Edge Computing in Healthcare: Vendor Risk Management for Distributed Processing
Post Summary
Edge computing is changing healthcare by enabling data processing closer to where it's generated - like at hospital bedsides, in ambulances, and within medical devices. This reduces delays in critical care and improves data security by minimizing reliance on distant cloud servers. However, it also introduces new challenges, especially in managing risks associated with third-party vendors who handle sensitive patient data across distributed systems.
Key Takeaways:
- Edge Computing Benefits: Faster data processing in real-time scenarios (e.g., ambulances or wearable devices) and reduced reliance on cloud servers.
- Vendor Risks: Increased attack surfaces, regulatory challenges, and potential operational failures due to reliance on third-party infrastructure.
- Risk Management Strategies:
- Identify and rank vendors by risk level.
- Include strict security requirements in contracts.
- Use tools like AI and Zero Trust to monitor and secure vendor interactions.
Healthcare organizations must take ownership of vendor risk management to protect patient data, ensure compliance, and maintain uninterrupted care. Platforms like Censinet RiskOps™ help streamline this process with automated assessments and real-time monitoring.
Main Challenges in Managing Vendor Risks for Edge Computing
Healthcare Vendor Risk Statistics: Edge Computing Security Challenges
Healthcare organizations grapple with three major challenges when it comes to managing vendors in edge computing: safeguarding patient data, meeting strict regulatory standards, and ensuring uninterrupted operations across extensive device networks. Let's break down these challenges and their impact on healthcare vendors.
Data Security and Privacy Threats
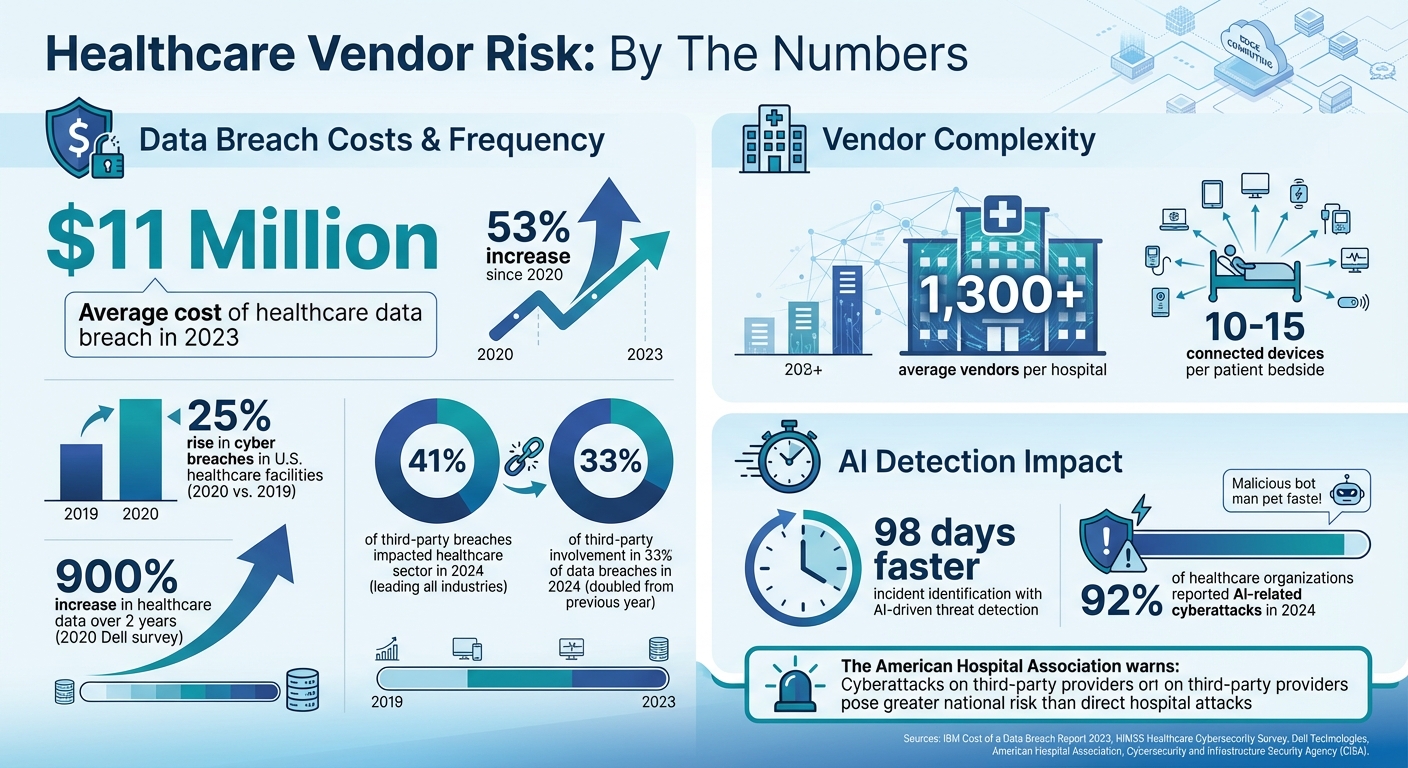
Edge computing's distributed setup creates a vast attack surface, with every edge device acting as a potential gateway for cybercriminals. And the stakes are high - data breaches in healthcare are becoming alarmingly expensive. In 2023, the average cost of a breach hit nearly $11 million, a staggering 53% jump since 2020 [9]. Back in 2020, U.S. healthcare facilities saw a 25% rise in cyber breaches compared to the previous year [8].
One of the toughest hurdles is finding the balance between strong encryption and the need for real-time processing [6]. Vendors must deploy robust authentication systems without hampering critical care applications. The complexity grows when patient data moves across different edge locations, each requiring its own security protocols and access controls. These challenges make it clear how vital thorough vendor risk management is for safeguarding distributed healthcare systems.
Meeting Regulatory and Compliance Requirements
Regulatory compliance becomes a tricky puzzle when patient data flows through multiple regions and vendors [6][7]. Whether it’s a device in an ambulance, a bedside monitor, or a remote clinic, every edge location must meet stringent healthcare regulations. When data crosses state or international borders, additional rules - like GDPR - add another layer of complexity [7][9].
Business Associate Agreements (BAAs), which are often used to define vendor responsibilities, frequently fall short when addressing the nuances of edge computing. To address these gaps, organizations need well-defined data governance strategies. These strategies should outline how vendors must protect data at each edge location [7]. Contracts must also include clear language about security standards, audit rights, and compliance checks tailored to distributed environments [10]. Without clear vendor accountability, managing regulatory obligations in edge computing becomes a daunting task.
Operational Failures and Scalability Issues
The average hospital relies on over 1,300 vendors [4], and in 2024, healthcare led all industries, with 41% of third-party breaches impacting the sector [4]. When vendors face system failures or struggle to scale, the consequences directly affect patient care. The American Hospital Association (AHA) even highlighted how cyberattacks on third-party providers could have broader national repercussions than direct attacks on hospitals [4].
Scalability is another pressing issue, especially with the rapid growth of healthcare data. A 2020 Dell survey reported a 900% increase in healthcare data over just two years, with hospitals now connecting 10 to 15 devices per patient bedside [2]. Vendors must process this enormous data load in real time while ensuring system reliability. Integration challenges - like compatibility issues and data quality problems - can slow down implementations and inflate costs [13]. On top of that, Denial of Service (DoS) attacks targeting edge devices can completely shut them down, disrupting critical healthcare operations [12]. These operational risks highlight the importance of a solid vendor risk management framework to keep healthcare services running smoothly.
Using Censinet RiskOps™ for Vendor Risk Management
Tackling vendor risks in healthcare - especially in edge computing environments - demands a centralized, efficient approach. The Censinet RiskOps™ platform brings vendor risk assessments and real-time monitoring together in one place. This integrated system is designed to address the complexities of securing medical devices, clinical applications, and PHI across multiple locations. Let’s explore how Censinet Connect™ and Censinet AI™ make vendor risk management easier and more effective.
Simplifying Vendor Assessments with Censinet Connect™
Censinet Connect™ streamlines the vendor evaluation process by creating a standardized way for vendors to submit their security documentation. This consistent, collaborative workflow eliminates delays caused by mismatched formats and miscommunication. With this system in place, healthcare organizations can onboard vendors faster and gain a clearer understanding of each vendor's security practices.
Automating Risk Analysis with Censinet AI™
Censinet AI™ takes automation to the next level by summarizing vendor-provided evidence and identifying potential risks. While routine tasks are handled automatically, human oversight ensures that complex decisions remain in expert hands. The platform’s configurable rules and integrated dashboards route critical findings for further review, enabling scalable and efficient risk management. This is especially important in dynamic environments where processing is distributed across various locations.
Practical Strategies for Managing Vendor Risks in Edge Computing
Effectively managing vendor risks in edge computing goes beyond initial evaluations - it requires a structured, ongoing approach to ensure the security of edge deployments. Building on the challenges of vendor risks outlined earlier, these strategies help maintain strong oversight of vendors. Healthcare organizations, in particular, must identify every third-party vendor interacting with their edge infrastructure and establish ongoing monitoring systems. The process starts by pinpointing the vendors that are most critical to patient care and operational stability. From there, organizations can layer protections through well-constructed contracts and continuous oversight. This approach helps prioritize vendor risks in an environment where distributed processing and rapid data flows increase exposure to vulnerabilities.
Categorizing Vendors by Risk Level
Start by creating a comprehensive inventory of all third-party vendors involved in your edge computing environment. Once the list is complete, rank vendors based on their importance to healthcare operations, patient care, and revenue. This allows you to focus resources on those vendors posing the highest risks.
"Identifying the third-party vendors and prioritizing them based on criticality enables the HDO to focus its efforts consistent with its risk management strategy based on business needs. Implementing processes to identify new third parties and changes to existing third parties is the first step in developing a risk management program. Once all third-party vendors have been identified, the HDO should risk-rank the vendors to identify the criticality of the vendor." - Cloud Security Alliance [11]
Establish clear criteria for evaluating vendor risks. Consider factors like financial stability, HIPAA compliance, data security measures, and operational capabilities related to distributed edge data processing. Require vendors to submit essential security documentation and assign scores based on two factors: the likelihood of a risk event (like a data breach or operational failure) and the potential impact of such an event. Engage cross-functional teams to ensure diverse perspectives are included in the risk assessment process.
Once high-risk vendors are identified, the next step is to incorporate strict security requirements into vendor contracts.
Setting Security Requirements in Vendor Contracts
The contracting phase is your best opportunity to set firm security expectations. Include mandatory security standards that vendors must meet. With third-party involvement in nearly one-third of data breaches in 2024 - double the rate from the previous year [14] - this step is more critical than ever.
Require vendors to maintain certifications like SOC 2, ISO 27001, or HITRUST, and clearly outline liability in the event of a security breach. The HIPAA Security Rule is undergoing updates in 2024, which will eliminate the distinction between "required" and "addressable" controls, making more controls mandatory. These updates also introduce requirements for annual compliance audits and address emerging risks tied to AI and quantum computing [14].
"This isn't about mistrusting vendors. It's about building transparent, accountable partnerships where both sides are committed to security." - Steve Ryan, Senior Manager of BARR's attest services practice and head of BARR's healthcare services [14]
Ongoing Monitoring and Performance Reviews
Continuous monitoring is essential for maintaining real-time visibility into vendor performance and security within your edge network. Regular reviews help prevent human error and allow organizations to concentrate on the most critical vendor relationships. Track key performance indicators (KPIs) to measure vendor performance and identify deviations from agreed-upon objectives.
Develop a Plan of Action and Milestones (POA&M) to track and address vendor-related risks over time. This ensures that security gaps are resolved systematically [4]. Include third-party vendors in your core cybersecurity initiatives, such as incident response plans, disaster recovery tests, and business continuity planning. Establish clear communication protocols for emergencies so every stakeholder knows their role when threats arise.
Additionally, monitor vendor access to systems to detect unusual activity and regularly reassess vendors managing critical edge infrastructure. This proactive approach ensures compliance with federal regulations and internal policies while adapting to the evolving risks associated with distributed processing environments.
sbb-itb-535baee
Using AI and Zero Trust for Scalable Risk Management
Managing vendor risks in distributed edge computing environments is no small feat. The sheer volume of data and rapid pace of threats in healthcare networks make manual approaches impractical. This is where AI-powered monitoring and Zero Trust security frameworks step in. Together, they automate risk detection and enforce strict access controls across all vendor interactions, creating a layered security strategy. These tools not only adapt to the complexities of edge computing but also provide the visibility healthcare organizations need to safeguard patient data and clinical operations. They build upon earlier discussions on vendor risk controls, offering scalable, automated solutions and continuous access verification.
Real-Time Risk Monitoring with AI Dashboards
AI has transformed how healthcare organizations manage vendor risks, especially in edge environments where hundreds or even thousands of devices generate constant data streams. By analyzing these massive data sets, AI-powered tools can detect threats in real time, delivering actionable alerts and even predicting potential risks before they escalate. This kind of automation is a game-changer for healthcare IT teams.
The numbers speak volumes. AI-driven threat detection systems have reduced incident identification times by as much as 98 days compared to traditional methods [15]. This speed is critical, especially when 92% of healthcare organizations reported AI-related cyberattacks in 2024 [15]. AI/ML-powered observability platforms provide a unified view of hybrid infrastructures, automatically highlighting and prioritizing critical security issues across edge devices, cloud systems, and application layers [3].
"An important benefit of observability is that it automatically prioritizes and surfaces real problems, whether they're at the edge; in the cloud; or within web applications, networks or databases. This way, IT pros can make more informed decisions." - HealthTech Magazine [3]
Take Censinet RiskOps™ with Censinet AI™, for example. This platform offers real-time visibility via an intuitive AI risk dashboard that consolidates assessment findings and routes urgent tasks to the right stakeholders. Acting as a central hub for AI-related policies, risks, and tasks, it ensures risk teams stay informed while automation handles routine monitoring. AI also excels at spotting early warning signs of anomalies in vendor systems, enabling predictive maintenance and proactive interventions before small issues lead to major disruptions [8].
Applying Zero Trust Principles to Vendor Access
While AI excels at detecting threats, Zero Trust strengthens security by continuously verifying vendor interactions. The core principle of Zero Trust is simple: never trust, always verify [1]. This approach is particularly important for edge computing, where vendors require access to distributed systems but should never have unrestricted network privileges. Instead of relying on initial authentication alone, Zero Trust continuously reassesses trust every time an account attempts to access additional data or resources [1].
Granular access policies are key here. Tools like Identity and Access Management (IAM) and Secure Access Service Edge (SASE) solutions, including Zero Trust Network Access (ZTNA), ensure vendors only access the specific systems they need [1].
User and Entity Behavior Analytics (UEBA) adds another layer of security by monitoring vendor account behavior in real time. For instance, if a wearable sensor’s service account logs in from an unusual location, UEBA can block access and trigger a re-verification process through IAM. This might involve sending a text to the patient’s verified mobile phone to confirm the device's location. If the location isn't verified, the account's password can be reset to prevent unauthorized access to sensitive patient data or lateral movement within the hospital network [1].
Zero Trust also limits what edge devices can do once connected. For example, when an edge device sends data analytics to the main hospital network, ZTNA verifies its identity and grants access only to the requested resources. The device is completely isolated from other network resources, reducing the risk of a broader attack [1]. This granular control is essential, as even minor tampering could lead to diagnostic errors or treatment failures [15].
Conclusion
Edge computing is reshaping how healthcare is delivered, but it also magnifies the risks tied to third-party vendors. With hospitals relying on an average of over 1,300 vendors and a substantial number of breaches involving third parties [4], the potential attack surface has never been larger. Vendors play a critical role in both operational systems and patient care. When a vendor’s security fails, the ripple effects can go far beyond data breaches, potentially disrupting life-saving equipment and putting patient safety at risk. This heightened threat environment calls for stronger risk management strategies to secure every connection.
To address these challenges, healthcare organizations must adopt comprehensive vendor risk management practices. They are fully responsible for their cybersecurity posture, including the actions of every vendor handling Protected Health Information (PHI) [5]. This means implementing frameworks designed to identify, protect, detect, respond to, and recover from potential third-party vulnerabilities [11], all while maintaining compliance with regulations like HIPAA.
Censinet RiskOps™ offers a streamlined approach to managing vendor risks. By leveraging AI, the platform simplifies tasks like completing questionnaires, validating evidence, and flagging critical findings for review through an intuitive AI-powered risk dashboard. This blend of automation and human oversight helps risk teams scale their efforts without losing the attention to detail required to uphold patient safety. With tools like real-time monitoring, automated workflows, and collaborative features such as Censinet Connect™, organizations can reduce risks more effectively while staying compliant. These tools work alongside existing risk management frameworks, automating vendor assessments and strengthening compliance efforts.
Effective vendor risk management goes far beyond checking boxes. Patient data is an incredibly lucrative target for cybercriminals due to its wealth of personal, medical, and financial information [4]. As third-party security incidents continue to rise [11], healthcare organizations must adapt to the fast-paced, complex reality of edge computing. Prioritizing critical vendors, enforcing strict security requirements in contracts, and utilizing AI-driven monitoring are essential steps to safeguard patient care and ensure operational stability.
FAQs
How does edge computing enhance data security in healthcare?
Edge computing plays a crucial role in boosting data security within healthcare by handling sensitive patient information directly on-site, within the healthcare facility's network. By keeping data processing local, it reduces the need to send information over the internet, which significantly lowers the risk of interception and helps meet strict regulations like HIPAA.
Healthcare organizations can also strengthen their defenses with tools like zero trust architecture, network segmentation, and real-time threat monitoring. These measures are designed to identify and address cybersecurity threats quickly, protecting patient data while ensuring the smooth operation of healthcare systems.
What are the key challenges of managing vendor risks in edge computing for healthcare?
Managing vendor risks in edge computing for healthcare comes with its fair share of hurdles. A major issue revolves around cybersecurity - with numerous devices and access points in play, the risk of breaches is high if security measures aren’t up to par. Another critical factor is ensuring interoperability among the wide variety of devices and systems, which is key for smooth data exchange and processing.
On top of that, edge devices often face tough conditions, so their durability becomes a priority. Keeping these devices from overheating is another challenge, making thermal performance management essential. To stay ahead of these risks, conducting detailed vendor risk assessments and maintaining constant monitoring are non-negotiable. These steps help identify weaknesses, ensure compliance, and keep operations running smoothly.
How do AI and Zero Trust improve vendor risk management in healthcare?
AI plays a powerful role in improving vendor risk management within healthcare. It enables real-time threat detection, continuous monitoring, and automated risk assessments. These tools allow organizations to quickly spot vulnerabilities and stay aligned with strict healthcare regulations.
Zero Trust takes security up a notch by enforcing verification for every access request, minimizing insider threats, and segmenting networks to reduce attack surfaces. When combined, AI and Zero Trust provide healthcare organizations with stronger protection for sensitive data and help ensure smooth operations when dealing with third-party vendors.


