Revenue Cycle Vendor Risk Management: Protecting Healthcare Financial Operations
Post Summary
Revenue cycle management (RCM) plays a critical role in healthcare financial operations, but working with third-party vendors introduces risks that can jeopardize data security, compliance, and revenue. Here's what you need to know:
- RCM Overview: Manages financial processes from patient scheduling to final payment, often relying on vendors for tasks like billing, claims, and payment processing.
- Key Risks: Errors, cyberattacks, and compliance failures from vendors can lead to financial losses, denied claims, and breaches of Protected Health Information (PHI).
- Regulatory Requirements: HIPAA, HITECH, and PCI DSS mandate strict vendor oversight, including Business Associate Agreements (BAAs) and data security protocols.
- Risk Management Steps: Build a vendor inventory, assess risks, set performance metrics, and use technology for centralized oversight.
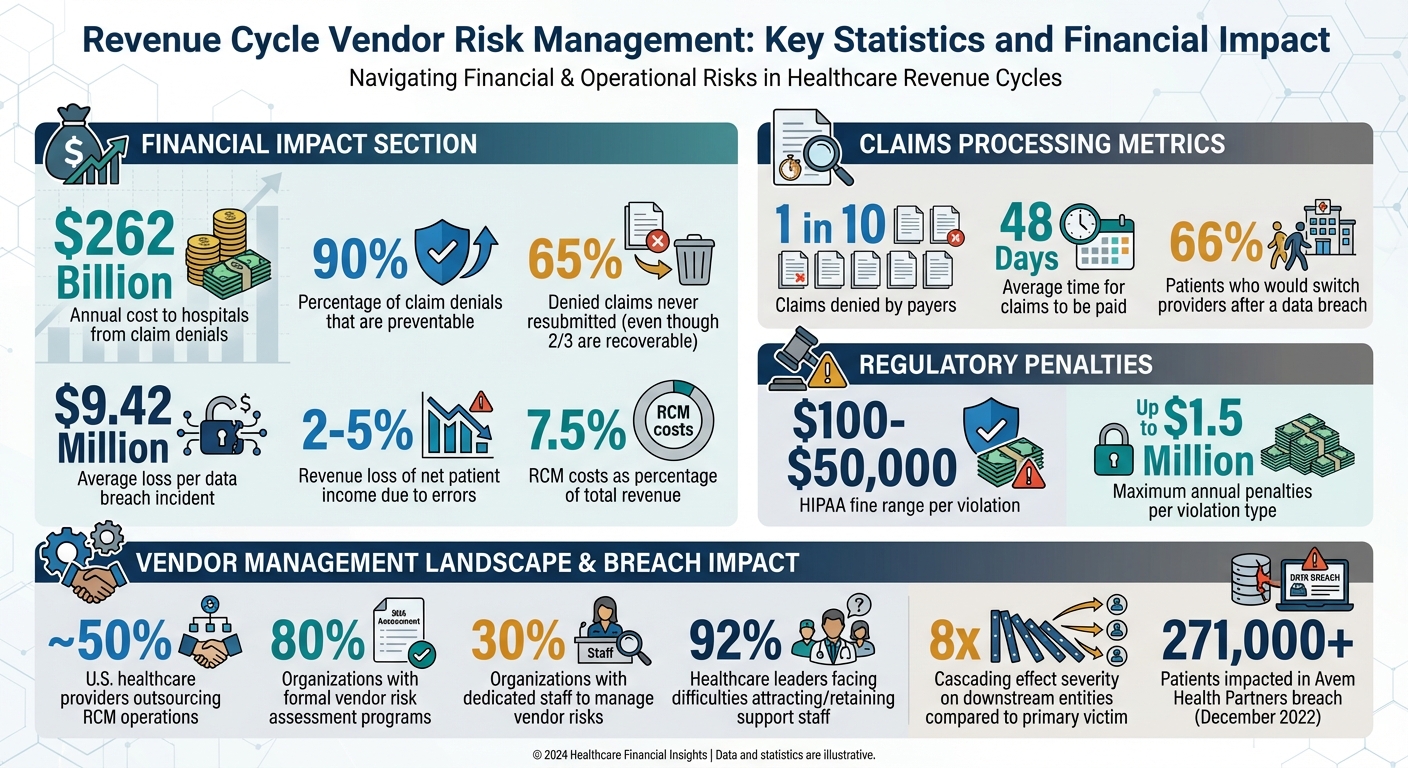
- Financial Impact: Claim denials cost hospitals $262 billion annually, with 90% preventable. Breaches average $9.42 million in losses per incident.
To safeguard finances and ensure compliance, healthcare organizations must actively monitor vendor performance, secure PHI, and streamline risk management processes.
Revenue Cycle Vendor Risk Management: Key Statistics and Financial Impact
Risk Landscape and Regulatory Requirements
Managing vendor risks effectively starts with identifying weak points in revenue cycle workflows and understanding the rules that govern vendor relationships.
Where Risks Occur in Revenue Cycle Workflows
Revenue cycle workflows are full of potential vulnerabilities that can disrupt financial operations. For instance, during patient access and preregistration, collecting inaccurate data - like insurance details, deductibles, or coverage - can lead to claim rejections before the process even begins. These early mistakes often create a ripple effect throughout the entire revenue cycle [2][5].
Another high-risk area is charge capture and coding. When vendors handle coding tasks like ICD-10 or CPT/HCPCS, errors such as missed charges or incorrect billing can occur. The stakes are high: hospitals lose approximately $262 billion annually due to claim denials, and providers face a revenue loss of 2% to 5% of their net patient income [2].
Claim submission and processing add further challenges. Using outdated billing systems or failing to properly scrub claims can result in "dirty" claims. Payers deny roughly one in ten claims submitted, and about 90% of these denials are preventable. Yet, up to 65% of denied claims are never resubmitted - even though two-thirds are recoverable. On top of that, manual payment posting slows reimbursements, with claims taking an average of 48 days to be paid, while revenue cycle management (RCM) costs consume about 7.5% of total revenue [5][6].
Data security is another major concern. Vendors handling Protected Health Information (PHI) and financial data are prime targets for cyberattacks. A breach can have a cascading effect, impacting downstream entities more than eight times as severely as the primary victim [7].
These vulnerabilities highlight the importance of stringent regulatory oversight.
U.S. Regulatory and Compliance Requirements
Healthcare organizations must navigate a maze of federal and state regulations when working with revenue cycle vendors. These rules emphasize the need for thorough vendor risk management at all levels. HIPAA (Health Insurance Portability and Accountability Act) plays a central role, safeguarding patient health information through its Privacy and Security Rules. Any RCM vendor dealing with PHI must comply with HIPAA, and organizations are required to formalize Business Associate Agreements (BAAs) with third-party billing vendors [8][9][10][1]. Violating HIPAA can result in fines ranging from $100 to $50,000 per violation, with annual penalties reaching up to $1.5 million per violation type [1].
The HITECH Act further enforces HIPAA by extending compliance responsibilities to business associates. Additionally, PCI DSS (Payment Card Industry Data Security Standard) outlines strict technical and operational controls for vendors handling credit card payments. Many states have also introduced privacy laws that go beyond federal requirements, adding another layer of complexity.
Beyond these regulatory frameworks, healthcare boards play a critical role in ensuring compliance and mitigating risks.
Board and Audit Requirements for Vendor Oversight
Healthcare boards and audit committees demand clear evidence that vendor risk management programs are functioning effectively. A vendor's failure to comply with regulations can lead to hefty financial penalties, damage to reputation, and a loss of patient trust [1]. Boards expect frequent updates on vendor performance, security measures, and compliance status. Without proper due diligence, ongoing monitoring, and well-defined Service Level Agreements (SLAs), organizations risk destabilizing vendor operations and failing to meet regulatory standards [1][3][7].
Building a Revenue Cycle Vendor Risk Management Program
Once you've identified potential risks and the regulations that apply, the next step is to establish a structured program to manage those risks. This process includes creating a comprehensive inventory of vendors, setting clear objectives, and utilizing technology to streamline operations. Let’s break down the key components of building an effective vendor risk management program.
Creating a Vendor Inventory and Risk Categories
Start by listing all vendors involved in your revenue cycle. This includes billing companies, coding services, payment processors, and claims clearinghouses. Don’t overlook smaller vendors that may have access to your data, systems, or facilities - they can pose risks, too.
Once your inventory is complete, categorize vendors by their risk level. Assess factors like the sensitivity of the data they handle (e.g., Protected Health Information or financial records), their impact on cash flow, and the level of system access they have. Assign each vendor a low, medium, or high risk rating using a consistent scoring method, such as a numbered scale or color-coded system. This classification helps determine the level of scrutiny each vendor requires and how often they should be monitored [7].
For example, in December 2022, Avem Health Partners faced a significant data breach that impacted over 271,000 patients. The breach stemmed from a security incident at their vendor, 365 Data Centers. This case highlights the importance of thoroughly assessing all vendors, regardless of their size or reputation [7].
Setting Key Metrics and Program KPIs
To ensure vendors meet your expectations, establish measurable goals. Define Key Performance Indicators (KPIs) that monitor both financial and operational performance. Focus on metrics like denial rates (aim to keep them below 5%), days in accounts receivable (A/R), breach-related costs, and first-pass resolution rates [4][11].
When drafting contracts, make sure performance metrics are clearly outlined. Specify how frequently performance will be reviewed, how metrics will be calculated, and the level of detail required in reports. For example, if a vendor’s denial rate exceeds 10%, this should trigger an immediate review [3].
Using Technology for Centralized Risk Management
Managing vendor risks manually through spreadsheets and emails can lead to critical oversights. A centralized platform simplifies the process by consolidating data, automating workflows, and providing real-time insights into risk scores and compliance statuses. Tools like Censinet RiskOps™ offer healthcare organizations a comprehensive view of third-party risks. This platform enables detailed vendor assessments, tracks performance, and visualizes risks across the entire vendor network. Features like automated workflows reduce administrative burdens, while Censinet AI™ speeds up tasks like completing security questionnaires and validating evidence, significantly cutting down assessment times.
Given that nearly 80% of organizations have formal vendor risk assessment programs but only about 30% have dedicated staff to manage them, automation becomes crucial [7]. A centralized system ensures nothing gets overlooked, routes important findings to the right stakeholders, and provides a clear audit trail for board reporting and regulatory compliance.
Managing Risks Across the Vendor Lifecycle
Managing vendor risks isn’t a one-time task - it’s an ongoing process that spans from initial evaluation to contract termination. Each stage requires specific security measures to safeguard your organization.
Pre-Contract Due Diligence and Risk Assessment
Before entering into any agreement, it’s crucial to evaluate the vendor’s security and operational capabilities. Start by requesting a comprehensive security questionnaire that covers areas like data handling practices, access controls, and incident response protocols. Additionally, verify the vendor’s compliance with relevant regulations using independent attestations.
Refer to your established risk categories to guide this assessment. Evaluate the vendor’s overall stability alongside the potential impact their service could have on your systems. Key areas to examine include financial health, compliance with regulations, technical capabilities, operational reliability, and reputation. Use your risk rating system to determine how the vendor’s services could affect your revenue cycle and overall operations [7].
Once risks are identified, you can move forward by setting clear expectations through detailed contracts and onboarding processes.
Contracting and Onboarding Best Practices
After completing due diligence, formalize the partnership with contracts that explicitly outline security and performance requirements. These agreements should include necessary Business Associate Agreements (BAAs) and specify data handling protocols such as encryption standards, data retention policies, and breach notification timelines.
Incorporate Service Level Agreements (SLAs) to define performance benchmarks, response times, and remediation steps. During onboarding, confirm that access controls are in place, data flows are secure, and monitoring systems are active. These measures ensure that the vendor is fully prepared before they manage any live patient or financial data.
Monitoring and Termination Protocols
Once the contract is in place, ongoing oversight is essential. Schedule regular reassessments - quarterly for high-risk vendors and annually for lower-risk ones - to confirm continued compliance with your security standards [12]. Leverage real-time monitoring tools such as network monitoring and anomaly detection systems to quickly identify suspicious activity, emerging threats, or vulnerabilities [12][14].
When it’s time to end a vendor relationship, implement a structured offboarding process to protect your organization. Immediately revoke access permissions, deactivate shared accounts, and update shared passwords. Ensure the vendor securely destroys any patient data they’ve handled, in line with your data retention policies. Obtain written confirmation of data destruction to close the loop [12][13]. A thorough termination process minimizes the risk of lingering security vulnerabilities tied to former vendors.
sbb-itb-535baee
Implementing Financial and Cyber Risk Controls
To tackle vulnerabilities in revenue cycle workflows, it's essential to implement controls that address both cybersecurity and financial risks. These safeguards must extend across all revenue cycle vendors to ensure comprehensive protection.
Key Control Areas for RCM Vendors
Start with Role-Based Access Control (RBAC) and Multi-Factor Authentication (MFA) to limit access to sensitive systems. Regularly review permissions to ensure they align with current roles. Implement continuous monitoring tools with behavioral analytics to detect unusual user activity. Adding Data Loss Prevention (DLP) mechanisms further reduces the risk of unauthorized data transfers [1][15][8].
For data protection and encryption, all Protected Health Information (PHI) and sensitive financial data should be encrypted both at rest and in transit. Use advanced encryption protocols like AES-256 and secure all communications with end-to-end encryption. Tokenization is another essential layer, particularly for safeguarding credit card information [1][15][8].
When it comes to financial transaction security, ensure that payment processing complies with PCI-DSS standards. Tokenize credit card data and integrate machine learning-based fraud detection tools to identify irregular transactions in real time [1].
These controls form the backbone of a secure and efficient system, paving the way for automation to further optimize risk management.
Integrating Automation and AI for Risk Management
Automation and AI can significantly enhance risk operations. AI-powered threat detection tools and machine learning algorithms can quickly identify cyberattacks and spot unusual financial transactions [1].
Take, for instance, Censinet AI™, which combines human oversight with autonomous automation. This approach ensures that risk teams maintain control through customizable rules and review processes, allowing automation to support, not replace, critical decision-making.
Automation also plays a role in streamlining processes like denial appeals. By using machine learning and advanced trend analysis, organizations can reduce financial risks and improve cash flow efficiency [5][6]. Pair this with robust issue management to address vulnerabilities as they arise.
Managing Issues and Remediation
Centralized issue tracking is critical for assigning responsibility, monitoring progress, and ensuring timely resolutions. Establish clear evaluation criteria for vendors, covering financial, compliance, technical, operational, and reputational risks [7].
Continuous monitoring, combined with regular performance assessments, ensures that issues are detected and addressed promptly. Use analytics to measure vendor performance, focusing on how effectively they resolve problems and meet deadlines. This approach not only creates accountability but also provides transparency into which vendors consistently meet security standards and which may need closer oversight.
Measuring Success and Improving Over Time
Connecting Vendor Risk to Financial Performance
Vendor risk management isn't just about reducing risks - it directly impacts financial health. To see this connection, track metrics like denial rates, days in accounts receivable, and net collection rates. These numbers tie back to your key performance indicators (KPIs) and highlight how vendor performance influences financial outcomes [2][16][17].
Security breaches are a costly example of how poor vendor management can hurt finances. On average, healthcare organizations lose $9.42 million per breach. Even worse, 66% of patients surveyed by Semafone said they’d switch providers if their data was compromised [19]. Considering that 90% of claim denials are preventable - and 65% of denied claims are never resubmitted - the financial stakes of vendor risk management become undeniable [6].
To stay on top of these challenges, set S.M.A.R.T. KPIs that align with your risk goals [18]. These indicators help you measure vendor outcomes while prioritizing long-term security over short-term cost savings. After all, the financial fallout from breaches, lawsuits, or fines often far exceeds any upfront savings [12][18].
Once the financial impacts are clear, effective reporting becomes the next critical step.
Reporting to Stakeholders
Streamlined reporting ensures that revenue cycle leaders, compliance teams, and board members get the information they need - without being bogged down by unnecessary technical details. Centralize vendor risk management data in dashboards that highlight regulatory updates, security concerns, vendor performance, and policy changes [12].
Include key metrics like billing performance, clean claims rates, net collections, and compliance scores in your reports [3][17]. To enhance accountability, outline the frequency, format, and participants of performance reviews directly in vendor contracts [3]. Real-time reporting tools can also empower stakeholders to monitor operations broadly or dive into specific claim statuses and vendor trends [6].
This regular reporting structure lays the groundwork for consistent improvements in managing vendor risks.
Creating a Continuous Improvement Process
Effective vendor risk management doesn’t stop after the initial assessment. Regularly review vendor performance data to identify areas for improvement. While 80% of organizations have formal vendor risk programs, nearly 30% still lack dedicated staff to oversee these efforts [7]. Vendors should be evaluated annually - or more often if they pose higher risks [7].
Dive into denial trends by analyzing payment and reason codes to uncover patterns and redesign processes that prevent future issues [6]. Review fee schedules annually to ensure they reflect updated rates, contracts, and allowable amounts, avoiding unnecessary revenue loss [16]. Bring in specialists from compliance, finance, IT, security, and legal teams to provide comprehensive insights during reviews and planning [7].
To keep improving, invest in regular training, monitor performance closely, and listen to patient feedback [17]. Stay ahead of regulatory changes and require vendors to adapt accordingly [7]. This ongoing cycle of evaluation and refinement ensures your vendor risk management strategies remain effective over time.
Conclusion
Managing vendor risks in the revenue cycle is a cornerstone of financial stability. With nearly half of U.S. healthcare providers outsourcing their revenue cycle operations[3], the potential for vulnerabilities - and their consequences - has never been greater. Each vendor relationship carries inherent risks that, if unchecked, could disrupt both financial and operational stability.
To address these risks effectively, organizations must implement a well-rounded vendor risk management strategy. This includes maintaining detailed vendor inventories, crafting performance-based contracts, conducting regular assessments, and keeping a close watch through continuous monitoring. Technology plays a vital role here, offering tools to centralize risk data and automate routine oversight tasks, making the process more manageable.
The challenges don’t stop at risk mitigation. A report from Kauffman Hall highlights that 92% of healthcare leaders face difficulties in attracting and retaining support staff[5]. This underscores the importance of thoughtful vendor selection and sustained monitoring to ensure operational resilience.
Vendor risk management isn’t static - it must adapt to an ever-changing landscape. As threats become more sophisticated, regulations shift, and operational needs evolve, organizations must adopt proactive, data-driven approaches. By aligning vendor performance with financial goals and leveraging transparent reporting, vendor risk management can move beyond compliance. It becomes a strategic tool that strengthens financial health and positions your organization for long-term success.
FAQs
What steps should healthcare organizations take to create a strong vendor risk management program for revenue cycle operations?
To set up a strong vendor risk management program, begin with a well-thought-out plan that pinpoints possible risks and lays out strategies to address them. Regularly assess vendors to gauge their cybersecurity measures, compliance standards, and operational dependability.
Leverage real-time monitoring tools to keep tabs on vendor performance and quickly tackle any emerging risks. Make sure your contracts clearly define service level agreements (SLAs), compliance obligations, and penalties for violations. Promote open communication and teamwork between your internal teams and vendors to ensure everyone stays on the same page and accountable.
What steps can healthcare organizations take to stay compliant with HIPAA and other regulations when working with revenue cycle management (RCM) vendors?
Healthcare organizations aiming to comply with HIPAA and similar regulations need to take deliberate and preventative actions. Start with regular staff training to ensure employees are well-versed in data privacy rules and understand the best practices for protecting sensitive information.
Next, bolster security by introducing strong cybersecurity measures. This includes using encryption, firewalls, and multi-factor authentication to create multiple layers of defense against potential threats.
It's also crucial to securely store both electronic and physical records. Access should be restricted to only those who are authorized, reducing the likelihood of unauthorized exposure. Lastly, have a clear and detailed incident response plan in place. This ensures your organization can respond quickly to data breaches or compliance issues, protecting patient information and minimizing any financial or operational fallout.
How does technology help healthcare organizations manage vendor risks in financial operations?
Technology plays a key role in managing vendor risks within healthcare financial operations. It simplifies risk assessments, offers real-time monitoring, and ensures secure communication through encrypted data. Tools powered by machine learning and analytics are particularly useful for spotting vulnerabilities like cybersecurity risks, compliance issues, and potential data breaches.
By automating tasks such as maintaining audit trails, generating clear reports, and responding to incidents, technology not only reduces administrative strain but also strengthens security. It helps organizations stay compliant with regulations like HIPAA and SOC 2, enabling healthcare providers to protect their financial operations with greater confidence.


