Zero-Day AI: Using Machine Learning to Catch Unknown Cyber Threats
Post Summary
Zero-day threats are cybersecurity attacks targeting vulnerabilities that are unknown to software developers and security teams. These threats are especially dangerous in healthcare, where sensitive patient data and critical systems are at risk. Machine learning (ML) is transforming how organizations detect and respond to these threats by identifying unusual patterns, analyzing behaviors, and predicting potential vulnerabilities before they are exploited.
Key takeaways:
- Zero-day threats exploit undiscovered flaws, making them hard to detect with traditional tools.
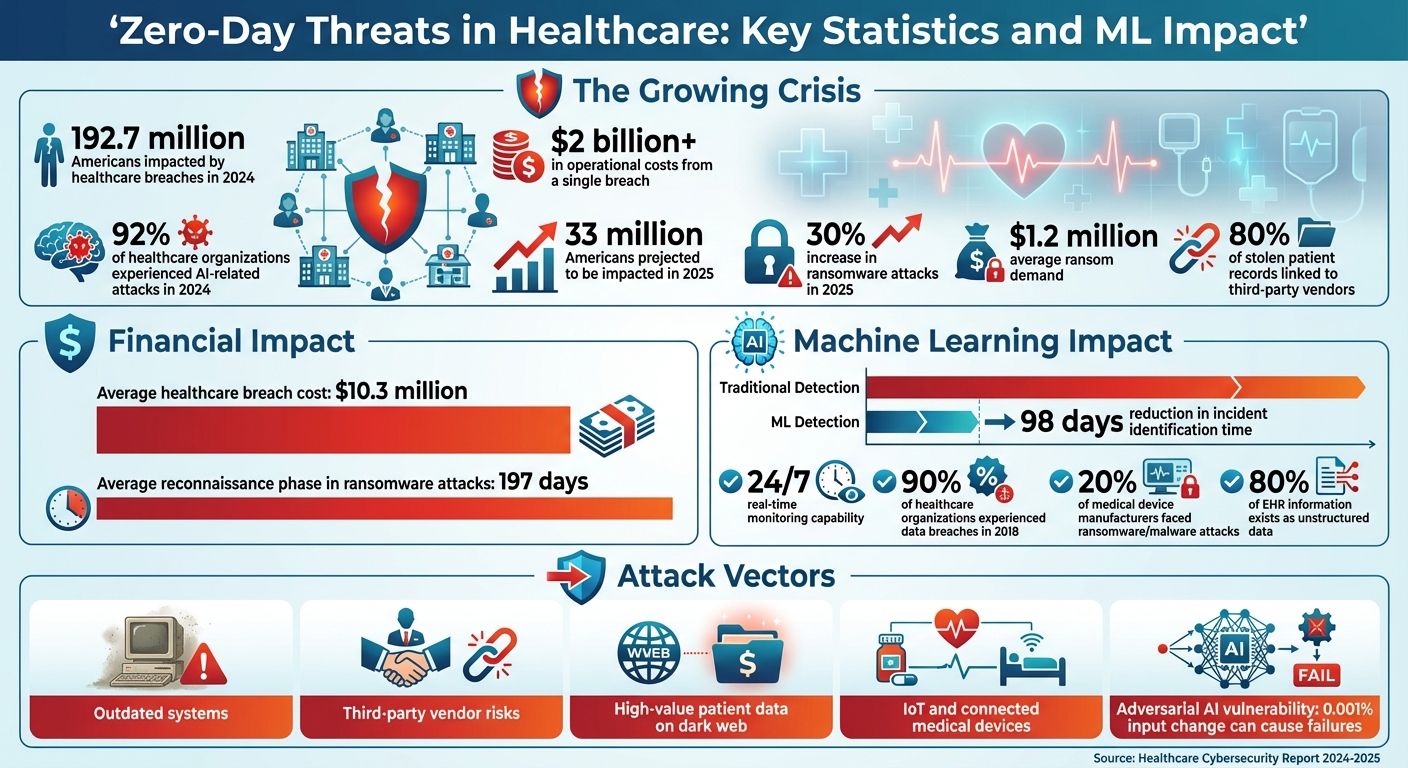
- In 2024, a healthcare breach impacted 192.7 million Americans, halting operations and costing over $2 billion.
- Healthcare is particularly vulnerable due to outdated systems, third-party vendor risks, and the high value of patient data on the dark web.
- Machine learning tools offer real-time detection, anomaly monitoring, and predictive threat modeling to reduce detection time by up to 98 days.
- AI-driven platforms like Censinet RiskOps™ streamline risk assessments, automate responses, and help secure healthcare ecosystems.
Zero-Day Threats in Healthcare: Key Statistics and ML Impact 2024-2025
How Machine Learning Detects Zero-Day Threats
Machine learning is revolutionizing the way healthcare organizations defend against zero-day threats. Unlike traditional security tools that depend on predefined rules or known threat signatures, AI-powered systems continuously learn and adapt to new threats - even without prior knowledge of specific attack patterns [4]. This ability is particularly critical in the healthcare sector, where sensitive data and patient safety are at stake.
By processing vast amounts of data in real time, machine learning enables near-instant decisions. For example, AI-driven threat detection systems have been shown to reduce the time needed to identify incidents by up to 98 days [2]. This speed and adaptability highlight the transformative role of machine learning in healthcare cybersecurity.
Here’s a closer look at three key machine learning techniques used to detect zero-day threats in real time.
Anomaly Detection for Unusual Activity
Anomaly detection is a cornerstone of AI-driven zero-day threat defense. These systems analyze system logs, user behaviors, and network traffic to establish a baseline of normal activity [4]. By continuously learning and adapting, they can detect even subtle deviations from the norm - potentially signaling a zero-day exploit - without relying on predefined signatures [4].
Unsupervised learning models play a major role here. They group similar events into clusters, allowing outliers to stand out. This makes it possible to uncover novel attack methods before specific threat signatures are developed [5]. In healthcare, this technique is particularly effective for monitoring device behavior across thousands of IoT and operational technology devices, flagging unusual activity that could indicate a compromise or insider threat [3].
"AI is a perfect match for ingesting [internet of things] IoT data, as the devices generate such huge amounts of data that we couldn't access before, or we couldn't access in real time."
- Tapan Mehta, Healthcare and Pharma Life Sciences Executive, Strategy and GTM [3]
These methods have proven effective across the industry. Behavioral analytics powered by AI and machine learning has successfully identified deviations in system and user behavior that hint at zero-day exploits. For healthcare organizations, this means better protection of sensitive patient data from ransomware attacks exploiting zero-day vulnerabilities [1][3].
The scalability of these systems is a game-changer. As Tapan Mehta explains, "AI is really, really good at scaling up a solution to these billions of IoT devices, which is very hard for a human being to do" [3].
Behavioral Analysis for Threat Profiling
Building on anomaly detection, behavioral analysis digs deeper into profiling threats. This technique uses machine learning to study patterns in user and entity behavior across networks, applications, and digital environments [6]. For zero-day threats, it identifies sophisticated attacks by spotting anomalies that deviate from established behavioral norms [7].
In healthcare, these systems continuously monitor users, devices, and systems - including connected medical and IoT devices - to detect incidents such as insider threats early on [8]. User and Entity Behavior Analytics (UEBA) provides real-time insights by analyzing streaming data, identifying deviations from expected behavior, and flagging potential threats [6][7].
The importance of behavioral analysis is underscored by alarming statistics: nearly 90% of healthcare organizations experienced data breaches in 2018, and at least 20% of medical device manufacturers faced ransomware or malware attacks over a 20-month period [8]. With nearly 80% of electronic health record information existing as unstructured data, advanced tools like natural language processing are essential for analyzing these massive data sets effectively [9].
Predictive Modeling for Threat Forecasting
Predictive modeling takes cybersecurity a step further by shifting the focus from reacting to threats to anticipating them. This approach uses machine learning to forecast potential vulnerabilities and risks before attackers can exploit them [5]. Predictive analytics evaluates external threat feeds, open-source intelligence, and even insights from the dark web to identify emerging risks [5]. By clustering indicators of compromise (IOCs) and predicting attack vectors, these systems enable organizations to proactively strengthen defenses [5].
In healthcare, predictive modeling helps prioritize patching and remediation efforts by assessing which vulnerabilities pose the highest risks in a specific context [3]. These systems can also automate responses, such as isolating compromised systems or blocking suspicious IP addresses. Looking ahead, advancements in generative AI and multi-agent systems are expected to further enhance predictive capabilities by simulating attack scenarios and generating synthetic threat data to bolster defenses [5].
"Security needs to be automated and real-time in the era of AI. As we face new challenges and zero-day threats, we need to innovate new solutions at a much faster pace. And that's also where the opportunities will come to improve quality of care and access to care."
- Tapan Mehta, Healthcare and Pharma Life Sciences Executive, Strategy and GTM [3]
Using Censinet RiskOps™ for Zero-Day Defense

Censinet RiskOps™ leverages the power of AI to detect zero-day threats and turn those insights into actionable security measures. By identifying threats in real time, the platform ensures these insights lead to immediate and effective responses. It combines AI-driven automation with tools tailored for healthcare environments, enabling faster risk assessments, real-time monitoring of emerging threats, and a careful balance between automated processes and expert judgment. This seamless integration bridges the gap between identifying risks and taking meaningful action to mitigate them.
Automating Risk Assessments with Censinet AITM
Censinet AITM simplifies third-party risk assessments, allowing vendors to complete security questionnaires in a matter of seconds. The system automatically summarizes evidence, highlights critical integration details, and captures key information about product connections and fourth-party risks. It then generates detailed risk reports without requiring manual effort.
By shortening assessment timelines, the platform efficiently identifies vulnerabilities, validates evidence, drafts policies, and provides risk mitigation recommendations. Importantly, this process still includes human oversight to ensure accuracy and reliability.
Real-Time Risk Visualization with Censinet Connect™
Censinet Connect™ serves as a central hub for visualizing risks across the healthcare ecosystem. It consolidates real-time data from third-party vendors, internal systems, and ongoing assessments into a single, easy-to-navigate dashboard. This unified view enables security teams to track new threats, evaluate vendor security, and respond quickly to vulnerabilities as they arise.
The platform’s routing feature operates like air traffic control, ensuring that critical information reaches the right teams without delay. For instance, if a vendor is exposed to a newly discovered zero-day exploit, the system immediately assigns the necessary tasks to the appropriate stakeholders for review and action. This ensures swift and targeted responses to emerging threats.
Balancing Automation and Human Oversight
Automation boosts the speed and efficiency of risk management, but human expertise remains a vital component. Censinet RiskOps™ incorporates a "human-in-the-loop" approach, allowing analysts to validate AI-generated insights and refine system outputs. This collaboration enables risk teams to review AI decisions, flag potential errors, and provide feedback for system improvement. The partnership between data scientists and security professionals ensures that automation supports, rather than replaces, critical decision-making [10][4].
Together, the tools within Censinet RiskOps™ transform zero-day threat detection into coordinated, immediate action, strengthening defenses across the healthcare landscape.
Case Studies: AI Success in Mitigating Zero-Day Threats
Artificial intelligence is proving to be a game-changer in combating zero-day threats, especially in industries like healthcare, where timing and precision can make or break an organization’s ability to contain a breach. With the rise in cyberattacks and ransomware incidents, AI-driven detection tools are not just helpful - they’re becoming indispensable. Let’s dive into a few examples of how these tools are reshaping threat mitigation across different scenarios.
Blocking AI-Enhanced Phishing and Ransomware
AI-powered tools are uncovering threats that traditional defenses often miss. By using Natural Language Processing (NLP) and Computer Vision (CV), these systems can spot phishing attempts through subtle clues like grammatical errors, odd requests, unusual sending behaviors, fake logos, altered images, and suspicious email layouts. Deep learning goes a step further by identifying zero-day attacks and polymorphic malware - threats specifically designed to bypass conventional defenses.
These systems don’t sleep. They provide 24/7 monitoring across network logs, endpoints, and cloud environments, and they spring into action when anomalies are detected. Automated responses include isolating compromised devices, quarantining suspicious files, or blocking harmful IP addresses, ensuring swift containment of potential threats.
"Security needs to be automated and real-time in the era of AI. As we face new challenges and zero-day threats, we need to innovate new solutions at a much faster pace. And that's also where the opportunities will come to improve quality of care and access to care."
- Tapan Mehta, Healthcare and Pharma Life Sciences Executive, Strategy and GTM [3]
The impact of these systems is staggering. AI-powered threat detection can reduce the time it takes to identify incidents by 98 days [2]. Considering the average cost of a healthcare breach sits at $10.3 million [2], this kind of efficiency is a game-changer.
Reducing Risk Assessment Timelines
Traditional risk assessments can drag on for weeks - or even months - leaving organizations vulnerable while evaluations creep along. Attackers often exploit these delays, as seen in modern healthcare ransomware attacks, where reconnaissance phases can last an average of 197 days [2].
Enter Censinet AITM™, which slashes these timelines dramatically. Instead of weeks, vendors can complete security questionnaires in seconds. The platform automatically compiles evidence, flags critical integration details, identifies fourth-party risks, and generates detailed risk reports - all without manual intervention. This streamlined process complements real-time AI anomaly detection, ensuring healthcare organizations stay one step ahead of emerging threats.
Beyond assessments, the platform uses behavioral modeling to create unique profiles for individual users. By monitoring for unusual behaviors - like unexpected file downloads or irregular access patterns - it establishes a dynamic baseline of normal activity and flags deviations in real time [4]. This constant vigilance ensures threats are addressed before they escalate.
Collaborative Risk Management Success Stories
For healthcare organizations, the security risks tied to third-party vendors are a growing concern. Extending the security perimeter to include these external partners is no longer optional - it’s essential.
Censinet Connect™ steps in as a collaborative solution, acting as a central hub where healthcare providers and their vendors work together to address supply chain vulnerabilities. If a vendor discovers a zero-day exploit, the platform’s routing feature ensures that tasks are immediately assigned to the right stakeholders for review and action. This kind of coordination prevents critical information from falling through the cracks, ensuring vulnerabilities are dealt with swiftly rather than lingering in the system.
sbb-itb-535baee
Overcoming Challenges in AI-Driven Zero-Day Defense
AI-powered threat detection systems are undeniably powerful, but they come with their own set of challenges. For instance, a staggering 92% of healthcare organizations reported experiencing AI-related attacks in 2024 [2]. This alarming figure highlights the potential risks to patient safety and underscores the need to carefully weigh the benefits and limitations of machine learning in zero-day defense.
Advantages and Disadvantages of Machine Learning
Machine learning offers tremendous potential for zero-day threat defense, but it's not without its drawbacks. A clear understanding of both its strengths and weaknesses is crucial for healthcare organizations looking to implement these systems effectively.
| Advantages | Disadvantages |
|---|---|
| Real-time detection across networks, endpoints, and cloud environments around the clock | False positives can overwhelm security teams, leading to alert fatigue and overlooked genuine threats [4][5] |
| Scalability to process vast amounts of data without requiring additional staff | False negatives may fail to detect novel attacks, posing a serious risk in healthcare [4][3] |
| Faster response times, reducing incident identification by an average of 98 days [2] | Black box algorithms lack transparency, making it hard to understand how decisions are made [3] |
| Adaptive learning that evolves to counter emerging threats | Adversarial vulnerability, where even minor input changes (as small as 0.001%) can cause significant failures [2] |
| Cost savings in breach containment, with healthcare breaches costing an average of $10.3 million [2] | High implementation costs and a shortage of skilled IT professionals in healthcare |
The lack of transparency in machine learning models also creates compliance challenges, particularly with regulations like HIPAA. Addressing these hurdles requires a strategic approach to improve AI performance in zero-day defense.
Strategies for Mitigating Challenges
To navigate the limitations of AI-driven systems while maintaining strong defenses, healthcare organizations need to adopt targeted strategies.
Continuous model training is one of the most effective methods. AI systems must be constantly updated through feedback loops, where security teams validate and refine threat detections. This process helps reduce both false positives and false negatives, ensuring the system adapts to the ever-changing landscape of healthcare threats.
Human oversight is critical. While AI can handle vast amounts of data, it cannot replace the contextual understanding and judgment of experienced security professionals. By working together, AI and human experts can fine-tune detection thresholds, investigate ambiguous alerts, and make informed decisions that align with clinical workflows and patient care priorities. For example, platforms like Censinet balance automation with human review, flagging potential risks while leaving critical decisions to the appropriate stakeholders.
Data quality management is another key area to address. AI models trained on biased or incomplete datasets can carry these flaws into their threat detection processes. Healthcare organizations should implement robust data governance practices to ensure training datasets are diverse and representative of real-world attack scenarios, system configurations, and operational patterns. Regular audits of model performance can identify and correct biases, preventing them from undermining security efforts.
Best Practices for Scalable Zero-Day Defense in Healthcare
Building a scalable zero-day defense means integrating AI into a security framework that tackles regulatory demands, vendor risks, and patient safety. With a staggering 33 million Americans projected to be impacted by healthcare data breaches in 2025 and 80% of stolen patient records linked to third-party vendors [2], a well-thought-out, AI-driven defense strategy becomes non-negotiable. Here’s how healthcare organizations can align with industry standards and strengthen their defenses.
Aligning with Industry Frameworks
The updated HIPAA Security Rule now mandates multi-factor authentication (MFA), encryption, and enforces Business Associate Agreements (BAAs) with stricter technical controls and timelines [2]. To complement these requirements, healthcare organizations should adopt NIST frameworks, which provide structured guidance on implementing Zero Trust principles, continuous monitoring, and risk-based controls. However, current regulations like FDA and HIPAA still fall short in addressing AI-specific security assessments, ongoing monitoring, and incident response [2].
Testing the resilience of AI models is critical to ensure they can withstand adversarial conditions. Even slight input manipulations can lead to significant errors, making robustness testing essential. Organizations should also implement data provenance and integrity controls in AI training pipelines. This includes cryptographic verification of data sources, maintaining detailed audit trails, and isolating environments to prevent poisoning attacks [2]. These steps help create a proactive defense against emerging threats.
Using Censinet One™ for Vendor Benchmarking
Third-party vendors are a major weak spot in healthcare cybersecurity. Tools like Censinet One™ are designed to evaluate vendor security postures effectively. Its benchmarking capabilities allow organizations to assess vendor security controls against industry standards, identifying vulnerabilities before they can be exploited by zero-day threats.
Censinet RiskOps™ simplifies vendor risk management with automated workflows and real-time risk visualization. This system enables healthcare organizations to monitor vendor risks across their ecosystem and prioritize remediation efforts based on their potential impact on patient data and care. Given the new HIPAA Security Rule requirements, organizations must promptly update their BAAs to address non-compliance issues with vendors [2].
Censinet AI™ further accelerates third-party risk assessments by automating security questionnaires, summarizing evidence, and capturing key integration details, including fourth-party risks. This automation speeds up the assessment process while still allowing for critical human oversight in complex decision-making scenarios.
While vendor benchmarking strengthens external risk management, maintaining HIPAA compliance is vital for safeguarding internal operations and ensuring patient safety.
Ensuring HIPAA Compliance and Patient Safety
Striking the right balance between cybersecurity, compliance, and patient care is a challenge, especially in an AI-driven zero-day defense strategy. Healthcare organizations must adopt innovative security measures while navigating complex regulations like HIPAA and GDPR.
The "black box" nature of some AI algorithms presents unique risks in healthcare, where decisions can directly impact patient outcomes. Transparency and explainability are crucial - AI solutions with Explainable AI (XAI) capabilities can help clarify how decisions are made, building trust and supporting compliance audits.
Strong data governance is equally important. AI systems rely on large volumes of data, and any breach or misuse can significantly increase privacy risks [4]. Measures like encryption (both at rest and in transit), anonymizing personally identifiable information (PII), and enforcing role-based access controls are essential for protecting patient data while ensuring AI systems function effectively. These safeguards are key to preventing zero-day attacks.
Censinet RiskOps acts as a centralized hub for AI governance, streamlining workflows across Governance, Risk, and Compliance (GRC) teams. By routing key findings and tasks to the appropriate stakeholders, this approach ensures continuous oversight and accountability. It also aligns with patient safety priorities, maintaining the agility needed to counter zero-day threats effectively.
Conclusion: Building Resilience Against Zero-Day Threats
Zero-day threats remain a pressing issue in healthcare cybersecurity, targeting vulnerabilities that are unknown until exploited. By 2025, these breaches posed severe financial risks and far-reaching consequences [2]. To counter this, the role of machine learning and AI has shifted from merely responding to threats to actively preventing them. These technologies excel at identifying new threats in real time - something traditional, signature-based systems simply cannot achieve.
AI-driven solutions have drastically reduced detection times, cutting them by as much as 98 days. These systems flag unusual activity early, stopping potential breaches before they escalate. Platforms like Censinet RiskOps™ enhance this process by consolidating threat intelligence into automated workflows and offering real-time risk visualization. With human oversight integrated into the system, these platforms ensure a balance between rapid responses and patient safety. Additionally, tools like Censinet AI™ streamline third-party risk assessments, which is critical given the significant role vendor-related breaches play in healthcare security incidents [2]. However, operational efficiency must go hand in hand with strict compliance measures.
As discussed earlier, building resilience requires a layered approach. This includes leveraging AI capabilities, adhering to frameworks like the updated HIPAA Security Rule, and implementing strong data governance practices. Importantly, human oversight must remain central to decisions that affect patient safety and data security.
The cybersecurity landscape continues to evolve, with ransomware attacks increasing by 30% in 2025 and average ransom demands reaching $1.2 million [2]. To stay ahead, healthcare organizations must combine AI's predictive power with rigorous oversight and compliance. Those adopting these proactive strategies today are better equipped to detect, respond to, and neutralize zero-day threats, safeguarding both patient data and care. These efforts are the foundation of a resilient cybersecurity strategy in healthcare.
FAQs
How does machine learning help detect zero-day threats in healthcare?
Machine learning is transforming how healthcare organizations tackle zero-day threats by sifting through massive datasets to spot unusual patterns or behaviors that could signal new vulnerabilities. This approach catches anomalies that traditional methods might overlook, allowing for quicker and more precise responses.
By anticipating potential risks and automating the detection process, machine learning significantly cuts down the time needed to identify and address threats. This proactive approach helps healthcare providers stay a step ahead of cyberattacks while safeguarding sensitive patient data.
How does anomaly detection help identify zero-day cyber threats?
Anomaly detection is key to identifying zero-day threats by pinpointing unusual patterns or behaviors within systems and networks. These irregularities often act as red flags for potential vulnerabilities or attacks that haven’t been encountered before.
By concentrating on unexpected or out-of-the-ordinary activity, anomaly detection allows organizations to spot and address threats early - even in the absence of known signatures or prior data. This capability is crucial for staying prepared against evolving cyber risks.
How does Censinet RiskOps™ simplify risk assessments for healthcare cybersecurity?
Censinet RiskOps™ takes the complexity out of risk assessments in healthcare cybersecurity by integrating real-time threat intelligence with automated monitoring and dynamic risk scoring. It gathers data from various sources - like asset inventories, compliance metrics, and threat feeds - to deliver a clear and prioritized snapshot of vulnerabilities.
By simplifying this process, healthcare organizations can act faster and more decisively, strengthening their ability to manage risks and bolster their cybersecurity defenses.


