Real-Time Data Security in Healthcare IoT
Post Summary
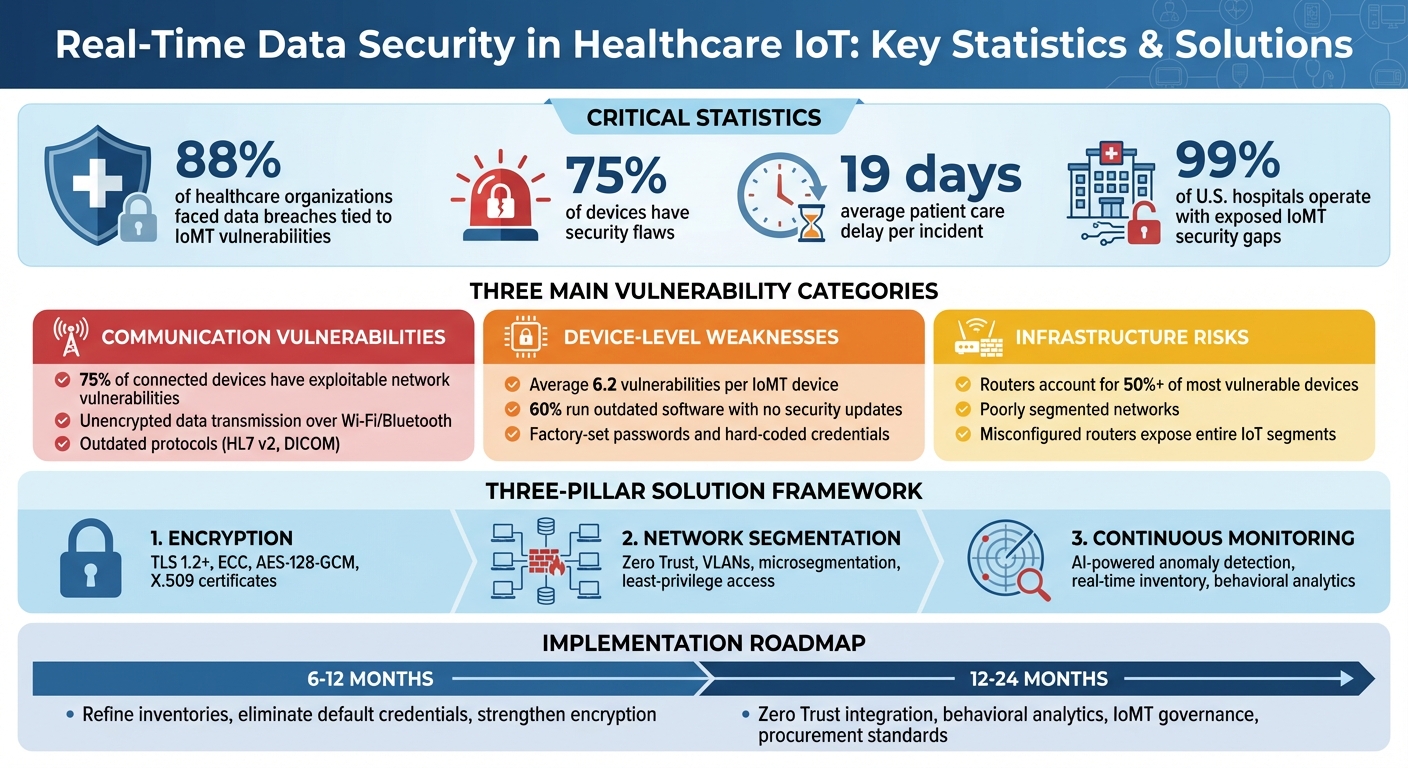
Healthcare IoT (IoMT) devices are transforming patient care but introducing new risks. Devices like infusion pumps, glucose monitors, and ventilators provide real-time data crucial for clinical decisions. However, 88% of healthcare organizations have faced data breaches tied to IoMT vulnerabilities, and 75% of devices have security flaws. These risks can delay patient care by an average of 19 days per incident and even jeopardize patient safety.
Key challenges include:
- Unsecured communication channels: Many devices transmit sensitive data without proper encryption, making them vulnerable to interception and manipulation.
- Device-level flaws: Outdated software, weak passwords, and lack of secure updates expose devices to persistent threats.
- Infrastructure risks: Poorly segmented networks allow attackers to exploit a single compromised device to access critical systems.
Solutions focus on three areas:
- Encryption: Use TLS 1.2+ and modern cryptographic protocols to secure data in transit.
- Network segmentation: Isolate IoMT devices from core systems using Zero Trust principles.
- Continuous monitoring: Employ AI tools to detect anomalies and respond to threats in real time.
Healthcare organizations must also adopt risk management platforms to maintain up-to-date IoMT inventories, prioritize security measures, and integrate these practices into governance frameworks. Immediate steps include eliminating default credentials, strengthening encryption, and improving network isolation. Over the next 1-2 years, organizations should implement Zero Trust policies, behavioral analytics, and stricter procurement standards to address evolving threats.
The bottom line: Securing IoMT devices is essential for protecting patient safety and ensuring uninterrupted care. Investing in encryption, segmentation, and monitoring today will help mitigate risks and prepare for future challenges.
Healthcare IoT Security Statistics and Key Vulnerabilities 2025
Main Vulnerabilities in Real-Time IoT Data Transmission
Recent studies break down IoT security issues in healthcare into three main categories: communication, device, and infrastructure vulnerabilities. These weaknesses are particularly concerning for real-time data, which is essential for quick clinical decisions. Alarmingly, almost all hospitals face exploitable vulnerabilities in this area [5][7]. Below, we explore these vulnerabilities and their impact on real-time data security.
Unsecured Communication Channels
Communication vulnerabilities pose a direct threat to the accuracy and safety of real-time patient monitoring. Many Internet of Medical Things (IoMT) devices transmit sensitive data - like patient vitals or medication dosages - over poorly encrypted or completely unencrypted channels, such as Wi-Fi or Bluetooth [3][6]. This opens the door for attackers to intercept or manipulate critical information.
Adding to the problem, outdated protocols like HL7 v2 and DICOM often rely on unsecured methods like plain TCP or older VPNs. Without modern security layers like TLS or IPsec, these communications are highly vulnerable. For example, attackers could intercept and alter alarm thresholds or medication orders without immediate detection [6]. A recent industry survey (2023–2024) revealed that 75% of connected healthcare devices have vulnerabilities that could be exploited through network traffic, including unprotected data streams used for monitoring and remote configuration [3].
Device-Level Security Weaknesses
Flaws at the device level create lasting vulnerabilities in real-time data systems. According to DeepStrike's 2025 IoMT analysis, the average IoMT device has 6.2 vulnerabilities, with 60% of devices running outdated software that no longer receives security updates [5]. This leaves hospitals exposed to significant risks.
Common problems include unchanged factory-set passwords, hard-coded credentials, open debug services, and a lack of secure boot mechanisms or code integrity checks. These gaps allow attackers to gain persistent control over devices streaming critical patient data [5][6]. A 2025 academic study also highlighted weak authentication, outdated firmware, and insecure communication protocols as major contributors to unauthorized access and data breaches in healthcare IoT systems [6].
Network and Infrastructure Risks
Infrastructure vulnerabilities amplify the risks posed by compromised IoMT devices, making it easier for attackers to disrupt clinical systems. Many IoT medical devices operate on flat or poorly segmented networks, which means that a single compromised device can give attackers access to electronic health records, imaging archives, or other systems handling real-time data [2][4].
Forescout's 2025 report notes that misconfigured routers and controllers frequently expose entire IoT segments to untrusted networks [4]. Additional issues include routers, switches, and access points with exposed management interfaces, outdated Wi-Fi security (e.g., shared passwords, legacy WPA, or open SSIDs), and a lack of access control lists or firewalls between IoT VLANs and core clinical systems [3][4]. Research analyzing millions of IoT devices found that routers account for over 50% of the most vulnerable devices, often with flaws that enable remote code execution or credential theft [4][8]. These infrastructure weaknesses have led to ransomware attacks, delaying access to patient data for an average of 19 days [2][5].
Research-Backed Solutions for Real-Time Data Security
Tackling vulnerabilities in real-time IoT data security requires a layered approach. Three key strategies - encryption, network isolation, and continuous monitoring - can significantly reduce risks, especially in U.S. healthcare systems. Let’s break down how these methods address critical weaknesses in real-time IoT data transmission.
Strengthening Data with Encryption
Encrypting data in transit is crucial for protecting communication channels. Use TLS 1.2 or higher for TCP traffic and DTLS 1.2 or higher for UDP-based transmissions, such as continuous vital-sign monitoring [6]. For devices with limited resources, implement Elliptic Curve Cryptography (ECC) for efficient key exchange and AES-128-GCM or ChaCha20-Poly1305 for authenticated encryption. To further secure communications, enforce perfect forward secrecy with ECDHE key exchange while disabling outdated protocols and legacy ciphers [6].
To prevent spoofing and man-in-the-middle attacks, deploy mutual authentication using X.509 certificates or strong pre-shared keys for devices, gateways, and cloud services [6]. Device identities should originate from a hardware root of trust, such as a Trusted Platform Module or secure element. Use short-lived certificates with automated renewal, tie them to specific device serials and roles, and promptly revoke credentials for decommissioned or compromised devices [2][6]. Research shows that inadequate device identity and lifecycle management has been a key factor in major IoT breaches, where attackers mimicked clinical devices to tamper with live data [2].
Network Segmentation and Zero Trust Principles
Encryption alone isn’t enough - network isolation is another critical layer of defense. Segment IoT traffic using network segmentation and microsegmentation to place medical IoT devices on separate VLANs or microsegments, away from systems like EHR platforms, administrative IT, and guest Wi-Fi networks [6][4][7]. This approach reduces the risk of lateral movement, ensuring that a compromised device cannot easily access other critical systems.
Zero Trust security principles take isolation a step further by requiring continuous authentication and authorization for every device and user request, even within the hospital network [2][6]. Enforce least-privilege access to restrict lateral movement [2][4]. A phased rollout of Zero Trust can help minimize disruptions. Start by conducting a comprehensive device discovery and classification to map out real-time data flows. Define clinical-safe policies that allow necessary telemetry to reach monitoring platforms and nurse stations while blocking unnecessary communications, such as internet access or peer-to-peer traffic. Use software-defined segmentation to gradually enforce these policies [6][4].
To avoid disrupting patient care, pilot Zero Trust measures in non-critical units first. Monitor for latency and packet loss, and collaborate closely with clinical engineering and IT security teams before expanding to critical-care areas. Case studies highlight that organizations using phased Zero Trust implementations with strong change management saw reduced lateral movement without causing downtime during real or simulated attacks [2][4].
Monitoring and Detecting Anomalies in Real Time
Continuous monitoring is vital for identifying threats to real-time data streams. Real-time traffic analysis, combined with AI and machine learning, can help detect anomalies [6]. For example, these tools can flag unusual behavior, such as a vital-signs monitor attempting to send data to an external IP address or a medication pump receiving unauthorized commands, triggering alerts before patient safety is at risk.
Effective monitoring starts with maintaining a real-time inventory of all IoMT devices, including details like manufacturer, model, operating system, firmware version, location, network segment, and ownership [5][7]. This inventory can be cross-referenced with known vulnerabilities, helping security teams prioritize fixes for high-risk devices. Integrating monitoring alerts with incident response workflows enables rapid containment, such as isolating compromised segments automatically [5][7].
For U.S. healthcare providers, aligning these monitoring practices with HIPAA's Security Rule, NIST guidelines, and FDA recommendations for medical device cybersecurity not only enhances security but also supports compliance during regulatory and insurance audits [6][5].
Applying Research Insights with Risk Management Platforms
Healthcare organizations face a critical need for integrated risk management solutions to turn threat data into actionable steps. Research highlights the urgency: 99% of U.S. hospitals operate with exposed IoMT security gaps, and 88% of organizations have experienced at least one data breach tied to a connected device in the past two years [3][5]. Relying on manual, spreadsheet-based risk management simply can't keep up with these challenges. Instead, organizations need platforms designed to translate technical vulnerabilities - like weak encryption, outdated patches, and unsecured protocols - into practical insights that inform governance, procurement decisions, and incident response strategies.
Conducting Risk Assessments for IoT Security
An effective IoT risk assessment begins with a comprehensive, continually updated inventory of all connected devices. This inventory should include key details such as the device's manufacturer, model, operating system, firmware, network segment, and ownership. Once cataloged, these details must be cross-referenced with known vulnerabilities and patterns from past breaches.
Censinet RiskOps™ simplifies this process by replacing fragmented spreadsheets with an integrated platform. It uses research-backed criteria to standardize assessments, focusing on critical vulnerabilities like device authentication, firmware updates, encryption practices, legacy operating systems, default credentials, network segmentation, and incident response capabilities [4][5][6]. By embedding these criteria into structured questionnaires and evidence requests, organizations can ensure consistent evaluation of every IoT device and vendor based on the latest threat intelligence.
"Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare." - Matt Christensen, Sr. Director GRC, Intermountain Health [1]
The platform also leverages a collaborative risk network, encompassing over 50,000 vendors and products across the healthcare sector. This shared intelligence allows organizations to quickly assess which manufacturers have robust security measures and which require closer examination. This is especially vital as regulators and insurers increasingly demand evidence of strong IoMT defenses - such as penetration testing results and software bills of materials (SBOMs) - before approving new devices or policies [5].
Using Censinet AI for Real-Time Risk Mitigation

When it comes to securing real-time data, speed is crucial. Censinet AI automates key steps in the risk assessment process, enabling vendors to complete security questionnaires in seconds, summarizing evidence and documentation, and generating risk summary reports from all relevant data. This automation allows risk teams to handle more assessments with fewer resources while maintaining oversight.
"Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required." - Terry Grogan, CISO, Tower Health [1]
Although Censinet AI doesn't directly manage medical devices, it plays a pivotal role in identifying and mitigating risks in near real time. Integrated with discovery and scanning tools, the platform updates risk scores dynamically as new devices connect to the network, vulnerabilities surface, or unusual traffic is detected [4][5][7]. Risk teams can set rules and review processes to ensure automation supports decision-making while preserving the human oversight necessary for patient safety.
The platform also acts as a central hub for AI governance and risk management. Key findings and tasks are routed to the appropriate stakeholders, including AI governance committees, ensuring timely action. With real-time data aggregated in an intuitive dashboard, Censinet RiskOps™ helps organizations manage AI-related policies, risks, and tasks efficiently, extending its risk mitigation capabilities into broader governance frameworks.
Integrating Real-Time Data Security into Governance
Technical controls like encryption, Zero Trust architecture, and network segmentation are most effective when paired with formal governance processes. Censinet RiskOps™ helps healthcare organizations align IoT security risks with enterprise risk registers, HIPAA/HITECH requirements, and patient safety priorities, enabling leadership to allocate resources effectively [5][7].
The platform supports various governance activities, such as security reviews during procurement, workflows for risk acceptance and exceptions, incident response runbooks for IoMT (like device isolation and failover procedures), and board-level reporting.
"Not only did we get rid of spreadsheets, but we have that larger community [of hospitals] to partner and work with." - James Case, VP & CISO, Baptist Health [1]
Procurement teams can also use the platform to ensure new IoT and medical device purchases meet security requirements from the outset. Vendors must demonstrate compliance with encryption standards (TLS 1.2 or higher, DTLS 1.2 or higher), mutual authentication using X.509 certificates, and support for network segmentation and Zero Trust policies. This approach helps prevent vulnerabilities from entering the system in the first place [6]. Benchmarking features allow security leaders to compare their IoT security posture against industry standards, making it easier to advocate for necessary resources.
"Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters." - Brian Sterud, CIO, Faith Regional Health [1]
Incident response plans also benefit from being integrated with IoT risk data. When a real-time clinical system is compromised, having a centralized platform with up-to-date device inventories, risk scores, and vendor contact details enables faster containment and recovery. Lessons learned from such incidents can feed back into procurement criteria, configuration baselines, and risk assessment processes, creating a continuous improvement cycle that strengthens governance over time [5][7].
sbb-itb-535baee
Future Directions and Research Gaps
As healthcare IoT defenses evolve, the focus is shifting toward improving cryptographic efficiency, safeguarding data privacy, and refining standardization efforts to ensure real-time data security. While risk mitigation strategies continue to advance, there are still critical gaps in cryptographic techniques, analytics, and standardization that need attention. Healthcare organizations must stay informed about these emerging areas to effectively tackle the next wave of threats.
Advances in Lightweight and Post-Quantum Cryptography
Traditional encryption methods like RSA and TLS are often too resource-intensive for low-power devices such as wearable monitors and implantable sensors that rely on real-time data transmission [6]. These devices lack the processing power and energy capacity to handle conventional cryptographic algorithms without compromising performance. Enter lightweight cryptography (LWC) - a solution designed to reduce CPU usage, memory demands, and energy consumption. In 2023, NIST introduced the ASCON family as its first LWC standard, targeting constrained devices such as medical sensors and wearables.
Meanwhile, post-quantum cryptography (PQC) is transitioning from theoretical research to practical applications. Algorithms like CRYSTALS-Kyber for key encapsulation and CRYSTALS-Dilithium for digital signatures have been standardized by NIST to withstand future quantum computing threats. However, PQC algorithms come with their own challenges, such as larger key sizes and higher computational costs, making them difficult to implement on small IoT devices. Researchers are now exploring hybrid solutions that combine classical and post-quantum encryption methods, as well as tailoring PQC for edge gateways that manage secure connections between IoT devices and cloud systems.
To prepare for these advancements, healthcare organizations should embrace crypto-agility - the flexibility to switch cryptographic algorithms without replacing hardware. This could involve using lightweight encryption like ASCON for resource-limited devices while assigning more demanding PQC tasks to edge servers or gateways. Such a layered approach ensures both real-time performance and long-term protection against emerging threats. Beyond encryption, new privacy-preserving techniques are also becoming essential for real-time data analytics.
Privacy-Preserving Analytics for Real-Time Data
Analyzing IoT data in real time can significantly enhance clinical outcomes, but centralizing raw patient data introduces privacy risks. Federated learning offers a solution by training models directly on edge devices, sending only model updates - not raw data like ECG readings or video feeds - to a central server [6]. This minimizes the risk of exposing protected health information (PHI) during transmission while allowing hospitals to collaborate on tasks such as arrhythmia detection or early sepsis warnings without sharing sensitive data.
Another key approach is differential privacy (DP), which adds mathematically controlled noise to aggregated data. This makes it nearly impossible to re-identify individual patients from trends or dashboards [6]. When combined with secure aggregation and homomorphic encryption, these methods enable hospitals to analyze device performance and operational metrics while safeguarding patient privacy.
Despite these innovations, practical challenges remain. Older medical devices with limited processing power, unreliable network connectivity, and the complexity of managing model updates across diverse endpoints can hinder deployment [3][6]. To address these issues, organizations can offload federated learning tasks to edge gateways, which consolidate data from multiple devices and perform training on more capable hardware before communicating updates to central servers [3]. For differential privacy, fine-tuning the noise level is critical - too much noise reduces the data's usefulness, while too little compromises privacy. Hospitals can start by testing these methods on secondary use cases, such as operational analytics, before applying them to critical clinical decision-making [6]. These privacy-preserving techniques complement cryptographic advancements by protecting data during real-time analysis.
Addressing Standardization and Testing Gaps
Although regulatory bodies like the FDA, HHS, and CISA emphasize secure-by-design principles, Software Bills of Materials (SBOMs), and coordinated vulnerability disclosures, the healthcare industry still lacks consistent methodologies for evaluating IoT security [7]. According to Claroty's 2025 "State of CPS Security: Healthcare Exposures" report, nearly every hospital and healthcare delivery organization operates connected devices with known vulnerabilities [7]. This highlights a significant gap between existing guidance and real-world implementation.
A major roadblock is the absence of repeatable testing and validation methods. Current frameworks, such as those from NIST and IEC 62443, are only partially adopted and often misaligned with the workflows of real-time IoMT systems. What’s needed are standardized testbeds, benchmarks, and conformance tests that continuously monitor device security rather than relying on one-time certifications [5][7]. Risk management platforms can help by providing ongoing risk assessments, real-time visibility into device vulnerabilities, and benchmarking against industry standards. These tools enable organizations to translate cutting-edge research into practical governance and procurement strategies.
To stay ahead, healthcare organizations should integrate research insights into their IoT lifecycle management. This includes requiring vendors to demonstrate crypto-agility, support for privacy-preserving analytics, and compliance with evolving standards. Adaptive governance processes will also be essential for navigating changes in cryptographic, privacy, and testing protocols. By addressing these gaps, healthcare systems can strengthen their defenses against vulnerabilities and prepare for a more secure future.
Conclusion
Ensuring the security of real-time IoT data is crucial for patient safety in the U.S., as any failure can directly compromise care. Recent studies reveal that ransomware attacks and breaches involving IoMT (Internet of Medical Things) devices have delayed patient services by an average of 19 days per incident [5]. Additionally, 88% of healthcare organizations reported at least one data breach in the past two years due to vulnerabilities in connected devices [3]. These numbers highlight the systemic risks posed by IoMT vulnerabilities. While essential safeguards - such as strong encryption, network segmentation guided by Zero Trust principles, and continuous anomaly detection - are well-known, consistent implementation and governance remain significant challenges.
To mitigate these risks, healthcare organizations must prioritize creating a real-time IoT asset inventory that tracks device types, firmware versions, and data flows, as poor visibility has been a key factor in many breaches. Enforcing TLS 1.2+ with strong ciphers for critical data transmissions is essential to prevent interception. IoMT networks should be segmented to isolate life-critical devices, and continuous monitoring should be implemented to detect unusual traffic patterns. A disciplined patching strategy, focusing on high-risk devices and routers, is equally important. These technical measures need to be integrated into enterprise governance frameworks, with clear accountability, regular reporting of IoMT risk metrics to leadership, and alignment with U.S. regulatory standards for PHI and medical device safety.
A robust risk management platform can further strengthen these efforts. For instance, Censinet RiskOps™ simplifies risk assessments, consolidates risk data, and supports continuous monitoring and benchmarking. By embedding these insights into governance structures - such as risk committees and board-level reporting - organizations can ensure IoT risks are addressed with proper funding and lead to sustained improvements.
Over the next 6–12 months, healthcare organizations should refine their IoMT inventories, eliminate default device credentials, strengthen encryption, and adopt a risk management platform. In the following 12–24 months, efforts should expand to integrate Zero Trust principles, implement behavioral analytics tailored to IoMT traffic, establish dedicated IoMT governance with regular executive reporting, and incorporate IoMT criteria into vendor and procurement decisions. While advancements like lightweight cryptography and privacy-preserving analytics will influence the future, immediate action is needed to address existing vulnerabilities, secure device lifecycles, and embed IoT risk considerations into organizational strategies.
The security of real-time IoT data is not just a technical necessity - it’s a cornerstone of patient safety and uninterrupted care. With increasing demands from regulators, insurers, and boards for demonstrable IoMT defenses, investing in encryption, segmentation, monitoring, and governance today will protect clinical operations, safeguard sensitive data, and prepare organizations to confidently face the evolving threat landscape.
FAQs
What steps can healthcare organizations take to secure real-time data from IoMT devices?
Healthcare organizations can protect real-time data from IoMT (Internet of Medical Things) devices by prioritizing strong cybersecurity practices. Key steps include using encryption protocols to secure data during transmission, performing regular risk assessments to pinpoint weaknesses, and employing continuous monitoring to quickly identify and respond to threats.
Specialized platforms tailored for the healthcare sector can make these tasks easier by automating risk management, enhancing visibility, and ensuring compliance with strict data protection regulations. These tools are essential for safeguarding sensitive patient information and securing communications between medical devices, reducing the chances of data breaches.
How can healthcare organizations apply Zero Trust principles to secure IoT networks?
To strengthen IoT networks in healthcare using Zero Trust principles, the first step is to constantly verify the identity of every user and device attempting to access the network. This ensures that only authorized entities are allowed in. Next, apply strict access controls and segment the network to restrict access to sensitive systems, reducing potential exposure.
Real-time activity monitoring is also essential. By keeping a close eye on network behavior, you can quickly identify unusual activity or potential threats before they escalate. Pair this with a least privilege approach, granting users and devices access only to the resources they absolutely need.
Sensitive data must be safeguarded with strong encryption, both while it's being transmitted and when it's stored. And because vulnerabilities evolve over time, regular risk assessments and updates are critical to staying ahead of emerging threats. Tools like Censinet RiskOps™ can simplify these processes, helping healthcare organizations manage risks more efficiently and strengthen their cybersecurity posture.
How does continuous monitoring enhance IoMT data security?
Continuous monitoring is essential for bolstering the security of IoMT (Internet of Medical Things) data. It works by spotting vulnerabilities and threats as they happen, giving healthcare organizations the ability to act quickly and reduce the risk of breaches. This not only limits potential damage but also helps shield sensitive patient information.
With constant oversight, healthcare providers can ensure that transmitted data remains secure and confidential. This approach not only protects critical systems but also reinforces patient trust by prioritizing their privacy and safety.


