How to Address HIPAA Compliance Gaps
Post Summary
HIPAA compliance gaps can expose healthcare organizations to data breaches, fines, and operational risks. Here's what you need to know to protect electronic protected health information (ePHI) and meet updated 2025 requirements:
- Common Gaps: Incomplete risk analyses, missing encryption, outdated vendor agreements, and lack of multi-factor authentication (MFA).
- 2025 Updates: Encryption, MFA, asset inventories, and annual compliance audits become mandatory.
- Key Safeguards: Administrative (policies, training), physical (facility controls, device management), and technical (encryption, access controls).
- Steps to Close Gaps:
- Inventory systems, data, and vendors handling ePHI.
- Conduct a risk analysis to identify vulnerabilities.
- Prioritize high-risk gaps like unencrypted data or missing MFA.
- Implement fixes, track progress, and document efforts.
- Tools: Platforms like Censinet RiskOps™ can streamline risk management, vendor oversight, and compliance tracking.
Treat HIPAA compliance as an ongoing process. Regular audits, monitoring, and updates to policies and safeguards are essential to avoid penalties and ensure patient data security.
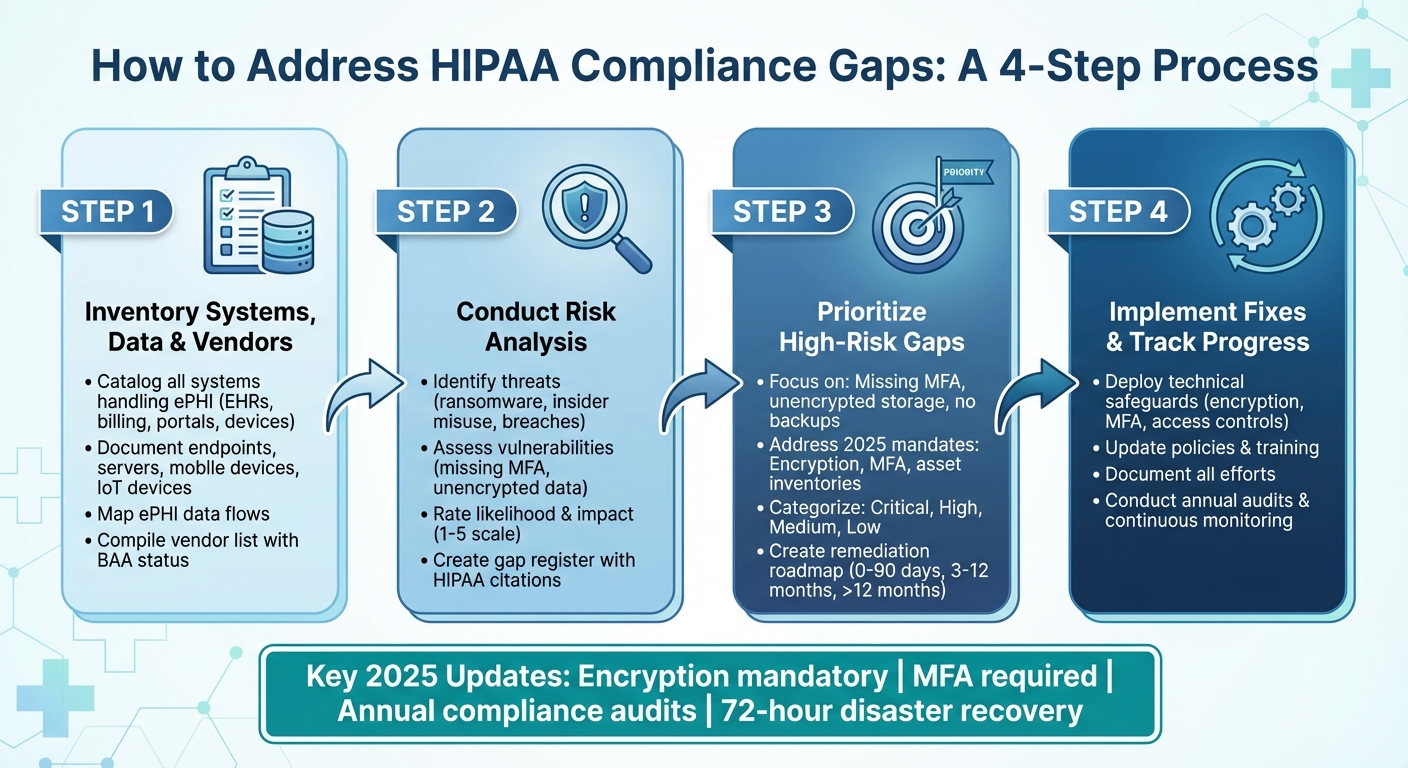
4-Step Process to Close HIPAA Compliance Gaps
Understanding HIPAA Security Rule Requirements
The HIPAA Security Rule breaks down protection requirements into three main safeguard categories: administrative, physical, and technical safeguards[6]. Each category focuses on different aspects of securing electronic protected health information (ePHI), from crafting policies and procedures to implementing physical barriers like locked server rooms and technical defenses like encryption. By understanding these categories, healthcare organizations can pinpoint where their current practices might need improvement.
The Security Rule was designed to accommodate organizations of varying sizes and technical capabilities, giving them some flexibility in how safeguards are applied[6]. However, this flexibility has its limits. All organizations are required to manage risks to a reasonable level, and the proposed 2025 updates aim to clarify the distinction between "required" and "addressable" safeguards. These changes will make it clear which measures are non-negotiable moving forward[3].
With this foundation in mind, let’s take a closer look at the three safeguard categories.
Administrative, Physical, and Technical Safeguards
Administrative safeguards lay the groundwork for a strong security program by focusing on policies, workforce training, and risk management[6]. This includes conducting a formal risk analysis to identify potential threats to ePHI across systems and networks. Workforce training is equally important - employees need to know how to handle ePHI securely, spot phishing attempts, and report incidents. Other key responsibilities include documenting procedures for granting and revoking system access, maintaining contingency plans for data recovery, and managing business associate agreements with vendors who handle ePHI.
Physical safeguards protect the spaces and equipment where ePHI is stored or accessed[6]. This involves implementing facility access controls like badge readers, visitor logs, and locked server rooms to limit physical access to sensitive areas. Policies around workstation security help ensure computers are used appropriately, such as placing privacy screens at registration desks to prevent unauthorized viewing of patient information. Additionally, device and media controls ensure that hardware containing ePHI is properly managed, whether through certified data destruction for retired devices or documented chain-of-custody protocols for portable media.
Technical safeguards rely on technology to secure ePHI and control who can access it[6]. These include access controls, such as unique user IDs, strong authentication methods, and automatic logoffs, to ensure only authorized personnel can view patient data. Audit controls require monitoring system activity - collecting logs from electronic health record (EHR) systems, medical devices, and networks to detect unusual behavior. Encryption is another critical measure, now mandatory for ePHI both at rest and in transit under the 2025 updates[3]. Other technical measures include multi-factor authentication for remote access, integrity controls to prevent unauthorized data changes, and transmission security protocols like TLS and VPNs to protect data during transmission[6].
Creating a HIPAA Compliance Baseline
To establish a compliance baseline, start by inventorying all systems that handle ePHI[2]. This includes EHR platforms, medical devices, cloud services, and third-party applications. The 2025 updates emphasize the need for a complete and documented technology asset inventory and network map for all ePHI-related systems[2]. Once you’ve identified these assets, map each HIPAA Security Rule standard to them. This helps pinpoint where controls like encryption, access management, and incident response are needed. Documenting how data flows - such as from bedside devices to EHR systems and then to billing vendors - ensures that transmission security and vendor protections are addressed comprehensively[2].
A control matrix can help organize this information. For example, create a table that links each Security Rule requirement to specific controls, the systems they apply to, responsible personnel, and their implementation status. Typical columns might include the Security Rule citation (e.g., 45 C.F.R. §164.308(a)(1)), safeguard category, control description, system mapping, control owner (e.g., a Privacy Officer), evidence location, and risk rating. This approach ensures accountability, supports audits, and helps track progress on closing compliance gaps. Risk management platforms like Censinet RiskOps can also streamline these efforts by aligning enterprise controls with vendor assessments to protect ePHI across the supply chain.
Brian Sterud, CIO at Faith Regional Health, stated, "benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters"[1].
When building your compliance baseline, focus on areas that regulators often flag, such as incomplete asset inventories, poor workforce training, insufficient audit logging, undocumented incident response plans, and weak encryption practices[3]. Addressing these issues early is crucial, as they are common areas of enforcement. Use this baseline to guide your HIPAA gap analysis and prioritize corrective actions effectively.
Conducting a HIPAA Gap Analysis
After setting your compliance baseline, the next step is to pinpoint where your organization falls short of HIPAA Security Rule requirements. This is where a gap analysis comes in. It compares your current safeguards - like policies, technical measures, documentation, and vendor relationships - against the Security Rule's mandates. The goal? To uncover missing, incomplete, or ineffective controls [2][3]. Unlike a general IT security assessment, a HIPAA gap analysis directly ties findings to specific implementation standards and provides written proof of how ePHI is protected [2][6]. With proposed 2025 updates requiring annual compliance audits and removing the "required versus addressable" distinction, a thorough and well-documented gap analysis is no longer optional - it’s essential [3][5][7].
The Department of Health and Human Services (HHS) has emphasized that failing to conduct a thorough risk analysis is one of the most frequent and serious violations found during OCR audits [3]. In fact, during the most recent HIPAA audits conducted between 2016 and 2017, many entities were found noncompliant with this requirement [3]. This highlights the need for a structured, data-driven approach to identifying and documenting compliance gaps. Let’s break down the process into actionable steps: creating an inventory of systems, data, and vendors; conducting a HIPAA-aligned risk analysis to identify gaps; and prioritizing those gaps for remediation based on their risk level and regulatory importance.
Inventory Systems, Data, and Vendors
A complete inventory is the backbone of any effective gap analysis. Start by cataloging all systems that create, receive, maintain, or transmit ePHI. This includes EHRs, billing platforms, patient portals, email systems, cloud services, backup systems, and even connected medical devices [2][6]. Make sure to account for endpoints, servers, mobile devices, IoT devices, and network infrastructure that might store or process ePHI [2][8]. For each asset, document details like its name, owner, location, type and volume of ePHI it handles, connectivity (interfaces, APIs, VPNs), and current authentication and encryption measures [2][9].
While building this inventory, map out how ePHI flows through your environment. This can help you identify hidden vulnerabilities, such as unencrypted email channels or unsecured file transfers, that wouldn’t be obvious from a simple asset list [2][6]. Additionally, compile a vendor list by pulling information from accounts payable, procurement records, contracts, and IT service catalogs. Flag vendors that access or influence ePHI and document key details like the services they provide, data flows they handle, and the status of their business associate agreements (BAAs) [2][5][9].
Tools like Censinet RiskOps™ can simplify this process by centralizing vendor data, automating security questionnaires aligned with HIPAA, and maintaining an up-to-date catalog of third parties interacting with ePHI. As James Case, VP & CISO at Baptist Health, puts it:
"Not only did we get rid of spreadsheets, but we have that larger community [of hospitals] to partner and work with."
With a comprehensive inventory in place, the next step is to assess the risks tied to these assets.
Performing Risk Analysis and Identifying Gaps
A HIPAA-aligned risk analysis examines threats, vulnerabilities, and residual risk across your ePHI environment [2][6]. Start by identifying potential threats, such as ransomware, insider misuse, lost or stolen devices, misconfigured cloud storage, vendor breaches, and legacy system failures [2][3][6]. Then, assess vulnerabilities for each asset and data flow. Examples include missing multi-factor authentication (MFA), unencrypted databases, outdated software, weak backup practices, insufficient network segmentation, and lack of audit logging [2][3].
For each identified threat-vulnerability pair, use a 1–5 scale to rate the likelihood and potential impact, which helps determine the residual risk [2][9]. Document your existing security measures and highlight gaps where they fall short of HIPAA standards [2][3][6]. This analysis should be documented in writing and updated annually or whenever significant operational changes occur [5][6][9].
As part of this process, create a gap register - a detailed log of areas where your current practices don’t fully meet HIPAA requirements or internal policies [2][9]. Each entry should include the relevant HIPAA citation (e.g., 45 C.F.R. §164.312(a)(2)(iv) for encryption), a description of the gap (like "MFA not enabled on remote EHR access"), affected systems and data, associated risk ratings, and proposed remediation steps. Include details such as the responsible owner, target completion date, and current status [2][3][9]. This gap register transforms your risk analysis into a concrete remediation plan and provides a clear audit trail [2][5][9].
Once risks are assessed and documented, the focus shifts to addressing the gaps.
Prioritizing Gaps for Remediation
Not all gaps are created equal - some demand immediate attention, while others can be addressed over time. The gaps identified during your analysis serve as the foundation for a remediation plan. Use a multi-factor scoring model to prioritize them. This model should consider factors like risk severity (likelihood and impact of a breach), regulatory urgency (e.g., common OCR violations such as incomplete risk analyses), data sensitivity, and operational impact (including cost, complexity, and downtime) [2][3][9]. Based on these factors, categorize gaps as critical, high, medium, or low [2][9].
Focus first on high-risk, high-impact gaps - those that could result in significant ePHI exposure, disrupt patient care, or attract regulatory penalties [2][3][8]. Examples include missing MFA for remote access, unencrypted cloud storage, lack of off-site backups, and untested incident response plans [2][3]. Additionally, prioritize gaps highlighted in the proposed 2025 updates, such as enforcing MFA, encrypting data both in transit and at rest, maintaining complete asset inventories, and meeting the 72-hour disaster recovery requirement [2][3][4].
Develop a remediation roadmap that is both time-phased and risk-based. Start with quick wins that significantly reduce exposure [2][8][9]. Then, organize actions into short-term (0–90 days), medium-term (3–12 months), and long-term (>12 months) initiatives. Each initiative should include milestones, budget estimates, dependencies (e.g., completing an asset inventory before network segmentation), assigned owners, and success metrics, such as a reduction in unresolved high-risk items [2][3][9]. Governance committees should regularly review and update the roadmap to ensure progress.
As Brian Sterud, CIO at Faith Regional Health, explains:
"Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters."
Implementing Solutions to Address Compliance Gaps
To effectively address HIPAA compliance gaps, start by breaking down identified issues into specific, actionable tasks. Assign clear ownership for each task and establish timelines based on risk priorities [2][9]. The objective is to systematically close gaps spanning technical, administrative, and physical safeguards while maintaining a clear and defensible record of compliance efforts. Addressing technical vulnerabilities is especially critical to protect electronic protected health information (ePHI).
Strengthening Technical Safeguards
Technical safeguards often represent the most pressing vulnerabilities and are a common source of breaches. Start by implementing FIPS 140-2 or NIST-compliant encryption for ePHI, ensuring data is encrypted both at rest (databases, file shares, endpoint devices, backups) and in transit (TLS 1.2+ for network traffic, VPN for remote access) [2][9]. Require multi-factor authentication (MFA) for all ePHI systems, including electronic health records (EHRs), cloud applications, and remote access portals, ensuring compliance with updated 2025 security protocols [2][3][9].
Enhance access controls by mandating unique user IDs, eliminating shared accounts, and implementing role-based access control (RBAC) tied to job responsibilities and the "minimum necessary" standard outlined in the Privacy Rule. Automate processes for onboarding, role changes, and terminations to ensure timely updates to access rights [2][3]. Enable audit logging on all systems containing ePHI, and centralize these logs in a secure platform such as a Security Information and Event Management (SIEM) system. Logs should capture key activities like authentication attempts, privilege changes, data exports, and unusual network behavior. Automated alerts tied to incident response plans can help identify and address suspicious activities promptly [2][3][6].
Establish a vulnerability management program that includes biannual scans, risk-based remediation, and annual penetration testing [9]. Secure system configurations by using standardized images for servers and workstations, removing unnecessary software, hardening ports and protocols, and deploying endpoint protection tools [9]. Regularly test backups and disaster recovery plans, maintaining encrypted, offline, or immutable backups of ePHI. Ensure recovery procedures meet the 72-hour restoration requirement and document recovery time objectives (RTOs) [2][9].
Platforms like Censinet RiskOps™ can centralize data on clinical applications, medical devices, and vendors handling ePHI. These tools help pinpoint gaps in safeguards like encryption and MFA, standardize risk assessments, and track remediation tasks with supporting evidence such as policies and test results [2]. By focusing resources on high-risk systems, organizations can ensure safeguards are effective before new systems go live or contracts are renewed [2].
Improving Administrative and Physical Safeguards
Technical measures are essential, but administrative and physical safeguards provide the framework for a well-rounded compliance strategy. Begin by updating core policies to address risk management, workforce security, access control, incident response, disaster recovery, and vendor oversight [2][6][9]. Ensure these policies are up-to-date and easily accessible.
Implement a security awareness and training program for all employees, with orientation for new hires and annual refreshers. Training should cover phishing awareness, proper handling of PHI, mobile device security, password and MFA best practices, and incident reporting [2][3]. Maintain records of attendance and comprehension to provide evidence during audits. Strengthen workforce security processes by formalizing onboarding, access authorization reviews, and swift access revocation when employees leave or change roles [2].
For physical safeguards, enforce facility access controls through badge systems, visitor sign-ins, escorted access to sensitive areas, and video surveillance where needed [2]. Workstation policies should define appropriate usage, enforce automatic screen locks, and ensure monitors are positioned to prevent unauthorized viewing in clinical areas [2]. Secure portable devices like laptops and tablets by enabling encryption and tracking, and conduct regular inspections of server rooms and network closets to ensure physical safeguards remain effective [6]. Document these measures thoroughly to demonstrate compliance during audits.
Centralized platforms can also streamline the storage of policies, training records, and evidence of risk mitigation efforts, simplifying audits and inspections [5][6].
Terry Grogan, CISO at Tower Health, shared that using Censinet RiskOps allowed the organization to reallocate three full-time employees, enabling them to perform more risk assessments with just two dedicated staff members.
Managing Third-Party Risk
Third-party vendors handling ePHI pose additional risks, making their oversight a critical part of compliance. Categorize vendors into risk tiers - high, medium, or low - based on the sensitivity of the PHI they handle and the importance of their services. Secure Business Associate Agreements (BAAs) with all vendors before sharing data, as required by HIPAA, and ensure they meet regulatory expectations [2][3][9].
Evaluate vendor safeguards using security questionnaires mapped to HIPAA requirements, review independent audits like SOC 2 or HITRUST, and, when necessary, request technical validation such as penetration test results or configuration evidence [2][9]. For high-risk vendors, consider conducting on-site assessments or commissioning third-party audits. This due diligence helps ensure vendors’ security measures align with your organization's compliance goals.
Tools like Censinet RiskOps™ can simplify vendor management by centralizing inventories, BAAs, risk assessments, and remediation plans. The platform automates the distribution and scoring of security questionnaires, flags high-risk responses, and links findings to specific HIPAA safeguards requiring remediation [2]. Its collaborative features allow healthcare organizations and vendors to track and document progress, improving transparency and accountability. By standardizing risk management processes and providing leadership dashboards, Censinet helps demonstrate a structured third-party oversight program during audits or investigations [2].
sbb-itb-535baee
Maintaining Continuous HIPAA Compliance
HIPAA compliance isn't a one-and-done task. It's an ongoing process that demands constant attention, from regular monitoring and documentation to adapting to new challenges. The proposed 2025 Security Rule updates highlight this by requiring annual risk analyses, compliance audits, and continuous system monitoring for electronic protected health information (ePHI) [5]. Treating compliance as a static checklist rather than a dynamic program can leave organizations vulnerable to regulatory penalties and security breaches.
To keep up, continuous monitoring and proactive adjustments are critical as threats and regulations evolve.
Monitoring and Auditing Compliance
A well-structured compliance calendar can save organizations from scrambling at the last minute before an OCR review. An annual risk analysis - or one conducted after major changes - should identify where ePHI is stored, processed, and transmitted. It should also evaluate current safeguards, anticipate potential threats like ransomware or insider misuse, and document risk mitigation strategies [2].
The proposed Security Rule also calls for formal compliance audits at least once a year. These audits verify adherence to policies, technical controls (such as multi-factor authentication and encryption), workforce training, vendor oversight, and incident response capabilities [5]. A comprehensive compliance calendar should include regular reviews, vulnerability scans, penetration tests, disaster recovery testing (to meet the 72-hour restoration requirement), and monthly reviews of metrics like failed logins, open vulnerabilities, and vendor assessments [2].
Continuous monitoring takes this a step further by providing real-time visibility and automated detection. Essential tools include centralized log collection for systems accessing ePHI, automated alerts for high-risk activities (like unusual logins or large data exports), continuous vulnerability management, and automated asset discovery to ensure all ePHI systems are accounted for [8]. Security tools such as SIEM platforms and endpoint detection solutions can enhance real-time compliance efforts.
Platforms like Censinet RiskOps™ simplify compliance tracking by acting as a centralized hub for risk analyses, audit results, policies, and corrective action plans. The platform also maintains records of clinical applications, medical devices, and vendors handling ePHI. It tracks remediation tasks with supporting evidence and generates reports for leadership and auditors, highlighting risk trends and program maturity. This streamlined documentation can ease the burden during OCR investigations.
Adapting to Regulatory and Industry Changes
In addition to monitoring, staying updated on regulatory changes ensures safeguards remain effective. Compliance teams should keep an eye on updates from HHS, OCR, and guidance from organizations like CISA and NIST, particularly concerning ransomware preparedness [3]. When new rules or recommendations are introduced, organizations should assess their impact, revise policies, adjust technical controls (e.g., tightening MFA or encryption settings), and update training materials.
While HIPAA doesn't prescribe specific system architectures, proposed updates and best practices from HHS emphasize adopting zero-trust principles. These include enforcing MFA for all ePHI access, applying least-privilege access with regular role reviews, segmenting networks to isolate clinical systems, and using continuous authentication to reduce reliance on perimeter security [2]. For ransomware preparedness, organizations should maintain hardened, immutable backups, test recovery processes to meet the 72-hour restoration goal, implement email and endpoint protections, and conduct incident response drills simulating ransomware attacks on critical systems [2].
Benchmarking against other healthcare organizations can also provide valuable insights. Comparing metrics like MFA enforcement rates, time to patch critical vulnerabilities, frequency of risk assessments, incident detection and containment times, and the proportion of high-risk vendors with completed remediation plans can help validate an organization's approach [8]. Tools like Censinet's healthcare-focused platform offer anonymized benchmarking data, enabling leaders to identify areas for improvement, prioritize actions, and demonstrate alignment with industry standards to regulators.
Conclusion
Addressing HIPAA Security Rule compliance gaps isn’t a one-and-done task - it’s an ongoing process that safeguards patient information, minimizes breach risks, and keeps your organization prepared for OCR reviews. The approach is simple but essential: understand the requirements (including the proposed 2025 updates), conduct a thorough gap analysis, implement targeted fixes for high-risk areas, and commit to continuous improvement with regular audits and monitoring. Consistently prioritizing and addressing high-risk vulnerabilities strengthens your HIPAA compliance posture, reduces costs tied to incidents, protects your reputation, and helps prevent breaches that could harm patients or disrupt care. Ignoring these gaps, on the other hand, opens the door to penalties, operational setbacks, and data breaches.
For organizations with limited resources or older systems, tackling everything at once can feel overwhelming. That’s why risk-based prioritization is key. Focus first on controls that significantly reduce the likelihood or impact of incidents, saving lower-priority gaps for later. Tools like automation and specialized platforms can help lighten the load, especially for smaller teams, by streamlining vendor risk assessments, documentation, and evidence collection. These efficiencies make it easier to show progress to both executives and regulators.
Platforms designed specifically for healthcare, like Censinet RiskOps™, can simplify the remediation and monitoring process. By centralizing risk analyses, audit results, vendor inventories, and remediation plans, Censinet provides a one-stop solution tailored to healthcare needs. It automates risk assessments for third parties and internal systems, offers real-time tracking of clinical tools and medical devices handling PHI, and even includes anonymized benchmarking data to compare your efforts to industry standards.
Terry Grogan, CISO at Tower Health, shared: "Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required."
To build a strong compliance program, adopt a recurring cycle of assess → remediate → monitor → improve, supported by regular audits, updated risk analyses, and continuous vendor oversight. Clearly define ownership and use measurable metrics - like the number of unresolved high-risk findings or time to remediate critical vulnerabilities - to track progress. By embedding compliance into everyday operations, you create a culture of safety that benefits everyone.
FAQs
What are the key changes to HIPAA compliance requirements for 2025?
HIPAA compliance requirements for 2025 are shifting to prioritize stronger cybersecurity measures, a more detailed approach to risk assessments, and tighter breach notification protocols. These updates are designed to tackle the growing challenges posed by modern threats and to enhance the protection of patient information.
Healthcare organizations are being urged to embrace advanced technologies, such as AI-driven platforms, to simplify risk management processes and stay aligned with compliance standards. Taking a proactive stance on these updates can help minimize risks and protect sensitive patient data more effectively.
What is the best way for healthcare organizations to conduct a HIPAA gap analysis?
To carry out a meaningful HIPAA gap analysis, healthcare organizations need to take a close look at their current security measures and compare them to the requirements laid out in the HIPAA Security Rule. This process includes pinpointing vulnerabilities, documenting areas where compliance is lacking, and deciding which issues need immediate attention.
Tools like Censinet RiskOps™ can make this process easier by automating risk assessments, spotting compliance issues, and offering ongoing monitoring. These capabilities help healthcare organizations stay ahead of potential risks, safeguard sensitive patient information, and stay aligned with regulatory requirements.
What is the role of third-party vendors in HIPAA compliance, and how can they be effectively managed?
Third-party vendors play a crucial role in healthcare operations, but they can also bring compliance challenges, especially when handling protected health information (PHI) or other sensitive data. To maintain HIPAA compliance, healthcare organizations must take a proactive approach to managing these vendor relationships.
Here’s how organizations can effectively manage third-party vendors:
- Conduct detailed risk assessments to uncover potential vulnerabilities in vendor systems and processes.
- Set clear contractual terms that explicitly outline HIPAA compliance obligations and expectations.
- Perform regular security reviews and implement continuous monitoring to address new or evolving risks.
Using platforms specifically designed for healthcare risk management can simplify these efforts. These tools help organizations evaluate risks, track vendor compliance, and resolve issues before they escalate. With proper oversight, healthcare providers can ensure that their vendors meet HIPAA standards, safeguarding sensitive patient information effectively.


