Telehealth, EHRs, and Pharmacy Systems: Mapping Your Healthcare Organization's AWS Exposure
Post Summary
Healthcare organizations rely heavily on AWS for telehealth, EHRs, and pharmacy systems, but misconfigurations and weak security practices can expose sensitive patient data. This article highlights the most common security risks and provides actionable strategies to safeguard your AWS environment while maintaining compliance with regulations like HIPAA.
Key Points:
- Common Risks: Misconfigured S3 buckets, overly permissive IAM roles, unencrypted data, and weak network controls.
- Compliance Challenges: HIPAA and NIST standards require strong administrative, physical, and technical safeguards.
- AWS Shared Responsibility Model: AWS secures the infrastructure, but customers are responsible for securing their data and configurations.
Solutions:
- Use tools like AWS CloudTrail, GuardDuty, and Security Hub for monitoring and threat detection.
- Secure your systems with TLS encryption, fine-grained IAM policies, and regular audits.
- Automate compliance checks using AWS Config or third-party platforms like Censinet RiskOps.
Proactively addressing these risks ensures better protection of patient data, uninterrupted care, and regulatory compliance.
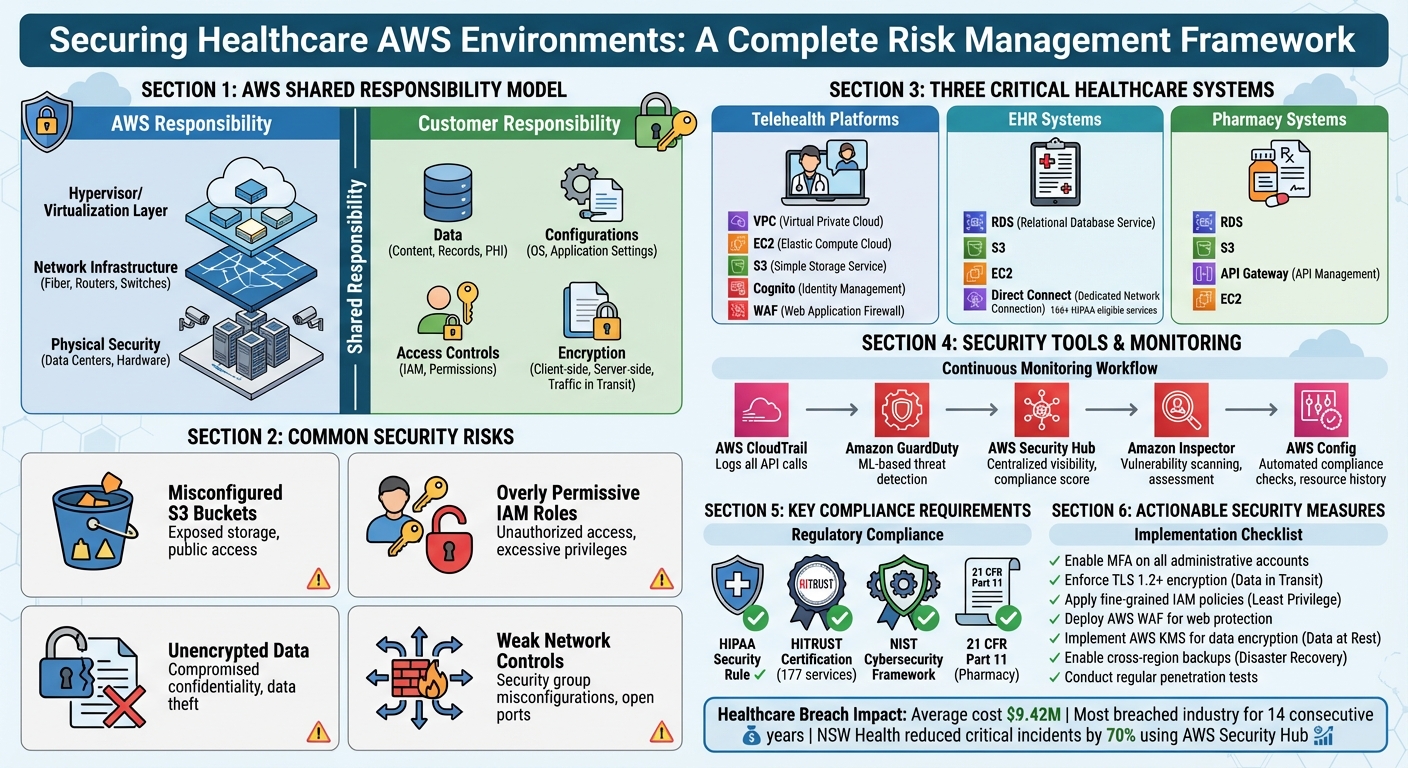
AWS Security Risk Management Framework for Healthcare Organizations
Common AWS Security Risks in Healthcare Systems
Healthcare organizations often encounter recurring vulnerabilities within AWS-powered systems like telehealth platforms, EHRs, and pharmacy applications. These weaknesses frequently stem from architectural misconfigurations, which can put sensitive patient data at risk. Below, we’ll explore the specific challenges tied to these misconfigurations and the compliance hurdles they introduce.
AWS Services Used in Healthcare Applications
Key AWS services - such as Amazon VPC, EC2, S3, RDS, and IAM - serve as the backbone for many healthcare applications[2][7]. These services are integral to running essential operations, but any misstep in their configuration can ripple across interconnected systems, amplifying security risks. Understanding the vulnerabilities tied to these components is crucial for mapping out and addressing potential threats.
Common Misconfigurations and Security Gaps
Several common misconfigurations and gaps in security practices can leave healthcare systems exposed. These include:
- Overly permissive IAM roles: Broad access permissions can allow unauthorized users to exploit sensitive systems.
- Exposed S3 buckets: Mismanaged storage configurations can lead to data leaks.
- Insufficient encryption: Weak or absent encryption mechanisms can compromise data confidentiality.
- Misconfigured security groups and network ACLs: Inadequate network controls open doors for unauthorized access.
Research identifies data confidentiality as one of the most pressing challenges in cloud security for healthcare[1]. Basic security measures, like multifactor authentication, may no longer suffice against increasingly sophisticated threats. Without robust monitoring and timely patching, systems remain vulnerable. For instance, limited tracking of AWS activities - such as user logins or IAM role changes - delays breach detection. Additionally, unpatched systems and insecure APIs exacerbate the risk landscape. Recognizing these vulnerabilities is a critical first step in mitigating AWS-related risks within healthcare environments.
Connecting AWS Risk Management to Compliance Requirements
Because healthcare systems handle sensitive electronic protected health information (ePHI), aligning AWS security measures with regulatory standards like HIPAA and NIST is non-negotiable. The HIPAA Security Rule requires organizations to safeguard the confidentiality, integrity, and availability of ePHI through robust administrative, physical, and technical controls[8].
AWS has made strides in compliance, achieving HITRUST certification for 177 services under version 11.5.1 of the HITRUST CSF as of August 2025[5]. Utilizing frameworks like the NIST Cybersecurity Framework can streamline the identification and prioritization of risks. Automated Governance, Risk, and Compliance (GRC) tools also play a vital role in maintaining a continuous overview of security posture.
It’s important to note that AWS operates under a Shared Responsibility Model, where AWS secures the infrastructure, but healthcare organizations are responsible for their data and configurations. This shared approach emphasizes the need for organizations to align their practices with HIPAA and NIST standards to ensure comprehensive protection.
Assessing AWS Security Risks in Telehealth Platforms
How Telehealth Platforms Use AWS Infrastructure
Telehealth platforms heavily depend on AWS services to operate efficiently and securely. They use Amazon VPC for creating isolated networks, EC2 for running application servers, S3 for storing patient records and consultation recordings, and RDS for managing appointment schedules and clinical databases. For example, when a patient logs in for a virtual consultation, their data flows through AWS Cognito for authentication, video streams via EC2-hosted applications, and files are stored in S3 buckets. While this setup is powerful, every point in this process could become a vulnerability if not safeguarded properly. Understanding these workflows is the first step in pinpointing potential risks.
Identifying and Reducing Telehealth Security Risks
Telehealth platforms face unique security challenges that demand targeted measures. Weak firewalls in patient-facing applications can leave endpoints exposed. Without enforcing TLS encryption, sessions are vulnerable to hijacking, and a lack of proper logging mechanisms can delay the detection of breaches.
"Threat and vulnerability management is a critical function of your foundational cloud environment. With the ever-evolving threat landscape and the shared responsibility model in cloud computing - where customers share security responsibilities with cloud providers - proactive threat and vulnerability management has become fundamental to identifying and addressing emerging risks and maintaining the integrity of cloud-based operations." - AWS Solutions Library [9]
To address these risks, telehealth providers should implement practical safeguards, including:
- Deploying AWS WAF to protect against common web exploits.
- Enforcing TLS 1.2 or higher for all communications.
- Applying fine-grained IAM policies to restrict access.
Regularly reviewing IAM roles and permissions using AWS IAM Access Analyzer can help detect overly permissive rules and identify unused credentials. Strengthening the root account is equally critical - enabling MFA and removing access keys can block unauthorized administrative access. By adopting these strategies, telehealth platforms can ensure their AWS environments remain secure and compliant.
Tools for Monitoring Telehealth Security Risks
Continuous monitoring is a cornerstone of effective security. AWS CloudTrail logs every API call within an AWS environment, creating a detailed audit trail of user logins, configuration changes, and data access attempts. When combined with Amazon CloudWatch, these logs can trigger real-time alerts, such as notifications for suspicious activity like multiple IAM user creations in a short period [4].
For advanced threat detection, Amazon GuardDuty analyzes CloudTrail logs, VPC Flow Logs, and DNS query logs using machine learning. It detects unusual behaviors, such as unauthorized access attempts, brute force attacks, or data exfiltration patterns. For instance, NSW Health leveraged GuardDuty and AWS Security Hub after migrating to AWS, automating security checks and reducing critical incidents by 70% while saving hundreds of hours annually [10].
Additionally, Amazon Inspector scans EC2 instances, container images, and Lambda functions for vulnerabilities and network exposure. Its findings are integrated into Security Hub for centralized visibility. Pairing these AWS-native tools with solutions like Censinet RiskOps provides continuous risk monitoring, ensuring telehealth platforms maintain compliance with HIPAA while keeping their operations secure and efficient.
Assessing AWS Security Risks in EHR Systems
How EHR Systems Are Deployed on AWS
Electronic Health Record (EHR) systems can be deployed on AWS in three main ways: fully cloud-hosted, hybrid setups, or through vendor SaaS models. Fully cloud-hosted systems rely on AWS services like Amazon RDS, S3, and EC2. Hybrid deployments, on the other hand, connect on-premises systems to the cloud using tools like AWS Direct Connect. Vendor SaaS solutions provide secure access through managed interfaces. A key consideration in these deployments is identifying which AWS services handle Protected Health Information (PHI). AWS supports more than 166 HIPAA-eligible services, offering a wide range of options for compliance [14]. However, the complexity of these setups makes targeted risk assessments essential - similar to what’s required for telehealth platforms.
Major Security Risks in AWS-Hosted EHR Systems
When it comes to securing cloud-based EHR systems, healthcare organizations carry a significant responsibility. Misconfigurations on the customer side are the leading cause of vulnerabilities [5][12]. Common issues include unencrypted RDS instances, publicly accessible databases, and weak authentication measures. These lapses can leave sensitive data exposed to cyberattacks. For example, in January 2025, Oracle Health experienced a breach that impacted 6 million patients. This incident was tied to a legacy server used during a cloud migration, highlighting how outdated systems can introduce serious risks [11].
Insecure API integrations are another weak point. Without proper authentication or protection - such as that offered by Amazon API Gateway - EHR systems are vulnerable to injection attacks and unauthorized access [11][13]. Weak privileged access controls also pose significant risks. The February 2024 ransomware attack on Change Healthcare, which exploited the absence of multifactor authentication on remote-access systems, serves as a stark reminder of the consequences of inadequate security [11][13].
Under AWS’s shared responsibility model, healthcare organizations must take proactive steps to secure their deployments. Misconfigurations and weak controls remain persistent challenges, and the stakes are high: healthcare has been the most breached industry for 14 years in a row, with the average cost of a breach nearing $10 million [13].
Maintaining Compliance and Uptime for EHR Systems
Securing EHR systems isn’t just about preventing breaches - it’s also about ensuring compliance and maintaining system uptime, both of which are critical for patient care. HIPAA compliance requires constant oversight of data storage, transmission, and access controls. Tools like AWS Config help automate compliance checks by mapping rules directly to HIPAA requirements. This allows organizations to quickly identify issues such as unencrypted EBS volumes or overly permissive security groups [1][7].
To safeguard data, encrypting it at rest using AWS Key Management Service (KMS) and enforcing TLS 1.2 or higher for data in transit are essential practices [7]. For instance, Baptist Memorial Health Care reported a 20% boost in system performance and improved disaster recovery after migrating its Epic system to AWS in 2025 [14].
System uptime is equally critical. Solutions like AWS Backup with cross-region replication and S3 versioning provide protection against ransomware attacks and accidental data loss. Centralizing security findings through AWS Security Hub and automating incident response with tools like Amazon Detective and Lambda scripts ensures quick detection and resolution of issues. These measures not only help maintain compliance but also minimize disruptions to clinical workflows, ensuring uninterrupted patient care [7].
sbb-itb-535baee
Assessing AWS Security Risks in Pharmacy Systems
AWS Services That Support Pharmacy Operations
Pharmacy systems hosted on AWS manage a variety of critical tasks, including e-prescribing, inventory tracking, payment processing, and integration with systems like EHRs, PBMs, and insurers. Core AWS services supporting these operations include RDS (for prescription databases), S3 (for document storage), EC2 (for hosting), and API Gateway (for external connectivity). AWS is built to align with compliance standards such as HIPAA, HITECH, and 21 CFR Part 11. However, healthcare organizations must ensure these services are configured correctly to maintain strong security measures [12]. These foundational tools are essential, but they also introduce specific vulnerabilities, which are explored below.
Security Vulnerabilities in Pharmacy Workflows
Despite the robust infrastructure AWS provides, pharmacy systems face unique security challenges. A notable example is the cybersecurity breach experienced by the online pharmacy Ravkoo in September 2021. Hackers exploited a hidden admin panel in its AWS-hosted prescription portal, compromising the personal information of 105,000 individuals. Exposed data included full names, addresses, phone numbers, and prescription details [15][16]. Ravkoo reported the breach to the FBI and subsequently implemented stricter security measures.
"Ravkoo utilizes AWS cloud services for online hosting of its prescription portal. On September 27, 2021, Ravkoo detected that this portal was the target of a cybersecurity attack." - Ravkoo, Data Breach Notification Letters [16]
In pharmacy workflows, weak security controls can expose sensitive PHI (Protected Health Information) and disrupt critical operations like medication processing. Common risks include DDoS attacks targeting poorly configured load balancers, inadequate network segmentation that allows unauthorized lateral movement, and insufficient encryption for data at rest or in transit. The financial impact of breaches is staggering, with pharmacy breaches averaging $9.42 million per incident. Between December 2020 and February 2021, phishing attacks alone surged by 189% [17]. Additionally, human error and vulnerabilities introduced through third-party integrations further amplify these risks.
Ranking Risks by Patient Safety and Compliance Impact
Given these vulnerabilities, healthcare organizations need to prioritize risks based on their potential impact on patient safety and regulatory compliance. Pharmacy systems, unlike telehealth or EHR platforms, directly influence medication accuracy and dispensing, making rapid mitigation of risks critical. Risks that could lead to prescription errors, medication delays, or system outages should be addressed immediately, as they directly affect patient care and safety [18].
To combat these threats, organizations should adopt a multi-layered security approach:
- Implement strong authentication: Use multi-factor authentication (MFA) for all administrative accounts.
- Enforce least privilege access: Limit access to sensitive data and systems.
- Encrypt PHI: Ensure all data is encrypted both at rest and during transit.
- Conduct regular assessments: Perform audits, vulnerability scans, and penetration tests to identify and fix misconfigurations.
- Utilize real-time monitoring tools: Deploy tools like AWS GuardDuty to detect threats early.
- Maintain secure backups: Keep offline backups to safeguard against data loss and ensure business continuity.
Managing AWS Security Risks with Censinet

Ongoing Risk Assessment and Monitoring
Healthcare organizations face the challenge of managing AWS security risks across critical systems like telehealth platforms, EHRs, and pharmacy applications. Censinet RiskOps simplifies this process by centralizing risk assessment and monitoring. It enables teams to track vulnerabilities, evaluate their security posture, and coordinate remediation efforts effectively. With real-time data aggregated into a user-friendly risk dashboard, security teams gain the visibility needed to address critical risks before they escalate into breaches.
In February 2025, Censinet partnered with AWS to enhance healthcare governance, risk, and compliance (GRC) and cybersecurity risk management using advanced AI. This partnership ensures that Censinet AI operates within a dedicated Virtual Private Cloud (VPC) on AWS infrastructure. By doing so, customer data remains securely encrypted both during transit and at rest, safeguarding privacy at every step [19].
Using Censinet AI for AWS Governance
Censinet AI takes centralized monitoring a step further by streamlining governance across AWS environments. One of its standout features is the automation of third-party risk assessments. It handles tasks like completing vendor questionnaires, summarizing evidence, capturing integration details, and identifying risks from fourth-party relationships. For healthcare organizations juggling multiple AWS-hosted systems, this automation dramatically reduces the time required to assess and address risks. Vendors can now complete security questionnaires in seconds instead of weeks, and risk summary reports are generated automatically from the assessment data.
Censinet AI also aligns governance efforts with the NIST AI Risk Management Framework (RMF). It enhances risk visibility, helps governance committees establish and enforce AI policies, and supports AI implementation across AWS environments. The platform autonomously validates evidence, drafts policies, and mitigates risks while ensuring human oversight remains intact [19].
"Our collaboration with AWS enables us to deliver Censinet AI to streamline risk management while ensuring responsible, secure AI deployment and use. With Censinet RiskOps, we're enabling healthcare leaders to manage cyber risks at scale to ensure safe, uninterrupted care."
– Ed Gaudet, CEO and founder of Censinet [19]
Combining AWS Security Tools with Censinet RiskOps

AWS-native tools like GuardDuty, Security Hub, and Macie are effective at identifying technical vulnerabilities. However, Censinet RiskOps complements these tools by providing a comprehensive risk management framework. It integrates seamlessly with AWS security services to coordinate governance and compliance efforts. For example, Censinet RiskOps routes assessment findings and remediation tasks to the appropriate stakeholders, including members of AI governance committees. This ensures that the right teams address the right issues promptly.
As a centralized hub for managing AWS-related policies, risks, and tasks, Censinet RiskOps ensures continuous oversight and accountability. Its orchestration capabilities extend across telehealth systems, EHR platforms, and pharmacy applications, making it an invaluable tool for healthcare organizations striving to maintain secure and compliant operations [19].
"With AWS's AI infrastructure powering Censinet RiskOps, healthcare organizations gain the tools they need to more efficiently manage cyber risks and guide safe AI adoption – AWS is proud to support Censinet in delivering cybersecurity solutions that the healthcare industry, and their patients, can rely on."
– Ben Schreiner, Head of Business Innovation for SMB, U.S. at AWS [19]
This collaboration provides healthcare organizations with a robust framework for ongoing cybersecurity management, offering the tools needed to maintain compliance and protect patient care.
Conclusion: Reducing AWS Security Risks in Healthcare
Key Points for AWS Risk Management
Healthcare organizations leveraging AWS for telehealth, EHR, and pharmacy systems face a challenging security environment. To safeguard patient data and comply with regulations like HIPAA and HITECH, it’s crucial to assess AWS exposure thoroughly. A proactive approach involving continuous monitoring and layered security measures across critical systems is key to mitigating risks from misconfigurations and vulnerabilities.
Misconfigurations are the most common weak point, making regular audits with tools such as AWS Security Hub essential [3]. Still, technical tools alone aren’t enough. A well-rounded framework, like the NIST Cybersecurity Framework (CSF) 2.0, is necessary. This framework addresses governance, identification, protection, detection, response, and recovery [20][6], providing a comprehensive strategy for security.
With these principles in place, the next step is turning this understanding into actionable measures.
Next Steps for Healthcare Organizations
To strengthen security, healthcare organizations should focus on actionable strategies. The growing threat of ransomware and the rapid integration of AI require swift, effective measures to protect critical systems from disruption [19]. Start by performing a detailed review of your telehealth, EHR, and pharmacy systems to uncover vulnerabilities. This includes conducting a thorough evaluation of AWS configurations, defining strict security parameters, and scheduling regular penetration tests to pinpoint emerging risks [21].
Consider implementing AI-driven GRC (Governance, Risk, and Compliance) solutions to manage risks more efficiently. These tools can speed up security reviews, enabling vendors to complete assessments in seconds and automatically generate risk summaries. They also ensure data remains encrypted and securely isolated within dedicated AWS VPCs [19].
"With AWS's AI infrastructure powering Censinet RiskOps, healthcare organizations gain the tools they need to more efficiently manage cyber risks and guide safe AI adoption – AWS is proud to support Censinet in delivering cybersecurity solutions that the healthcare industry, and their patients, can rely on."
– Ben Schreiner, Head of Business Innovation for SMB, U.S. at AWS [19]
FAQs
What are the top AWS security risks healthcare organizations should watch out for?
Healthcare organizations leveraging AWS encounter several security challenges that require careful attention. One common issue is misconfigured S3 buckets, which can unintentionally expose sensitive patient information. Similarly, overly permissive IAM roles may provide unnecessary access to critical systems, increasing the risk of unauthorized activity. Another concern is unrestricted access to EC2 instances, which can open the door to unauthorized users. On top of this, insufficient encryption - whether for data stored on AWS or while it’s being transmitted - can leave sensitive information vulnerable to breaches.
Another major risk comes from relying entirely on a single cloud provider, as this creates a single point of failure. To mitigate this, it’s essential to have robust backup systems and disaster recovery plans in place. Proactively tackling these risks is not just about securing systems; it also plays a critical role in meeting healthcare regulations and protecting patient data.
How can healthcare organizations using AWS stay HIPAA-compliant?
Healthcare organizations can ensure HIPAA compliance on AWS by following a structured approach. First, leverage AWS services certified under HITRUST and make sure to sign a Business Associate Agreement (BAA) with AWS. Encryption is key - use tools like AWS Key Management Service (KMS) to encrypt data both at rest and during transit.
To strengthen security, set up robust access controls with Identity and Access Management (IAM) roles and enforce Multi-Factor Authentication (MFA) for additional protection. Continuous monitoring is equally important - tools like AWS CloudTrail and CloudWatch can help track activity and detect anomalies.
Lastly, align your practices with NIST and HIPAA security guidelines, and conduct regular audits and assessments to uncover and address potential risks. This proactive approach not only safeguards sensitive data but also keeps your organization compliant.
What are the best tools to monitor and reduce security risks in telehealth systems on AWS?
To keep telehealth systems secure on AWS, there are several powerful tools you can rely on. AWS CloudTrail and AWS Config are essential for tracking and logging changes in your environment, making it easier to spot and respond to any unauthorized activities. For advanced threat detection and centralized management, Amazon GuardDuty and AWS Security Hub are great options. Meanwhile, Amazon Inspector automates security assessments to uncover vulnerabilities in your system. Lastly, AWS Identity and Access Management (IAM) helps enforce strict access controls, ensuring sensitive healthcare data remains protected.
By combining these tools, your organization can stay ahead of security risks, address threats effectively, and meet healthcare compliance standards.
Related Blog Posts
- HIPAA Compliance for Cloud Services: Checklist
- 7 Hours Down, Millions Affected: Inside the AWS Outage That Broke Healthcare's Digital Backbone
- The Hidden Cost of Cloud Dependency: What the AWS Outage Means for HIPAA Compliance
- The 30-40% Problem: Why Healthcare's Over-Reliance on US-EAST-1 Is a Patient Safety Risk


