Top 5 Questions for Vendor Risk Assessment
Post Summary
Vendor risk assessment is a critical process for healthcare organizations to ensure third-party partners handle sensitive patient data securely and comply with HIPAA standards. Weak vendor practices can lead to data breaches, regulatory penalties, and disruptions in clinical care. To mitigate these risks, healthcare organizations should ask these five key questions when assessing vendors:
-
How do you handle Protected Health Information (PHI)?
- Understand the vendor's processes for accessing, storing, transmitting, and disposing of PHI.
- Verify encryption standards, access controls, and data lifecycle management practices.
-
What cybersecurity controls are in place?
- Evaluate identity and access management (e.g., multi-factor authentication, role-based access).
- Assess network security measures, vulnerability management, and incident detection systems.
- How do you ensure compliance with regulatory and security frameworks?
-
What are your incident response and business continuity plans?
- Examine their incident response procedures, breach notification timelines, and disaster recovery capabilities.
- Confirm readiness through evidence of regular testing and clear recovery objectives.
-
How do you manage subcontractors and long-term risks?
- Ensure subcontractors meet the same security and compliance standards.
- Review the vendor’s financial stability, supply chain oversight, and exit strategies.
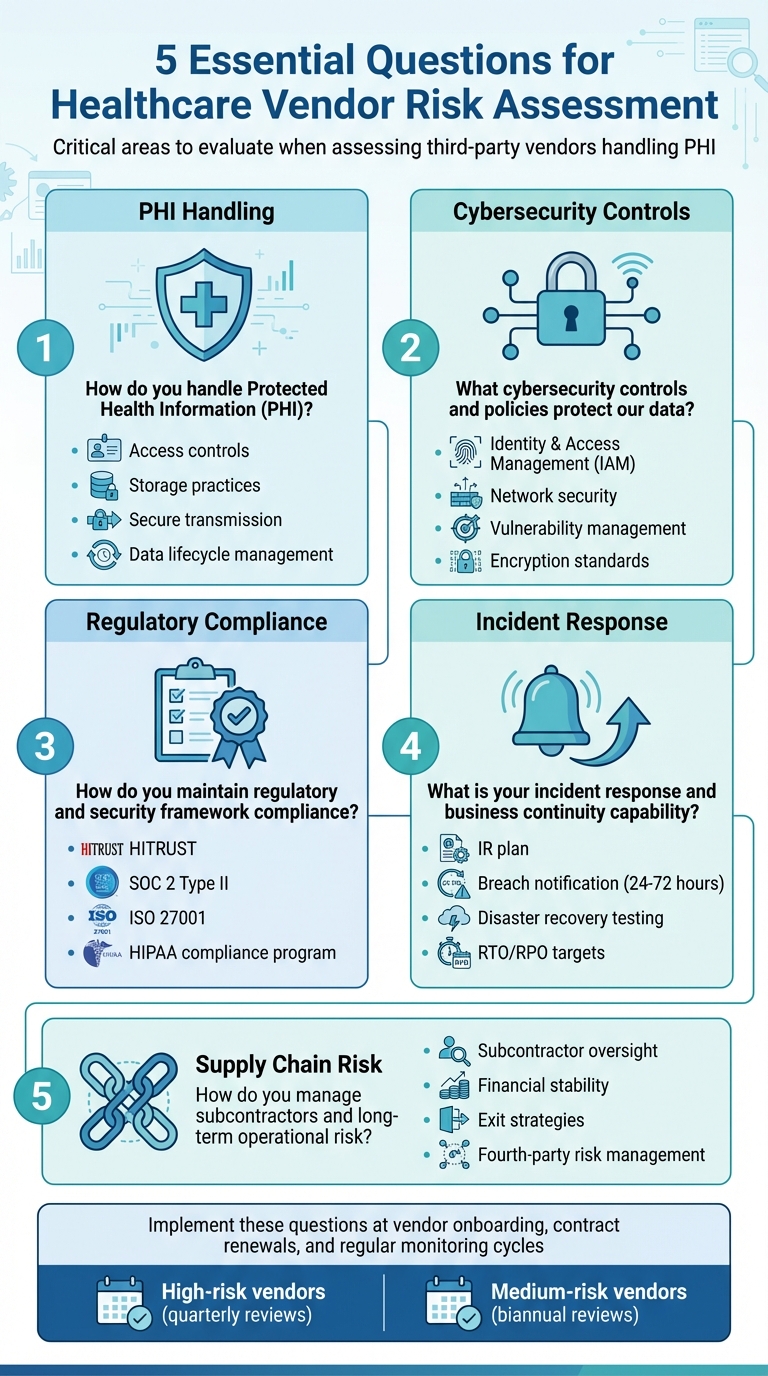
5 Essential Questions for Healthcare Vendor Risk Assessment
1. How Will You Access, Use, Store, and Transmit Protected Health Information?
Before granting vendor access, it's crucial to understand their data handling procedures. This step forms the foundation of a thorough risk assessment, ensuring compliance with HIPAA regulations and safeguarding patient information. Healthcare organizations are required to document and evaluate how vendors access, use, disclose, store, transmit, and dispose of Protected Health Information (PHI). This process is a key part of due diligence and is formalized through Business Associate Agreements (BAAs) [2]. By starting with this big-picture understanding, you can dive deeper into specifics like access, storage, and transmission.
Access Controls
Begin by assessing the vendor's access controls. Ask them to explain their user authentication processes, how they enforce role-based access restrictions, and whether they adhere to the principle of least privilege. A good question to pose is: "How do you log, monitor, and review access to PHI and administrative actions?" Strong vendors typically maintain detailed audit logs that track every interaction with PHI and generate alerts for any unusual activity.
Storage Practices
Next, focus on how the vendor stores PHI. Determine whether the data is housed on-premises, in the cloud, or a combination of both. Ask about the encryption standards they use to protect data at rest. Make sure the BAA explicitly outlines what uses and disclosures of PHI are allowed, leaving no room for misinterpretation.
Secure Transmission
Data transmission is another critical area. Vendors should clearly explain their methods for securely moving PHI, both internally and externally. This includes their encryption standards for data in transit, how they integrate securely with clinical systems, and how they oversee subcontractors who may handle PHI.
Data Lifecycle Management
It's also essential to review how the vendor manages PHI throughout its lifecycle. Ask about their policies for data retention, archival security, and destruction. Request supporting documentation to back up their claims, such as certifications like SOC 2 or HITRUST, detailed security policies, and evidence of regular audits.
An effective vendor assessment should focus on three main areas:
- Compliance: Ensure the vendor meets HIPAA requirements, has a proper BAA in place, and holds certifications like HITRUST or SOC 2.
- Security Controls: Look for alignment with frameworks like NIST or CIS, strong access management, and a solid incident response plan.
- Data Protection: Confirm their encryption standards and policies cover every stage of the data lifecycle.
2. What Cybersecurity Controls and Policies Protect Our Data and Clinical Operations?
When it comes to safeguarding Protected Health Information (PHI) and ensuring the smooth functioning of clinical systems, both technical and administrative measures play a critical role. These safeguards form the backbone of a vendor's security program, covering everything from preventing breaches to detecting threats and maintaining system integrity. A closer look at identity management and network security is essential to ensure robust protection.
Start by examining the vendor's Identity and Access Management (IAM) practices. Multi-factor authentication (MFA) should be mandatory for accessing PHI and administrative systems. Access permissions must be role-based, with clearly defined roles, regular reviews, and immediate removal of access when roles change. For accounts with elevated privileges - like cloud or database administrators - ask about controls such as just-in-time access, session recording, and restrictions on direct access to production PHI.
Next, focus on network security, which serves as a strong defense for clinical operations. Vendors should explain their network segmentation strategies, particularly how they isolate systems handling PHI from other environments. Key protections include firewalls, intrusion detection and prevention systems (IDS/IPS), secure VPNs for remote access, and comprehensive logging and monitoring. These measures help limit the spread of threats and safeguard critical systems in the event of a breach.
Regular vulnerability scans are another must. Vendors should address critical vulnerabilities within 15–30 days and maintain a documented patch management process. For hosted applications, look for evidence of a secure development lifecycle (SDLC), including code reviews and penetration testing. Additionally, ask if the vendor employs AES-256 encryption for PHI during transfer and storage, and whether MFA and role-based access controls are enforced for systems managing PHI.
Request copies of key security policies like acceptable use, incident response, data classification, and change management. These documents provide insight into governance and accountability. Also, verify their backup procedures, disaster recovery plans, service-level agreements (SLAs), and business continuity measures. These elements ensure the vendor’s security practices align with recognized frameworks like NIST or CIS and comply with HIPAA's technical safeguard requirements.
3. How Do You Maintain Regulatory and Security Framework Compliance?
Once you've established strong cybersecurity measures, the next step is ensuring ongoing compliance. This isn’t just a one-time task - it’s a continuous process that requires vendors to provide proof through documentation, certifications, and audits. For healthcare organizations, verifying that vendors meet HIPAA requirements and hold recognized security certifications is absolutely essential. Start by determining whether the vendor processes or stores protected health information (PHI). If they do, ask for evidence of their HIPAA compliance program. This should include third-party assessments, detailed security policies, and employee training records. Additionally, request the vendor's latest HIPAA risk assessment and remediation plans to see how they identify and address vulnerabilities.
Certifications like HITRUST, SOC 2 Type II, and ISO 27001 are key indicators of a vendor’s security practices. Ask for their current HITRUST certification letter, including the scope of coverage, their most recent SOC 2 Type II report for systems handling your data, and any ISO 27001 certificates if applicable. These documents not only confirm the existence of security controls but also show whether those controls have been tested and proven effective over time. Pay close attention to findings or exceptions in SOC 2 reports and ask how the vendor resolved those issues.
It’s also important to understand how vendors keep their compliance programs up to date. Ask how often they review and update policies, track regulatory changes, and address past audit findings. Compliance should be an ongoing effort, with annual evaluations of policies, risk assessments, and security controls. Internal or external audits should verify their effectiveness. Additionally, inquire about any regulatory violations or significant audit findings from the past three to five years and how those were resolved. This demonstrates whether the vendor treats compliance as a priority or just a checkbox.
Documentation plays a critical role in verifying a vendor’s compliance. Request schedules for policy reviews, timelines for internal audits, and logs of corrective actions. Contracts should also include clauses requiring vendors to notify you immediately of any enforcement actions, compliance failures, or security incidents. Tools like Censinet RiskOps™ simplify this process by allowing vendors to share completed security questionnaires, along with supporting documentation, in a streamlined way[1].
As Brian Sterud, CIO of Faith Regional Health, stated: "Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters."[1]
Be vigilant for warning signs such as vague answers, expired certifications, reluctance to share audit reports, or inconsistencies between documented policies and real-world practices. If a vendor cannot provide clear evidence of compliance or has unresolved issues from recent audits, it may be time to dig deeper or consider other options. Ultimately, verifying compliance isn’t just about reviewing paperwork - it’s about ensuring the vendor’s program is actively implemented and maintained.
sbb-itb-535baee
4. What Is Your Incident Response, Breach Notification, and Business Continuity Capability?
No vendor is immune to security incidents or operational disruptions. The key is how well they can respond and recover when challenges arise. Start by requesting the vendor's written incident response (IR) plan. This plan should outline critical elements like a designated incident response lead and team, severity levels with clear escalation criteria, round-the-clock availability, and detailed procedures for detecting, containing, eradicating, and recovering from incidents such as ransomware attacks, credential compromises, or web application breaches[2]. Look for evidence of tools like EDR/XDR, continuous monitoring, and predefined isolation protocols, along with runbooks for restoring services. Regular testing of this plan is essential to ensure readiness in real-world scenarios.
Testing incident response and disaster recovery plans is a vital part of preparedness. Ask vendors about their most recent tests, the results, and how they addressed any vulnerabilities uncovered. Due diligence often includes verifying whether vendors have a dedicated security or incident response team and if they routinely conduct drills for their IR and disaster recovery plans. Vendors who prioritize regular reviews and simulations demonstrate a serious commitment to being prepared[2].
Breach notification timelines are another critical consideration. While HIPAA allows up to 60 days for breach notifications, Business Associate Agreements (BAAs) often require much faster action - typically within 24 to 72 hours. Ensure the notification process includes defined channels, required content, and escalation steps to guarantee timely responses. Additionally, ask vendors to disclose any security incidents or breaches from the past three to five years, including the measures they took to strengthen their systems and the lessons they learned from those events[4]. Beyond quick notifications, vendors must also show they can maintain operational resilience during and after an incident.
For business continuity and disaster recovery, vendors should have a documented plan that covers critical areas like data center or cloud region arrangements, failover architectures, and prioritized recovery for systems that handle patient care and PHI. Request clear Recovery Time Objective (RTO) and Recovery Point Objective (RPO) targets for each service, especially for essential clinical systems. Vendors should also provide proof of regular disaster recovery tests, such as semiannual failover exercises, and explain how they addressed any gaps identified during these tests[3].
Tools like Censinet RiskOps™ can simplify the process of assessing vendors' incident response, business continuity, and disaster recovery capabilities. These platforms help standardize evaluations, making it easier to benchmark resilience and establish consistent expectations across vendors.
5. How Do You Manage Subcontractors, Fourth Parties, and Long-Term Operational Risk?
When it comes to vendor security, the weakest link in the supply chain often dictates the overall risk. If a vendor depends on subcontractors or fourth parties for services, data storage, or clinical operations, your organization inherits those risks. Unfortunately, many Business Associate Agreements in healthcare fall short, lacking enforceable terms for subcontractor oversight. This limits your ability to address issues when they arise [3]. To mitigate this, start by requesting a full list of subcontractors who will access, process, or store protected health information (PHI). Contracts should clearly prohibit the use of undisclosed subcontractors for covered services and require vendors to notify you of any changes in their supply chain.
Assess how well vendors extend their risk management practices to their subcontractors and fourth parties. Vendors should hold subcontractors to the same high standards you expect from them. Your contracts should ensure that subcontractors meet or exceed your security and compliance requirements, and they should include audit rights for all subcontractors. Ask vendors about their processes for evaluating subcontractor security measures, compliance certifications, and incident histories. Additionally, include clauses that require subcontractors to participate in annual disaster recovery and incident response drills, complete with well-defined escalation procedures [3].
Long-term risk management goes beyond cybersecurity. Financial and operational stability are just as critical. Request three years of financial statements and inquire about any major liabilities or ongoing litigation [4]. Evaluate whether the vendor can scale with your organization's growth without disrupting services. A key question to consider is: "If we suddenly lost this vendor, how significantly would our operations be affected?" [5]. For essential services, contracts should include detailed exit strategies, specifying data export formats, support commitments, and clear timelines.
Incorporate vendors and their subcontractors into your business continuity and disaster recovery plans. This ensures a unified approach to risk management across all levels. Vendors supporting critical clinical operations or IT systems should participate in incident response drills and provide documented commitments for Recovery Time Objectives (RTO) and Recovery Point Objectives (RPO) [3]. By treating vendors as integral parts of your infrastructure, you can ensure they are equipped to maintain operations during disruptions.
Tools like Censinet RiskOps™ simplify vendor evaluations by standardizing questionnaires, mapping vendor-subcontractor relationships, and identifying downstream risks. Its AI-driven features capture fourth-party risk exposures and route findings to the appropriate stakeholders, creating a centralized system for managing extended supply chain risks.
Conclusion
These five questions form the backbone of effective vendor risk assessments by addressing critical vulnerabilities. They focus on how vendors manage protected health information, their cybersecurity measures, adherence to regulatory standards, readiness to respond to incidents, and their approach to subcontractor oversight and long-term operational risks. By tackling these areas, healthcare organizations can strengthen patient safety, safeguard sensitive data, and maintain smooth clinical operations.
The healthcare industry’s complexity calls for risk management strategies that are specifically designed to meet its unique challenges. These essential questions support a proactive approach to risk management, helping organizations achieve tangible improvements in their operations.
In practice, streamlined risk assessments have shown to boost efficiency while reducing the strain on resources. Shifting from reactive processes, like chasing down questionnaires, to a proactive risk management model allows organizations to catch potential issues early - before they evolve into security breaches or disrupt operations.
Incorporating these questions at key stages - vendor onboarding, contract renewals, and regular monitoring - can make a significant difference. For instance, high-risk vendors might need comprehensive security reviews every quarter, while medium-risk vendors could undergo shorter evaluations twice a year. Tools like Censinet RiskOps™ make it easier to embed these critical questions into the vendor lifecycle, offering centralized and scalable solutions tailored to healthcare’s stringent regulatory and operational demands.
FAQs
What certifications should a vendor have to demonstrate compliance with HIPAA standards?
When evaluating compliance with HIPAA standards, it's essential to check for certifications that reflect robust security measures. Some of the most relevant certifications include HITRUST CSF, which aligns closely with HIPAA guidelines, as well as frameworks like SOC 2, SSAE 18, and ISO 27001. These certifications signal that the vendor employs stringent protocols to safeguard sensitive data, including patient details and Protected Health Information (PHI).
What steps can healthcare organizations take to ensure a vendor’s incident response plan is effective?
Healthcare organizations can evaluate how effective a vendor’s incident response plan is by taking a close look at their documented procedures. These should align with established industry standards to ensure the vendor is prepared for potential threats. One practical way to test this is by conducting tabletop exercises or simulated incident drills. These activities can reveal how well the vendor’s team handles various scenarios.
Another key step is reviewing the vendor’s track record. Audits and post-incident reports can shed light on their ability to manage and resolve security incidents effectively. Consistent testing and validation of the response plan are also crucial. This ensures the plan is ready to protect sensitive data, like patient information and PHI, under real-world conditions.
How can healthcare organizations evaluate a vendor's subcontractor management and long-term risk strategy?
To properly assess a vendor's approach to managing subcontractors and mitigating long-term risks, healthcare organizations should focus on a few key areas:
- Evaluate the vendor’s oversight of subcontractors: Look into how the vendor monitors subcontractors, particularly their cybersecurity practices and adherence to industry standards. This can reveal how seriously they take security and compliance.
- Scrutinize contractual agreements: Ensure that subcontractors are held to the same security protocols as the primary vendor. This alignment is critical to maintaining consistent security measures across all parties.
- Review ongoing risk management practices: Check for mechanisms like regular audits, performance reviews, and systems for reporting incidents. These efforts demonstrate a proactive approach to identifying and managing potential risks.
By integrating these steps into a larger risk management strategy, organizations can establish stronger, more secure relationships with vendors and their subcontractors.


