Rural Hospital Vendor Risk Management: Resource Constraints and Critical Dependencies
Post Summary
Rural hospitals face mounting challenges in managing vendor risks, including tight budgets, staffing shortages, and outdated technology. These facilities rely on external vendors for critical services like electronic health records (EHR) and medical equipment maintenance, but limited resources leave them vulnerable to cyberattacks and system failures.
Key issues:
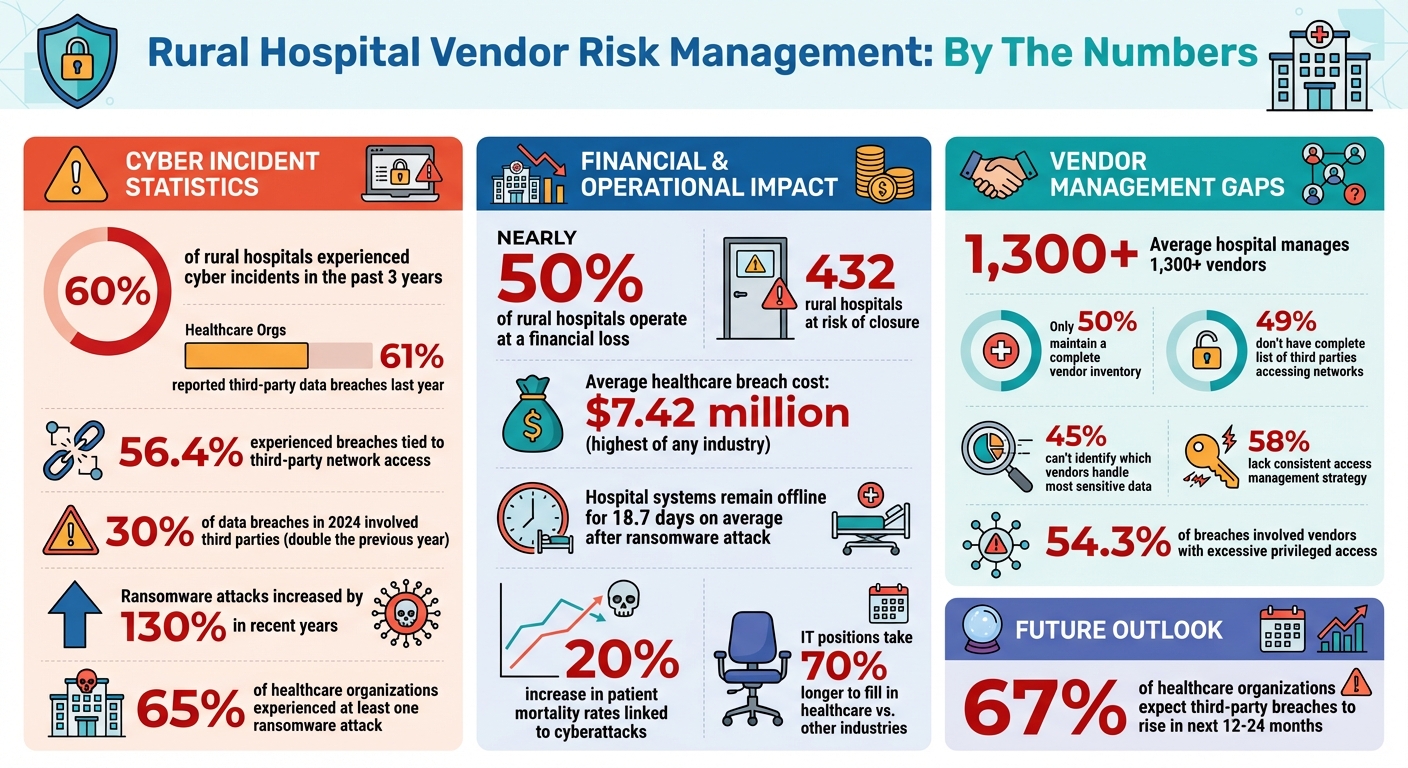
- 60% of rural hospitals experienced cyber incidents in the past three years.
- Nearly half operate at a financial loss, with 432 at risk of closure.
- Many lack dedicated IT staff, relying on generalists without security expertise.
Vendor overdependence and poor oversight amplify risks:
- 61% of healthcare organizations reported third-party data breaches last year.
- Only 50% maintain a complete vendor inventory; fewer monitor vendor security practices.
Actionable steps for rural hospitals:
- Build a vendor inventory: List all vendors, their access levels, and data handled.
- Implement risk tiering: Classify vendors into high, medium, and low-risk groups.
- Strengthen contracts: Include breach notification timelines and security protocols.
- Plan for failures: Create incident response plans and manual workarounds for outages.
- Leverage tools: Use automation platforms like Censinet RiskOps™ to streamline risk assessments.
Rural Hospital Vendor Risk Management Statistics and Key Challenges
Resource Limits and Vendor Dependencies in Rural Hospitals
Resource Challenges Impacting Vendor Risk Management
Rural hospitals are under constant strain, juggling tight budgets, staff shortages, and outdated technology. These challenges force them to focus on immediate clinical needs, often leaving cybersecurity on the back burner. With limited funds, these hospitals struggle to implement strong vendor risk management practices. IT teams, often made up of generalists without specialized security training, are left to handle increasingly complex risks. To make matters worse, filling specialized IT roles in healthcare can take up to 70% longer compared to other industries [3].
Adding to the problem, many rural hospitals rely on aging infrastructure and legacy systems, which often lack vendor support and are more vulnerable to cyberattacks. Without essentials like multi-factor authentication, data encryption, or regular monitoring, these facilities are left exposed. They also lack the resources to thoroughly vet third-party vendors or conduct detailed security assessments, making them particularly vulnerable to supply chain risks. These internal limitations make the situation even more precarious when combined with an overdependence on a handful of key vendors.
Risks of Overdependence on Critical Vendors
Rural hospitals often rely heavily on a small group of external vendors for crucial services like electronic health records, telehealth platforms, medical equipment maintenance, and picture archiving systems. This dependency creates serious risks. If one of these vendors experiences a cyberattack or system failure, rural hospitals have few backup options and limited ability to respond.
The numbers tell a worrying story: 61% of healthcare organizations reported a third-party data breach in the past year, and 56.4% experienced breaches tied to third-party network access [7]. In over half of these cases (54.3%), vendors with excessive privileged access became entry points for attackers, exposing multiple healthcare systems. Shockingly, only about half of healthcare organizations maintain a complete inventory of third parties with network access. Even fewer routinely evaluate or monitor vendor security practices - 58% lack a consistent access management strategy [7]. These gaps in oversight leave rural hospitals particularly vulnerable to external threats.
Threats Stemming from Vendor Failures
When vendors fail, the consequences for rural hospitals can be immediate and severe. Ransomware attacks, for example, have skyrocketed by nearly 130% in recent years, with the healthcare sector being hit harder than any of the other 16 critical infrastructure sectors in the U.S. [6][3]. The rise of ransomware-as-a-service has made cybercrime more sophisticated, with attackers employing double extortion tactics - demanding payment not only to unlock systems but also to prevent the release of stolen patient data.
The fallout from these attacks can be devastating. On average, hospital systems remain offline for 18.7 days after a ransomware attack. During this time, hospitals are forced to revert to manual processes, delay patient care, and sometimes divert emergency cases to other facilities [3]. The financial impact is staggering, with healthcare breaches costing an average of $7.42 million - the highest of any industry [7]. For rural hospitals already operating on razor-thin margins, such disruptions can be catastrophic. Alarmingly, two-thirds of healthcare organizations expect third-party data breaches to rise in the next 12 to 24 months [7].
Core Vendor Risk Management Practices for Rural Hospitals
Basic VRM Components for Rural Hospitals
Rural hospitals operate with limited staff, tight budgets, and often juggle oversight of more than 1,300 vendors [5]. To tackle vendor risk management effectively, these hospitals need a straightforward approach that prioritizes protection without overloading small teams. A good starting point is creating a vendor inventory - a comprehensive list of every third party with access to systems or patient data. Once that’s done, implement risk tiering to categorize vendors based on their potential impact. High-risk vendors should receive more rigorous oversight, while low-risk ones can be monitored with less intensity.
Detailed due diligence doesn’t have to be exhaustive. Focus on critical vendors and set up continuous monitoring to track changes in their security practices and to identify any new vulnerabilities. The American Hospital Association has emphasized the dangers of cyberattacks targeting third-party providers, noting that such attacks can have "national consequences" and often cause more damage than direct attacks on hospitals [5].
Two other practices can make a big difference in improving vendor risk management. First, clearly assign roles and responsibilities for managing vendor risks - both internally and with vendors. Second, create a Plan of Action and Milestones (POA&M) to track how identified risks are being addressed. This plan should outline specific tasks, resources needed, milestones, and deadlines [5]. These steps ensure accountability and prevent risks from being overlooked. Together, these foundational practices help rural hospitals align their vendor risk management with HIPAA requirements.
Meeting HIPAA and Regulatory Requirements Through VRM
HIPAA compliance demands consistent and well-documented vendor management. On January 6, 2025, the Department of Health and Human Services proposed updates to the HIPAA Security Rule, making it more flexible and scalable. These updates acknowledge the unique challenges faced by small and rural providers while introducing clearer requirements for tasks like maintaining an accurate technology inventory, conducting risk analyses, implementing patch management, enabling multi-factor authentication, and performing compliance audits [9].
A key component of HIPAA-aligned vendor management is the Business Associate Agreement (BAA). These agreements outline vendor services and their HIPAA obligations and must be regularly reviewed [8]. Your vendor inventory plays a pivotal role here by identifying which vendors are subject to regulatory requirements, particularly those handling electronic protected health information (ePHI). By combining properly reviewed BAAs with effective risk tiering and regular assessments, rural hospitals can build a manageable and defensible compliance strategy.
Vendor offboarding is another critical piece. Contracts should include provisions for returning or securely destroying data, terminating access, and conducting final security audits when a vendor relationship ends. These steps help eliminate lingering access points that could become security vulnerabilities [5].
Using Censinet for Scalable Risk Management
Once compliance and due diligence processes are in place, technology can help scale these efforts. Rural hospitals need tools that work within their resource limits, and Censinet RiskOps™ offers a solution tailored to this challenge. The platform simplifies third-party risk assessments by automating workflows, cutting down on the manual back-and-forth typically required for gathering vendor security documentation. With Censinet Connect™, standardized vendor risk assessments are streamlined, making collaboration with vendors more efficient.
For even faster assessments, Censinet AITM™ allows vendors to complete security questionnaires in seconds. The platform automatically summarizes vendor evidence, captures integration details, identifies fourth-party risks, and generates comprehensive risk reports. While automation handles much of the heavy lifting, human oversight ensures critical decision-making remains in the hands of hospital staff.
Censinet’s auto-scoring feature prioritizes vendor risks based on customizable criteria, helping hospitals direct their limited resources toward the most pressing concerns. With a centralized dashboard for real-time risk visualization and continuous monitoring, rural hospitals can maintain a clear view of their vendor ecosystem without needing to expand their team. This approach turns vendor risk management into a manageable, systematic process that fits comfortably within the constraints of smaller hospitals.
Practical Methods for Risk Prioritization and Oversight
Building a Vendor Inventory and Risk Tiering System
For rural hospitals with limited resources, prioritizing risks efficiently is a must. The first step? Create a detailed vendor inventory. Shockingly, nearly half of organizations - 49% - don’t have a complete list of third parties accessing their networks, and 45% can’t pinpoint which vendors handle their most sensitive data [11]. Considering that rural hospitals manage an average of over 1,300 vendors, this lack of visibility can lead to major vulnerabilities [5]. Start by listing each vendor, identifying the systems they access, and noting the type of data they handle.
Once you’ve built this inventory, implement a risk tiering system to classify vendors into low, medium, and high-risk categories. This helps small teams focus their attention where it matters most. Vendors handling protected health information (PHI) or providing essential clinical services, like electronic medical records (EMR), often fall into the high-risk category. For example, a breach involving a high-risk EMR vendor could result in millions of compromised records and costly settlements [12]. Risk tiering ensures that oversight efforts are directed toward the most critical areas.
Risk Prioritization Criteria for Rural Hospitals
Prioritizing risks effectively means looking beyond data sensitivity alone. Four key factors should guide this process: data sensitivity, service criticality, system integration, and the difficulty of replacing a vendor. For instance, while a patient scheduling system may not handle as much PHI as your billing provider, a failure in that system could bring operations to a standstill [11]. These criteria build on the vendor inventory and risk tiering efforts, creating a well-rounded oversight strategy.
It’s also important to consider the broader consequences of vendor failures. As Steve Ryan, Senior Manager of BARR's Attest Services Practice and Head of BARR's Healthcare Services, explains:
vendor security isn't just an IT issue - it's a patient safety issue [12].
The stakes are high. In 2024, 30% of data breaches involved third parties - double the rate from the previous year [12]. This makes a thoughtful, prioritized approach to vendor oversight not just smart, but necessary.
Using Tools and Automation to Reduce Manual Oversight
For small teams, automation can be a game-changer. Manually managing vendor oversight simply isn’t scalable. Tools like Censinet RiskOps™ tackle this problem by automating time-consuming workflows. The platform consolidates vendor risk data into a single, user-friendly dashboard, eliminating the chaos of juggling spreadsheets and email chains. Censinet AI™ takes it a step further, speeding up security assessments by allowing vendors to quickly complete questionnaires, summarizing evidence, and flagging potential risks from fourth-party relationships.
Additionally, rural hospitals can benefit from partnerships with federal and state programs that offer cost-effective security solutions. For example, the Small Rural Hospital Improvement Program (SHIP) provides eligible hospitals with about $13,000 annually to invest in health information technology, equipment, and cybersecurity training [4]. These resources enable small teams to access high-quality tools without breaking the bank.
sbb-itb-535baee
Low-Cost Vendor Due Diligence and Compliance
Simplified Security Assessments for High-Risk Vendors
Rural hospitals don’t need to spend a fortune or rely on overly complicated processes to ensure vendor security. The HIPAA Security Rule allows flexibility, acknowledging that smaller organizations operate differently than large health systems [16]. A good starting point? Streamlined questionnaires that focus on the essentials: Is there a current Business Associate Agreement? How is protected health information encrypted? What’s the breach notification process? For high-risk vendors managing sensitive data or critical systems, check for HIPAA compliance by reviewing recent risk assessments and audit reports. These straightforward assessments help lay the groundwork for strong contractual safeguards.
Adding Security Requirements to Vendor Contracts
Vendor contracts are more than just agreements - they’re key tools for compliance. Make sure they include specific terms like data handling protocols, breach notification timelines (24–48 hours), and audit rights. Your hospital’s compliance isn’t just about what you do - it extends to your vendors as well. When renegotiating contracts, look for opportunities to improve security while keeping costs in check [15].
But here’s the real game-changer: finding vendors who act like genuine partners. HFMA suggests healthcare leaders ask:
Will this vendor understand my organization's unique challenges? Will they be responsive? Do they have a proven record with hospitals like mine? [14]
Vendors familiar with the realities of rural healthcare are more likely to collaborate on practical security measures, saving you from the need for costly legal reviews. Plus, using publicly available resources to align contract terms with security requirements makes compliance more attainable.
Federal and State Resources for Rural Hospitals
Rural hospitals have access to several funding sources and free tools to help manage vendor risks. For instance, the Small Rural Hospital Improvement Program (SHIP) offers about $13,000 annually to eligible hospitals. These funds can cover health IT needs, cybersecurity training, or even vendor management software [4]. Another valuable resource is the free "Cybersecurity Toolkit for Rural Hospitals and Clinics" from RuralCenter.org. This toolkit includes checklists, guides, and tools tailored for hospitals with limited resources [17].
Outsourcing can also be a smart move for resource-strapped hospitals. As the NRHA points out:
Critical access hospitals often operate with limited resources, warranting outsourcing or automation to manage vendor risks effectively [13].
Incident Response and Business Continuity for Vendor Failures
Adding Vendors to Incident Response Plans
When a critical vendor experiences a breach or goes offline, having a well-prepared incident response plan can make all the difference. Unfortunately, many rural hospitals still lack structured plans that specifically address vendor failures [1][2]. To prepare, identify potential vendor-related scenarios - like electronic health record (EHR) or lab system outages - and assign clear responsibilities for contacting vendors, notifying staff, and escalating issues. These scenarios should be seamlessly integrated into your existing incident response framework, complete with well-defined communication protocols.
Healthcare organizations accounted for 41% of all third-party breaches in 2024 [5]. To prepare for such incidents, establish direct emergency contacts with each critical vendor. Test these contacts quarterly, and include vendors in tabletop exercises to ensure everyone knows their role during a system failure. Make sure to document key details like vendor notification procedures, expected response times, and backup communication channels in case primary methods are unavailable.
These steps not only help you respond to crises but also ensure you're ready to maintain essential operations when vendor systems fail.
Business Continuity Planning for Vendor Outages
To keep patient care uninterrupted during vendor outages, document manual workarounds for critical processes. Cyberattacks on hospitals have been linked to a 20% increase in patient mortality rates due to delayed care [1][2]. A solid business continuity plan must answer this crucial question: How will you continue providing care if critical vendors can’t deliver their services? For each essential vendor, outline alternative workflows - whether it’s switching to paper charts, using backup systems for lab orders, or creating contingency plans for medication administration when digital systems are down.
Focus restoration efforts on systems that directly impact patient care. For example, life-saving equipment and emergency department systems should take precedence, while less critical functions, like billing, can be addressed later. Also, maintain tight control over vendor access to your network. Knowing who has access and when is essential for ensuring accountability and compliance [10]. Regularly test your downtime procedures and measure how long it takes staff to transition to manual processes. This helps establish a baseline for improvement and ensures smoother operations during future outages.
Metrics to Measure Recovery and Preparedness
Once your incident response and continuity plans are established, tracking performance metrics is key to evaluating recovery and preparedness. Start with Mean Time-to-Repair (MTTR) to measure how quickly systems are restored. Beyond MTTR, monitor metrics like staff participation in downtime training and vendor involvement in emergency exercises. For instance, track how long it takes to detect an issue, resolve it, and fully restore systems. Analyze vendor performance during these incidents to identify any weak points in your partnerships.
Other useful metrics include the percentage of staff completing downtime training each quarter, the duration of your last tabletop exercise, and whether vendors actively participated. These measurements can uncover preparedness gaps before they turn into emergencies. With over 65% of healthcare organizations experiencing at least one ransomware attack [8], tracking readiness is crucial to protecting patients and maintaining operations when vendor failures occur.
Conclusion
Creating an effective vendor risk management program is achievable, even for rural hospitals with limited resources. The key lies in smart prioritization and leveraging the right tools. Alarmingly, 60% of rural hospitals have faced a cyber incident in the past three years [2][1]. However, by adopting scalable strategies, these facilities can minimize risks without overextending their resources.
Start by focusing on critical vendors, enforcing robust cybersecurity contracts, and incorporating vendor-related scenarios into your response plans. This practical, step-by-step approach ensures progress over time. While vendor risks are a significant challenge for rural hospitals [2][1], addressing them systematically can help safeguard patient care and maintain operational stability.
Advanced tools can make this process even more manageable. For example, Censinet RiskOps™ simplifies vendor risk management by automating assessments, centralizing vendor data, and enabling collaborative oversight - all without requiring additional staff. Paired with Censinet AITM™, hospitals can accelerate tasks like completing questionnaires and validating evidence, cutting down the time needed for thorough vendor evaluations while ensuring human oversight remains intact.
Considering that the average hospital works with over 1,300 vendors [5], third-party breaches can be even more damaging than direct attacks [5]. Your vendor risk management program doesn’t have to be flawless from the start - it just needs to be actionable, adaptable, and continuously improving. By implementing these practical steps and leveraging advanced tools, rural hospitals can protect patient care, reduce vendor-related risks, and maintain operational continuity even with limited resources.
FAQs
What steps can rural hospitals take to manage vendor risks despite limited resources?
Rural hospitals can tackle vendor risks by emphasizing prioritization and efficiency in their approach. Start by pinpointing the vendors whose services are most critical to daily operations and patient safety. These vendors should be the focus of detailed risk assessments, with contracts clearly outlining cybersecurity requirements to address any potential weaknesses.
Given the challenge of limited resources, rural hospitals can turn to budget-friendly solutions like cloud-based security tools and enforce multi-factor authentication to tighten access controls. Maintaining open communication and keeping a close watch on vendor activities are equally important to ensure compliance and reduce risks. By concentrating on these practical steps, rural hospitals can strengthen their defenses without straining their financial resources.
What risks come with relying too heavily on a few key vendors in rural hospitals?
Relying too much on just a few key vendors can spell trouble for rural hospitals. This kind of dependence can lead to serious operational challenges, especially if a vendor faces issues like system outages or cyberattacks. Such disruptions can make it harder to keep vital services running smoothly.
On top of that, putting all your eggs in one basket increases supply chain risks. If a vendor struggles to deliver necessary tools, technologies, or services on time, it could lead to delays that directly affect patient care. Even worse, it might jeopardize data security - something no healthcare provider can afford to compromise. These kinds of issues can erode both trust and regulatory compliance, two pillars of effective healthcare management.
To reduce these risks, rural hospitals should aim to work with a broader range of vendors, conduct thorough risk assessments, and develop strong oversight processes that fit within their limited resources. Diversification and proactive management can go a long way in safeguarding operations and patient care.
How does Censinet RiskOps™ support rural hospitals in managing vendor risks effectively?
Censinet RiskOps™ takes the hassle out of vendor risk management for rural hospitals by automating tedious tasks like risk assessments and compliance reviews. It pinpoints high-risk vendors, helping hospitals allocate their limited resources to the areas that need the most attention.
With features like real-time monitoring and simplified workflows, Censinet RiskOps™ boosts oversight and keeps risk mitigation efforts ongoing. This means patient data stays protected, and hospital operations remain steady - even when staffing and budgets are tight.


