Role-Based Encryption for PHI: Compliance Best Practices
Post Summary
Role-based encryption is a game-changer for securing Protected Health Information (PHI) in healthcare. It pairs encryption with role-based access control (RBAC) to ensure only specific job roles can access sensitive patient data. This approach enforces HIPAA's "minimum necessary" standard by limiting data access based on responsibilities, reducing risks of unauthorized exposure.
Key Highlights:
- What It Is: Role-based encryption ties decryption privileges to job roles, ensuring access aligns with specific duties.
- Why It Matters: It strengthens HIPAA compliance by protecting electronic PHI (ePHI) and builds patient trust.
- How to Implement:
- Map PHI data and assess risks.
- Define roles and enforce RBAC.
- Use strong encryption standards (e.g., AES-256) and centralized key management.
- Encrypt data at rest and in transit, including backups and devices.
- Integrate encryption with IAM systems for automated access control.
Compliance Essentials:
- Follow HIPAA Security Rule safeguards like Access Control (§164.312(a)) and Audit Controls (§164.312(b)).
- Use FIPS 140-validated encryption standards and maintain detailed audit logs.
- Manage third-party risks with Business Associate Agreements (BAAs) and tools like Censinet RiskOps for vendor assessments.
By combining encryption with role-based access, healthcare organizations can meet regulatory requirements while safeguarding patient data. Start by evaluating your current practices, updating policies, and training teams to ensure your encryption strategy aligns with compliance standards.
Regulatory Requirements for Role-Based Encryption
HIPAA Security Rule Requirements
The HIPAA Security Rule (45 CFR Part 164, Subpart C) outlines technical safeguards that healthcare organizations must follow to implement role-based encryption effectively. A major focus is Access Control (§164.312(a)), which requires organizations to assign unique user IDs, establish emergency access procedures, enforce automatic logoff, and implement encryption and decryption mechanisms for electronic protected health information (ePHI) [5]. These measures ensure that decryption capabilities are tied to specific roles, limiting access to authorized personnel only.
Audit Controls (§164.312(b)) mandate logging all data access and decryption activities, providing a clear record for compliance purposes [5]. Meanwhile, Person or Entity Authentication (§164.312(d)) ensures that users are properly verified, often through multi-factor authentication integrated with role-based access systems. The Integrity standard (§164.312(c)) further protects ePHI by requiring safeguards to prevent unauthorized alterations or destruction. Encryption, paired with tools like checksums and database integrity controls, ensures that only authorized roles can make changes to sensitive data [5]. Together, these safeguards create a secure framework for role-based encryption.
How Role-Based Encryption Meets Compliance Standards
Role-based encryption aligns with HIPAA’s "minimum necessary" standard (45 CFR 164.502(b)) by restricting access to only the information essential for an individual’s job duties. While encryption is considered an "addressable" control under HIPAA - allowing for alternative measures if encryption isn’t feasible - current cybersecurity threats make encryption a practical and widely adopted choice [6]. Most healthcare organizations follow NIST guidelines (e.g., SP 800-66, SP 800-53, and SP 800-111) and use FIPS 140-validated algorithms like AES to meet these requirements [6]. This approach ensures both compliance and robust data protection.
Business Associate and State Regulation Requirements
Expanding on role-based access principles, additional regulations emphasize strict oversight of vendors and third parties. Any service provider handling PHI must sign a Business Associate Agreement (BAA), which clearly defines access control responsibilities. These agreements typically require the use of role-based access control (RBAC), least privilege principles, and unique user IDs. While vendors share encryption and key management duties, the covered entity remains ultimately responsible for ensuring that business associates maintain the required safeguards.
State-level privacy and security laws often impose even stricter requirements, particularly regarding breach notifications when PHI is left unencrypted. These heightened standards have prompted organizations to adopt strong encryption and role-based access as default practices [6]. Tools like Censinet RiskOps simplify vendor risk assessments and facilitate secure data-sharing, helping organizations verify ongoing compliance with BAAs [1]. Continuous monitoring is critical for adapting to regulatory changes and ensuring that business associates uphold the same security standards as the organization’s role-based encryption model.
How to Design a Compliant Role-Based Encryption Model
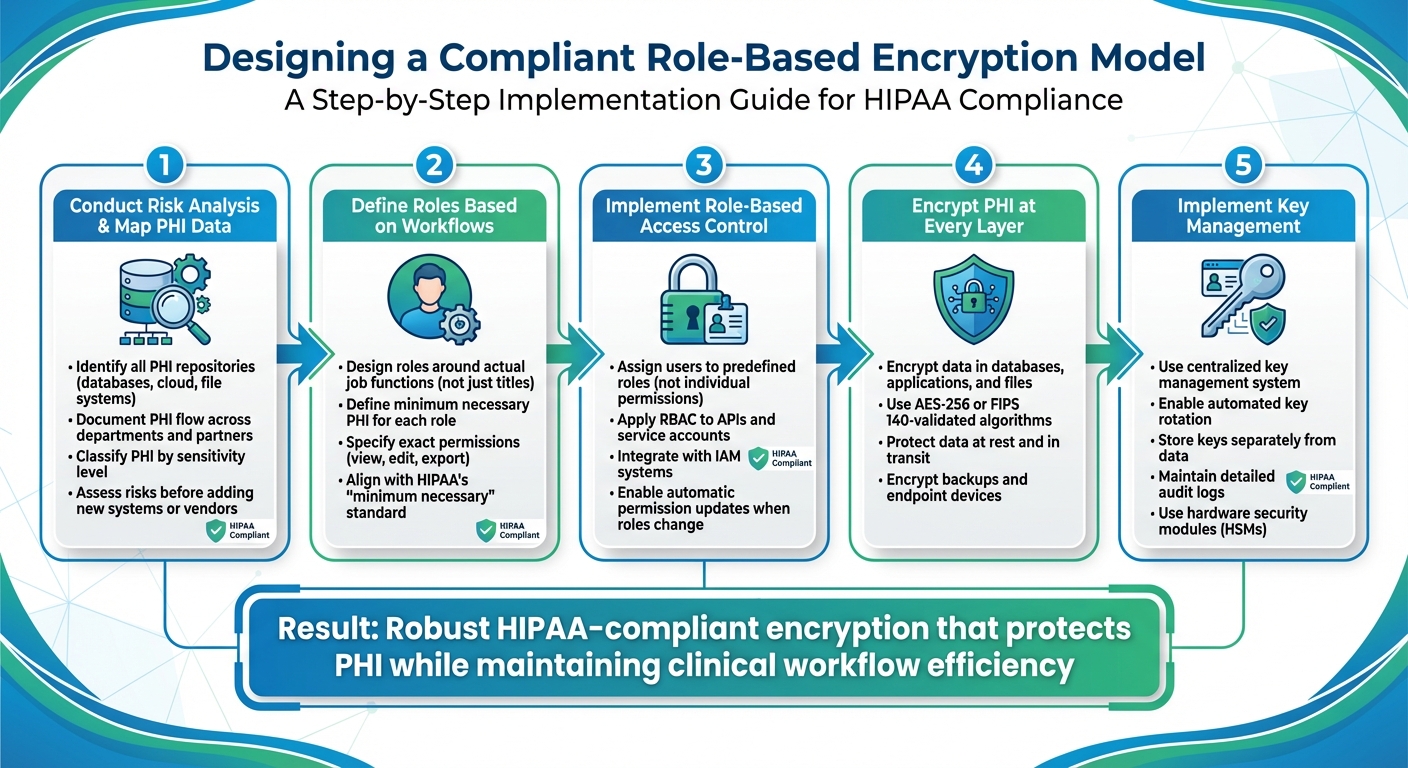
5-Step Role-Based Encryption Implementation Process for HIPAA Compliance
Conduct Risk Analysis and Map PHI Data
Start by identifying where Protected Health Information (PHI) is stored and how it moves within your organization. This includes mapping out all PHI repositories like databases, cloud storage, file systems, and any third-party platforms. A thorough inventory of PHI is the backbone of any encryption strategy. Document how PHI flows - where it originates, who accesses it, how it moves, and where it is stored - by detailing interactions across departments, roles, and external partners.
Incorporate risk assessments into your change management process. Before adding new roles, applications, cloud services, or vendors, evaluate their potential impact on PHI security [3]. This proactive step helps avoid security gaps and ensures encryption policies evolve with infrastructure changes. Additionally, classify PHI based on its sensitivity - such as basic demographics, clinical notes, mental health records, or substance abuse treatment information. This categorization guides decisions on encryption strength and access restrictions.
With a complete understanding of your PHI inventory and associated risks, you can move forward with defining roles for encryption access.
Define Roles and Implement Encryption
Design roles based on actual workflows in healthcare settings rather than just job titles. For instance, the PHI access needs of a billing specialist will differ significantly from those of an emergency room physician or a quality assurance analyst. For each role, outline the minimum PHI required and specify exact permissions, such as viewing, editing, or exporting data, in line with HIPAA's "minimum necessary" standard [2][3].
Instead of assigning permissions to individuals, associate users with predefined roles. This approach simplifies audits, makes access policies more manageable, and ensures permissions can be easily updated when staff members change roles or leave the organization [3]. Encrypt PHI at every layer - whether in databases, applications, or files - to protect it throughout its lifecycle. Extend role-based access to APIs, service accounts, and batch processes by using secure Identity and Access Management (IAM) systems and strong authentication mechanisms.
Choose Cryptographic Standards and Key Management Solutions
Once roles are defined and encryption is in place, finalize your model with robust cryptographic standards and effective key management. Use modern, industry-recognized encryption protocols for both data at rest and data in transit, avoiding outdated or insecure options.
Centralized key management is crucial. It should support automated key rotation, secure storage (ideally using hardware security modules), and detailed audit logging. By storing encryption keys separately from the data and enforcing strict controls over key generation, retrieval, and revocation, you add an extra layer of protection. Even if unauthorized access occurs, properly managed keys ensure PHI remains secure.
Technical Best Practices for Implementation
Encrypt PHI at Rest and in Transit
Safeguarding Protected Health Information (PHI) starts with encryption - both where the data resides and as it moves. For data at rest, rely on AES-256 or other FIPS 140-validated algorithms. These meet NIST guidelines and align with the HIPAA Security Rule [6][4]. To simplify encryption for entire databases, enable Transparent Data Encryption (TDE) in systems like SQL Server, Oracle, and PostgreSQL. For especially sensitive data, such as Social Security numbers or mental health records, add an extra layer of protection with field-level or column-level encryption [4].
Don't forget about backups and devices. Encrypt backup media and snapshots using protections equal to or stronger than those for primary storage, whether they’re on-premises or cloud-based [4]. Apply full-disk or volume encryption to file systems, and enforce encryption on endpoint devices like laptops, tablets, and mobile phones that might store PHI. Regularly test encrypted backups through restoration drills to ensure they’re functional [4].
When PHI is in transit, secure it with TLS 1.2 or higher for all transmissions, whether across internal networks, APIs, or external systems. Configure TLS with strong cipher suites, and disable outdated protocols like SSL 3.0 and TLS 1.0. Even internal traffic within your network should be encrypted. Additionally, make sure encryption keys are securely managed and stored separately [4].
Integrate Encryption with RBAC and IAM Systems
Strong encryption is just the first step - controlling access to decrypted data is just as crucial. Integrate encryption protocols with Role-Based Access Control (RBAC) and Identity and Access Management (IAM) systems to ensure only authorized users can access PHI. For instance, define role-specific permissions through role catalogs that align with job functions and data sensitivity [3]. A nurse might access clinical notes, while a billing specialist could view account details but not sensitive health information [2][3].
Limit decryption privileges to only those roles that require it. Configure applications and databases to allow decryption exclusively for authorized processes [4]. Enforce the principle of least privilege by restricting key access to specific roles and setting up automatic session timeouts and re-authentication for systems handling PHI [2]. If an employee changes roles or leaves the organization, ensure your IAM system revokes their decryption permissions immediately - no manual intervention needed.
Use Cloud-Native Security Features
As healthcare increasingly adopts cloud environments, leverage the security tools provided by major U.S. cloud platforms like AWS, Azure, and Google Cloud. These providers offer built-in encryption features tailored for PHI workloads. Enable default encryption at rest using provider-managed keys for databases, storage buckets, and virtual machine disks. For enhanced control, opt for customer-managed keys stored in services like AWS KMS, Azure Key Vault, or Google Cloud KMS. Use IAM policies to tightly restrict access to these keys based on specific roles.
Take advantage of native monitoring and auditing capabilities to maintain encryption compliance. Activate detailed audit logs to track access attempts, decryption activities, and any changes to encryption policies. Set up alerts for unusual activity, such as a role decrypting large amounts of PHI or accessing data during off-hours. Cloud platforms also offer dashboards and compliance reports to help demonstrate to auditors that your technical safeguards are in place and working as intended.
sbb-itb-535baee
Maintaining Compliance Through Governance and Monitoring
Staying compliant with encryption requirements isn't just about having the right technical tools; it also requires strong governance and constant oversight.
Establish Policies and Train Your Workforce
Encryption can only work effectively when paired with well-defined policies and a knowledgeable workforce. Start by creating an encryption governance model with clear ownership. Assign an executive - often the CISO or CIO - to take charge of safeguarding PHI encryption and ensuring HIPAA compliance. Build a multidisciplinary team that includes IT, security, compliance, legal, and clinical leaders. This group should meet at least quarterly to review encryption policies, access controls, and any exceptions. Clearly document roles and responsibilities in policies that align with HIPAA requirements and measurable performance indicators.
Training is equally important. All staff should be educated on PHI handling and encryption protocols during onboarding and through annual refreshers. Tailor the training to specific roles: clinical staff need to understand secure device usage and the principle of minimum necessary access, billing teams must grasp how encryption protects sensitive account data, and IT professionals require advanced training on key management, decryption processes, and logging. Keep track of training completion to ensure everyone is equipped to use role-based encryption properly and maintain HIPAA compliance.
Monitor and Audit Encryption Practices
HIPAA mandates audit controls to track and analyze activities involving electronic PHI [5]. Centralize logging across all PHI systems to capture key activities like authentication, decryption, key access, and policy changes. Set up alerts to flag unusual behaviors and review logs monthly, conducting full audits quarterly. These reviews help identify trends that could signal misuse or unauthorized access to encrypted PHI.
Go a step further by using behavioral analytics to catch anomalies that standard logs might miss. For instance, if a billing clerk suddenly accesses clinical records outside their usual scope, the system should flag this for investigation. Maintaining a detailed audit trail - including who accessed what data, when, and from which device - is critical for HIPAA compliance and can be vital during OCR investigations or in the event of reportable breaches. Organizations with strong encryption practices and thorough audit controls often face fewer enforcement actions and build a more reliable compliance track record with HHS [6].
These internal safeguards should also extend to managing risks posed by third-party vendors.
Manage Third-Party Risks with Censinet
Beyond internal audits, it's crucial to apply these compliance measures to third-party vendors. Vendors handling PHI can introduce significant risks that traditional review processes may not fully address. Censinet RiskOps™ provides a specialized platform designed for healthcare, simplifying vendor risk assessments and verifying encryption compliance across external systems. This platform connects healthcare organizations with a collaborative risk network of over 50,000 vendors and products, enabling secure sharing and access to cybersecurity and risk data.
Tower Health's CISO, Terry Grogan, shared, "Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required." [1]
Baptist Health's VP & CISO, James Case, noted, "Not only did we get rid of spreadsheets, but we have that larger community [of hospitals] to partner and work with." [1]
Faith Regional Health's CIO, Brian Sterud, added, "Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters." [1]
Conclusion and Key Takeaways
Summary of Best Practices
Role-based encryption for PHI is a cornerstone of a strong security framework, safeguarding patient data while ensuring clinical workflows remain smooth. To achieve this, start with a comprehensive risk analysis and PHI data mapping to pinpoint where electronic PHI resides and how it moves within your systems. Clearly define roles that align with specific job responsibilities and implement RBAC to restrict access to only what's necessary. Pair this with robust cryptographic standards and reliable key management solutions for added security. Beyond the technical aspects, it's essential to have continuous monitoring and auditing in place to track access events, encryption usage, and key management - this helps detect potential misuse early and provides crucial evidence for regulatory purposes. Rounding out these measures, prioritize workforce training and maintain oversight of third parties through business associate agreements and vendor evaluations.
When done right, role-based encryption offers more than just regulatory compliance. Centralized RBAC and encryption policies lead to better audit logs and stronger documentation, which can make a difference in OCR investigations, potentially lowering enforcement risks. Plus, organizations that adopt proactive, standards-driven security measures often gain greater trust from patients, partners, and regulators - an invaluable edge in a healthcare industry frequently shaken by data breaches.
With these practices in mind, now is the time to take immediate steps to strengthen your encryption strategy.
Next Steps for Healthcare Organizations
The outlined best practices provide a clear roadmap for action. Begin by evaluating your current encryption and RBAC practices against HIPAA Security Rule requirements. Check whether PHI is consistently encrypted across all environments, including production systems, backups, logs, and test setups - gaps in encryption coverage are a common issue. Over the next 30 to 90 days, focus on updating your policies and enhancing training programs, ensuring all key teams are well-prepared and documentation is up to date.
For managing third-party risks, explore platforms designed to simplify vendor assessments and ensure encryption compliance. Censinet RiskOps™ offers healthcare-specific tools to help reduce risks continuously. It allows organizations to benchmark their cybersecurity stance, collaborate with a network of over 50,000 vendors, and track remediation efforts with ease.
Investing in role-based encryption, IAM systems, and specialized risk management tools is more than a technical upgrade - it's a demonstration of due diligence that builds trust with patients, partners, and regulators. When security measures are thoughtfully integrated with usability through well-designed roles, encryption becomes seamless, making access management easier while proving that robust protection can coexist with clinical efficiency. This alignment ensures both security and operational success.
FAQs
How does role-based encryption help meet HIPAA compliance requirements?
Role-based encryption plays a crucial role in bolstering HIPAA compliance by restricting access to Protected Health Information (PHI) based on an individual's specific role within an organization. This means that only those with a legitimate purpose tied to their job responsibilities can view sensitive data, significantly lowering the chances of unauthorized access or data breaches.
On top of that, this method enhances compliance efforts by making it easier to track and audit who accessed what information and when - an essential requirement under HIPAA. By aligning data access with specific job functions, organizations can better safeguard patient privacy while adhering to regulatory obligations.
How can I effectively implement role-based encryption for PHI compliance?
To put role-based encryption into action while staying compliant with healthcare regulations like HIPAA, start by establishing well-defined roles and access policies. These should be tailored to job functions and responsibilities within your organization. Instead of assigning encryption keys to individuals, tie them to specific roles. This simplifies access control and minimizes the chances of unauthorized access.
Make sure to implement secure key management practices. Use strong encryption algorithms and restrict access to encryption keys to only those who absolutely need it. Regularly review and audit access logs to spot any unusual activity or potential security issues. It's also crucial to update your policies and encryption protocols regularly to keep pace with changing regulations and new security challenges.
Taking these steps helps ensure the protection of sensitive health information (PHI) while meeting the required industry standards.
How can healthcare organizations use role-based encryption to reduce third-party risks?
Healthcare organizations can better manage third-party risks by using role-based encryption, which ensures that sensitive data, like protected health information (PHI), is accessible only to individuals based on their specific roles and responsibilities. This targeted access helps limit exposure to unauthorized personnel, reducing the chances of data breaches while staying in line with regulations such as HIPAA.
By adopting robust access controls and encryption protocols, organizations can protect PHI across their systems and those of third-party vendors. Additionally, healthcare risk management platforms can simplify this process by enforcing encryption policies consistently and addressing potential vulnerabilities within the supply chain.


