NIST Tiers vs. Profiles: Key Differences for Healthcare
Post Summary
NIST Tiers and Profiles are essential tools for improving cybersecurity in healthcare. While Profiles focus on defining what cybersecurity outcomes an organization currently achieves or aims for, Tiers assess how well those outcomes are managed and governed. Together, they provide a roadmap for identifying gaps, prioritizing improvements, and aligning cybersecurity efforts with business goals.
Key Points:
- Profiles: Map current and target cybersecurity outcomes based on business needs, regulations, and risk tolerance.
- Tiers: Measure the maturity of cybersecurity governance and risk management, ranging from reactive (Tier 1) to advanced (Tier 4).
- Healthcare Use: Profiles help address specific challenges like protecting patient health information (PHI) or securing medical devices, while Tiers evaluate the effectiveness of governance processes supporting these efforts.
- Combined Approach: Comparing Profiles and Tiers helps healthcare organizations prioritize investments, close gaps, and improve both outcomes and governance.
By using NIST CSF Profiles and Tiers together, healthcare organizations can better protect patient data, comply with regulations, and strengthen their overall cyber resilience.
NIST CSF Profiles: Definition and Healthcare Use
What Are NIST CSF Profiles?
NIST CSF Profiles are tailored mappings of the framework's Categories and Subcategories, designed to align with an organization's unique business needs, risk tolerance, and available resources. Essentially, a Profile provides a snapshot of your cybersecurity posture, showing the outcomes you're currently achieving and the ones you're striving toward [3][5].
Profiles are divided into two types: the Current Profile, which reflects your achieved outcomes, and the Target Profile, which outlines your desired results based on business goals, regulatory requirements, and risk appetite [3][5]. This dual approach offers healthcare leaders a clear understanding of their current cybersecurity standing and their future objectives.
To support this process, NIST provides an Organizational Profile template and maintains a Community Profiles repository. This repository allows sectors, including healthcare, to create and share specialized Profiles [3][5]. These tools enable healthcare organizations to conduct focused risk assessments and develop targeted strategies.
How Healthcare Organizations Use Profiles
Healthcare organizations adapt the NIST CSF to create actionable plans that fit their clinical and operational needs. The HHS Healthcare and Public Health Cybersecurity Framework Implementation Guide advises healthcare entities to develop both Current and Target Profiles, compare them, and prioritize risk mitigation efforts based on identified gaps [4].
This gap analysis is where Profiles become especially useful. By comparing your Current Profile to your Target Profile at the Subcategory level, you can pinpoint specific vulnerabilities - whether those involve EHR security, maintaining PACS uptime, managing connected devices, or overseeing third-party vendors. With this information, organizations can assess the clinical and operational impacts of these gaps, set priorities for projects, allocate budgets efficiently, and justify staffing needs [4].
Profiles also play a key role in demonstrating compliance with the HIPAA Security Rule. The HHS 405(d) Task Group developed a HICP Threat Mitigation Matrix, which maps NIST CSF Categories and Subcategories directly to HIPAA Security Rule requirements [4]. This means your Profile outcomes not only strengthen cybersecurity but also provide valuable evidence for HIPAA audits and compliance assessments.
Healthcare Profile Examples
Here are some practical examples of how healthcare organizations use Profiles to address specific cybersecurity challenges:
- PHI Protection Profile: Focuses on securing patient health information through measures like access controls, encryption, audit logging, and incident response.
- Connected Medical Device Security Profile: Tackles the complexities of securing Internet of Medical Things (IoMT) devices and clinical engineering systems. Key priorities include asset inventory management, network segmentation, vulnerability management for outdated devices, and collaboration between IT and biomedical engineering teams.
- Clinical System Resilience Profile: Aims to maintain care delivery during cyber incidents. This Profile emphasizes backup and recovery processes, business continuity planning, and incident response strategies to ensure critical systems - like EHRs, imaging platforms, and lab information systems - remain operational under attack.
For example, Censinet RiskOps™ leverages NIST CSF Profiles to map third-party and enterprise risks, helping healthcare organizations benchmark their cybersecurity posture. It also tracks progress between Profiles and manages risks across patient data, clinical applications, and medical devices. These Profiles integrate seamlessly with the NIST CSF framework, supporting a comprehensive cybersecurity approach for healthcare.
NIST CSF Tiers: Definition and Healthcare Use
What Are NIST CSF Tiers?
While Profiles in the NIST Cybersecurity Framework (CSF) focus on the desired cybersecurity outcomes, Tiers evaluate how structured and effective your approach to risk management is. Essentially, Tiers reflect the maturity of an organization’s cybersecurity governance and risk management practices. Profiles define what you aim to achieve; Tiers describe how you manage the process - from reactive measures to fully integrated, proactive strategies [3].
The framework identifies four distinct Tiers: Tier 1 (Partial), Tier 2 (Risk Informed), Tier 3 (Repeatable), and Tier 4 (Adaptive) [2][3]. At Tier 1, organizations tend to operate in a reactive, ad-hoc manner, while Tier 4 represents a state of continuous improvement and adaptive cybersecurity practices [2][3].
Tiers are used alongside Current and Target Profiles to gauge and improve the strength of cybersecurity governance [3]. The HHS Healthcare and Public Health Sector Cybersecurity Framework Implementation Guide specifically advises healthcare organizations to combine Profiles and Implementation Tiers to assess their current standing, establish goals, and plan for enhancements [4].
These Tiers have practical implications for healthcare operations, as explored below.
Tier Characteristics in Healthcare
Healthcare organizations at different Tiers demonstrate varying levels of cybersecurity readiness and governance. For instance, a small rural clinic operating at Tier 1 might only address cybersecurity issues as they arise. In such cases, decisions are often made by the practice administrator without formal policies or oversight from leadership. Documentation is minimal, cybersecurity training is sporadic, and leadership rarely prioritizes cybersecurity in strategic discussions.
As organizations advance to Tier 2 or Tier 3, their approach becomes more structured. They implement formal policies, conduct regular risk assessments, and incorporate cybersecurity into broader risk management strategies. For example, a regional hospital at Tier 3 typically employs a dedicated security officer, ensures that documented procedures are consistently followed, and coordinates incident response efforts across departments. Cybersecurity updates are also regularly reported to the board.
Healthcare systems that reach Tier 4 demonstrate cutting-edge practices. These include leveraging threat intelligence, employing continuous monitoring, and utilizing automated responses to threats [2][3]. They actively participate in information-sharing networks like ISACs and make decisions based on real-time data. Notably, the "Govern" function introduced in CSF 2.0 strengthens the connection between Tiers and governance by emphasizing leadership accountability, risk management strategies, and supply chain risk oversight [2][3].
When Healthcare Organizations Should Adjust Tiers
Understanding when to move to a higher Tier is crucial for healthcare organizations. Advancing becomes necessary when current governance practices no longer align with the risks the organization faces. For example, a data breach exposing patient records often highlights gaps in governance that demand more rigorous processes. Similarly, mergers and acquisitions require higher Tiers to manage the complexities of integrating cybersecurity across multiple systems and locations.
Regulatory changes also drive Tier adjustments. Increased enforcement of HIPAA by the OCR or stricter state breach notification laws often necessitate more advanced risk management practices. The sensitivity of PHI, patient safety concerns, and the potential for disruptions to clinical systems should all influence decisions about Tier progression.
To determine your current Tier and set realistic goals, consider using benchmarking tools to evaluate your organization’s maturity and resilience [1]. As Brian Sterud, CIO at Faith Regional Health, explains:
"Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters." [1]
Start by assessing your governance structures, risk management practices, use of threat intelligence, and supply chain risk management. Map these findings to the Tier 1–4 levels using NIST CSF 2.0 guidance and Organizational Profile templates [3][5]. This evaluation lays the groundwork for planning your journey toward a higher Tier within a clear timeframe.
Key Differences Between NIST CSF Tiers and Profiles
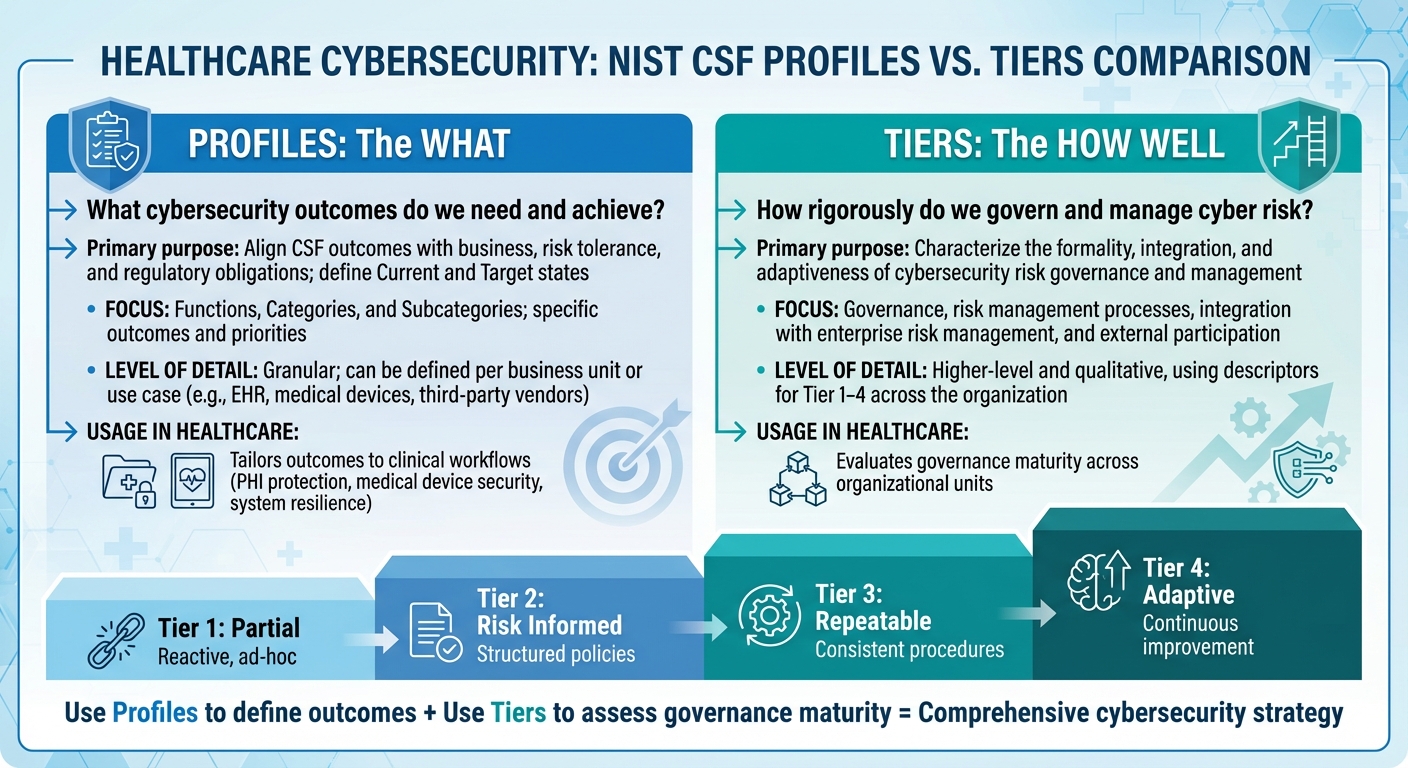
NIST CSF Tiers vs Profiles Comparison for Healthcare Organizations
Tiers vs. Profiles Comparison Table
Here’s the key distinction: Profiles focus on "what" cybersecurity outcomes an organization is achieving or aiming for, while Tiers assess "how well" those outcomes are governed and managed within the organization’s risk processes [3][5]. In essence, a Profile aligns the CSF Core outcomes to either your current or desired state, considering business goals and risk tolerance. On the other hand, a Tier reflects the maturity and integration of your cybersecurity risk management practices [2][3].
In healthcare, two hospitals might aim for the same Target Profile outcomes, like ensuring comprehensive protection of PHI. However, their Tiers could differ based on how structured and adaptive their risk governance processes are [2][4]. The table below highlights these differences:
| Aspect | NIST CSF Profiles | NIST CSF Tiers |
|---|---|---|
| Core Question | What cybersecurity outcomes do we need and achieve? | How rigorously do we govern and manage cyber risk? |
| Primary Purpose | Align CSF outcomes with business, risk tolerance, and regulatory obligations; define Current and Target states | Characterize the formality, integration, and adaptiveness of cybersecurity risk governance and management |
| Focus | Functions, Categories, and Subcategories; specific outcomes and priorities | Governance, risk management processes, integration with enterprise risk management, and external participation |
| Level of Detail | Granular; can be defined per business unit or use case (e.g., EHR, medical devices, third-party vendors) | Higher-level and qualitative, using descriptors for Tier 1–4 across the organization |
| Usage in Healthcare | Tailors outcomes to clinical workflows and evaluates governance maturity across organizational units [2][6][4] |
How Tiers and Profiles Work Together
NIST CSF 2.0 emphasizes that Tiers can be applied to Organizational Profiles, allowing organizations to assess not only the outcomes they achieve but also the rigor of the processes supporting those outcomes [3]. For example, a healthcare organization might develop a Current Profile for systems like EHR, imaging, or telehealth, mapping controls to the CSF Core [3][4]. They then assign a Current Tier (e.g., Tier 2 – Risk Informed) based on the maturity of their risk governance processes, set a Target Tier (e.g., Tier 3 – Repeatable), and outline the governance, process, and technology improvements needed to close the gap between Current and Target Tiers [2][3][4].
This approach provides a dual perspective: it identifies what needs improvement (Profile gaps) and how governance and processes must evolve (Tier enhancements) to support those improvements. For each gap between Current and Target Profile, organizations can analyze whether weak governance or processes are the root cause, then prioritize initiatives that address both the Profile gaps and the Tier deficiencies [3][4].
Impact on Healthcare Risk Management
By comparing Current and Target Profiles and Tiers, healthcare organizations can pinpoint gaps that pose the highest risk and depend the most on governance maturity [3][4]. For instance, if a hospital’s Current Profile reveals weaknesses in supply chain risk management and its Tier is only at Tier 1–2, leadership could prioritize formalizing third-party risk management processes and improving executive-level cyber risk reporting. These actions would help align with the organization’s overall risk appetite and move it toward Tiers 3–4 [2][6][4].
This integrated approach creates a clear link between cybersecurity investments and tangible outcomes. By tying spending to closing Profile gaps and advancing Tier maturity, healthcare organizations can better justify their investments. Incorporating Profile and Tier statuses into executive dashboards also helps communicate how cyber initiatives directly support patient safety, compliance, and financial risk management.
sbb-itb-535baee
Using Technology to Implement Tiers and Profiles in Healthcare
Integrating NIST CSF into Healthcare Cybersecurity Workflows
Healthcare organizations need specialized tools to incorporate NIST CSF Tiers and Profiles into their daily operations. The HHS Healthcare Sector Cybersecurity Framework Implementation Guide suggests creating Current and Target Profiles, selecting Implementation Tiers, identifying gaps, and monitoring progress over time. Using a dedicated platform simplifies these tasks by automating control mapping to the CSF Core, maintaining evidence repositories tied to specific functions and categories, and adapting automatically to operational changes [4].
By integrating NIST CSF into enterprise risk management, organizations can connect CSF outcomes to risk registers, issue management systems, and board-level reporting. These platforms also evaluate third-party risks against CSF subcategories, such as those related to cloud hosting for electronic health records (EHR) or medical device connectivity, and flag gaps that could impact the Current Profile. Applying Tiers at both enterprise and unit levels - like EHR systems or medical device networks - allows for tailored expectations and targeted investments.
Dashboards and reports provided by these platforms clearly show Tier positions and Profile gaps, helping organizations prioritize remediation based on risk and regulatory significance. This transforms compliance from a static checklist into a dynamic, ongoing risk management process that evolves with the healthcare threat landscape. Platforms like Censinet RiskOps™ further enhance this approach by streamlining CSF implementation through automation.
How Censinet Supports NIST CSF Implementation
Technology platforms have become indispensable for effectively implementing the NIST CSF in healthcare cybersecurity workflows. These tools are vital for managing cyber risks in alignment with NIST CSF guidelines.
Censinet RiskOps™ stands out by offering a cloud-based risk exchange that consolidates third-party and enterprise risk data from healthcare organizations and over 50,000 vendors. Its automated workflows replace time-consuming manual processes like managing spreadsheets and chasing down questionnaires. Terry Grogan, CISO at Tower Health, highlighted how the platform optimized team efficiency by reducing the need for dedicated risk resources.
"Not only did we get rid of spreadsheets, but we have that larger community [of hospitals] to partner and work with." - James Case, VP & CISO, Baptist Health
Censinet RiskOps™ also provides cybersecurity benchmarking tools, enabling organizations to measure their cyber program maturity against industry standards. This directly supports the evaluation and enhancement of NIST CSF Tiers. Acting as a system of record for NIST CSF Profiles and related evidence, the platform helps healthcare organizations track their progress toward achieving Target Profiles and Tiers. It also aids in managing risks across critical areas like patient data, protected health information (PHI), clinical applications, medical devices, and supply chains. Brian Sterud, CIO at Faith Regional Health, emphasized the impact of benchmarking, stating, "Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters."
Conclusion
The NIST Cybersecurity Framework (CSF) Profiles play a key role in defining the cybersecurity goals a healthcare organization currently achieves or aims to achieve. These Profiles capture both the existing and desired posture across the CSF Core. Meanwhile, the Tiers - Partial, Risk-Informed, Repeatable, and Adaptive - assess how well governance and risk management practices support these outcomes, offering a structured way to measure maturity and effectiveness in handling cybersecurity risks.[3][5][2]
Healthcare organizations use Current and Target Profiles to evaluate how effective their controls are, and then apply Tiers to improve governance practices. For example, a hospital might set a Target Profile that includes stronger third-party risk controls for electronic health record (EHR) vendors and medical devices. By advancing from Tier 2 (Risk-Informed) to Tier 3 (Repeatable), the hospital can ensure these controls are consistently applied across all departments.[3][5][2][4] This methodical approach not only strengthens risk management but also enhances operational efficiency.
Using both Profiles and Tiers together provides significant benefits, including better patient safety, improved regulatory compliance, and greater resilience in operations. Profiles help focus on critical outcomes, such as keeping EHR systems running and securing medical devices. Higher Tiers, on the other hand, reflect advanced risk management capabilities that allow for quicker detection, containment, and recovery during incidents.[2][3][4]
The U.S. Department of Health and Human Services (HHS) Healthcare and Public Health Cybersecurity Framework Implementation Guide encourages organizations to compare their Current Profiles and Tiers against their Target goals. This process helps identify and prioritize gaps, ultimately supporting national health security and ensuring uninterrupted care delivery.[4]
Healthcare leaders must regularly revisit their Profiles and Tiers, track progress toward their goals, and adjust investments in response to evolving threats. Tools like Censinet RiskOps™ simplify this process by centralizing the monitoring and evaluation of Profiles and Tiers across critical areas, such as patient data, protected health information (PHI), clinical systems, and supply chains. This transforms compliance from a rigid checklist into a flexible and proactive strategy.
FAQs
What’s the difference between NIST Profiles and Tiers, and how do they work together to enhance healthcare cybersecurity?
NIST Profiles and Tiers play distinct yet interconnected roles in bolstering cybersecurity within the healthcare sector.
Profiles allow organizations to adapt the NIST Cybersecurity Framework to their specific circumstances. For example, they might focus on protecting sensitive patient information or securing medical devices. Profiles help prioritize actions and ensure that cybersecurity efforts align with an organization’s particular goals and challenges.
Meanwhile, Tiers act as a maturity model, helping organizations assess and improve their overall cybersecurity readiness. They outline a progression from basic risk management practices to more advanced, adaptive strategies that can handle evolving threats.
By using Profiles to set targeted priorities and Tiers to evaluate and enhance maturity, healthcare organizations can create a strong, customized strategy to manage cybersecurity risks while continuously improving their defenses.
How do healthcare organizations use NIST Profiles to tackle cybersecurity challenges?
Healthcare organizations rely on NIST Profiles to tailor their cybersecurity strategies to address unique risks and operational demands. For instance, a hospital might adjust its Profile to strengthen the security of medical devices, protect clinical applications, or ensure the safety of patient data.
By adhering to established industry standards and meeting compliance requirements, NIST Profiles enable healthcare organizations to allocate resources wisely and tackle vulnerabilities efficiently, building a more robust defense against cyber threats.
When should a healthcare organization advance to a higher NIST Cybersecurity Tier?
When a healthcare organization's risk environment grows more challenging or intricate, it may be time to transition to a higher NIST Cybersecurity Tier. This shift often becomes necessary as cybersecurity threats escalate, new regulations emerge, or advanced technologies are integrated into operations.
Organizations might also consider this move after facing major security incidents or as part of a broader effort to strengthen their risk management strategies. Advancing to a higher tier can help ensure better protection of sensitive patient information, secure critical systems, and stay in line with evolving compliance requirements.


