Ultimate Guide to Post-Breach Compliance in Healthcare
Post Summary
When a healthcare organization discovers a data breach, quick action is critical to meet legal requirements, reduce risks, and maintain patient trust. Post-breach compliance involves identifying the breach, notifying affected parties, meeting HIPAA and state-specific deadlines, and taking steps to prevent future incidents.
Here’s what you need to know:
- HIPAA Requirements: Notify affected individuals within 60 days. Larger breaches (500+ individuals) require reporting to HHS and media outlets. Smaller breaches must be logged and reported annually.
- Risk Assessments: Evaluate the type of data involved, who accessed it, and mitigation efforts. Documentation is essential for audits.
- State Laws: Often stricter than HIPAA, with shorter timelines and additional requirements like notifying attorneys general.
- Vendor Risks: Third-party breaches are common. Ensure strong contracts, risk assessments, and prompt vendor reporting.
- Regulatory Oversight: Keep thorough documentation, including policies, training logs, and breach files, to meet OCR expectations.
- Improving Security: Strengthen internal controls, update policies, and implement tools like multi-factor authentication and encryption.
Recovering from a breach is about more than just compliance - it’s about stabilizing operations, addressing vulnerabilities, and rebuilding trust. The steps you take now can protect your organization in the future.
Regulatory Requirements for Post-Breach Recovery
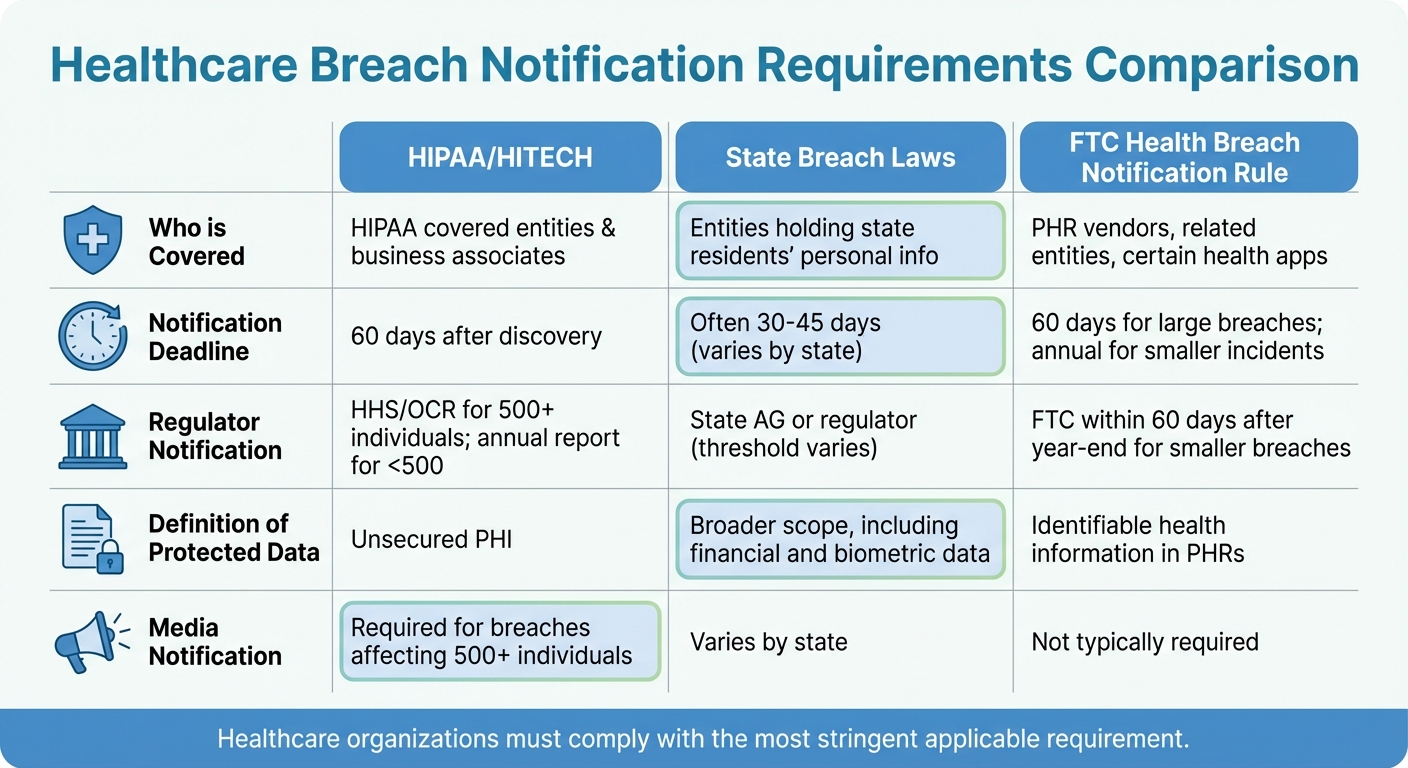
Healthcare Breach Notification Requirements: HIPAA vs State Laws vs FTC Rules
Healthcare organizations must navigate a maze of compliance rules after a data breach. Federal laws provide a foundation, but state regulations and industry standards often add stricter layers. These combined requirements aim to avoid penalties and rebuild trust, which is critical for recovery and maintaining operations in the face of reputational and operational risks.
HIPAA and Federal Requirements
The HIPAA Breach Notification Rule is the cornerstone for post-breach compliance, applying to covered entities and business associates. When there's an unauthorized use or disclosure of unsecured protected health information (PHI), organizations must conduct a risk assessment based on four specific factors. If the assessment does not show a low probability of compromise, the incident is presumed to be a breach, triggering notification requirements [4].
Notifications must be timely and clear. Affected individuals need to be informed within 60 days, and for larger breaches, additional steps must be taken [2]. These notices should explain what happened, the type of PHI involved, steps individuals can take to protect themselves, and how to get more information [2].
Business associates also have responsibilities. They must notify the covered entity promptly - no later than 60 days after discovering a breach - and provide details about affected individuals and other relevant information [2]. Delays in communication can lead to violations, making swift coordination between vendors and healthcare organizations essential [2].
The HITECH Act reinforces these timelines and requires detailed logging, annual reporting, and stricter penalties for noncompliance [4]. For entities handling substance use disorder records, 42 CFR Part 2 adds another layer of confidentiality rules that must align with HIPAA, often necessitating legal review for compliance [4].
Beyond notification, the HIPAA Security Rule mandates updates to safeguards after a breach. This includes revising policies, retraining staff, documenting corrective actions, and keeping a breach file ready for potential Office for Civil Rights (OCR) inquiries [4]. OCR expects thorough documentation of risk assessments, notification decisions, mitigation efforts, and implemented security measures [4].
For organizations outside HIPAA’s scope - like certain health apps and personal health record (PHR) vendors - the FTC Health Breach Notification Rule applies. These entities must notify individuals and the FTC after a breach. Smaller incidents require annual reporting, while larger breaches demand notification within 60 days [3].
State and local laws further refine these requirements, adding another layer of complexity.
State and Local Breach Laws
While HIPAA sets a federal standard, state data breach laws often impose stricter deadlines and broader definitions [2][6]. Many states require notification to the Attorney General (AG) when a certain number of residents - often 500 or 1,000 - are affected, typically within 60 days of notifying individuals [6]. Some states also dictate the content of notices, require language accessibility, or mandate services like credit monitoring and identity theft protection [6]. For instance, Oklahoma’s 2025 update expanded the definition of personal information to include biometric data, government IDs, and unique electronic identifiers, and now requires AG notification for breaches affecting 500 or more residents [6].
For multi-state health systems, managing compliance can be particularly challenging. A practical approach is maintaining an internal "50-state breach law" guide summarizing deadlines, content requirements, regulatory thresholds, and special provisions for health data [2]. When multiple states are impacted, organizations should default to the shortest applicable timeline and use adaptable template notification letters to meet state-specific requirements [2].
| Requirement Area | HIPAA / HITECH | State Breach Laws | FTC Health Breach Notification Rule |
|---|---|---|---|
| Who is covered | HIPAA covered entities & business associates | Entities holding state residents' personal info | PHR vendors, related entities, certain health apps |
| Notification deadline | 60 days after discovery | Often 30–45 days (varies by state) | 60 days for large breaches; annual for smaller incidents |
| Regulator notification | HHS/OCR for 500+ individuals; annual report for <500 | State AG or regulator (threshold varies) | FTC within 60 days after year-end for smaller breaches |
| Definition of protected data | Unsecured PHI | Broader scope, including financial and biometric data | Identifiable health information in PHRs |
| Media notification | Required for breaches affecting 500+ individuals | Varies by state | Not typically required |
Industry Cybersecurity Guidelines
In addition to regulatory mandates, following industry cybersecurity guidelines strengthens post-breach recovery efforts. Two key resources here are HHS's Cybersecurity Performance Goals (CPGs) and the NIST frameworks.
HHS’s Cybersecurity Performance Goals outline security practices tailored to healthcare, such as multi-factor authentication, network segmentation, secure email, asset inventory, regular backups, and incident response planning [4]. After a breach, organizations can map the root cause to specific CPGs and create a remediation plan to address vulnerabilities. Incorporating these goals into risk registers, capital plans, and board reports demonstrates alignment with federal recommendations.
The NIST Cybersecurity Framework (CSF) and NIST SP 800-53 are widely used to align security controls with HIPAA’s Security Rule and guide remediation efforts [4]. The NIST CSF organizes security practices into five functions - Identify, Protect, Detect, Respond, and Recover - helping organizations assess weaknesses and prioritize improvements. Meanwhile, NIST SP 800-53 provides detailed security and privacy controls that can be customized for HIPAA compliance. For example, a hospital might conduct a post-breach review, update its risk register and corrective action plans, and align its policies with NIST 800-53 security controls [4].
Breach Notification and Reporting Steps
When a potential breach arises, healthcare organizations must act swiftly and systematically to evaluate the situation, fulfill reporting obligations, and notify all necessary parties. Missing deadlines or skipping critical steps can lead to penalties and damage patient trust. That’s why having a clear, well-defined plan is crucial. Below is an outline of the process, from assessing the risk to coordinating with regulatory agencies.
Post-Incident Risk Assessment Process
Once a breach is suspected, the first step is to determine if it qualifies as a reportable incident. This involves confirming whether unsecured PHI (protected health information not encrypted to NIST standards) was involved. From there, apply the four-factor risk assessment to evaluate whether there’s more than a “low probability” that PHI has been compromised[5]. This includes:
- Nature and extent of the PHI involved: Assess the sensitivity of the data, such as Social Security numbers, medical diagnoses, or financial information.
- Identity of the unauthorized party: Determine whether the breach involved an internal employee, a trusted vendor, or an external attacker.
- Acquisition or viewing of PHI: Use forensic evidence or system logs to verify whether the data was accessed or viewed.
- Risk mitigation efforts: Review actions taken to reduce risk, such as retrieving the data or confirming no further access occurred.
Under HIPAA, an incident is presumed to be a reportable breach unless the risk assessment clearly shows a low probability of compromise[5]. For breaches involving third-party vendors, include vendor reports, business associate agreements, forensic findings, and centralized risk management tools to evaluate the situation thoroughly. Document every decision and piece of evidence, as this may be required by the Office for Civil Rights (OCR) or state attorneys general during investigations[5].
Notification Deadlines and Requirements
If the risk assessment determines the incident is a reportable breach, notifications must be sent to affected individuals, the Department of Health and Human Services (HHS)/OCR, and, in some cases, the media. Under HIPAA rules, affected individuals must be notified no later than 60 calendar days after the breach is discovered[5]. Discovery is defined as the point when any workforce member or agent knows - or reasonably should know - about the breach.
Notifications to individuals should be sent via first-class mail to their last known address or by secure email if the individual has opted for electronic communication. Each notification must include:
- A brief explanation of the breach, including the dates of the incident and discovery.
- Details about the types of PHI involved.
- Steps individuals can take to protect themselves.
- Actions your organization is taking to investigate and prevent future breaches.
- Contact information, such as a toll-free number, email, or mailing address.
For HHS/OCR, breaches affecting 500 or more individuals must be reported via the HHS breach portal within 60 days of discovery. For smaller breaches (fewer than 500 individuals), maintain a breach log and submit a consolidated report to HHS within 60 days after the end of the calendar year in which the breach occurred[5]. Additionally, if the breach impacts more than 500 residents in a single state or jurisdiction, prominent media outlets must be informed within the same 60-day window.
State laws often have stricter deadlines, such as 30 or 45 days, and may require notification to state attorneys general. For example, Oklahoma's updated law mandates notifying the state attorney general within 60 days when 500 or more residents are affected[6]. To ensure compliance, identify the most stringent deadlines across HIPAA and state laws, and create an internal timeline to meet them[6]. After completing notification requirements, coordinate with law enforcement and regulatory bodies to manage the response effectively.
Working with Law Enforcement and Regulators
If criminal activity, such as ransomware or theft, is suspected, notify law enforcement immediately. Be sure to document any requests from investigators to delay notifications, which are typically made to avoid interfering with ongoing investigations. These delays must be limited to the timeframe specified by law enforcement[5]. Maintain regular communication with investigators, sharing forensic findings and coordinating public messaging to ensure consistency.
For breaches involving business associates, confirm that they meet their reporting obligations, which are generally within 60 days of discovery. Collaborate with affected vendors to gather evidence, define the scope of the breach, and prepare documentation for regulators. If the breach spans multiple states or involves several vendors, assign a single point of contact to streamline communication with state attorneys general, OCR, and other regulatory bodies. This approach minimizes the risk of conflicting reports and ensures a cohesive response[6].
Creating a Compliance Documentation Strategy
After addressing breach notifications and performing initial risk assessments, your next critical step is establishing a solid documentation process. This serves as a vital defense mechanism. Regulators, particularly the Office for Civil Rights (OCR), demand clear evidence that your organization has implemented and maintained effective security and privacy measures before, during, and after an incident.
The cornerstone of a strong documentation strategy is a centralized repository where all essential records are stored in one place. These records should include:
- The latest HIPAA security risk analysis and risk management plan
- Formal incident response plans
- Detailed breach files, including investigation notes and forensic reports
- Copies of breach notifications sent to patients and regulators
- Business associate agreements with security provisions
- Security policies and procedures
- Training materials and attendance logs
- Governance documents like committee charters and meeting minutes
- Corrective action plans with progress tracking [4][5]
To make this repository functional and audit-ready, use consistent naming conventions, version control, and an indexed system to quickly retrieve evidence when needed [4][7].
When breaches involve third-party vendors, the documentation workload grows. You’ll need to maintain a detailed timeline that includes when the vendor notified your organization, when internal teams escalated the issue, key milestones in risk assessment, containment actions, and the dates notifications were sent to required parties [2][5]. Supporting materials should include vendor reports, forensic findings, business associate agreements, and timestamps for notification approvals [2][7]. Tools like Censinet RiskOps™ can help centralize vendor risk assessments, security questionnaires, and remediation plans, making it easier to prove due diligence in managing vendor risks.
Retention Requirements and Regulatory Expectations
Under HIPAA, organizations are required to retain documentation for at least six years from the date of creation or the last effective date, whichever is later [8]. This includes policies, procedures, breach logs, and records of actions taken. Some state laws impose even longer retention periods, so aligning your practices to cover six to seven years ensures compliance with both federal and state regulations [4][5][6]. The stakes are high - since 2003, OCR has collected over $150 million in HIPAA settlements, with notable cases like Anthem’s $16 million and Premera’s $6.85 million penalties highlighting failures in documentation and risk management.
Required Documentation for Audits
When OCR or state regulators investigate, they typically request a specific set of records to assess compliance. Your organization should be prepared to provide:
- Breach risk assessments, including methodologies and conclusions on whether PHI was compromised
- Copies of notifications sent to individuals, HHS/OCR, media, and state attorneys general (if applicable)
- Logs of smaller breaches affecting fewer than 500 individuals, reported annually to HHS
- Security incident and breach policies and procedures
- Access and activity logs related to the incident
- Records of any sanctions against workforce members
- Corrective action plans with evidence of their effectiveness [4][7][5]
OCR investigations often highlight common compliance failures, such as inadequate risk analysis and management, insufficient policies, and poor documentation of training or workforce sanctions. Large penalties frequently stem from missing or incomplete records, particularly around risk analysis, patch management, and access controls. Regulators expect organizations to back up their compliance efforts with logs, tickets, meeting minutes, training records, and system configurations.
To meet these expectations, maintain a standardized documentation template that includes:
- The date and time of discovery and containment actions
- Affected systems and data, including PHI types and record counts
- Root cause analysis and forensic findings
- Decision-making rationale for determining reportability
- Copies of notifications issued, along with dates and recipient lists
- Post-incident corrective and preventive actions with assigned responsibilities and deadlines [5][7][3]
For third-party risks, retain signed business associate agreements, vendor risk assessments, security questionnaires, remediation tracking records, and evidence of ongoing monitoring. These materials are critical and often scrutinized during OCR settlements and regulatory reviews.
| Documentation Category | Key Artifacts to Maintain | Audit / OCR Use Case |
|---|---|---|
| Risk Analysis & Management | Risk analyses, asset inventories, risk registers, treatment plans | Demonstrates compliance with HIPAA Security Rule requirements |
| Policies & Procedures | Privacy/security policies, incident response plans, BAAs | Establishes a governance framework and workforce expectations [8] |
| Training & Awareness | Training curricula, attendance logs, role-based training | Proves workforce training and awareness, addressing frequent OCR findings |
| Incident & Breach Files | Incident logs, timelines, investigation notes, notifications, CAPs | Shows timely and appropriate breach response and remediation [5][7] |
| Third-Party & Supply Chain | Signed BAAs, vendor risk assessments, remediation tracking | Demonstrates oversight and risk management in the supply chain |
| Governance & Oversight | Committee charters, meeting minutes, leadership reports | Reflects leadership accountability and continuous compliance monitoring |
Preparing for OCR Investigations
Regular tabletop exercises and internal audits are essential to ensure readiness for OCR investigations. These exercises should simulate data requests, testing your ability to quickly locate and produce all required documents. They also verify the clarity of incident timelines, the consistency between written policies and actual practices, and the preparedness of key personnel - such as your privacy officer, CISO, and legal counsel - to answer detailed questions [4][7].
Each exercise should end with a gap analysis and an action plan to update your documentation index, refine policies, and identify additional evidence to collect during real incidents. For larger organizations, involve teams managing supply chain, vendor oversight, and IT operations to ensure third-party documentation is readily accessible.
"Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required." - Terry Grogan, CISO, Tower Health [1]
Beyond tabletop exercises, conduct annual internal HIPAA audits that reflect OCR’s typical requests. These audits should:
- Ensure risk analyses are current and include all ePHI systems, such as cloud services and medical devices
- Test policies like access controls, log reviews, and sanction enforcement
- Validate that breach notifications meet HIPAA and state law requirements [5][7]
Post-breach audits should focus on areas impacted by the incident, such as vendor risk management, access controls, and patching processes. Confirm that corrective actions from root cause analyses have been implemented and that updated controls are functioning as intended. Finally, review recent policy changes to ensure alignment with actual practices and verify that notification processes comply with updated timelines, especially in states with stricter deadlines than HIPAA’s 60-day requirement [2][6].
Document audit results thoroughly, including findings, remediation owners, deadlines, and evidence of closure. This approach not only strengthens your compliance posture but also ensures you’re prepared to demonstrate timeliness and sound decision-making during an OCR investigation [2][5]. Key materials regulators will expect include a detailed breach timeline, meeting notes, and records showing the rationale for any delays, as well as documentation of when notifications were drafted, approved, and sent.
sbb-itb-535baee
Improving Cybersecurity After a Breach
A breach calls for immediate action to strengthen cybersecurity defenses. Ransomware groups often return to exploit organizations that fail to adapt their security measures. In 2023, the average cost of a healthcare breach in the U.S. reached $10.93 million - making it the most expensive industry for breaches for 13 straight years. This highlights the dual importance of compliance and financial protection when reinforcing security after an incident.
Once containment is achieved and notifications are sent, it’s crucial to reassess where sensitive data, including electronic protected health information (ePHI), is stored. This includes cloud applications and medical devices. Evaluate access controls, authentication methods, and the accuracy of your latest HIPAA risk analysis. Pay close attention to vendor-facing controls, especially for third parties involved in the breach, and review logging, monitoring, and incident response processes. Documenting these efforts for OCR and state investigators is critical. This documentation not only helps prioritize remediation efforts but also ensures clear ownership, timelines, and budgeting. These steps build on prior compliance measures to secure future operations.
Reviewing Third-Party and Vendor Risks
Start by listing all vendors that access PHI or support critical clinical and supply chain systems. Conduct fresh risk assessments on these vendors, focusing on their security controls, breach history, and readiness to respond to incidents. Review and update Business Associate Agreements (BAAs) to ensure they align with current HIPAA, HITECH, and state regulations. These agreements should include clear breach notification timelines, audit rights, minimum security standards (like MFA and encryption), and oversight of subcontractors.
For vendors using subcontractors, demand transparency through data flow diagrams and SOC 2 reports. Ensure BAAs require vendors to enforce similar safeguards and reporting obligations on their subcontractors, addressing risks further down the chain. High-risk vendors should be placed under corrective action plans, with the option to suspend or terminate contracts if they fail to meet security expectations.
Implement a tiered system to categorize vendors based on risk - critical, high, medium, or low. Factors like PHI volume, patient care impact, network connectivity, and security history should guide this classification. Critical and high-risk vendors should undergo more rigorous security reviews, including detailed questionnaires, SOC reports, and technical validations like vulnerability scans. Contracts with these vendors should mandate shorter notification deadlines and more frequent security attestations. Continuous monitoring tools can help track vendor security postures, while joint tabletop exercises can test incident response coordination across the supply chain.
Implementing Security Controls
After reviewing vendor risks, focus on strengthening internal controls. Address the root causes of the breach first. Enforce multi-factor authentication (MFA) for remote access, privileged accounts, VPNs, and systems handling ePHI. Expand encryption for data both in transit and at rest, and adopt least privilege and role-based access to limit who can view or modify sensitive data. Enhance logging and monitoring by using centralized security solutions like SIEM for critical applications, and implement network segmentation to restrict lateral movement, particularly around medical devices and supply chain interfaces.
A risk-based rollout is key. Start by securing privileged and external-facing access, then move to high-value clinical and financial systems. This process should include configuration baselines, change management procedures, and post-deployment validations like access reviews and log checks. Adopting a Zero Trust model can further improve security by treating every user, device, and application as untrusted until continuously verified. This includes measures like strong identity proofing, centralized access management, just-in-time privilege elevation, and rigorous device checks.
Update HIPAA policies, formalize a risk management plan, and ensure each identified gap has a clear remediation action, deadline, and owner. Governance improvements might involve making cybersecurity a regular topic at board meetings, forming a cross-functional cyber risk council, and enhancing training programs with role-specific modules. Simulations of phishing attacks and social engineering, as well as regular incident response drills, can demonstrate to regulators that the organization is committed to building resilience.
Using Censinet RiskOps™ for Post-Breach Compliance

Censinet RiskOps™ offers healthcare organizations a streamlined way to reassess both third-party and internal risks after a breach. The platform simplifies vendor evaluations by centralizing risk questionnaires tailored to healthcare standards like HIPAA and HITECH. It collects and scores evidence such as SOC 2 reports, penetration tests, and BAAs, while benchmarking vendors’ security postures against industry peers. This helps prioritize high-risk vendors, track corrective actions, and document decisions for audits and regulators.
Censinet RiskOps™ also maps vendor roles within clinical services and critical operations, enabling organizations to focus on areas with the greatest patient-care impact. It serves as a centralized system for risk assessments, remediation plans, and supporting evidence - key documentation requested during OCR investigations. By linking identified risks to mitigation actions, owners, and timelines, the platform provides a structured approach to risk management. Dashboards keep leadership and compliance teams informed, ensuring audit readiness and demonstrating active management of cyber and vendor risks.
Post-breach metrics like the percentage of high-risk vendors mitigated, MFA coverage, and incident response times are crucial for tracking progress. Censinet RiskOps™ aggregates and visualizes these metrics, offering insights by vendor, business unit, and project. This ensures organizations can maintain resilience and stay prepared for regulatory scrutiny.
Conclusion
Recovering from a healthcare breach is no small feat. Every step, from assessing the risks to implementing remediation, plays a crucial role in navigating the aftermath. It's about more than just meeting legal requirements - it’s about adopting a thorough approach that prioritizes compliance, operational stability, and trust. Organizations need to act swiftly to contain the incident, conduct detailed risk assessments, and meet notification obligations. For example, HIPAA requires timely notifications, but treating those deadlines as the maximum limit rather than a target is key. Documenting every decision and action along the way not only prepares organizations for OCR investigations but also signals a strong commitment to accountability.
Regaining trust goes hand in hand with improving security and clear communication. Transparent notifications, supportive measures, and consistent public updates show a dedication to protecting patients. Internally, it’s essential to address the root causes of the breach with measures like multi-factor authentication, encryption, network segmentation, and continuous monitoring. Strengthening supply chain and third-party risk management is another critical step in closing security gaps.
Strong governance and well-organized documentation also play a significant role in building regulatory confidence. Regular mock OCR audits, cross-functional risk committees, and role-based workforce training help maintain a proactive security stance. Tools such as Censinet RiskOps™ can simplify vendor risk assessments and ensure documentation is audit-ready, enabling organizations to shift from reactive crisis management to a more consistent, evidence-based approach to reducing risks.
A breach is often a turning point. By treating recovery as an ongoing process, organizations can build long-term resilience. Stabilizing operations, strengthening compliance, and evolving security practices create a foundation for future success. Incorporating lessons learned, investing in modern security frameworks, and embedding cyber risk into broader enterprise strategies can transform a challenging incident into an opportunity to build a safer, more reliable environment for both patients and partners.
FAQs
What should healthcare organizations do right after discovering a data breach?
When a breach occurs, the first thing you need to do is alert your incident response team. Their job is to take charge of the situation and start managing it immediately. Containing the breach as quickly as possible is critical to prevent any further exposure of sensitive data. Make sure to document every single step and action taken throughout the response process.
It's also essential to inform affected patients and notify regulatory authorities within the required timeframes to meet legal requirements. Once the immediate crisis is under control, conduct a thorough forensic investigation. This will help you determine the full scope of the breach, uncover its root cause, and implement measures to prevent it from happening again. These steps are key to minimizing damage and ensuring a smoother recovery.
What are the key differences between HIPAA and state laws for breach notifications?
HIPAA mandates that breach notifications be sent "without unreasonable delay" and no later than 60 days after the breach is discovered. However, many state laws set tighter deadlines, often requiring notifications within 30 days - or even less. On top of that, some states require additional steps, like notifying specific regulatory agencies or using particular methods to inform affected individuals.
State laws can also introduce unique rules or impose stricter penalties for failing to comply. For healthcare organizations, it's crucial to stay on top of both federal and state requirements. Understanding these differences helps ensure breaches are handled promptly and correctly, reducing the risk of legal trouble.
How can healthcare organizations reduce the risk of future data breaches?
To minimize the chances of data breaches, healthcare organizations need to embrace proactive risk management strategies. Solutions like Censinet RiskOps™ offer real-time monitoring, cybersecurity benchmarking, and customized risk management tools tailored to the unique challenges of healthcare. These features help pinpoint and address weaknesses before they escalate into serious threats.
In addition, organizations should enforce strict access controls, regularly train staff on data security practices, and ensure adherence to regulations such as HIPAA. Establishing a solid breach response plan and conducting routine audits can further enhance security measures and help maintain patient trust in protecting sensitive information.


