How Security Maturity Models Measure Readiness
Post Summary
Security maturity models help organizations evaluate their cybersecurity readiness by assessing how well they manage people, processes, and technology. Unlike compliance checklists, these models measure the depth and consistency of security practices, offering a structured way to identify gaps and prioritize improvements. In healthcare, where cybersecurity failures can risk patient safety, these models are especially critical.
Key Takeaways:
- Purpose: Assess readiness to prevent, detect, respond to, and recover from cyber threats.
- Domains: Includes governance, risk management, medical device security, incident response, and more.
- Framework Alignment: Often mapped to NIST Cybersecurity Framework for consistency.
- Assessment Process: Involves cross-functional teams, documentation review, and setting measurable goals.
- Maturity Levels: Ranges from ad hoc (Level 1) to fully integrated (Level 5).
- Actionable Insights: Results guide targeted improvements tied to patient safety and compliance.
Healthcare Cybersecurity Maturity Model: 5 Levels and 8 Core Domains
What Readiness Means in Security Maturity Models
Core Domains in Healthcare Maturity Models
In the world of healthcare cybersecurity, readiness goes beyond simply checking compliance boxes. It’s about an organization’s ability to prevent, detect, respond to, and recover from cyber threats while protecting patient safety, keeping clinical operations running, and safeguarding sensitive patient data (PHI). For example, encrypting data alone isn’t enough - if an organization lacks a tested incident response plan, regular risk assessments, or proper device management, its readiness is still low, even if it meets HIPAA standards.
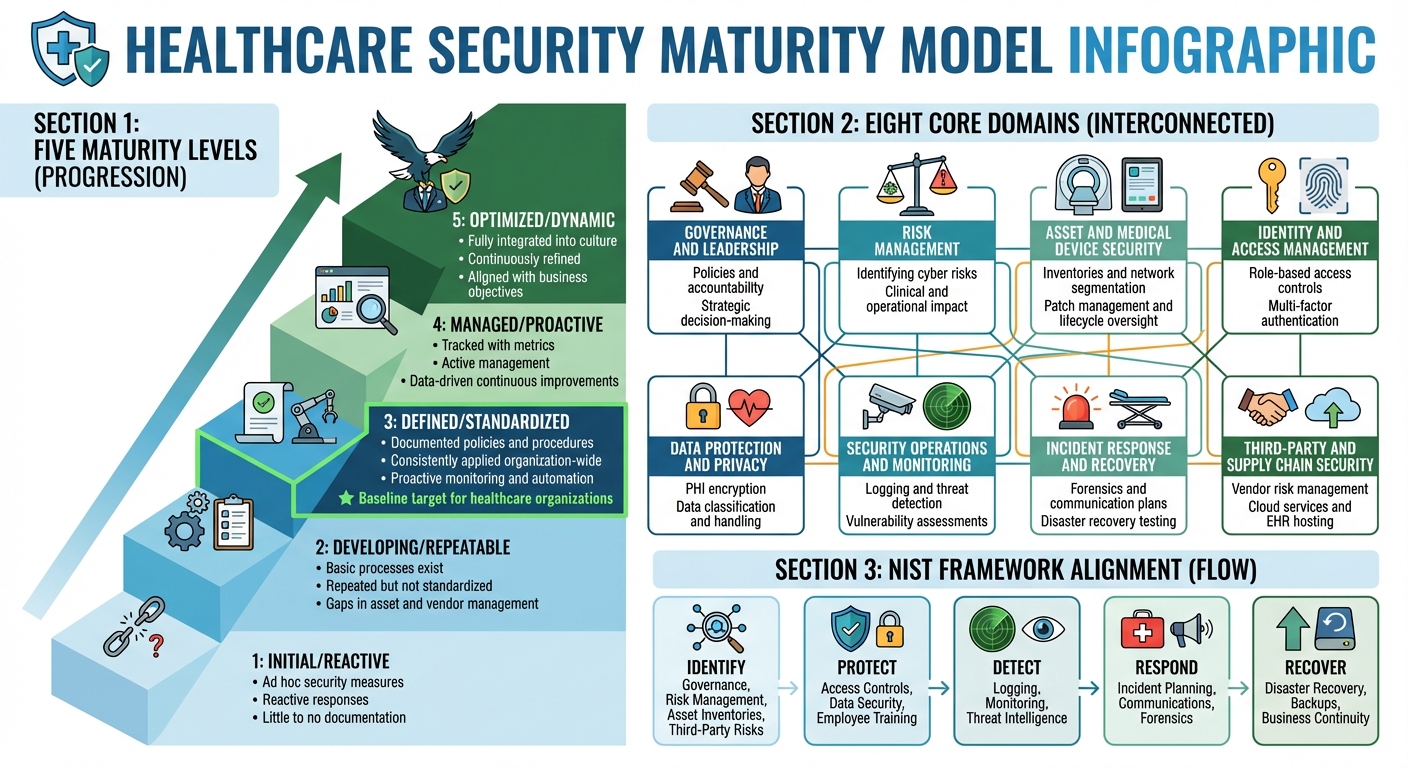
Healthcare maturity models typically break readiness into eight essential domains:
- Governance and Leadership: This includes the structures, policies, and accountability measures that embed security into strategic decision-making.
- Risk Management: Processes for identifying, assessing, and addressing cyber risks that could impact clinical, operational, or financial outcomes.
- Asset and Medical Device Security: Managing inventories, segmenting networks, applying patches, and overseeing the lifecycle of endpoints, servers, IoT devices, and medical equipment.
- Identity and Access Management: Implementing role-based access controls, multi-factor authentication, and continuous monitoring for systems like EHRs and clinical applications.
- Data Protection and Privacy: Protecting PHI through encryption, proper data classification, and handling procedures in line with U.S. privacy standards.
- Security Operations and Monitoring: Logging, threat detection, vulnerability assessments, and continuous monitoring to quickly identify and address potential issues.
- Incident Response and Recovery: Developing and testing plans for forensics, communication, and disaster recovery to ensure a swift response to cyber incidents.
- Third-Party and Supply Chain Security: Managing risks from vendors, cloud services, telehealth platforms, EHR hosting, and medical device manufacturers.
These areas are especially critical in the U.S., where disruptions to systems like EHRs or medical devices can directly impact patient safety, revenue, and compliance. Maturity models encourage a unified approach, integrating these domains to provide a full picture of an organization’s cybersecurity posture. This comprehensive perspective aligns with established frameworks like NIST.
Solutions like Censinet RiskOps™ help healthcare organizations tackle these interconnected challenges. By addressing risks tied to vendors, patient data, medical devices, and supply chains within one system, these platforms cater to the unique complexities of healthcare cybersecurity.
How Domains Align With Established Frameworks
Mapping these domains to established frameworks helps organizations align their cybersecurity practices with industry standards. Many healthcare maturity models closely follow the NIST Cybersecurity Framework, which organizes practices into five core functions: Identify, Protect, Detect, Respond, and Recover. Here's how they connect:
- Identify: Covers governance, risk management, asset inventories (including medical devices), third-party risks, and data classification.
- Protect: Focuses on access controls, endpoint protections, configuration management, data security, and employee awareness training.
- Detect: Involves logging, monitoring, anomaly detection, threat intelligence, and managing vulnerabilities.
- Respond: Includes planning for incidents, coordinating communications, conducting forensic investigations, and collaborating with clinical leaders and vendors.
- Recover: Emphasizes disaster recovery, backups, business continuity, and ensuring the resilience of critical systems like EHRs.
Frameworks like HITRUST align their controls with these NIST categories, while healthcare-specific models such as the HIMSS Cybersecurity Maturity Model and guidance from HHS/HC3 adapt these principles to the realities of clinical and regulatory environments. This alignment not only helps organizations benchmark their readiness against industry standards but also simplifies communication with executives, regulators, and insurers.
"Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters."
- Brian Sterud, CIO, Faith Regional Health
Such frameworks provide a foundation for defining and assessing maturity levels.
Understanding Maturity Levels
Maturity models often use a five-level scale to assess cybersecurity readiness, ranging from Initial (Reactive) to Optimized (Dynamic):
- Level 1 (Initial/Reactive): Security measures are ad hoc, and responses are reactive, with little to no documentation.
- Level 2 (Developing/Repeatable): Basic processes exist and are repeated, but they lack standardization across the organization. Gaps often remain in areas like asset and vendor management.
- Level 3 (Defined/Standardized): Security policies, procedures, and standards are documented and consistently applied organization-wide. Proactive monitoring and automation are in place. This is often seen as the baseline target for healthcare organizations.
- Level 4 (Managed/Proactive): Security processes are tracked with metrics, enabling active management and continuous improvements based on data.
- Level 5 (Optimized/Dynamic): Cybersecurity is fully integrated into the organization’s culture. Practices are continuously refined using lessons learned and threat intelligence, aligning security goals with broader business objectives.
At higher levels, cybersecurity shifts from being a set of tasks to an integral part of daily operations. This ensures organizations can adapt and stay resilient as cyber threats evolve.
How to Prepare for a Maturity Model Assessment
Assembling a Cross-Functional Team
To ensure a thorough and effective assessment, bringing together a team from across various departments is key. This group should include representatives such as the CISO, CIO/CTO, clinical leaders, biomedical engineers, IT and networking staff, compliance officers, risk management experts, and vendor risk specialists. Each member brings a unique perspective and expertise to the table.
The CISO typically leads the effort, setting the strategy and interpreting security controls. The CIO or CTO contributes insights on technology infrastructure, applications, and how they align with organizational goals. Compliance and privacy officers connect the dots between maturity gaps, regulatory risks, and past audit findings. Clinical leaders help identify how security measures affect patient care, acceptable downtime limits, and potential safety concerns. Biomedical engineers focus on medical devices and IoMT risks, while IT operations and networking leads address infrastructure, identity management, and system availability. Risk management or internal audit representatives ensure the scoring process aligns with enterprise risk priorities, and a vendor risk or supply chain lead evaluates third-party and cloud risks, especially for systems like cloud-based EHRs or imaging platforms.
"Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required."
- Terry Grogan, CISO, Tower Health
It's important to appoint an executive sponsor - often the CIO or CISO - who has the authority to resolve disagreements and allocate resources. The team should meet weekly during the preparation phase, with clear RACI assignments (Responsible, Accountable, Consulted, Informed) for each domain, such as incident response, access control, vendor risk, and data protection. Keep workshops focused by limiting them to 2–3 hours per domain.
Once the team is in place, the next step is gathering the necessary documentation and data for the assessment.
Collecting Documentation and Data
Getting all the required documentation ahead of time helps avoid unnecessary delays. Key documents include:
- Security and privacy policies: Covering areas like access control, incident response, data classification, acceptable use, and disaster recovery.
- Asset inventories: For servers, endpoints, network devices, clinical systems (EHR, PACS, LIS, RIS), medical devices, IoT, and cloud services handling PHI.
- Network and data-flow diagrams: Showing where PHI travels and any external connections.
Additionally, collect incident logs and reports from the past 12–24 months, including ransomware attacks, phishing incidents, outages, and data loss, along with root-cause analyses and lessons learned. Include vulnerability management data such as scan results, penetration test reports, and patch management records. Other critical documents include audit and assessment reports (e.g., HIPAA security risk assessments, HITRUST or HIMSS evaluations, internal audits, and regulator findings), business continuity and disaster recovery plans, backup test results, and RTO/RPO documentation for critical systems.
Also gather security awareness and training records, phishing simulation results, and role-based training materials. For vendor risk, compile business associate agreements (BAAs), SOC 2 or HITRUST reports, vendor questionnaires, and remediation plans for third-party issues. Assign local coordinators to collect evidence using a standardized checklist, and centralize everything using shared platforms or repositories. Tools like Censinet RiskOps™ can streamline this process, reducing manual effort and ensuring consistency.
With documentation in hand, it’s time to define measurable goals to guide readiness improvements.
Setting Measurable Readiness Goals
Using the team’s input and the collected data, set clear, measurable goals that directly tie to patient safety and regulatory compliance. Goals should be specific, measurable, and time-bound, focusing on tangible outcomes. For example, instead of vague objectives like "become more proactive", aim for targets such as reducing incident response time by 30% within 12 months or cutting unplanned clinical system downtime (e.g., EHR outages) by a specific number of hours per quarter. Another example: increasing the percentage of critical systems with tested backups from 70% to 95% within a year.
Each goal should align with a maturity domain. For instance, aim to elevate incident response capabilities from Level 2 to Level 3 within 18 months. Assign quantitative KPIs like mean time to detect (MTTD), mean time to recover (MTTR), or the percentage of critical vendors with completed risk assessments. Tie these metrics to real-world impacts, such as the number of patient visits affected by system downtime or the potential financial penalties from a data breach. This approach helps secure executive buy-in and funding.
"Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters."
- Brian Sterud, CIO, Faith Regional Health
Conduct a capability and resource assessment alongside the maturity review to evaluate staffing levels, tool coverage, and existing contracts. Focus on initiatives that address multiple domains simultaneously, such as implementing centralized identity and access management. Develop a phased roadmap, starting with high-impact areas like asset inventory and vulnerability management, before tackling more advanced solutions. Link your goals to budget cycles and capital planning to ensure improvements align with funding opportunities.
How to Measure Readiness Step by Step
Selecting the Right Maturity Model
Picking the right framework starts with identifying your organization's regulatory and operational priorities. The NIST Cybersecurity Framework (CSF) is a commonly used baseline in the U.S. healthcare sector, often extended with healthcare-specific controls. For organizations that need to align with regulations like HIPAA, HITECH, and various state privacy laws, the HITRUST CSF is a popular choice. It’s tailored for healthcare and provides mapping to multiple regulatory requirements. Meanwhile, organizations that focus heavily on clinical workflows, medical devices, and hospital operations often turn to the HIMSS Cybersecurity Maturity Model, which addresses healthcare-specific operational needs and the protection of PHI.
When choosing a framework, consider factors like how well it addresses healthcare-specific concerns (e.g., PHI, EHRs, connected medical devices), its compatibility with existing audits and certifications, the availability of tools and benchmarks, and the size and maturity of your cyber program. Many healthcare systems in the U.S. opt for a primary model supplemented with a sector-specific overlay to ensure compliance and operational readiness. Tools like Censinet RiskOps™ can streamline the process by mapping assessment data across various frameworks, simplifying risk assessments for PHI, clinical applications, and medical devices.
Once you’ve selected the right model, the next step is to define the scope of the assessment and gather essential evidence.
Running the Assessment
Start by outlining the scope of your assessment. This involves listing all in-scope assets and environments, such as EHR platforms, critical clinical applications, networked medical devices, cloud services handling PHI, and essential operational systems like scheduling tools or revenue cycle platforms. The scope should directly tie to patient safety and business impact, prioritizing areas where a cyber incident could disrupt care - like operating room systems, imaging equipment, or pharmacy operations.
Next, conduct targeted interviews with key leaders to understand how processes function in real-world scenarios, rather than relying solely on documented procedures. Collect supporting evidence such as incident response plans, vulnerability scans, access reviews, training completion reports, and disaster recovery test results. For each domain - such as identify, protect, detect, respond, and recover (as outlined in NIST CSF) - assign maturity levels based on observed practices. These levels typically range from initial or reactive to optimized. To ensure consistency, reviewers should meet to normalize scores across domains and facilities. Automated tools can further streamline this process by standardizing questionnaires, evidence collection, and scoring across multiple sites and third parties.
This structured approach lays the foundation for identifying gaps and taking action quickly.
Reading Results and Finding Gaps
Once the assessment is complete, visualize the results to identify where readiness falls short and patient safety may be at risk. Use charts to highlight domain scores and pinpoint high-risk areas that could impact care delivery or operational continuity. Create a comprehensive system-wide profile, along with individual profiles for specific facilities or clinics, and third-party profiles for external partners managing PHI or clinical applications.
Focus on high-risk gaps in critical areas like medical device security, incident response, backup and recovery, or identity and access management. Validate these gaps using recent incident reports, near-miss data, audit findings, and penetration test results to confirm that low maturity correlates with actual vulnerabilities - such as unpatched devices or frequent unauthorized access attempts.
Use a risk-based matrix to prioritize remediation efforts. Rank gaps based on their potential impact on patient safety, the likelihood of exploitation (informed by threat intelligence), regulatory exposure (e.g., HIPAA requirements), and the complexity and cost of remediation. From there, develop an actionable roadmap that outlines specific projects, assigns ownership, sets timelines, and estimates costs in U.S. dollars. Include measurable KPIs, such as the percentage of critical medical devices running current operating systems, average time to detect and respond to incidents, and the completion rate for security training programs.
sbb-itb-535baee
How to Turn Assessment Results Into Action
Ranking Gaps and Improvement Areas
After identifying gaps in your maturity assessment, the next step is to prioritize them based on their impact on patient care, compliance, and overall risk. Connect each gap to potential risks like treatment delays, data breaches, or system failures. Focus on high-risk issues - such as insecure EHR access, unsegmented clinical networks, or weak backup systems - that could disrupt care, even if their maturity scores are only slightly lower than others. It's worth noting that healthcare breaches remain among the costliest, with an average price tag exceeding $10 million per incident [1].
To organize this process, use a structured risk register. Link each gap to affected assets, potential threat scenarios (like ransomware or data theft), and the controls already in place. For regulatory concerns, align gaps with HIPAA safeguards, CMS conditions of participation, and state privacy laws. For broader organizational risks, estimate financial impacts like hourly downtime costs or breach expenses per record, while also factoring in reputational damage and potential loss of patient trust.
A decision matrix can help weigh impact, effort, and cost. Address high-impact, low-to-medium-effort items first, while high-impact, high-effort initiatives can be planned as longer-term projects with executive backing. For instance, if your assessment shows gaps in multi-factor authentication (MFA) for remote EHR access and outdated security training, prioritize MFA since compromised remote access poses a greater risk to patient information and clinical data integrity. Tools like Censinet RiskOps™ can assist by linking assessment results with third-party and enterprise risk data, highlighting where security gaps intersect with critical vendors, PHI flows, or clinical systems. Once priorities are set, define clear KPIs to track progress and address these risks without delay.
Setting Readiness Metrics and KPIs
Establish specific KPIs to track progress on closing gaps. For incident response and resilience, monitor metrics like mean time to detect (MTTD), mean time to respond (MTTR), and the time needed to fully restore EHR and other critical systems during drills. Also, track how many high-priority incidents are resolved within defined timeframes and how many undergo thorough root-cause analysis and remediation.
For vulnerability and patch management, measure the percentage of critical vulnerabilities fixed within set timelines (e.g., 7 or 30 days) and ensure clinical and biomedical devices are running supported operating systems.
Workforce readiness can be assessed through training completion rates, phishing simulation results, and response times for high-risk behaviors. Similarly, for third-party risk, track metrics like the percentage of high-risk vendors that have completed security assessments, the number of unresolved high-risk findings per vendor, and the time it takes to address vendor-related issues. Regularly review these KPIs using dashboards or risk management platforms, and adjust them as new threats emerge.
"Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters."
– Brian Sterud, CIO, Faith Regional Health
Adding Results to Governance Processes
With KPIs in place and progress tracked, integrate these findings into your governance framework. Include key maturity findings and KPIs in your governance processes for continuous monitoring. Add major gaps and remediation tasks to your enterprise risk register. Present maturity levels and trends - baseline, current, and target - to executive leadership, risk committees, and the board. Use non-technical language to connect security concerns with patient safety and regulatory risks. For example, report incident response metrics alongside clinical downtime and patient safety data, while training and phishing metrics can be reviewed in HR and compliance meetings.
Align maturity roadmap milestones with existing governance bodies, such as IT steering committees and clinical quality committees, to ensure security decisions are made alongside clinical and operational priorities. Assign each KPI to an executive sponsor (like the CIO, CISO, or CMIO) and an operational owner. Set thresholds that trigger escalation, corrective actions, or additional investment. Many healthcare organizations conduct comprehensive maturity assessments annually, supplemented by targeted mini-assessments or reviews of high-risk areas. Tracking year-over-year changes in maturity levels, reductions in high-risk gaps, and improvements in KPIs can help build a case for sustained or increased investment.
Censinet RiskOps™ supports this process by enabling standardized risk assessments, cross-organization benchmarking, collaborative workflows with vendors, and continuous monitoring for risks tied to PHI, medical devices, and clinical systems. This ensures readiness between formal assessments.
Conclusion
Security maturity models offer healthcare organizations a clear way to evaluate their cybersecurity readiness, directly linking technical controls to critical outcomes like patient safety, uninterrupted clinical operations, and regulatory compliance. These models provide measurable readiness levels, helping organizations understand whether they are reactive, merely compliant, or proactively addressing risks across people, processes, and technology. This approach highlights practical impacts, such as preventing treatment delays, protecting electronic health records (EHRs) during ransomware incidents, and maintaining patient trust. Beyond assessment, these models guide organizations in identifying areas for improvement and prioritizing actions.
By establishing clear key performance indicators (KPIs) - such as incident detection times or patching rates - maturity models enable organizations to track progress and demonstrate risk reduction. These metrics not only provide tangible evidence of improvement to boards and regulators but also create a continuous cycle of reassessment, remediation, and measurement. This dynamic process ensures readiness evolves alongside emerging threats, new technologies, and shifts in care delivery models. With these insights, leadership can strategically allocate resources to address the most pressing risks.
To fully leverage these models, leadership must integrate findings into everyday governance. This means validating results with clinical, IT, compliance, and executive teams, prioritizing gaps based on their impact on patient safety and business continuity, and setting achievable 12- to 24-month maturity goals aligned with budget cycles. These gaps should translate into funded projects with dedicated owners and clear deadlines. Embedding maturity model findings into governance structures - such as risk registers, board dashboards, and security committees - ensures that cybersecurity readiness is treated as a core organizational priority, alongside financial, operational, and clinical goals.
Censinet RiskOps™ streamlines this process by centralizing risk assessments, automating data collection, and integrating maturity findings into governance workflows. It also enables benchmarking against peer organizations, helping healthcare leaders set realistic goals and make a strong case for necessary investments.
The flexibility of maturity models makes them valuable for organizations of any size, even those with limited resources. By committing to a long-term, structured approach to cybersecurity maturity, healthcare organizations can safeguard patients, uphold trust, and ensure the safety and reliability of digital health innovations.
FAQs
Why are security maturity models better than compliance checklists for healthcare cybersecurity?
Security maturity models provide a comprehensive and evolving framework for assessing and enhancing cybersecurity preparedness. They enable healthcare organizations to pinpoint weaknesses, set priorities, and track improvements over time. This approach supports a forward-thinking strategy that keeps pace with shifting threats and aligns with broader, long-term objectives.
On the other hand, compliance checklists are more static, focusing on meeting specific requirements at a given moment. This can leave organizations vulnerable to new and unforeseen risks. By adopting a maturity model, healthcare providers can strengthen their defenses, better safeguard sensitive data like patient health information (PHI), and remain adaptable in an ever-changing digital environment.
How do security maturity models help healthcare organizations align with frameworks like NIST?
Security maturity models provide healthcare organizations with a structured approach to evaluate and improve their cybersecurity readiness while aligning with frameworks like NIST. These models help identify vulnerabilities, prioritize areas for improvement, and ensure compliance with NIST standards, such as the Cybersecurity Framework (CSF).
By adopting a maturity model, healthcare organizations can monitor their progress, implement best practices, and bolster their defenses against cyber threats. This proactive strategy is essential for protecting sensitive patient information, securing medical devices, and safeguarding other critical systems.
How can healthcare organizations prepare for a cybersecurity maturity model assessment?
Preparing for a cybersecurity maturity model assessment requires thoughtful planning and a structured approach to ensure your organization is ready to evaluate and strengthen its security measures. Start by establishing a baseline - take stock of your current cybersecurity practices and pinpoint the critical assets and data that need safeguarding. Collect documentation on your existing policies, procedures, and controls to create a clear snapshot of your current security framework.
The next step is conducting an internal gap analysis. This involves comparing your current practices to the standards outlined in the maturity model to identify areas that need improvement. It's important to involve stakeholders from various departments to ensure a well-rounded and thorough evaluation. Address any gaps you uncover before the official assessment. Tools such as Censinet RiskOps™ can assist by simplifying risk assessments and offering useful benchmarks to guide your progress.
By taking these steps, your organization will be better positioned to measure its cybersecurity readiness and take actionable steps toward improvement.


