CMMC 2.0 Levels: What Healthcare Needs to Know
Post Summary
CMMC 2.0 compliance is now mandatory for organizations involved in Department of Defense (DoD) contracts, including healthcare providers. Here's what you need to know:
- What is CMMC 2.0? It's the updated framework to protect Federal Contract Information (FCI) and Controlled Unclassified Information (CUI).
- Who needs it? Healthcare organizations working with the DoD, such as those handling TRICARE claims, military research, or VA contracts.
- When is it required? Compliance began in December 2024, with full implementation across contracts by 2027.
- Levels of certification:
- Level 1: Basic cybersecurity for FCI (self-assessment).
- Level 2: Advanced controls for CUI (self or third-party assessment).
- Level 3: Highest security for critical defense data (DoD assessment).
If you're a healthcare provider managing sensitive DoD-related data, it's time to evaluate your cybersecurity practices, identify gaps, and prepare for certification. The CMMC framework builds on existing standards like NIST SP 800-171, so leveraging current HIPAA or NIST-based controls can simplify the process.
Key takeaway: Start now. Compliance requires detailed planning, documentation, and assessments, especially for Level 2 and beyond.
The 3 CMMC 2.0 Levels Explained
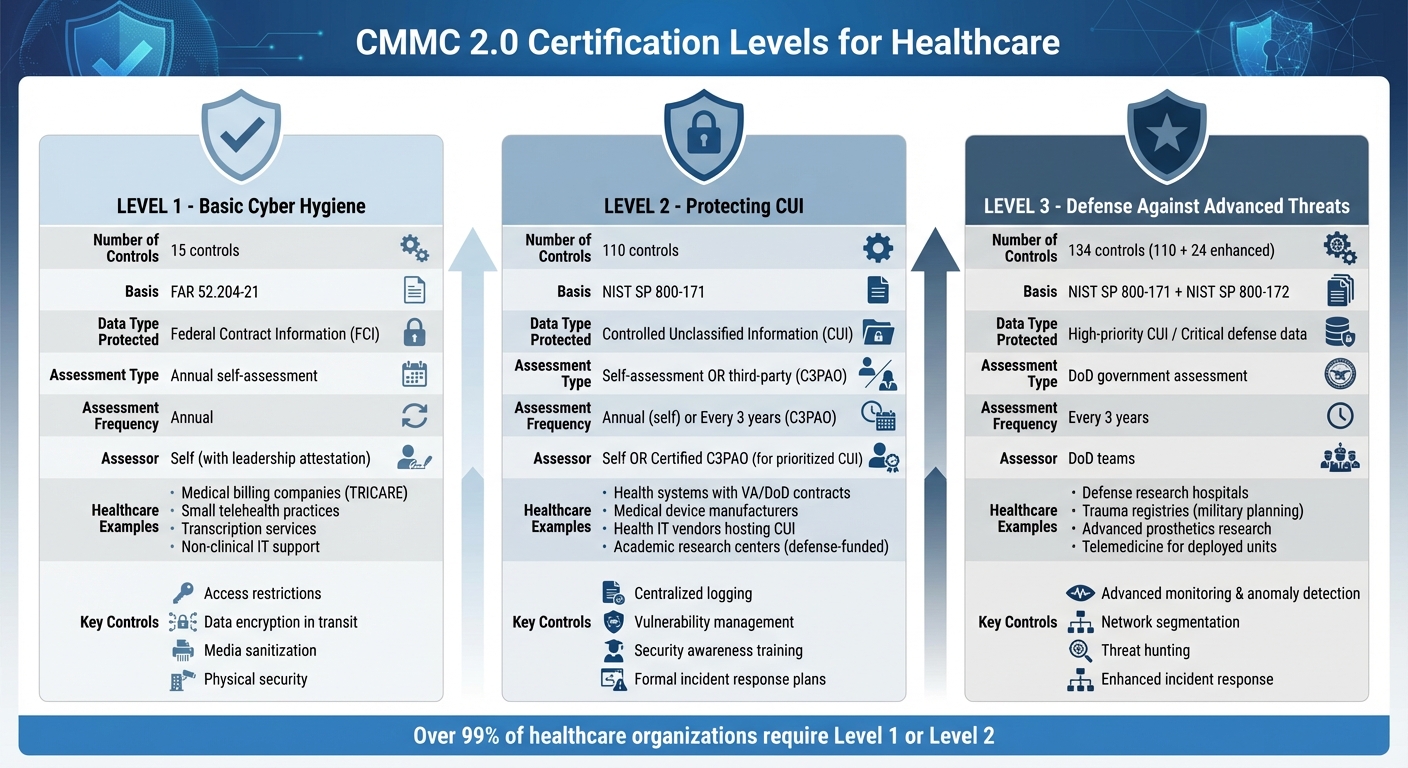
CMMC 2.0 Levels Comparison for Healthcare Organizations
CMMC 2.0 breaks cybersecurity requirements into three levels, each tailored to the sensitivity of the information involved and the level of assessment rigor needed. Here’s a quick overview:
- Level 1: Focuses on safeguarding basic Federal Contract Information (FCI), like contract details such as pricing and schedules.
- Level 2: Protects Controlled Unclassified Information (CUI), which includes sensitive data like clinical research findings and patient information tied to Department of Defense (DoD) care.
- Level 3: Defends high-value CUI against advanced threats, aimed at organizations involved in critical national security missions or classified medical research.
Level 1: Basic Cyber Hygiene
Level 1 is all about establishing a foundation of basic cybersecurity practices. It includes 15 controls derived from FAR 52.204-21, covering essentials like:
- Restricting system access to authorized users.
- Encrypting data during transmission.
- Sanitizing media before disposal.
- Physically securing devices that process FCI.
This level applies to contracts involving only FCI, such as non-clinical IT support, equipment provisioning, or administrative services. Organizations at Level 1 conduct annual self-assessments, documenting their compliance and recording scores in the DoD's Supplier Performance Risk System (SPRS). Leadership must formally attest to compliance, but no third-party audits are required.
Level 2: Protecting Controlled Unclassified Information
Level 2 introduces more rigorous controls to secure CUI, aligning with the 110 requirements in NIST SP 800-171. These controls span 14 categories, including Access Control, Incident Response, and System Integrity. Key practices include:
- Centralized logging.
- Vulnerability management.
- Security awareness training.
- Formal incident response plans.
Level 2 is typically required for healthcare organizations involved in DoD-funded care or research. The assessment process depends on whether the contract involves prioritized CUI:
- Non-prioritized CUI: Annual self-assessments are sufficient.
- Prioritized CUI: Requires a third-party assessment by a certified C3PAO every three years.
Preparing for third-party assessments can take months, often involving gap analysis, remediation, and mock audits. Organizations should carefully review contract requirements early to determine the appropriate path.
Level 3: Defense Against Advanced Threats
Level 3 represents the highest level of cybersecurity under CMMC 2.0. It builds on the 110 controls from NIST SP 800-171 and adds approximately 24 enhanced controls from NIST SP 800-172, totaling 134 requirements. These include:
- Advanced monitoring and anomaly detection.
- Cyber resiliency measures like network segmentation.
- Threat hunting and enhanced incident response capabilities.
This level is less common in healthcare but applies to organizations handling high-priority military biomedical research or classified-adjacent clinical data. Examples might include trauma registries for military planning, advanced prosthetics research, or telemedicine platforms for forward-deployed units. Assessments at this level are conducted by DoD teams every three years, with a focus on how well the organization implements controls, integrates threat intelligence, and responds to sophisticated attacks.
Understanding these levels is critical for healthcare organizations to align their cybersecurity efforts with the appropriate CMMC 2.0 requirements, ensuring they meet DoD standards while protecting sensitive information.
How Each CMMC 2.0 Level Applies to Healthcare
Healthcare organizations interact with the Department of Defense (DoD) in various ways, such as handling TRICARE billing or participating in military research. The appropriate Cybersecurity Maturity Model Certification (CMMC) level depends on the sensitivity of the DoD data they manage. Below, we'll break down the specific requirements for healthcare vendors, organizations, and high-priority contractors under each CMMC 2.0 level.
Level 1 Requirements for Healthcare Vendors
Level 1 applies to healthcare vendors that only handle Federal Contract Information (FCI). FCI typically includes basic contract details like pricing, schedules, and administrative data. Examples of vendors in this category include medical billing companies managing TRICARE claims, small telehealth practices serving military families, transcription services, and specialized clinics with non-clinical DoD contracts.
To meet Level 1, vendors must implement 15 basic security controls that align closely with everyday operations. These include:
- Access control: Limit access by enforcing strong passwords, unique logins, and restricting personal device use.
- Media protection: Securely wipe data from hard drives, USB devices, and printers before disposal or reuse.
- Physical protection: Ensure server rooms are locked, maintain visitor logs, and enforce screen-lock policies in shared spaces like call centers.
- System integrity: Regularly update anti-malware software and apply patches to laptops accessing DoD systems.
While HIPAA may address some aspects of security, it often lacks guidance on media sanitization or physical access protocols, making additional steps necessary. Vendors also need to complete an annual self-assessment, which requires minimal evidence, such as screenshots of access controls, training records, and asset inventories. These can often be incorporated into existing compliance workflows.
Level 2 Requirements for Healthcare Organizations
Level 2 is aimed at organizations handling Controlled Unclassified Information (CUI), which includes sensitive data like clinical research results, patient records tied to DoD care, or telemetry from medical devices used in military settings. This level applies to larger entities such as health systems with VA or DoD contracts, medical device manufacturers, health IT vendors hosting CUI, and academic research centers conducting defense-funded studies.
At this level, organizations must implement 110 controls based on NIST SP 800-171, covering 14 security domains. These controls require more advanced capabilities, such as:
- Centralized audit logging: Track and retain logs for systems managing CUI, including electronic health records, research databases, and device management platforms.
- Incident response: Develop and document plans to detect, contain, and report security incidents involving CUI.
- Formal risk assessments: Create a documented System Security Plan (SSP) and track remediation efforts using Plans of Action and Milestones (POA&Ms).
Many healthcare organizations already compliant with HIPAA's Security Rule may have a strong foundation in areas like access management, encryption, and audit logging. However, CMMC Level 2 calls for more detailed documentation and a broader scope, focusing specifically on protecting CUI rather than just Protected Health Information (PHI). Mapping existing HIPAA or NIST Cybersecurity Framework controls to the 110 Level 2 requirements can help identify gaps and streamline compliance efforts.
Level 3 Requirements for High-Priority Healthcare Contractors
Level 3 is less common in healthcare but applies to organizations involved in high-priority DoD programs or those facing advanced cybersecurity threats. Examples include defense research hospitals conducting sensitive clinical studies, trauma registries used for military planning, and large IT providers running telemedicine platforms for deployed units.
Organizations at this level must meet 134 controls, which include the 110 from NIST SP 800-171 plus 24 enhanced requirements from NIST SP 800-172. These additional controls focus on advanced security measures such as:
- Threat hunting: Actively monitor systems for potential threats.
- Network segmentation: Isolate critical systems to limit exposure.
- Anomaly detection: Use advanced tools to identify unusual activity.
DoD assessments, conducted every three years, go beyond verifying the existence of these controls. They evaluate how well organizations integrate threat intelligence and respond to sophisticated cyber threats. While less prevalent in healthcare, these measures are critical for protecting sensitive research and ensuring the security of strategic operations tied to national defense.
How CMMC 2.0 Aligns With Healthcare Cybersecurity Standards
Healthcare organizations can tap into their existing frameworks like HIPAA, HITECH, and NIST to align with CMMC 2.0 requirements. Since CMMC 2.0 is built on NIST standards, there's a natural overlap - Level 2 aligns with NIST SP 800-171, while Level 3 incorporates elements of NIST SP 800-172.
This overlap is substantial. For instance, the 110 controls required for CMMC 2.0 Level 2 cover 14 domains, including access control, audit and accountability, incident response, and risk assessment. These domains closely mirror the requirements of HIPAA's Security Rule and the NIST Cybersecurity Framework. Additionally, HITECH’s push for meaningful use of electronic health records has led many healthcare providers to adopt NIST-based controls, creating a solid starting point for CMMC compliance. The table below provides a detailed breakdown of these alignments and the gaps that remain.
CMMC 2.0 Levels vs. Healthcare Standards Comparison
The table below shows how CMMC 2.0 levels align with healthcare cybersecurity standards and highlights where additional efforts may be needed.
| CMMC 2.0 Level | Primary NIST Basis | Healthcare Framework Alignment | Key Gaps & New Requirements |
|---|---|---|---|
| Level 1 – Foundational | Basic cyber hygiene | Aligns with HIPAA Administrative Safeguards and basic NIST CSF practices | Focuses on essential cybersecurity measures already in place in many healthcare settings. |
| Level 2 – Advanced | NIST SP 800-171 (110 controls) | Reflects the HIPAA Security Rule, HITRUST CSF, and related NIST CSF domains | Requires documented System Security Plans (SSPs), Plans of Action & Milestones, and enhanced audit logging to safeguard Controlled Unclassified Information (CUI). |
| Level 3 – Expert | NIST SP 800-172 | Matches high-level HITRUST implementations and advanced NIST CSF profiles | Introduces advanced capabilities like threat hunting, network segmentation, and anomaly detection, exceeding standard HIPAA safeguards. Primarily applies to high-priority contractors. |
This alignment reveals clear opportunities for healthcare organizations to leverage their existing controls to ease compliance efforts.
Using Existing Controls to Meet CMMC Requirements
Healthcare organizations can streamline their path to CMMC compliance by mapping their current practices to the framework. Start by identifying where Federal Contract Information (FCI) or Controlled Unclassified Information (CUI) resides in your systems. These areas often overlap with environments handling Protected Health Information (PHI).
Documenting existing HIPAA controls, such as centralized audit logs and formal risk assessments, can help meet CMMC Level 2’s evidence requirements. By mapping HIPAA and NIST controls to CMMC standards, organizations can avoid redundant work and simplify compliance.
Matt Christensen, Senior Director of GRC at Intermountain Health, shared, "Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare."
Solutions like Censinet RiskOps can help healthcare providers manage overlapping requirements efficiently. By enabling continuous risk assessments, cybersecurity benchmarking, and vendor risk management, Censinet RiskOps has proven to reduce the burden on staff. Terry Grogan, CISO at Tower Health, noted that the platform reduced the full-time employee (FTE) demand for risk assessments from three to two, making it easier to manage both HIPAA and CMMC requirements without duplicating efforts.
sbb-itb-535baee
How to Achieve CMMC Compliance in Healthcare
Identifying Your Required CMMC Level
To get started with CMMC compliance, the first step is figuring out which level applies to your specific Department of Defense (DoD) contracts. Take a close look at your contracts to find the CMMC level specified in the solicitation or contract clauses. This will be clearly outlined as a condition for being awarded the contract.
If your organization only handles Federal Contract Information (FCI) - basic, non-public information - you'll likely need Level 1 (Foundational). This level requires an annual self-assessment of 15 basic safeguards. However, if your systems are used to store, process, or transmit Controlled Unclassified Information (CUI) - like defense-related research or technical data - you'll probably need Level 2 certification. Level 2 typically involves a third-party assessment every three years and is based on the NIST SP 800-171 standards.
Once you've identified your required level, map out all systems and vendors that interact with DoD data. Clearly defining where FCI or CUI resides will help you scope your compliance efforts. The majority of organizations, over 99%, will fall under Level 1 or Level 2 requirements, meaning most healthcare contractors won't need to meet the advanced standards for Level 3, which are reserved for critical defense programs.
Building a CMMC Compliance Program
Start by conducting a gap assessment based on the CMMC level you need to meet. For Level 1, evaluate your systems against the 15 basic safeguards outlined in FAR 52.204-21. For Level 2, use the NIST SP 800-171 assessment methodology to score your current controls in areas like access control, audit and accountability, incident response, and risk management. This process will help you identify which requirements are already covered - often through existing HIPAA controls - and where improvements are needed.
For any gaps, develop a Plan of Action and Milestones (POA&M). Under CMMC 2.0, POA&Ms can be used sparingly and under strict conditions. Most issues must be resolved within 180 days, and critical controls can't be deferred. Your POA&M should include each unmet requirement, who is responsible for addressing it, the resources needed, and a target completion date. Focus on foundational controls like multifactor authentication, encryption, centralized logging, and vulnerability management, as these typically need to be resolved before certification.
When implementing security changes, coordinate with clinical engineering and IT teams to avoid disruptions, especially for medical devices. Work with manufacturers to plan patches and network segmentation in a way that ensures patient safety and equipment functionality.
To prepare for your assessment, gather and organize all required documentation well in advance. For Level 1, this includes policies, procedures, screenshots, audit logs, and training records to support your annual self-attestation. For Level 2, you’ll need a detailed System Security Plan (SSP) that outlines system boundaries, data flows, and how each NIST SP 800-171 requirement is fulfilled. Engage a Certified Third-Party Assessment Organization (C3PAO) early to assist with your triennial certification. Assign control owners within your organization to ensure quick responses during the assessment process. Using specialized tools can also help streamline these efforts.
How Censinet Supports CMMC Compliance
Once your compliance program is in place, leveraging technology can make the process more efficient. Censinet RiskOps is one such tool designed to simplify CMMC compliance for healthcare organizations. The platform enables continuous risk assessments and gap analyses, directly aligned with CMMC requirements for Levels 1 and 2. Instead of juggling spreadsheets, Censinet RiskOps serves as a centralized hub where you can monitor control statuses, track POA&M progress, and flag overdue tasks - all while staying within the required 180-day remediation window.
The platform also offers cybersecurity benchmarking, allowing you to measure your program’s maturity against industry standards. This can demonstrate readiness to assessors and help secure necessary resources. For instance, Terry Grogan, CISO at Tower Health, shared:
"Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required."
Additionally, Censinet RiskOps addresses vendor and supply chain risks, a crucial aspect of CMMC compliance. Acting as a cloud-based risk exchange, the platform enables secure sharing of cybersecurity data with healthcare delivery organizations and third-party vendors. This collaborative approach helps you evaluate whether your vendors meet CMMC requirements, monitor their remediation efforts, and maintain ongoing compliance through both annual self-assessments and three-year certification cycles. Brian Sterud, CIO at Faith Regional Health, emphasized:
"Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters."
Preparing Your Healthcare Organization for CMMC 2.0
The CMMC 2.0 Final Rule is officially in place as of December 2024, and healthcare organizations partnering with the Department of Defense (DoD) need to act fast. The DoD is rolling out its CMMC requirements through a phased schedule from 2025 to 2027, making certification a mandatory condition for securing contracts. By December 2025, many solicitations will require Level 2 certification, and by late 2027, all applicable DoD contracts will include specific CMMC level requirements. This means taking a hard look at your cybersecurity practices now is essential.
Start by assessing where your organization currently stands. Conduct a baseline gap assessment to measure your compliance against the required controls - 15 for Level 1, 110 for Level 2, and 134 for Level 3. Use this assessment to create a remediation plan that prioritizes high-impact controls, such as multifactor authentication, centralized logging, incident response, and network segmentation. Since most healthcare organizations require 18–24 months to achieve full readiness, beginning now ensures you're on track to meet contract deadlines.
Leverage existing frameworks like HIPAA, HITRUST, and NIST to align with CMMC requirements. Many healthcare organizations already have a strong foundation in place, but CMMC introduces additional expectations, including stricter configuration management, continuous monitoring, and formalized Plans of Action and Milestones (POA&M). Aligning these frameworks not only reduces costs but also accelerates implementation and minimizes disruption to patient care.
To simplify the process, consider platforms like Censinet RiskOps™, which are designed to centralize risk assessments, track POA&M remediation within the required 180-day window, and benchmark your cybersecurity maturity against industry standards. These tools also address vendor and supply chain risks, a critical concern for healthcare organizations handling sensitive data. Purpose-built solutions like this are tailored to meet the unique challenges faced by the healthcare sector.
As part of your preparation, establish a cross-functional governance team for CMMC compliance. This team should include IT security, compliance, legal, supply chain, and clinical leaders involved in DoD contracts. Integrate CMMC requirements into your procurement processes, centralize documentation, and engage a C3PAO early to ensure a smooth path to Level 2 certification. With enforcement already underway, organizations that act now will not only secure DoD contracts but also bolster their defenses against the growing cyber threats to patient safety and care delivery.
FAQs
How can healthcare organizations align HIPAA controls with CMMC 2.0 standards?
Healthcare organizations can bring their HIPAA controls in line with CMMC 2.0 standards by mapping HIPAA’s security and privacy rules to the appropriate CMMC domains. This approach helps maintain consistency while highlighting areas that might require extra attention or improvements.
Leveraging a risk management framework like Censinet RiskOps™ can make this process smoother. It simplifies assessments, pinpoints gaps, and supports proactive compliance efforts. Additionally, continuous monitoring plays a critical role in staying aligned and tackling emerging cybersecurity threats as they arise.
How can healthcare providers prepare for a CMMC 2.0 Level 2 assessment?
To get ready for a CMMC 2.0 Level 2 assessment, healthcare providers should start by understanding the specific requirements tied to this level. A good first step is conducting a gap analysis to pinpoint areas where current cybersecurity measures might be lacking. Once gaps are identified, focus on implementing the necessary policies, procedures, and technical controls to close them.
Tools like Censinet RiskOps™ can simplify key tasks, such as performing risk assessments, organizing compliance documentation, and comparing your progress to industry benchmarks. It's also crucial to train staff on cybersecurity best practices, keep thorough records of your compliance activities, and set up a process for ongoing monitoring to ensure you stay on track over time.
What does CMMC 2.0 mean for managing sensitive healthcare data tied to the DoD?
CMMC 2.0 establishes a simplified set of cybersecurity standards aimed at protecting sensitive healthcare data tied to the Department of Defense (DoD). This framework ensures that healthcare organizations managing such information adhere to stringent security protocols, safeguarding critical patient details like PHI (Protected Health Information) and clinical records.
Following CMMC 2.0 helps healthcare providers minimize the chances of data breaches, maintain the integrity of their information, and meet the government's cybersecurity expectations. This is particularly important for entities involved in DoD contracts or handling defense-related healthcare data.


