Precision Medicine Vendor Risk: Genomic Data Security and Privacy Challenges
Post Summary
Genomic data is incredibly sensitive, permanent, and difficult to protect. It not only identifies individuals but also provides information about their relatives, making breaches far-reaching. Healthcare organizations increasingly rely on third-party vendors - like cloud storage providers and bioinformatics platforms - to process and store this data, which introduces significant risks.
Key challenges include:
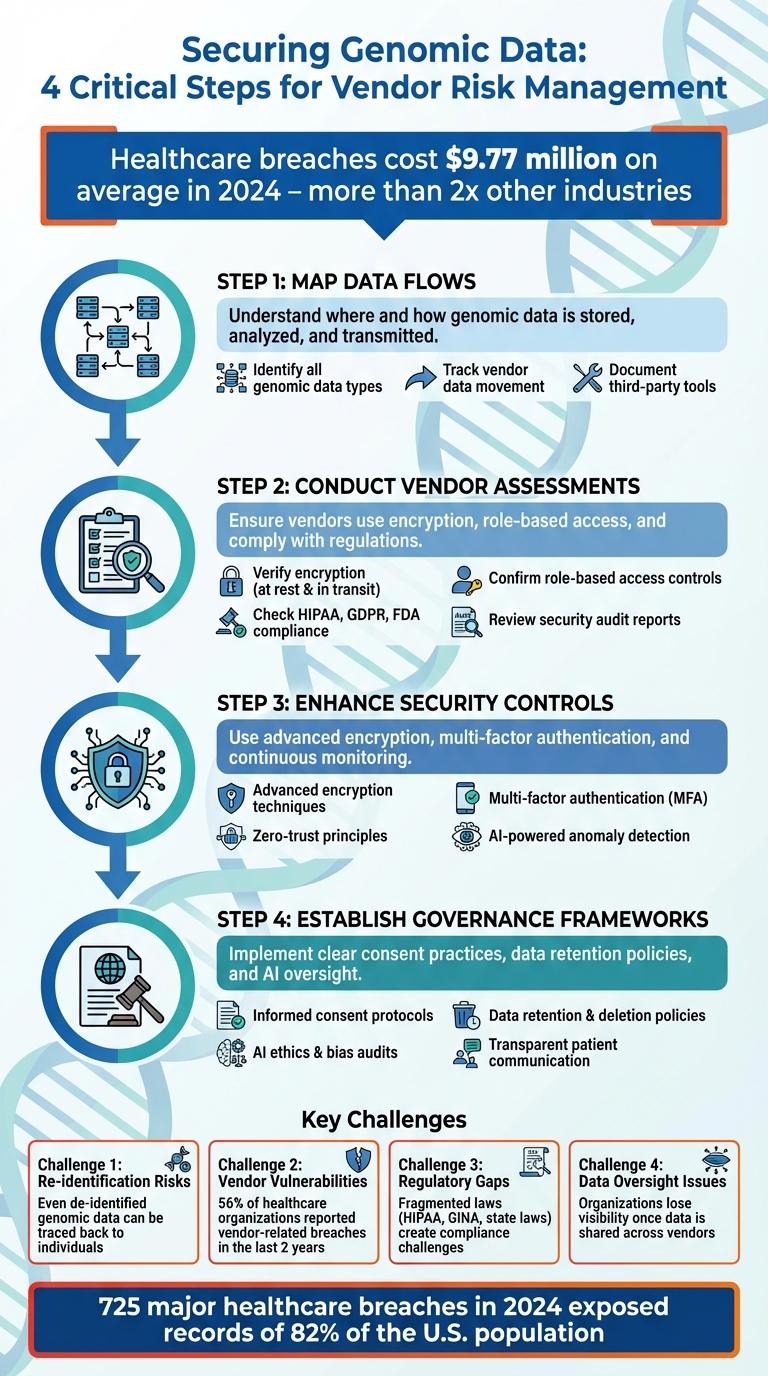
- Re-identification risks: Even de-identified genomic data can often be traced back to individuals using public databases or combined datasets.
- Vendor vulnerabilities: Each vendor partnership increases the chance of breaches, especially with weak access controls or poor security practices.
- Regulatory gaps: Existing laws, like HIPAA, don’t fully address the complexities of genomic data, leaving compliance and oversight fragmented.
- Data oversight issues: Once genomic data is shared across vendors, organizations often lose visibility into how it’s used or secured.
How to manage these risks:
- Map data flows: Understand where and how genomic data is stored, analyzed, and transmitted.
- Conduct vendor assessments: Ensure vendors use encryption, role-based access, and comply with regulations.
- Enhance security controls: Use advanced encryption, multi-factor authentication, and continuous monitoring.
- Establish governance frameworks: Implement clear consent practices, data retention policies, and AI oversight for genomic analytics.
With breaches in healthcare costing an average of $9.77 million in 2024, securing genomic data requires robust technical measures, thorough vendor management, and ethical governance to protect patient trust and privacy.
4-Step Framework for Managing Genomic Vendor Risks in Healthcare
Privacy and Security Challenges with Genomic Vendors
Collaborating with third-party vendors to handle genomic data introduces a unique set of risks. The decentralized nature of genomic data processing, combined with gaps in regulations and the identifiable nature of genetic information, creates a challenging environment for healthcare organizations. These factors demand thorough risk assessments and effective mitigation strategies.
Re-Identification Risks and Data Inference
Even when genomic data is de-identified, it remains at risk of re-identification through advanced techniques [9]. Researchers can often re-link anonymized genetic data to individuals by cross-referencing it with publicly available genealogical databases or combining it with information from other sources [1] [9] [10] [11].
The situation becomes even more precarious when genomic data is shared with external entities, like direct-to-consumer genetic testing companies. This practice increases the likelihood of re-identification across datasets [1] [4] [5] [6] [9] [10] [11]. For healthcare organizations, this highlights the critical need to scrutinize vendor practices rigorously.
Distributed Data Ecosystems and Limited Oversight
Genomic research often requires collaboration across multiple entities, leading to distributed data ecosystems [1]. However, once genomic data leaves a primary vendor, healthcare organizations frequently lose visibility into its movement and usage. Documented issues - such as system breaches, unauthorized data access, and non-compliant research - illustrate the challenges of maintaining oversight. Often, these problems are discovered through researcher updates, whistleblowers, or self-reports, rather than proactive monitoring [8].
This lack of transparency and oversight makes it even harder to navigate regulatory requirements and protect genomic data effectively.
Regulatory Complexity and Compliance Gaps
Beyond technical vulnerabilities, navigating the regulatory landscape adds another layer of complexity. In the U.S., fragmented regulations - including HIPAA, GINA, and various state laws - make compliance a significant challenge. Studies continue to reveal oversight gaps in managing genomic data throughout its lifecycle [7] [8] [9].
Without robust monitoring systems in place, agencies like the NIH and CDC risk overlooking violations that could expose Americans' genomic data to misuse, including by foreign entities in countries of concern [8].
How to Assess and Manage Genomic Vendor Risks
When working with genomic vendors, it’s essential to evaluate them thoroughly by charting data flows and ensuring robust, end-to-end security measures.
Data Mapping and Classification for Genomics
Start by identifying all genomic data types and assessing their risk profiles. For instance, raw sequencing files carry different risks compared to annotated results or clinical interpretations, and each type demands tailored safeguards based on its sensitivity and the likelihood of re-identification. Next, map how genomic data moves across vendors. Determine which vendors handle raw sequences, conduct analyses, store results, and access data at various stages. This visibility becomes even more critical when vendors use subcontractors or cloud services. Document every step of the process, including any third-party tools or platforms involved in data processing, storage, or transmission. A detailed inventory like this sets the stage for targeted and effective vendor risk management.
Genomic-Specific Vendor Due Diligence
Building on your data mapping, conduct due diligence specifically for genomic vendors. Traditional security questionnaires often fail to address vulnerabilities unique to genomic data. As part of your evaluation, confirm that vendors:
- Use encryption for data both at rest and in transit.
- Enforce role-based access controls.
- Comply with regulations like HIPAA, GDPR, and FDA 21 CFR Part 11.
- Integrate seamlessly with your EHR systems [12][13][14].
Additionally, ensure vendors have protocols for managing evolving genomic data [12][13]. Request proof of regular security audits, specialized penetration tests targeting genomic databases, and incident response plans tailored to genetic data breaches. These measures collectively strengthen your cybersecurity defenses for handling sensitive genomic information.
Automated Risk Management with Censinet RiskOps™
Managing these detailed processes manually can be time-consuming and inefficient, especially with the growing number of vendors and evolving risks. Censinet RiskOps™ simplifies this process with its Digital Risk Catalog™, which includes over 50,000 pre-assessed vendors and products, each with a risk score [15][16]. The platform automates compliance checks using standardized questionnaires and sends real-time alerts for missing critical documents, such as Business Associate Agreements required for protected health information. With delta-based reassessments, review times can drop to less than a day [15][16]. The platform also generates automated corrective action plans to identify and address security gaps, ensuring continuous monitoring. Additional features, such as breach and ransomware alerts, provide ongoing oversight across your vendor network. Automated risk tiering further enhances the process by scheduling reassessments based on the potential business impact and exposure of protected health information [15][16].
Technical and Operational Controls for Vendor Risk Mitigation
Once a vendor risk assessment is complete, it's crucial to implement technical measures that ensure genomic data remains secure at every stage. These measures must account for the unique nature of genetic information - its permanence, familial connections, and the potential for re-identification.
Protecting Genomic Data
To safeguard genomic content, use a combination of advanced encryption techniques. For de-identified clean room analyses, reversible encryption is key. For computations on encrypted data, homomorphic encryption offers a secure solution. Additionally, pseudonymization helps by separating personal identifiers from genetic sequences. Together, these methods provide robust protection for genomic data, whether it’s being stored or transferred [17].
Tightening Vendor Access Controls
Encryption and pseudonymization are only part of the equation. Strong access controls are equally essential to prevent unauthorized access. Recent vulnerabilities in vendor software, including issues with remote access and token storage, highlight the importance of these controls. To address these risks, implement measures such as multi-factor authentication (MFA), role-based access control (RBAC), and zero-trust principles. These steps significantly reduce the chances of unauthorized access [18][19].
The stakes are high - 56% of healthcare organizations reported vendor-related breaches within the last two years [19]. As Mike Levin, General Counsel and Chief Information Security Officer at Solera Health, aptly puts it:
Your vendor's risk is your risk [19].
Monitoring and Incident Response
To stay ahead of potential threats, deploy Security Information and Event Management (SIEM) platforms and AI-powered anomaly detection tools. These systems aggregate logs and flag unusual activity, such as unexpected access or data transfers. Integrating vendor telemetry into your incident response framework allows you to trace access events quickly, minimizing damage during an attack. With 92% of healthcare organizations reporting cyberattacks in 2024 [18], continuous monitoring, combined with threat intelligence and dark web surveillance, is no longer optional - it’s essential [20].
sbb-itb-535baee
Governance and Long-Term Management of Genomic Data
Protecting genomic data for the long haul requires more than just technical safeguards. It calls for governance frameworks that address ethical, legal, and operational challenges, particularly when third-party vendors are involved. These frameworks work hand-in-hand with technical measures to create a well-rounded approach to securing genomic data.
Ethical and Informed Consent Practices
Informed consent for genomic data isn't just about getting a signature. It involves clear, thorough communication about how the genetic information will be used, who will have access to it, and what happens if unexpected findings arise. Patients need to understand that their genomic data doesn't just affect them - it can have implications for their family members as well [21][22][3].
Consent processes should also cover future uses of the data, such as potential sharing with commercial entities or applications in forensic investigations. Transparency in these areas builds trust, which can encourage more participation in precision medicine programs. Given the risks involved, it's critical to ensure patients fully understand how their genetic information might be used now and in the future.
Data Retention and Deletion Protocols
Because genomic data can never be fully anonymized, retaining it poses ongoing privacy risks [1]. Organizations must establish clear, measurable guidelines for how long genetic data will be stored - both internally and by third-party vendors.
Under GDPR, genomic data can be retained for research beyond its original purpose, but only if strict safeguards are in place [23]. Implementing data protection by design means documenting whether the data will be deleted or anonymized at the end of its lifecycle. When working with vendors, it's crucial to confirm that their deletion practices align with your organization's policies and any applicable data use agreements. Remember, your organization remains responsible for the data even after it leaves your direct control [24][25].
AI Governance for Genomic Data Analytics
As AI and machine learning increasingly play a role in analyzing genomic data, strong governance is needed to ensure these tools operate ethically and within legal boundaries. This governance complements consent and retention policies, ensuring alignment with your organization's values.
To oversee AI models handling genomic data, focus on transparency in how algorithms make decisions, conduct regular audits to identify and address bias, and enforce strict adherence to ethical standards [26]. This oversight ensures that AI-driven genomic data analytics remain both responsible and trustworthy.
Conclusion: Building a Secure Genomic Data Ecosystem
Creating a secure genomic data ecosystem hinges on more than just technical safeguards - it requires a blend of advanced technology, ethical oversight, and vigilant vendor management. Genomic data, with its permanent and far-reaching implications, demands protection that goes beyond typical cybersecurity measures. Organizations must adopt a multi-layered strategy combining strong technical controls, thorough vendor risk management, and ethical governance to achieve a truly secure framework [2][11].
"The intersection between genomics and Cyber Security is not just a technical matter - it's a human one, with implications for identity, privacy, and trust in science." - Telefónica Tech [11]
The stakes couldn't be higher. In 2024, 725 major healthcare breaches exposed the records of 82% of the U.S. population, with the average cost of a healthcare breach soaring to $9.77 million - more than double the $4.88 million average across other industries [19]. These alarming numbers highlight the critical need for constant vigilance, especially in managing vendor relationships.
Securing genomic data involves implementing advanced protections like encryption (including quantum-resistant methods), strict access controls with MFA, AI-driven threat detection, and privacy-preserving technologies such as federated learning and homomorphic encryption [2]. Beyond technical safeguards, ethical governance and patient-centric consent practices play a pivotal role. Clear consent policies that empower patients to control their genetic data and transparent data retention protocols - extending to third-party vendors - are essential to building trust [2][11].
Healthcare organizations that excel in protecting genomic data will be those that understand this is about more than compliance. It’s about preserving patient trust while advancing the potential of precision medicine. By integrating cutting-edge technology, continuous oversight of vendor practices, and ethical governance, healthcare can chart a path forward that not only safeguards sensitive data but also strengthens patient confidence in the future of medicine.
FAQs
What steps can healthcare organizations take to protect genomic data when working with third-party vendors?
Healthcare organizations can safeguard genomic data shared with third-party vendors by adopting strong security protocols and conducting detailed risk evaluations. Some key practices include implementing end-to-end encryption to secure data both in transit and at rest, enabling multi-factor authentication for added security, and applying role-based access controls to restrict access to only those who need it.
Conducting regular vendor risk assessments is vital to ensure that third parties comply with security and regulatory standards, such as HIPAA. Organizations should also monitor data activity, schedule frequent security audits, and opt for secure, compliant cloud services that offer data residency features. By focusing on these measures, healthcare providers can enhance the protection of genomic data and uphold patient confidentiality.
What are the key regulatory challenges in protecting genomic data privacy?
Managing privacy for genomic data presents a maze of regulatory hurdles. While laws like HIPAA, GINA, and the Common Rule provide some level of protection, they don’t fully address the unique challenges tied to genomic information. Issues such as data ownership, obtaining informed consent, and navigating the complexities of sharing data internationally often fall outside their scope.
One pressing issue is the threat of re-identification, even when genomic data has been stripped of identifying details. This risk underscores the need for organizations to adopt strong security measures and remain agile in responding to shifting privacy standards. Tackling these challenges is crucial to maintaining compliance and safeguarding highly sensitive genomic data.
Why is de-identified genomic data still at risk of re-identification?
Genomic data, even when stripped of personal identifiers, isn't entirely immune to re-identification risks. Why? Because genetic information is both unique and unchanging for every individual. Without proper safeguards, this data can sometimes be linked back to specific people by cross-referencing it with publicly available resources like demographic details, family connections, or other datasets.
This sensitivity makes genomic data particularly vulnerable, as it could unintentionally reveal personal or family-related details. To address these risks, implementing strong privacy protections and rigorous vendor risk management practices is absolutely crucial.


