Tokenization vs. Encryption: Which Is Better for PHI?
Post Summary
Protecting Protected Health Information (PHI) is critical for healthcare organizations. PHI includes sensitive data like medical records, Social Security numbers, and billing details, making it a prime target for cyberattacks. Two key methods for securing PHI are tokenization and encryption, each with distinct strengths and limitations. Here's a quick breakdown:
- Tokenization replaces sensitive data with random tokens stored in a secure vault. Even if stolen, tokens are useless without access to the vault. It's ideal for structured data like Social Security numbers or medical record numbers.
- Encryption converts data into unreadable ciphertext using cryptographic keys. It works well for unstructured data like clinical notes, images, and emails. However, compromised keys can expose the data.
Key Takeaways:
- Tokenization reduces compliance burdens and breach impact but requires a secure vault and careful system integration.
- Encryption is versatile but depends heavily on key management and can slow down performance.
- A layered approach - using both methods - provides the best protection for PHI, balancing security and usability.
Quick Comparison:
| Factor | Tokenization | Encryption |
|---|---|---|
| Best For | Structured data (e.g., SSNs, MRNs) | Unstructured data (e.g., notes, images) |
| Breach Impact | Tokens are useless without vault access | Compromised keys can expose data |
| Compliance Scope | Systems with tokens may fall outside HIPAA scope | Encrypted data remains in HIPAA scope |
| Performance | May introduce latency due to detokenization | Computationally intensive |
| Operational Needs | Requires secure token vault | Demands strong key management |
Both methods are essential for protecting PHI, but their effectiveness depends on the specific use case and system requirements.
Tokenization vs Encryption for PHI: Side-by-Side Comparison
Encryption for PHI Security
How Encryption Works in Healthcare Cloud Systems
Encryption transforms Protected Health Information (PHI) into unreadable ciphertext using sophisticated algorithms and encryption keys. Only authorized users with the correct decryption keys can restore the original data[5]. In the U.S., healthcare organizations commonly use AES-256 encryption to protect data at rest, such as databases, file systems, and backups. For data in transit - like information shared between electronic health records (EHRs), patient portals, APIs, and third-party services - TLS 1.2 or higher is the standard[5].
When PHI is transmitted, it travels over secure, TLS-encrypted connections to storage systems. For highly sensitive fields, additional field-level encryption is applied. Backup copies, logs, and data replicas inherit the same encryption protocols, ensuring consistent protection across all copies. This layered approach helps limit the impact of potential breaches and supports compliance with federal regulations.
Benefits of Encryption for PHI
Encryption plays a key role in minimizing the damage from data breaches by ensuring that only unreadable ciphertext is exposed. It also supports compliance with HIPAA by addressing its requirements for confidentiality, integrity, and availability[5].
Both structured PHI - like demographic information, claims data, and lab results - and unstructured PHI - such as scanned documents, radiology images, and clinical notes - can be encrypted without altering the underlying data structures. Additionally, some state laws offer a "safe harbor" provision, reducing liability or notification requirements if compromised information was encrypted and rendered unreadable.
Limitations and Risks of Encryption
While encryption provides essential security, it also introduces operational challenges. Managing encryption keys is critical - poorly managed or compromised keys can render encryption ineffective. To address this, healthcare organizations often rely on Key Management Services (KMS) or Hardware Security Modules (HSMs). Best practices include implementing role-based access controls, automating key rotation, and maintaining detailed audit logs to track access and changes.
Encryption can also slow down system performance, especially in environments with frequent read/write operations. To reduce this overhead, organizations often use hardware acceleration for AES encryption or implement solutions like Transparent Data Encryption (TDE) for broad protection. Field-level encryption is typically reserved for the most sensitive data to balance security with performance.
Another significant challenge arises when PHI is decrypted for tasks like viewing, processing, or analysis. Decrypted data becomes vulnerable to risks such as unauthorized access by privileged users, memory-scraping malware, improper exports, or retention of cleartext data in poorly configured analytics systems. These risks are heightened in centralized data lakes and AI/ML platforms where large volumes of PHI are consolidated.
To mitigate these vulnerabilities, tools like Censinet RiskOps™ can help by tracking decryption activities, assessing security controls, and monitoring third-party tools that handle decrypted PHI. This centralized approach helps organizations maintain visibility and control over sensitive data, even in complex environments.
Tokenization for PHI Protection
How Tokenization Works in Healthcare
Tokenization is a process that replaces Protected Health Information (PHI) with non-sensitive tokens, which are meaningless on their own and have no mathematical connection to the original data. Unlike encryption, which transforms data into reversible ciphertext, tokenization generates random values stored separately in a highly secure system called a token vault[7][4].
Here’s how it works: When PHI enters a healthcare system - via an EHR interface, patient portal, or FHIR API - sensitive fields like Social Security numbers, medical record numbers, or patient names are sent to a tokenization service. This service creates tokens that often mimic the format of the original data (such as maintaining the same length as a Social Security number) to ensure compatibility with existing systems[2]. The mapping between the original data and the token is securely stored in a token vault, which is protected with encryption, strict access controls, and audit logs[7][2][5].
Healthcare organizations store only the tokens in operational databases, data lakes, and analytics platforms, keeping the actual PHI out of reach. When workflows require the original data - such as for claims processing or patient matching - an authorized application accesses the vault's detokenization API. Role-based policies govern access, and every request is logged for compliance purposes[7][2].
Benefits of Tokenization for PHI
Tokenization significantly limits the impact of data breaches. If an attacker gains access to a database or analytics platform, they only obtain tokens, which are useless without access to the secured vault[7][4].
One key advantage is its ability to reduce compliance burdens. Many regulatory frameworks classify tokenized data as non-sensitive since the actual PHI remains in the vault. This can exempt entire systems, vendors, and workflows from stringent regulations like HIPAA, leading to lower security and infrastructure costs[7][4][8]. Tokenized datasets can also be safely shared with analytics teams, research groups, or offshore providers without exposing direct identifiers, minimizing legal and contractual risks[7][3][4].
Tokenization is also a game-changer for analytics and AI projects. Since the same individual always maps to the same token, longitudinal studies can track patient data across encounters, lab results, and claims without revealing identities[7][4]. This allows population health teams to run risk models and enables AI/ML systems to analyze large-scale clinical datasets in cloud environments while keeping PHI secure in the vault[2][4].
For organizations juggling multiple third-party vendors, platforms like Censinet RiskOps™ provide oversight by tracking which vendors handle tokenized versus raw PHI, assessing tokenization security, and monitoring detokenization activities. This centralized approach strengthens overall PHI protection strategies in complex, cloud-based healthcare ecosystems.
While tokenization offers substantial benefits, it also comes with challenges that require careful planning and investment.
Challenges of Tokenization
Implementing tokenization demands significant infrastructure investment. Healthcare organizations need to establish and maintain a reliable tokenization service and a secure vault with robust encryption (such as AES-256), HSM-backed key management, and network segmentation[7][2][5]. Since the tokenization service becomes critical infrastructure, any failure can disrupt clinical operations dependent on detokenization. This makes enterprise-grade availability, redundancy, and disaster recovery planning essential[2][5].
Legacy systems can pose additional hurdles. Older healthcare applications often rely on specific data formats or embed identifiers directly into their workflows. Transitioning to tokenized values may require schema modifications, code updates, and extensive testing to ensure compatibility[7][1][4].
Tokenization is most effective for structured identifiers like names, Social Security numbers, medical record numbers, insurance IDs, addresses, and phone numbers[7][3][4]. However, applying tokenization consistently to unstructured PHI - such as free-text clinical notes, scanned documents, radiology images, or emails - is far more complex. These formats require complementary measures like encryption, data loss prevention tools, redaction, or natural language processing (NLP)-based de-identification to ensure privacy[1][5][4][6].
sbb-itb-535baee
Tokenization vs. Encryption: A Direct Comparison
Key Differences Between Tokenization and Encryption
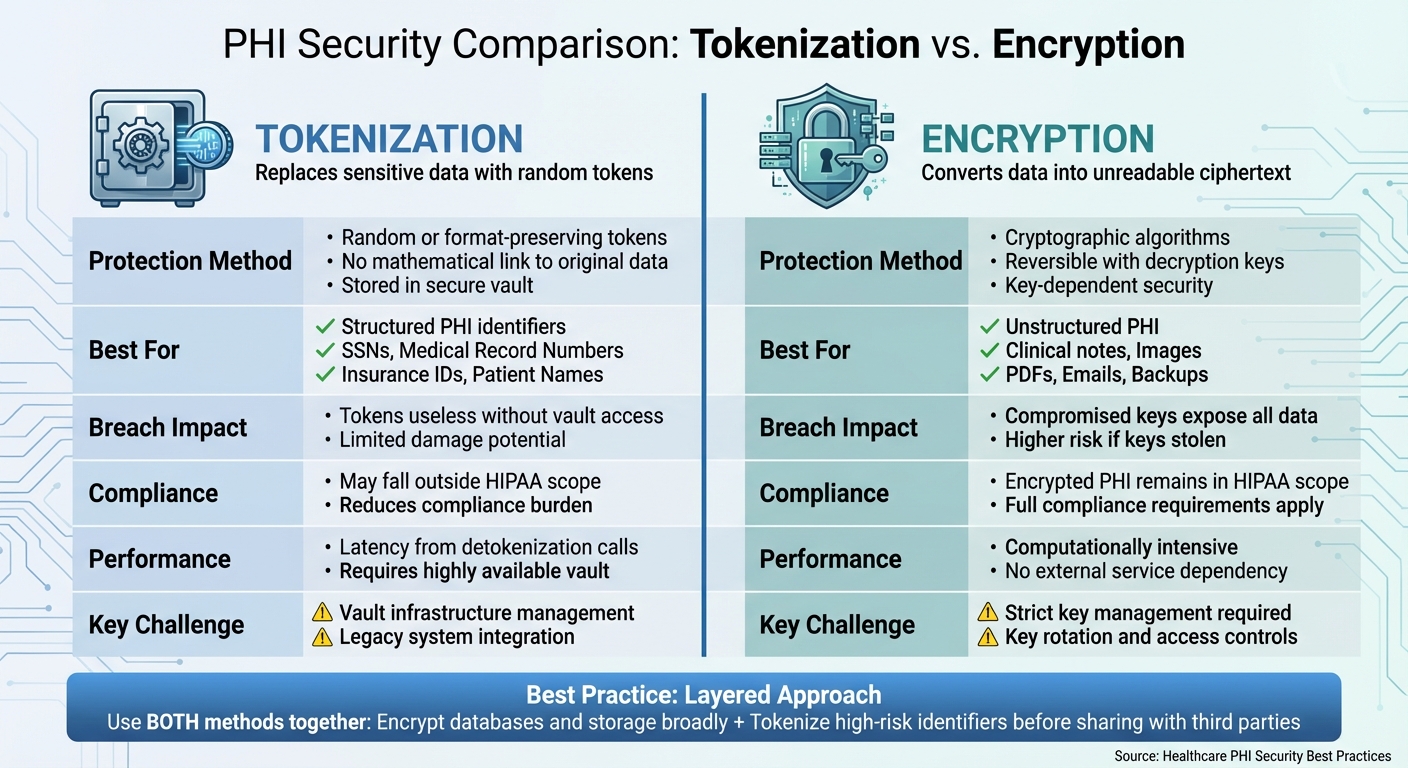
Tokenization and encryption both safeguard Protected Health Information (PHI), but they do so in fundamentally different ways. Encryption relies on cryptographic algorithms to convert data into ciphertext, which can be reversed using a valid decryption key. In contrast, tokenization swaps sensitive data with random or format-preserving tokens that have no mathematical link to the original information. The connection between these tokens and the actual data is securely stored in a token vault, making it impossible to reverse tokens through cryptographic means alone.
This distinction influences how each method is applied. Tokenization is especially effective for structured data like Social Security numbers, medical record numbers, insurance IDs, or patient names, where a one-to-one replacement works seamlessly. On the other hand, encryption is better suited for unstructured data, such as clinical notes, scanned documents, DICOM images, or emails.
The impact of a breach also varies between the two. If an attacker gains access to encrypted data and the associated keys - due to mismanaged credentials or poor key management - the entire dataset can be decrypted. With tokenization, however, stolen tokens are practically useless without access to the secure token vault, significantly limiting the damage.
Here’s a quick summary of these differences:
Comparison Table: Tokenization vs. Encryption
| Factor | Tokenization | Encryption |
|---|---|---|
| Protection Method | Replaces sensitive data with random or format-preserving tokens that lack a mathematical link. | Transforms data into ciphertext using cryptographic algorithms and keys, enabling reversibility. |
| Best For | Structured PHI identifiers (e.g., MRNs, SSNs, insurance IDs, names). | Unstructured PHI (e.g., clinical notes, images, PDFs, backups). |
| Breach Impact | Tokens are useless without vault access, limiting the damage. | If keys are compromised, an attacker can decrypt the data. |
| HIPAA Compliance Scope | Systems with only tokens may fall outside PHI scope, easing compliance efforts. | Encrypted PHI remains in scope under HIPAA because it is reversible. |
| Performance | May introduce latency due to detokenization calls; requires a highly available vault. | Computationally intensive but does not depend on external service calls once keys are available. |
| Operational Complexity | Requires managing token vault availability, scalability, and security. | Demands strict key management, including rotation and access controls. |
| Reversibility | Tokens are irreversible without the tokenization system. | Data can be recovered with the correct decryption key and algorithm. |
When to Use Tokenization, Encryption, or Both
The choice between tokenization, encryption, or a combination of both depends on the type of data and the compliance requirements of the system.
- Tokenization: Ideal for structured PHI identifiers in cloud-based systems, multi-tenant applications, analytics platforms, and SaaS tools. It’s particularly useful for reducing HIPAA compliance scope in non-production environments and enabling secure data sharing across organizations. Additionally, tokenization minimizes breach impact since stolen tokens are essentially worthless without access to the token vault.
- Encryption: Best suited for unstructured PHI like clinical notes, PDFs, DICOM images, and emails. Encryption is critical for protecting entire databases, data warehouses, file repositories, and backups. Whether the data is at rest or in transit, encryption ensures end-to-end protection and allows for granular access control, such as assigning different keys for clinical and billing data.
- Layered Approach: Combining both methods provides the strongest protection. For example, tokenizing PHI upon data entry and storing the token-to-data mapping in an encrypted vault reduces exposure of sensitive information. Encrypting the vault itself, along with securing logs, backups, and network connections, adds another layer of defense. When working with third-party vendors, sharing tokens instead of raw data offers additional security.
Platforms like Censinet RiskOps™ help healthcare organizations manage PHI security by mapping data flows, inventorying PHI locations, and determining the right security controls - whether tokenization, encryption, or both - for each system and vendor. This centralized approach strengthens risk management and ensures compliance with data protection standards.
Conclusion: Selecting the Right PHI Security Method
Key Takeaways for PHI Protection
Choosing between tokenization and encryption depends on factors like data type, use case, and cloud infrastructure. Encryption serves as a foundational safeguard for protecting PHI both at rest and in transit. It’s particularly effective for unstructured clinical data such as notes, images, and PDFs, and is recognized under HIPAA standards. However, encryption is only as strong as its key management. If attackers gain access to encryption keys or exploit weaknesses in key management, PHI can be compromised.
Tokenization, on the other hand, is ideal for safeguarding structured data like Social Security numbers, medical record numbers, and insurance IDs. By replacing sensitive data with tokens, it renders stolen tokens meaningless without access to the secure vault. This approach can significantly reduce the impact of breaches and even exempt certain systems from full HIPAA compliance requirements. However, tokenization introduces operational challenges, such as the need for a reliable vault and the complexity of integrating it into legacy systems like EHRs or billing platforms.
Experts often advocate for a layered security approach. This involves encrypting PHI broadly across databases, storage, and backups, while tokenizing high-risk identifiers before they are shared with cloud-based platforms or third-party tools. For instance, a hospital might encrypt its EHR database and file storage but tokenize patient account numbers and Social Security numbers before sharing data with a cloud-based appointment reminder service or analytics platform. This strategy minimizes exposure while maintaining robust protection for sensitive data.
Ultimately, the effectiveness of any method hinges on a strong, centralized risk management strategy.
The Role of Centralized Risk Management
To effectively combine tokenization and encryption, healthcare organizations need centralized visibility and governance across their PHI landscape. This means identifying where PHI resides, classifying data, evaluating current protections, and pinpointing vulnerabilities in areas like logs, testing environments, and third-party integrations.
Censinet RiskOps™ plays a crucial role in this process. The platform helps healthcare organizations map data flows, manage third-party vendor risks, and select the right security controls for each system. With its collaborative risk network, encompassing over 50,000 vendors and products, Censinet RiskOps™ simplifies risk assessments and supports secure data exchanges. By aligning security strategies with operational and regulatory demands, it ensures that PHI remains protected without unnecessary complexity.
Using a centralized approach like Censinet RiskOps™ strengthens the layered security model, enabling organizations to confidently deploy encryption, tokenization, or both in the areas where they’re needed most. This not only enhances protection but also frees up resources to focus on broader strategic initiatives.
FAQs
What’s the difference between tokenization and encryption when protecting PHI?
Tokenization replaces sensitive PHI (Protected Health Information) with unique, non-sensitive tokens that mimic the format of the original data. These tokens hold no value on their own and can't be reversed unless someone has access to a secure token vault. Encryption, on the other hand, transforms PHI into unreadable ciphertext using specific algorithms and encryption keys, which are necessary to convert the data back to its original form.
Tokenization is especially helpful for limiting exposure to sensitive data and meeting compliance requirements. Meanwhile, encryption works exceptionally well for safeguarding PHI when it’s stored or transmitted. Many organizations combine both approaches to ensure strong protection of patient data in healthcare settings.
How do tokenization and encryption work together to protect PHI?
Tokenization and encryption form a powerful duo when it comes to safeguarding Protected Health Information (PHI). Here's how they work: Tokenization swaps out sensitive data, such as patient details, with placeholder tokens that hold no value to unauthorized users. This means that even if a breach happens, the actual data remains protected. On the other hand, encryption transforms data into an unreadable code during both storage and transmission, ensuring that only those with proper authorization can decode and access it.
Together, these techniques create a robust defense system, helping healthcare organizations reduce risks, secure patient information, and adhere to stringent healthcare regulations.
What challenges come with using tokenization in healthcare systems?
Integrating tokenization into healthcare systems presents a tough challenge, primarily because it needs to fit smoothly with existing EHRs and clinical workflows without causing disruptions. Balancing this seamless integration with the demand for real-time performance and strong security measures adds to the complexity.
Another major concern is the secure handling of encryption keys and storage to prevent any unauthorized access. On top of that, adhering to strict healthcare regulations like HIPAA makes the process even more intricate, as it requires constant monitoring and updates to stay aligned with changing standards.


