Rehabilitation Hospital Vendor Risk Management: Specialized Equipment and Patient Safety
Post Summary
Vendor risk management in rehabilitation hospitals involves assessing, monitoring, and mitigating risks associated with third-party vendors to ensure patient safety and operational efficiency.
It ensures the safety of specialized equipment, protects patient data, maintains compliance with regulations, and prevents disruptions in patient care.
Risks include equipment failures, cybersecurity vulnerabilities, and non-compliance with healthcare regulations like HIPAA and FDA standards.
Best practices include conducting thorough vendor assessments, implementing Service Level Agreements (SLAs), continuous monitoring, and using automated tools like Censinet RiskOps™.
Compliance can be ensured by auditing vendors for adherence to HIPAA, FDA, and CMS standards, maintaining documentation, and monitoring cybersecurity practices.
Tools like Censinet RiskOps™ centralize vendor assessments, automate compliance tracking, and provide visibility into vendor risks.
Rehabilitation hospitals rely heavily on specialized equipment for patient recovery, making vendor management a critical priority. Failures in equipment or vendor services can disrupt care, compromise patient safety, and lead to significant financial losses. Cybersecurity risks, supply chain issues, and regulatory compliance are key challenges due to the increasing use of connected devices.
To address these risks, hospitals must:
- Implement structured vendor risk management programs.
- Focus on cybersecurity in all vendor relationships.
- Ensure compliance with standards like NIST and ISO 27001.
- Conduct regular risk assessments and vendor performance reviews.
- Prioritize patient safety by preparing for emergencies and maintaining oversight.
Risk Landscape for Specialized Rehab Equipment
Common Equipment in Rehab Settings
Rehabilitation hospitals depend on specialized tools to aid patient recovery. These devices are designed to improve mobility, support therapy, and monitor progress. Many of today’s rehabilitation tools come equipped with connectivity features, allowing real-time data sharing to streamline care coordination. However, this connectivity also introduces security vulnerabilities that need careful management. These risks can directly affect both patient safety and the smooth operation of healthcare services.
Main Risk Categories
Patient safety risks are a top priority. Issues like equipment malfunctions, delayed repairs, or compromised settings - often stemming from vendor security gaps - can put patients in danger. For individuals who rely on these tools for daily care, such failures could lead to severe or even life-threatening consequences[1][2].
Cybersecurity risks have become more pronounced, especially with the reliance on third-party vendors for connected rehab devices. These tools often depend on network connectivity for functions like therapy tracking and patient monitoring, making them vulnerable to cyberattacks.
Supply-chain reliability is another pressing concern. Delays in equipment delivery, shortages of essential components, or financial instability among vendors can disrupt access to critical tools. Hospitals that rely on a single vendor for specialized equipment or proprietary software face heightened risks if that vendor cannot meet their obligations.
Regulatory Requirements and Standards
To address these risks, rehabilitation hospitals turn to established industry standards such as NIST SP 800-53, HITRUST Common Security Framework (CSF), SOC 2 Type II, and ISO 27001. These frameworks provide guidelines for assessing vendor cybersecurity practices and help create consistent benchmarks for evaluating suppliers across the board. By adhering to these standards, hospitals aim to minimize vulnerabilities and ensure their equipment and systems remain secure and reliable.
How to Build a Vendor Risk Management Program
Setting Up Governance and Responsibilities
Creating a vendor risk management program starts with assigning clear responsibilities. Clinical teams contribute their expertise on how equipment affects patient care and recovery, while technical staff, including IT and security professionals, focus on identifying network vulnerabilities and monitoring device communications. Compliance teams ensure adherence to regulations like HIPAA and maintain proper documentation. Collaboration across these groups is critical because each brings a unique perspective to identifying risks. For instance, a physical therapist might notice inconsistent software updates on a gait training device, whereas a network engineer could detect unusual data traffic patterns. The FDA underscores this connection:
"Cybersecurity is Part of Device Safety and the Quality System Regulation" [5].
Temporary staff should also be included in governance structures, with mandatory security training and automatic revocation of access after their assignment ends to prevent gaps in security [4].
Risk Assessment Framework for Rehab Equipment
Once governance roles are established, the next step is to map out devices and evaluate their risks. Start by compiling a detailed inventory of all operational technology devices and their embedded components from various manufacturers. This inventory helps clarify device connections, communication pathways, and potential vulnerabilities [4]. Request a Hardware Bill of Materials (HBOM) and a Software Bill of Materials (SBOM) from vendors. These documents provide critical details about devices, software, firmware, communication frequency, and infrastructure requirements. For medical device manufacturers, providing SBOMs is already a regulatory requirement, and analyzing these can reveal third-party components that might pose hidden risks [4][5].
Cybersecurity risks should be assessed based on each device's intended use, foreseeable misuse, electronic data interfaces, and how it integrates into your existing network [5]. For example, a robotic therapy device used in a shared gym space has different vulnerabilities compared to one in a private treatment room with limited network access.
This thorough mapping of assets and risks directly supports the hospital's goal of ensuring patient safety and uninterrupted operations.
Vendor Due Diligence Best Practices
With a clear understanding of assets and risks, the focus shifts to thoroughly vetting vendors. Vendors should meet five critical security objectives: authenticity, authorization, availability, confidentiality, and timely updatability [5]. Don’t just take their word for it - request tangible proof such as audit records, anti-phishing training materials, and endpoint security policies. Additionally, confirm that vendors comply with key security standards like NIST Federal Information Product Standards (FIPS 140-2 and 140-3), NIST SP 800-82, CISA guidelines, NIST SP 800-161, and IEC 62443. Ensure alignment with the Medical Device and Health IT Joint Security Plan (JSP2) and IEC 81001-5-1 [4][5].
Demand full transparency about system interfaces and known vulnerabilities to accurately map network traffic and identify potential conflicts with your existing security measures [4]. A recent incident involving a flawed software update caused severe operational and financial disruptions, highlighting the importance of rigorous due diligence [4].
Cybersecurity Risks for Connected Rehab Equipment
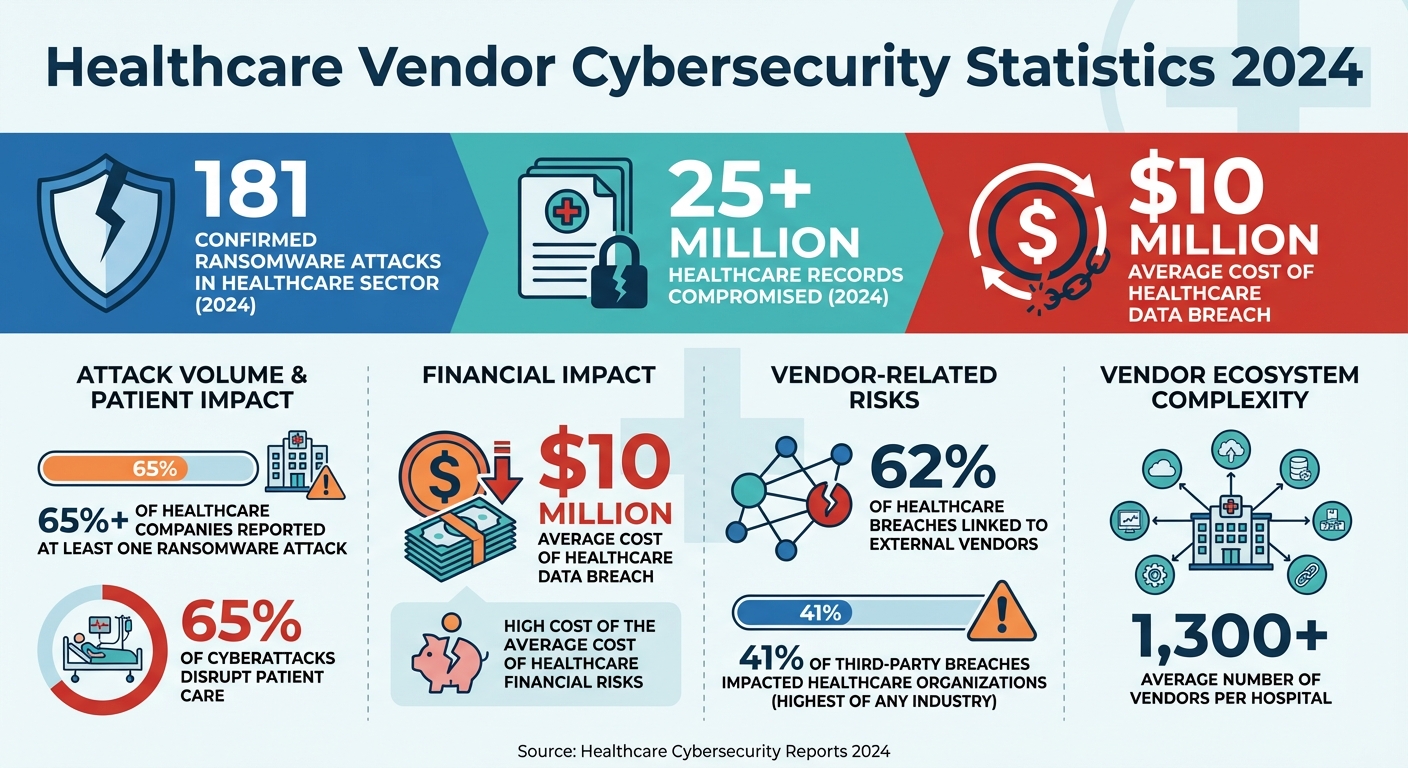
Healthcare Vendor Cybersecurity Statistics: Breach Impact and Risk Data 2024
Cybersecurity Threats in Connected Devices
Connected rehabilitation equipment faces many of the same cybersecurity challenges as other networked medical devices, but the stakes are particularly high when it comes to patient safety and recovery. Many of these devices - especially older models - weren’t designed with robust security in mind, making them vulnerable to attacks. In 2024 alone, the healthcare sector saw 181 confirmed ransomware attacks, which compromised over 25 million healthcare records [7]. For rehabilitation hospitals, where IT budgets are often tight and security teams are smaller, these risks are even more daunting. For example, when a robotic gait trainer connects to a hospital network to share patient progress data with electronic health records, it creates a potential entry point for unauthorized access. Additionally, unsecured remote access used for vendor troubleshooting can leave networks exposed to breaches. Alarmingly, recent statistics show that cyberattacks disrupt patient care in over 65% of cases, often leading to worse patient outcomes and even increased mortality rates [9]. Recognizing these risks is essential for evaluating the technical safeguards vendors must implement to ensure cybersecurity.
Cybersecurity Assessment Areas
Addressing these vulnerabilities requires a thorough and structured approach to identifying and mitigating risks. Vendors must demonstrate that their devices are equipped with proactive security measures from the development phase through deployment. This includes implementing comprehensive data protection strategies, such as encrypting data both at rest and in transit, with detailed documentation of encryption standards. Since breaches are inevitable, incident response capabilities are equally critical - vendors need to show they have effective plans for detecting, containing, and recovering from security incidents.
Third-party vulnerabilities pose a significant threat, with 62% of healthcare breaches linked to external vendors [8]. In 2024, 41% of third-party breaches impacted healthcare organizations, more than any other industry [3]. Considering the average hospital works with over 1,300 vendors [3], each partnership adds another layer of risk. These statistics highlight the importance of scrutinizing vendor relationships to minimize exposure.
Adding Cybersecurity to Vendor Risk Workflows
To address these challenges, cybersecurity must be woven into every stage of vendor risk management. Before onboarding a vendor, assess their security practices alongside their clinical capabilities and compliance with regulations. Traditional IT risk assessments often fail to account for healthcare-specific issues, such as unpatchable IoT devices or the operational disruptions caused by cyberattacks [8]. With the average cost of a data breach in healthcare nearing $10 million [1], prevention is far more cost-effective than dealing with the aftermath.
Make cybersecurity an ongoing priority by integrating security reviews into contract renewals. Require vendors to provide updated security documentation annually, ensuring their practices keep pace with evolving threats. Additionally, when vendors release software updates or introduce new features, conduct a security review to evaluate potential risks. With over 65% of healthcare companies reporting at least one ransomware attack [1], it’s clear that cybersecurity cannot be a one-time effort - it must be a continuous, active part of vendor oversight.
sbb-itb-535baee
Maintaining Operations and Patient Safety
Vendor Risk Controls Throughout the Lifecycle
To keep operations running smoothly and ensure patient safety, maintaining strong oversight of vendors is critical. Managing vendor risk isn’t a one-time task - it’s an ongoing process that spans the entire lifecycle of specialized rehabilitation equipment. This includes everything from evaluating potential vendors to procurement, implementation, daily operations, and eventual decommissioning. By embedding risk management at every stage, you can identify potential issues early and monitor developments to avoid disruptions [6].
Focus your attention on critical vendors - those who handle sensitive patient data, support life-saving equipment, or manage key operational systems. With so many vendor relationships, applying the same level of scrutiny to all of them isn’t practical. Instead, allocate resources to those whose failures could directly threaten patient care or compromise protected health information. During the procurement phase, include cybersecurity and compliance terms as mandatory contract requirements. Once the equipment is in use, schedule regular reviews to evaluate vendor performance, address security updates, and monitor any changes in their risk profile.
Patient Safety Controls
In rehabilitation settings, vendor failures can have serious consequences. Extended system outages could harm patients who rely on specialized equipment for their recovery [1]. Poor service delivery might reduce the quality of care and endanger patient health, making it essential to establish and enforce standardized safety controls.
Prepare for emergencies by creating detailed plans that spell out exactly what to do if a critical vendor system fails. These plans should clarify who to notify, identify available backup equipment, and outline steps to ensure patient care continues without interruptions. Having robust safety protocols in place protects patients when they are most vulnerable. This proactive approach to risk management also lays the groundwork for the centralized oversight tools discussed next.
Using Censinet RiskOps for Vendor Oversight

When managing risks across hundreds - or even thousands - of vendor relationships, a centralized platform becomes indispensable. Censinet RiskOps provides real-time visibility into vendor risks through dashboards that compile assessment results, compliance statuses, and security profiles across your entire vendor network. This creates a single, reliable source for tracking vendor-related risks.
The platform’s automated workflows simplify the assessment process by directing findings to the right stakeholders for review and approval. If a vendor’s security status changes or a new vulnerability is identified, the system triggers reassessments and alerts key team members. By combining continuous oversight with tools like Censinet RiskOps, you can ensure that safeguards stay effective throughout the equipment lifecycle. This approach helps prevent vendor risks from slipping through the cracks as your hospital navigates a complex web of equipment suppliers, maintenance providers, and technology vendors. With Censinet AITM, the end-to-end assessment process becomes faster, allowing vendors to complete security questionnaires efficiently while your team retains control through customizable review processes. This balance of efficiency and oversight is key to protecting patient safety.
Conclusion
Effectively managing vendor risk in rehabilitation hospitals is crucial for safeguarding patients and ensuring smooth operations. The specialized equipment that aids patient recovery introduces unique challenges, requiring careful oversight. When vendor failures go beyond IT disruptions, they can jeopardize patient safety, compromise data integrity, and disrupt critical care processes.
Healthcare organizations are increasingly vulnerable to third-party risks, with vendor-related breaches hitting all-time highs. These aren't just numbers - they represent real incidents where millions of patient records were exposed. As Barr Advisory emphasizes [2]:
"We're not just protecting business operations - we're protecting patient data, medical devices, and even life-saving services. That means vendor security isn't just an IT issue - it's a patient safety issue."
A well-structured vendor risk management program is essential to counter these threats. By implementing risk controls throughout the vendor lifecycle - from due diligence to ongoing monitoring - rehabilitation hospitals can safeguard patient data, meet regulatory requirements, and minimize disruptions to critical systems [1][2][10].
To stay ahead, continuous vigilance is non-negotiable. Focus on your most critical vendors, enforce strong cybersecurity measures in contracts, and maintain real-time visibility across your vendor network. With the right tools and framework, vendor risk management becomes more than a compliance task - it transforms into a strategic asset that bolsters both patient safety and operational stability. This proactive approach highlights the vital connection between patient care, operational strength, and cybersecurity.
FAQs
What steps can rehabilitation hospitals take to ensure vendors meet cybersecurity standards?
Rehabilitation hospitals can safeguard their cybersecurity by thoroughly evaluating vendors during onboarding. This includes conducting in-depth risk assessments and verifying certifications like SOC 2, ISO 27001, or HITRUST. Establishing clear contracts with specific cybersecurity controls and breach notification policies is equally important.
To maintain compliance, hospitals should consistently monitor vendor security practices, perform regular audits, and update Business Associate Agreements (BAAs) as needed. Including vendors in incident response plans and offboarding protocols further ensures the protection of patient data and the stability of operations.
What are the essential steps for creating a strong vendor risk management program in rehabilitation hospitals?
Creating a strong vendor risk management program begins with compiling a thorough inventory of vendors, especially those supplying specialized medical equipment. This inventory should cover all essential details about each supplier. Next, conduct in-depth due diligence to assess the reliability of vendors, their adherence to patient care standards, and their cybersecurity measures.
It's equally important to regularly track vendor performance to spot and address any risks early on. Additionally, establish a well-defined and organized offboarding process for vendors who fail to meet your hospital's standards. These practices are key to protecting patient safety and ensuring smooth operations.
Why is patient safety so important when using connected rehabilitation equipment?
Patient safety remains a critical concern, especially as connected rehabilitation equipment introduces risks like cyberattacks, malfunctions, or technical glitches. These issues can disrupt care, compromise sensitive health information, and potentially harm patients.
To address these challenges, hospitals must prioritize vendor risk management. By conducting regular evaluations and implementing strong cybersecurity protocols, healthcare facilities can reduce vulnerabilities, ensure smooth operations, and safeguard both patient care and data integrity.
Related Blog Posts
Key Points:
What is vendor risk management in rehabilitation hospitals?
Definition: Vendor risk management in rehabilitation hospitals is the process of assessing, monitoring, and mitigating risks associated with third-party vendors. This includes ensuring the safety and reliability of specialized equipment, protecting patient data, and maintaining compliance with healthcare regulations.
Why is vendor risk management important for rehabilitation hospitals?
Importance:
- Ensures the safety and reliability of specialized equipment critical for patient care.
- Protects sensitive patient data from breaches and unauthorized access.
- Maintains compliance with healthcare regulations like HIPAA, FDA standards, and CMS guidelines.
- Prevents operational disruptions caused by vendor-related issues, such as equipment failures or delayed deliveries.
What are the key risks associated with vendors in rehabilitation hospitals?
Key Risks:
- Equipment Failures: Malfunctions in specialized equipment can jeopardize patient safety and disrupt care.
- Cybersecurity Vulnerabilities: Network-connected devices and vendor systems can expose hospitals to cyberattacks.
- Regulatory Non-Compliance: Vendors failing to meet HIPAA, FDA, or CMS standards can result in penalties and reputational damage.
- Operational Disruptions: Delayed equipment deliveries or inadequate vendor support can impact patient care.
What are the best practices for managing vendor risks in rehabilitation hospitals?
Best Practices:
- Conduct thorough vendor assessments to evaluate financial stability, compliance, and technical reliability.
- Establish Service Level Agreements (SLAs) with clear performance expectations, including response times and maintenance schedules.
- Implement continuous monitoring to track vendor performance and detect potential risks.
- Use automated tools like Censinet RiskOps™ to streamline vendor evaluations and compliance tracking.
- Develop a vendor offboarding process to ensure secure termination of access and retrieval of sensitive data.
How can rehabilitation hospitals ensure compliance with vendor-related regulations?
Compliance Strategies:
- Audit vendors for adherence to HIPAA, FDA, and CMS standards.
- Maintain detailed documentation, including contracts, risk assessments, and compliance certifications.
- Monitor vendor cybersecurity practices, such as data encryption and incident response plans.
- Require vendors to provide timely updates and patches for connected devices.
What tools can streamline vendor risk management in rehabilitation hospitals?
Tools:
- Censinet RiskOps™: Centralizes vendor assessments, automates compliance tracking, and provides visibility into vendor risks.
- Identity and Access Management (IAM) Solutions: Manage vendor access to sensitive systems and data.
- Monitoring Dashboards: Track vendor performance and detect anomalies in real-time.


