5 Common Mistakes in Vendor Onboarding Security
Post Summary
Vendor onboarding in healthcare is more than just paperwork - it’s a critical step to protect patient data and ensure compliance. Yet, many healthcare organizations make avoidable mistakes that expose them to data breaches, HIPAA violations, and operational risks.
Here are the 5 most common missteps:
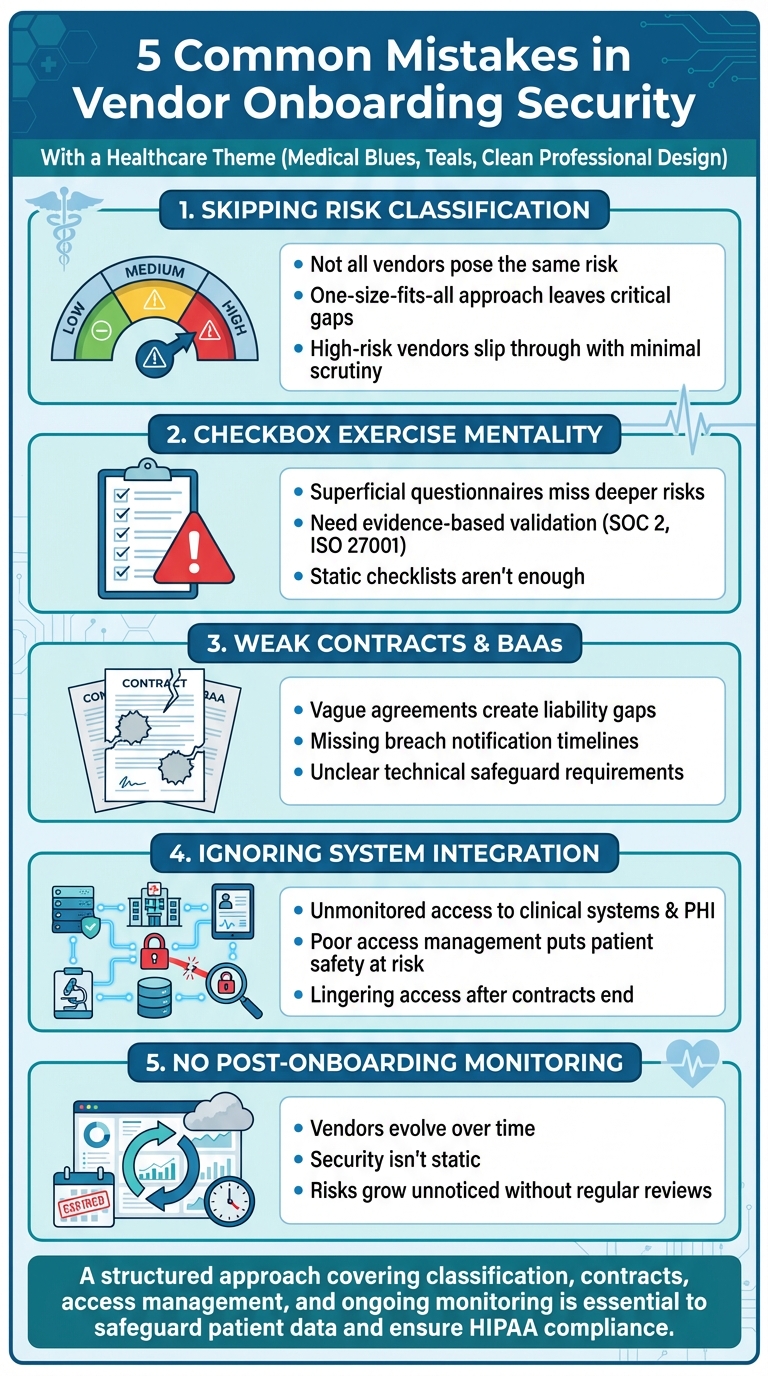
- Skipping Risk Classification: Not all vendors pose the same level of risk. Failing to classify vendors based on their access to sensitive data like PHI leads to wasted resources and missed vulnerabilities.
- Treating Security Reviews as a Checkbox Exercise: Superficial questionnaires don’t uncover hidden risks. Evidence-based assessments and continuous monitoring are essential.
- Weak Contracts and BAAs: Vague agreements leave liability gaps. Contracts must clearly define roles, safeguards, and breach protocols.
- Ignoring System Integration and Access Management: Poor oversight of vendor access to clinical systems and devices creates security gaps.
- No Monitoring After Onboarding: Security isn’t static. Vendors evolve, and without regular reviews, risks grow unnoticed.
Key takeaway: A structured, healthcare-specific approach to vendor security - covering classification, contracts, access management, and ongoing monitoring - is essential to safeguard patient data and ensure compliance.
5 Common Vendor Onboarding Security Mistakes in Healthcare
1. Skipping Risk Classification and Scoping
Not all vendors present the same level of risk. For instance, a vendor managing your electronic health record (EHR) system or handling Protected Health Information (PHI) poses a far greater threat than one supplying office furniture. Despite this, many healthcare organizations adopt a blanket approach during onboarding, applying identical security reviews to every vendor - regardless of the data they handle or the systems they access.
This "one-size-fits-all" method leaves critical gaps. Without formal risk classification, it's impossible to focus security efforts where they're needed most. High-risk vendors might slip through with minimal scrutiny, while low-risk vendors drain resources that could be better allocated elsewhere. This misstep underscores the importance of tailoring vendor onboarding based on risk.
Here's the reality: most healthcare data breaches trace back to vulnerabilities in third-party systems. When healthcare organizations fail to classify vendors by risk, they risk granting excessive access without proper oversight.
Risk classification in healthcare must address industry-specific concerns. Does the vendor have access to PHI? Will they interact with clinical applications or medical devices? Do they process financial data or integrate with your supply chain? Each of these scenarios introduces unique risks tied to patient privacy, clinical workflows, and compliance with HIPAA regulations. For example, a vendor connected to your medical device network could disrupt patient care if their security is compromised - a risk that’s particularly significant in healthcare settings. A well-defined risk profile helps create a targeted security checklist during onboarding.
Equally important is defining the scope of access from the outset. Vendors often request more system access than they actually need to perform their tasks. Without clear boundaries, they may end up with unnecessary access, violating the principle of least privilege. HIPAA and HITECH regulations require that vendors access only the minimum PHI necessary to complete their work.
Risk classification isn’t a one-and-done process. Vendors evolve - they may add services, experience ownership changes, or encounter security incidents. A vendor initially deemed low-risk could later integrate with clinical systems, raising their risk profile. Regular reassessments based on risk tiers are essential, with high-risk vendors requiring more frequent reviews. Tools like Censinet RiskOps™ can provide continuous risk intelligence and simplify ongoing monitoring.
2. Treating Security Reviews as a Checkbox Exercise
Once risk classifications are tailored, it’s crucial to move beyond the superficial act of ticking boxes during security reviews.
Many healthcare organizations rely on basic questionnaires for vendor assessments: “Are you HIPAA compliant?” Check. “Do you encrypt data?” Check. “Do you have a disaster recovery plan?” Check. While this might seem thorough at first glance, it creates only an illusion of security.
The problem with this checkbox approach is that it often misses deeper, more nuanced risks that can lead to breaches or ransomware attacks. For example, a vendor might truthfully claim HIPAA compliance but fail to disclose outdated encryption methods, weak access controls, or the lack of audits for their subcontractors. These hidden vulnerabilities can easily slip through the cracks.
A static checklist simply isn’t enough. Organizations need to adopt rigorous, evidence-based validation processes. Instead of accepting vague assurances, request tangible proof - such as SOC 2 Type II reports, ISO 27001 certifications, or results from recent third-party audits. When handling PHI (Protected Health Information), it’s essential to document critical details: how vendors segregate data, how long they retain it, and the procedures they follow during offboarding.
The Business Associate Agreement (BAA) is another area that demands closer attention. Too often, BAAs are treated as generic documents to sign and file away. However, a well-crafted BAA should outline vendor-specific services, permissible PHI uses, required safeguards, breach notification timelines, and obligations for subcontractors. These agreements must be regularly updated to align with current HIPAA and HITECH standards[2][4][5].
Beyond the initial review, continuous monitoring is key to maintaining security over time. Vendors evolve - they add new services, face security incidents, get acquired, or integrate with additional systems. Contracts should include requirements for ongoing monitoring, continuous scanning, and annual security reviews to address these changes[2]. Tools like Censinet RiskOps™ help healthcare organizations streamline third-party risk assessments and provide continuous risk intelligence.
"Not only did we get rid of spreadsheets, but we have that larger community [of hospitals] to partner and work with."
- James Case, VP & CISO, Baptist Health[1]
3. Weak Contracts and Unclear Business Associate Agreements
Even the most detailed security assessment becomes ineffective if contracts fail to enforce the necessary security measures. Vague vendor agreements and poorly structured Business Associate Agreements (BAAs) often create dangerous liability gaps, leaving healthcare organizations vulnerable to HIPAA violations, enforcement actions by the Office for Civil Rights (OCR), and expensive legal battles. Clear and precise contracts are essential to strengthen the onboarding framework discussed earlier.
Healthcare organizations, as covered entities, bear the ultimate responsibility for ensuring that their business associates protect Protected Health Information (PHI) appropriately. Claiming ignorance or placing sole blame on vendors is not a viable defense when contracts lack strong controls. Well-defined agreements act as a crucial first layer of protection.
Effective risk assessments mean little if contracts don’t require ongoing compliance with approved security measures. Common shortcomings in BAAs include vague or missing breach notification timelines, unclear technical safeguard requirements (like encryption standards, multi-factor authentication, or logging protocols), weak subcontractor oversight, and inadequate procedures for handling PHI at the end of a contract [2][3]. To stay aligned with evolving HIPAA guidelines and emerging threats, organizations must regularly update their BAA templates.
Contracts also need to clearly define shared security responsibilities. Specify roles for tasks such as access provisioning, patch management, incident response coordination, and security monitoring. Include detailed terms for access management, like ensuring the principle of minimum necessary access, using approved secure connection methods, and maintaining specific logging and retention practices. Breach reporting obligations should have strict timelines, require forensic cooperation, and include clear communication protocols [2][3].
Ongoing accountability should be baked into the agreement. For example, require annual security attestations (such as SOC 2 reports, HITRUST certifications, or penetration test results), provide rights for audits or access to assessment reports, and mandate timely remediation of critical vulnerabilities. At the end of a contract, ensure secure data destruction and require vendors to disable access and remove PHI from all backups. This prevents "zombie data" from being exposed in future security incidents [2][3]. Tools like Censinet RiskOps™ can streamline this process by aligning contract templates with the latest risk assessment findings, ensuring that updated control requirements are applied consistently across PHI, clinical applications, and medical devices.
sbb-itb-535baee
4. Ignoring System Integration and Access Management
Even the strongest contracts fall short if vendors gain unmonitored access to clinical systems and protected health information (PHI). Many healthcare organizations rush through technical integration processes without carefully mapping data flows, validating access controls, or understanding how vendor connections interact with patient care systems. This lack of oversight can create hidden vulnerabilities in electronic health records (EHRs), medical devices, and clinical applications - often going unnoticed until a security breach occurs. Such integration gaps pave the way for serious access management failures.
Whenever vendors connect through VPNs, APIs, or direct integrations, each connection becomes a potential weak point for attackers. Without clearly defined boundaries, a billing vendor might accidentally gain access to clinical documentation, or a maintenance contractor could end up with permissions far beyond what their role requires. These unchecked access points not only compound risks tied to insufficient vendor risk assessments but also undermine the safeguards built into contracts.
Poor access management puts both data privacy and patient safety at risk. For example, when vendors integrate with devices like infusion pumps, imaging systems, or lab equipment without thorough security checks, compromised credentials could disrupt clinical workflows or even interfere with device functionality. To prevent this, organizations should enforce multi-factor authentication, implement role-based access controls, and adhere to the principle of least privilege. It’s critical to document exactly which systems vendors can access, what actions they’re authorized to perform, and how long their permissions should remain active.
Another common oversight occurs when vendor relationships end. Organizations often fail to disable accounts, revoke VPN access, or ensure PHI is securely destroyed. This leaves lingering access points in clinical networks, even after contracts have expired. To close these gaps, organizations should follow a detailed checklist that includes disabling vendor accounts, revoking API keys, updating shared credentials, deactivating physical access badges, and confirming data deletion. Tools like Censinet RiskOps™ can simplify this process by centralizing vendor assessments, tracking integrations across EHRs, clinical systems, medical devices, and supply chains, and enabling continuous monitoring throughout the vendor lifecycle[2].
5. No Monitoring or Oversight After Onboarding
One common misstep organizations make is viewing vendor onboarding as a one-and-done process instead of an ongoing partnership. While initial security reviews and contract signings are essential, many healthcare providers mistakenly assume a vendor’s security measures remain static. Unfortunately, research shows that a significant number of healthcare data breaches are linked to third-party vendors. Without continuous monitoring, risks can quietly build across the network, potentially exposing sensitive patient data and violating HIPAA regulations.
Vendors don’t operate in a vacuum - they update software, bring in subcontractors, and face new cybersecurity threats. A vendor that passed security checks six months ago might now have weaker controls, experienced a breach, or expanded access beyond the original agreement. Healthcare organizations are still legally accountable for HIPAA violations caused by their vendors [3][5]. Ignoring ongoing compliance not only heightens risk but also increases exposure to regulatory penalties. The shifting threat landscape demands consistent oversight well beyond the onboarding phase.
To maintain security, organizations need structured post-onboarding protocols. This includes scheduling periodic reassessments, reviewing access controls regularly, and verifying HIPAA compliance on an ongoing basis. Business Associate Agreements (BAAs) should be reviewed annually to ensure they align with current services and subcontractor arrangements [3][5]. Monitoring access logs for unusual activity involving Protected Health Information (PHI) is crucial, as is ensuring vendors promptly report security incidents. Contracts should enforce clear notification timelines for such events [5][6]. Vendors with higher risk profiles - those with direct PHI access, extensive system integrations, or medical device connections - require more frequent evaluations [6].
Manual processes often make continuous monitoring a daunting task. However, healthcare-specific platforms can significantly ease the burden. Just as well-constructed contracts are key during onboarding, using the right tools ensures that these safeguards remain effective over time. For instance, after adopting Censinet RiskOps™, Tower Health reduced its staffing needs from three full-time employees (FTEs) to two while increasing the number of risk assessments. Terry Grogan, CISO at Tower Health, shared:
"Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required." [1]
This example highlights how the right technology can streamline vendor compliance tracking, monitor PHI access, and support regular reassessments - all without overloading security teams. It enables organizations to maintain vendor security throughout the entire relationship lifecycle.
Failing to monitor vendors after onboarding can lead to publicized breaches, damaging a healthcare provider’s reputation and eroding patient trust [5]. By committing to continuous oversight, organizations can identify issues early, hold vendors accountable, and reassure both auditors and leadership that vendor security is actively managed.
Conclusion
Addressing common pitfalls in vendor onboarding with a structured security checklist can significantly enhance protection and simplify vendor management. By tackling issues like risk classification gaps, a checkbox approach, weak contracts, integration oversights, and the lack of post-onboarding monitoring, healthcare organizations can establish a repeatable process that safeguards PHI and ensures smooth clinical operations. The goal is to move away from sporadic vendor reviews and adopt a consistent security checklist integrated into procurement and IT workflows. This ensures every vendor meets the necessary security requirements before accessing systems or handling sensitive patient data.
Embedding the checklist into routine procedures helps procurement validate risk levels and documentation, IT enforce access controls during integrations, and security teams perform regular assessments. A well-rounded checklist that includes risk tiering, due diligence (such as SOC 2, HITRUST, and penetration tests), contract terms, integration protocols, and monitoring schedules lays the groundwork for a strong and sustainable vendor security program. From initial risk classification to ongoing oversight, each step strengthens defenses against emerging threats.
For scaling this approach, purpose-built platforms can be a game-changer. For instance, Censinet RiskOps™ centralizes vendor inventories, questionnaires, Business Associate Agreements, and remediation tasks, while automating risk scoring for similar vendors. James Case, VP & CISO at Baptist Health, highlighted the benefits of this transformation:
"Not only did we get rid of spreadsheets, but we have that larger community [of hospitals] to partner and work with" [1].
This streamlined approach allows security teams to focus on making strategic decisions about risks instead of getting bogged down in chasing documentation.
FAQs
Why is it important to classify risks during vendor onboarding in healthcare?
Classifying risks during vendor onboarding plays a crucial role in healthcare. It allows organizations to pinpoint potential security threats and address them based on their severity. This targeted approach ensures that sensitive patient data is better protected, minimizing the chances of breaches.
By focusing on the most pressing risks, healthcare organizations can put effective security measures in place, stay compliant with industry regulations, and establish more secure vendor relationships. This approach not only safeguards patient trust but also helps uphold the reliability and integrity of healthcare operations.
How can healthcare organizations go beyond basic security checklists during vendor onboarding?
Healthcare organizations have the opportunity to strengthen their defenses by shifting from static security checklists to proactive, ongoing risk management strategies. Rather than depending on one-time assessments, they can utilize tools like AI-driven platforms to enable real-time monitoring, perform automated evaluations, and maintain continuous communication with vendors.
Embedding security into everyday operations not only enhances the protection of sensitive data but also ensures compliance and minimizes risks associated with third-party partnerships. This strategy safeguards patient information, critical systems, and supply chains while promoting a culture that prioritizes ongoing advancements in cybersecurity.
What should a strong Business Associate Agreement (BAA) include?
A well-crafted Business Associate Agreement (BAA) plays a crucial role in ensuring compliance with HIPAA while safeguarding sensitive information. Here are its key components:
- Scope of services: This section outlines, in detail, the services the business associate will provide.
- Confidentiality and security requirements: It specifies the obligations to protect Protected Health Information (PHI) and comply with HIPAA's security rules.
- Breach notification procedures: Clear steps are laid out for promptly reporting and managing any data breaches.
- Access and data management: This includes guidelines for accessing, modifying, or securely deleting data as required.
- Liability and indemnification: It establishes accountability and legal protections for both parties involved.
By including these elements, organizations can better manage risks and ensure their collaborations meet regulatory expectations.


