Why Access Control Matters for PHI Encryption
Post Summary
Encryption is not enough to protect sensitive health data. Without strict access controls, encrypted Protected Health Information (PHI) can still be exploited.
Here’s why access control is essential:
- Encryption keys must be safeguarded to prevent unauthorized decryption.
- Weak access controls - like shared logins or lack of session timeouts - create security gaps.
- HIPAA regulations require unique user identification and restrict access to authorized individuals only.
- Combining Role-Based Access Control (RBAC) and Multi-Factor Authentication (MFA) enhances security while ensuring compliance.
- Proper key management reduces risks, protects credentials, and minimizes breach notification requirements.
Encryption works best when paired with strong access controls. Together, they protect sensitive data, prevent insider threats, and maintain compliance with HIPAA standards.
HIPAA Security Rule – Safeguarding Electronic PHI (ePHI)
Risks of Weak Access Control in PHI Encryption
Access Control Weaknesses and Their Impact on PHI Encryption Security
Unauthorized Key Access and Insider Threats
When access controls are weak, encrypted PHI becomes vulnerable to insider threats. Without assigning unique user IDs, it's impossible to trace who accessed or decrypted sensitive information. This lack of traceability renders audit logs useless during forensic investigations.
The problem worsens when key management and data administration are handled by the same individual. If a single administrator has control over both, they could decrypt PHI without leaving a trace, creating a significant security blind spot.
Another critical issue is the absence of automatic logoff. Without session timeouts, an unattended workstation with an active session leaves the door wide open for unauthorized access. This risk extends to mobile devices if they lack automatic locking features.
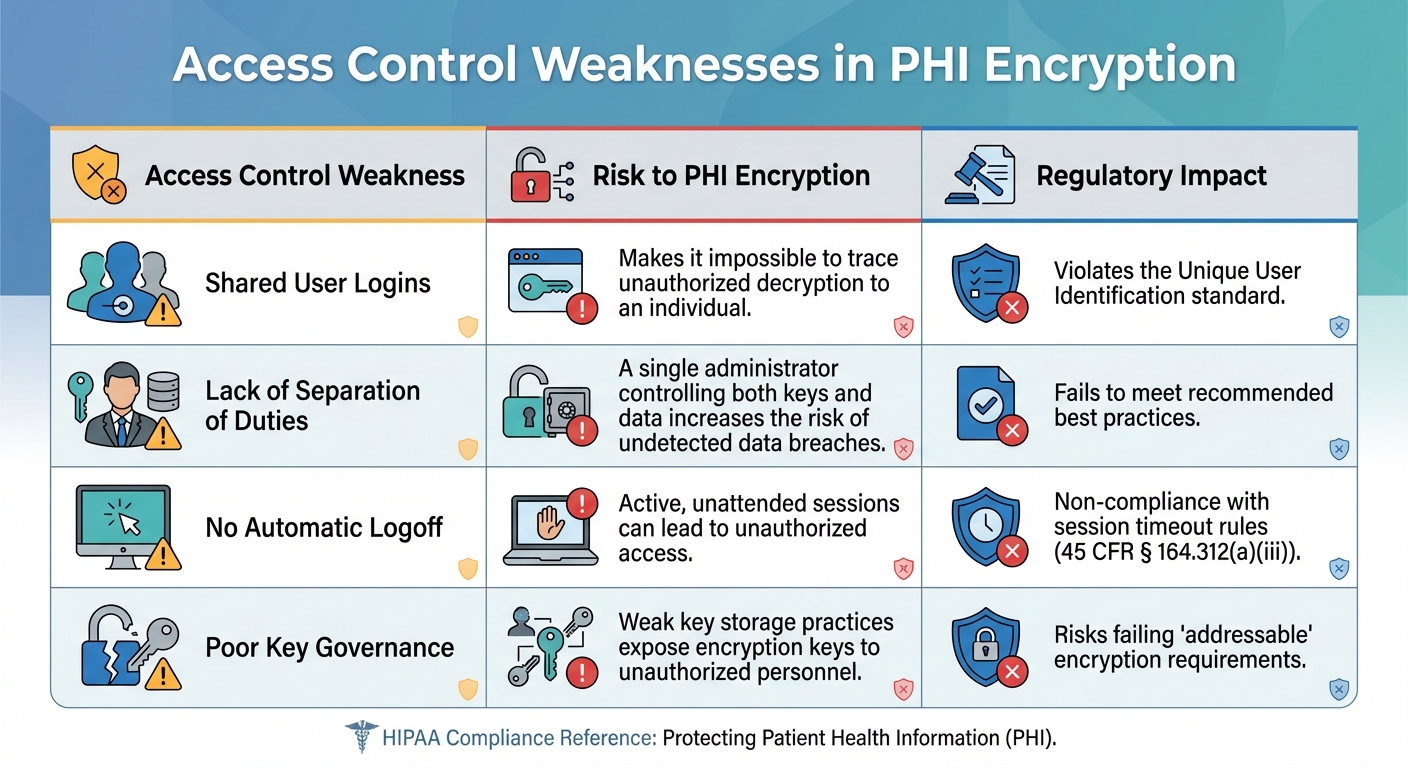
| Access Control Weakness | Risk to PHI Encryption | Regulatory Impact |
|---|---|---|
| Shared User Logins | Makes it impossible to trace unauthorized decryption to an individual. | Violates the Unique User Identification standard. |
| Lack of Separation of Duties | A single administrator controlling both keys and data increases the risk of undetected data breaches. | Fails to meet recommended best practices. |
| No Automatic Logoff | Active, unattended sessions can lead to unauthorized access. | Non-compliance with session timeout rules (e.g., 45 CFR § 164.312(a)(iii)). |
| Poor Key Governance | Weak key storage practices expose encryption keys to unauthorized personnel. | Risks failing "addressable" encryption requirements. |
These vulnerabilities don’t just expose PHI - they also pave the way for regulatory trouble. Internal security lapses like these can lead to serious compliance issues and penalties.
Regulatory and Compliance Consequences
Weak access controls don’t just increase internal risks - they also violate HIPAA’s technical safeguard requirements. Under 45 CFR § 164.312, HIPAA mandates that access to encrypted data is restricted to authorized individuals or software programs. A key part of this is ensuring unique user identification, which is a required implementation specification.
If encrypted ePHI is accessed by an unauthorized party and isn’t rendered unusable, unreadable, or undecipherable, a breach may need to be reported. Such incidents can lead to costly individual notifications, credit monitoring expenses, and civil monetary penalties. As Steve Alder, Editor-in-Chief of The HIPAA Journal, explains:
The purpose of the requirement is to ensure ePHI is unreadable, undecipherable, and unusable to any person or software program that has not been granted access rights.
Beyond fines and notifications, weak access controls can create opportunities for hackers to move laterally within a network. Once inside, attackers can exploit unprotected systems to reach healthcare databases. Without strong authentication methods or secure transmission protocols, even encryption keys can be intercepted during transit, completely undermining the encryption system.
How Access Control Strengthens PHI Encryption
Role-Based Access Control (RBAC) and Unique User IDs
Role-Based Access Control (RBAC) takes encryption beyond being a passive defense mechanism and turns it into an active security tool. By aligning access permissions with specific roles - like nurse, billing clerk, or database administrator - RBAC ensures that individuals can only access the encryption keys and protected health information (PHI) necessary for their job. This minimizes unnecessary exposure and reduces risk.
A key part of RBAC is unique user identification. Every time someone decrypts data or accesses an encryption key, their activity is logged and tied to their individual account. This creates a precise audit trail. For instance, if 500 patient records are decrypted at 2:00 AM, you'll know exactly who was responsible and when it happened.
Another critical element is separation of duties. Encryption keys should be stored in a centralized Key Management System (KMS) or Hardware Security Module (HSM), ensuring that data administrators don’t have direct access to the keys. As Kevin Henry, a HIPAA Specialist at Accountable, explains:
Treat keys as the crown jewels and separate their management from data owners [1].
This separation ensures no single person has unchecked access to both the encrypted data and the keys that unlock it. Modular permission settings reinforce this by limiting access and maintaining the principle of least privilege. For added security, some healthcare systems require additional approvals when queries return over 500 records [4], creating an extra layer of defense against large-scale data extractions.
On top of these measures, multi-factor authentication (MFA) provides even stronger protection for encryption keys.
Multi-Factor Authentication for Key Access
Multi-factor authentication (MFA) strengthens security by requiring users to verify their identity using multiple methods: something they know (like a password), something they have (such as a token or app), and something they are (biometric data). This is particularly crucial for users managing key generation, rotation, and access.
With MFA in place, stolen passwords alone are not enough to compromise security. Even if an attacker obtains a user’s credentials through phishing or other methods, they still need the second authentication factor to gain access. This significantly limits the potential damage and deters unauthorized activity.
However, not all MFA methods are equally secure. SMS-based MFA can be vulnerable to SIM-swapping attacks. For high-risk scenarios, it’s better to use phishing-resistant options like FIDO2 or hardware security keys. These hardware-backed solutions ensure that even sophisticated social engineering attempts can’t breach key access.
MFA also plays a role in emergency scenarios. For example, during a medical emergency, a physician might need immediate access to a patient’s encrypted records. MFA can facilitate "break-glass" procedures, temporarily elevating permissions while maintaining accountability through detailed audit logs [1]. This balance between urgent access and security ensures compliance with HIPAA while safeguarding sensitive data.
Alignment with HIPAA Security Rule
These access control measures align directly with the requirements of the HIPAA Security Rule (45 CFR § 164.312). Under this rule, unique user identification is mandatory, not optional. Organizations must track and identify exactly who is accessing electronic PHI (ePHI) and encryption keys.
While encryption itself is classified as an "addressable" specification under HIPAA, it’s expected that organizations assess its feasibility for their specific environment. When encryption is implemented, access controls ensure it functions effectively and securely.
There’s also a regulatory advantage. If ePHI is encrypted following the Department of Health and Human Services (HHS) standards and encryption keys are properly secured, a data loss may not qualify as a reportable breach under the Breach Notification Rule [2][6]. This "safe harbor" provision can save healthcare organizations from the financial and reputational costs of breach notifications, credit monitoring for affected individuals, and potential fines.
Together, encryption and access controls fulfill HIPAA’s "minimum necessary" standard, addressing the requirement to guard against "reasonably anticipated threats" [5][2]. These safeguards not only protect patient data but also ensure compliance with federal regulations, offering peace of mind for both organizations and patients alike.
sbb-itb-535baee
Key Management Best Practices with Access Control
Decentralized Role-Based Controls and Audit Trails
Strengthening PHI encryption starts with implementing strict access control measures. A key step is decentralizing key management by dividing key-related tasks among different roles. Assigning responsibilities like key generation, rotation, and use to separate teams creates a dual control system that reduces the risk of a single point of failure [3].
Using a Key Management System (KMS) or Hardware Security Module (HSM) ensures that key operations remain independent from data administration. This separation means database administrators managing patient records won’t have direct access to the encryption keys safeguarding that data [1][3]. Keys should be treated as the system’s most critical assets, with their management kept entirely separate from data owners.
To enforce this separation, audit trails are indispensable. Every key access should be logged with details like the user ID, action performed, dataset involved, and timestamp. These logs must be stored in an immutable, tamper-proof repository, creating a transparent and permanent record of all activity [1][3]. For instance, if someone decrypts 300 patient records late at night, the system will pinpoint exactly who did it, enabling immediate investigation.
Integrating key access with HR systems adds another layer of security. When an employee changes roles or leaves the organization, their decryption privileges should be automatically revoked. This automation eliminates the risk of lingering access rights, which could otherwise be exploited [1][3].
Automatic Logoff and Session Expiration
Beyond key management, robust session controls are essential for minimizing unauthorized access. In healthcare settings, unattended workstations present a serious vulnerability. Imagine a nurse stepping away from a terminal during an emergency, leaving decrypted PHI visible on the screen. Without automatic logoff, sensitive information could be exposed to anyone nearby.
To address this, implement short-lived, encrypted session tokens and device-level timeouts that automatically log off unattended workstations [2]. This strategy limits the time attackers have to exploit stolen tokens. Even if a token is intercepted, it becomes useless within minutes. HIPAA expert Kevin Henry emphasizes:
Use short‑lived, encrypted session tokens with secure settings and automatic logoff to reduce hijacking risk. Pair this with device timeouts so unattended terminals cannot be misused [2].
In urgent "break-glass" situations, where immediate access to encrypted records is critical, session controls should tighten further. Elevated-permission sessions used in emergencies should expire immediately after the task is completed and require a mandatory audit review [1][2]. This ensures patient care needs are met without compromising accountability.
Comparison of Access Control Methods
Not all access control systems provide the same level of security for PHI encryption. Role-Based Access Control (RBAC) and Discretionary Access Control (DAC) differ significantly in their ability to protect sensitive data:
| Feature | Role-Based Access Control (RBAC) | Discretionary Access Control (DAC) |
|---|---|---|
| HIPAA Compliance | High; enforces the "minimum necessary" standard. | Low; relies on individual user discretion. |
| Scalability | High; permissions are assigned by role, not individual users. | Low; managing access becomes chaotic as user numbers grow. |
| Effectiveness for PHI | Strong; applies consistent, policy-driven safeguards. | Weak; vulnerable to unauthorized sharing and "privilege creep." |
| Management | Centralized by administrators. | Decentralized; left to data owners. |
RBAC aligns permissions with specific clinical and administrative roles, ensuring users only access the data and keys necessary for their responsibilities [3]. This approach prevents the gradual accumulation of excessive access rights, a common flaw in DAC systems. Additionally, RBAC’s scalability makes it a practical solution for healthcare environments with large and diverse teams.
These practices set the stage for exploring more advanced security measures in the next section.
Implementing Solutions Using Censinet RiskOps™

Automated Workflows for Access Control and Risk Management
Censinet RiskOps™ simplifies encryption key management with automated workflows that handle role-based access provisioning and real-time policy enforcement. By streamlining approval processes, the platform ensures that decryption keys are shared exclusively with authorized personnel. It also maintains detailed and unchangeable audit logs to meet HIPAA requirements [8].
Healthcare organizations using this system have seen manual errors drop by as much as 70%. For instance, a mid-sized health delivery organization managing 500,000 patient records reduced access provisioning time by 80% thanks to automated workflows [8]. The platform also manages the entire lifecycle of encryption keys - from creation and rotation to revocation - using pre-designed RBAC templates tailored for healthcare needs. This has cut governance timelines from weeks to just hours [8].
AI-Driven Risk Assessments for PHI Security
Censinet RiskOps™ employs AI to continuously monitor encryption configurations and detect vulnerabilities, such as weak keys, through machine learning models trained on healthcare breach data [8]. Analytics from the platform show a 40–60% improvement in risk detection accuracy. Impressively, AI identifies 95% of insider threats before they escalate into breaches, while also reducing compliance audit preparation time by 50% [8].
The platform’s Censinet TPRM AI™ feature further enhances security by summarizing critical network access and IT integration details, including Multi-Factor Authentication (MFA) and Single Sign-On (SSO) setups. When gaps are identified, the system generates corrective action plans and consolidates findings in a Risk Register. These issues are then routed to the appropriate internal experts, with the platform tracking remediation progress. This AI-driven functionality works alongside scalable access governance to ensure robust PHI protection across all layers of operation.
Scalable Access Governance for Healthcare Delivery Organizations
Censinet RiskOps™ extends its capabilities with scalable governance tools that protect PHI for large user bases through federated RBAC and centralized key management [8]. For example, a 10-hospital system can implement the platform in just 4–6 weeks, achieving a 65% reduction in breach risks [8]. Risk assessments, which previously took weeks, can now be completed in under 10 days. Censinet TPRM AI™ accelerates this process, delivering an 80%+ reduction in assessment time and increasing productivity by over 400% [7].
The platform also provides automated alerts for breaches or ransomware incidents involving third-party vendors. These alerts enable quick action if cryptographic keys or access credentials are compromised. Pre-built assessments aligned with the HIPAA Security Rule and NIST Cybersecurity Framework further simplify the enforcement of encryption and access management standards for PHI [7].
Conclusion
Strong access control is the backbone of protecting PHI (Protected Health Information). While encryption is a powerful tool, its effectiveness depends entirely on how well access to the decryption keys is managed. Without strict controls, even the best encryption can be compromised. As Kevin Henry, a HIPAA Specialist, puts it:
Disciplined access policies and robust monitoring safeguard PHI and support efficient care [3].
Key measures like Role-Based Access Control (RBAC), Multi-Factor Authentication (MFA), and automated provisioning are critical in limiting access and preventing privilege creep. These tools not only protect sensitive data but also create detailed audit trails that align with HIPAA requirements, addressing both external breaches and insider risks.
By combining these access controls with encryption strategies, healthcare organizations can achieve stronger data protection and better manage risks. Tools like Censinet RiskOps™ further enhance these efforts, offering platforms that streamline and strengthen security practices.
When implemented effectively, access control transforms encryption from a static defense into a dynamic system that adapts to new threats, ensuring both regulatory compliance and robust protection for patient data.
FAQs
Why is access control important even if PHI is encrypted?
Access control plays a key role in safeguarding Protected Health Information (PHI), even when encryption is in place. While encryption makes data unreadable to unauthorized users, access control ensures that only the right people or systems can decrypt and use that data. Without proper access control, encrypted data is still at risk if unauthorized individuals manage to obtain decryption keys or access systems.
By restricting access to PHI to only those who truly need it, organizations can better protect patient privacy, reduce the risk of breaches, and meet compliance requirements like those outlined in HIPAA. Using measures like role-based permissions, multi-factor authentication, and routine access reviews helps strengthen security and ensures compliance with these regulations.
How does Role-Based Access Control (RBAC) improve the security of Protected Health Information (PHI)?
Role-Based Access Control (RBAC) strengthens the security of Protected Health Information (PHI) by restricting access to sensitive patient data based on an individual’s job responsibilities. This means only authorized personnel - like doctors, nurses, or administrative staff - can access the specific information they need to perform their tasks. By doing so, RBAC reduces the chances of unauthorized access or accidental exposure of sensitive data.
One of RBAC’s key features is enforcing the principle of least privilege. This approach ensures that users only have access to the minimum amount of data necessary for their role, which helps mitigate risks like credential theft and limits the potential damage of a data breach. Additionally, RBAC makes it easier for healthcare organizations to comply with regulations like HIPAA by providing a structured way to manage permissions, track user activity, and align access with clinical workflows.
To further enhance security, it’s important to regularly review role definitions and automate access management. These practices not only bolster data protection but also streamline operations, making it easier to maintain both security and efficiency.
What risks does weak access control pose to HIPAA compliance?
Weak access controls pose significant risks for healthcare organizations, especially when it comes to HIPAA compliance. Without the right protections in place, electronic protected health information (ePHI) could fall into the wrong hands, opening the door to data breaches. These breaches don't just carry the potential for financial penalties exceeding $10 million per incident - they can also tarnish an organization's reputation and erode the trust of its patients.
On top of that, failing to implement access controls like unique user IDs or emergency access protocols can lead to violations of HIPAA’s Security Rule. This could result in regulatory sanctions, mandatory corrective action plans, and difficulties in tracking or auditing PHI access. To safeguard patient information and remain compliant, healthcare organizations need to adopt role-based access controls and maintain constant monitoring to detect any unauthorized activity.


