is stored and how vendors access it. This clarity allows for faster, more confident responses to compliance questionnaires, OCR data requests, cyber-insurance evaluations, and third-party risk assessments [6][7]. Additionally, with the upcoming Security Rule updates requiring risk-based segmentation and regular validation, maintaining records like change logs, test reports, and segment-specific incident response playbooks becomes crucial. These documents serve as strong evidence of due diligence during audits [2][5][10].
Operational Benefits and Business Value
Segmentation doesn’t just boost security - it also enhances operational efficiency. By narrowing the scope of investigations to a specific segment, your security team can respond to incidents faster and restore normal operations more quickly [2]. Microsegmentation, which enables fine-tuned, identity-based policies, further accelerates threat containment and recovery processes [2][10].
These features support scalable and sustainable segmentation strategies. They also ensure that audit documentation stays up-to-date and allow for flexible adjustments to vendor access without compromising security. For healthcare organizations managing numerous vendors and third-party connections, tools like Censinet RiskOps™ can streamline the process. Such platforms help clarify which vendors need access to ePHI systems and under what conditions, enabling a more efficient and secure approach to vendor management.
Conclusion
The updated HIPAA Security Rule explicitly requires network segmentation as a technical safeguard, addressing the significant risks posed by vendor access to ePHI systems when networks lack proper isolation [2]. This regulatory change emphasizes the need for a thoughtful, risk-based segmentation strategy that aligns with existing cybersecurity frameworks.
With breaches costing millions, segmentation isn't just about compliance - it's a smart financial move [4]. A well-planned segmentation strategy helps contain breaches within isolated zones, accelerates incident response, and demonstrates due diligence during audits. Acting now can save organizations from costly, last-minute fixes as enforcement of the new rule ramps up.
For healthcare organizations managing complex vendor ecosystems, tools like Censinet RiskOps™ simplify vendor risk assessments and access management. This platform helps security teams identify which third parties require access to ePHI systems and define segmentation policies based on actual vendor security practices. By optimizing resources, organizations can conduct more assessments without overwhelming their teams.
Segmentation should be treated as an ongoing cybersecurity effort rather than a one-time task. Start by mapping vendor access points, creating risk-based zones, and implementing monitoring controls. Establish governance processes to regularly evaluate segmentation effectiveness, adapt policies as vendor relationships evolve, and maintain the audit documentation regulators now expect. This continuous strategy not only ensures compliance with HIPAA but also strengthens an organization's overall security posture. By adopting this structured approach, healthcare providers can better safeguard patient data, meet regulatory demands, and build a more resilient infrastructure for the future.
FAQs
How does network segmentation help ensure HIPAA compliance?
Network segmentation is a key strategy for aligning with HIPAA requirements, as it isolates sensitive healthcare data and ensures that only authorized individuals can access it. This approach minimizes the risk of unauthorized access and helps contain breaches, safeguarding protected health information (PHI).
By dividing networks into separate segments, healthcare organizations can more effectively oversee and manage data access. This setup makes it easier to comply with HIPAA's Security Rule, bolsters data protection, streamlines audits, and ensures that both vendors and personnel are limited to accessing only the information necessary for their roles.
How does network segmentation help protect sensitive healthcare data?
Network segmentation is an effective way to protect sensitive healthcare data by breaking a network into smaller, isolated sections. This approach limits access to critical systems and information, ensuring that only authorized individuals can interact with them. It also helps contain cyber threats, preventing them from spreading across the network and reducing the damage a potential breach might cause.
By keeping sensitive data and systems separate, healthcare organizations can strengthen their compliance with HIPAA regulations and improve the security of patient information and other essential assets.
How can healthcare organizations use network segmentation to enhance HIPAA compliance?
To strengthen HIPAA compliance, healthcare organizations should prioritize network segmentation. This involves separating sensitive data and critical systems from less secure parts of the network. Effective methods include using strict access controls, deploying firewalls, and setting up virtual local area networks (VLANs) to safeguard these key segments.
It's also crucial to routinely monitor and audit network activity to ensure the segmentation stays effective over time. Tools such as Censinet RiskOps™ can further enhance security by managing third-party vendor access and minimizing potential risks, adding an extra layer of protection for patient data and essential systems.


