How to Encrypt Vendor Communications in Healthcare
Post Summary
Healthcare organizations handle sensitive patient data daily, making encryption a critical tool to secure communications with vendors. Encryption protects electronic protected health information (ePHI) from breaches, ensures HIPAA compliance, and safeguards patient trust. Here’s a quick summary of how to secure these communications effectively:
- Understand communication channels: Identify how vendors exchange data (email, APIs, file transfers, etc.) and assess the sensitivity of the information shared.
- Use strong encryption standards: Implement AES-256 for data at rest and TLS 1.2/1.3 for data in transit.
- Establish a vendor inventory: Track all vendors, their communication methods, and encryption practices.
- Set risk-based controls: Apply encryption measures based on data sensitivity and business impact.
- Monitor and audit regularly: Ensure encryption protocols are consistently followed and updated as needed.
- Train your team: Educate staff on secure communication practices to prevent accidental breaches.
Encryption isn’t optional - it’s a necessary step to protect patient data and meet regulatory requirements. The article below breaks down these steps in detail, offering actionable guidance for healthcare organizations.
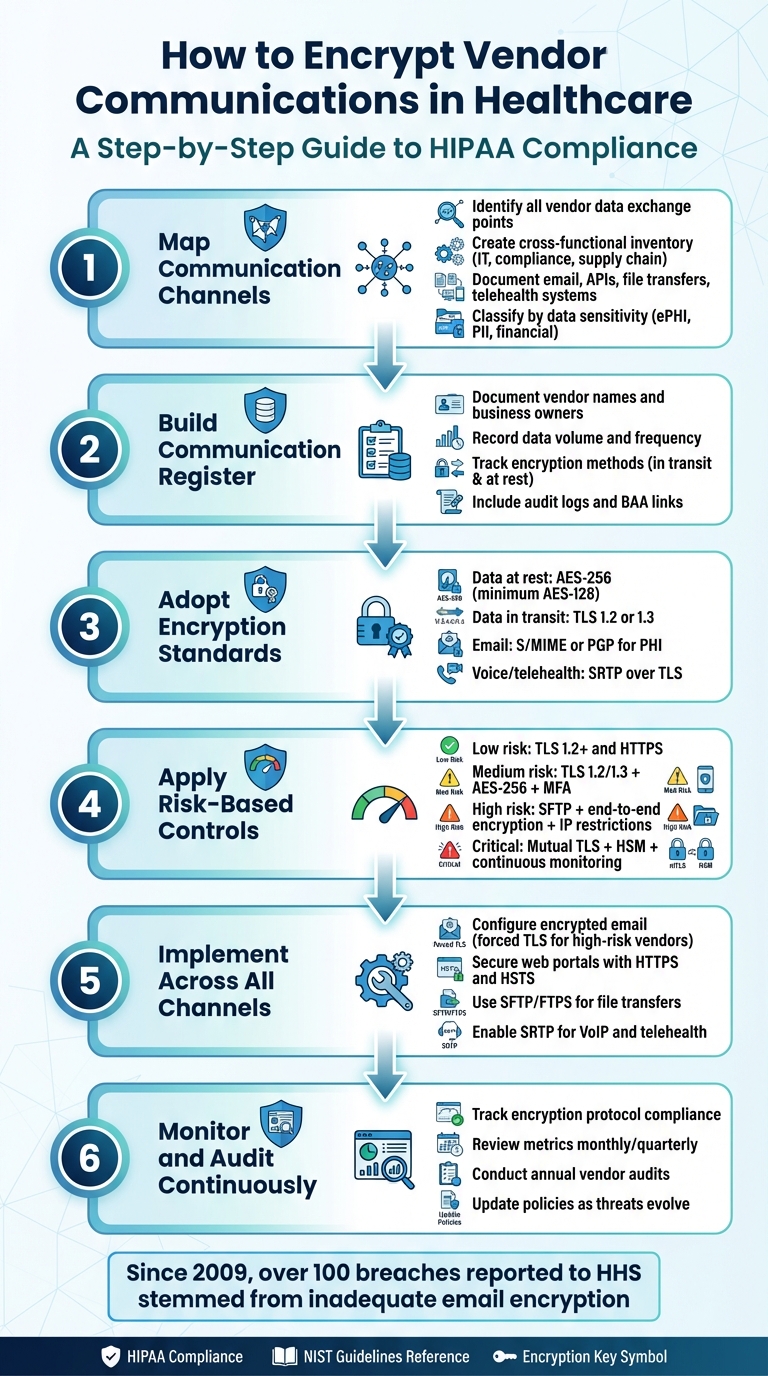
6-Step Process to Encrypt Healthcare Vendor Communications
Mapping Vendor Communication Channels and Data Flows
Identifying Communication Channels and Vendors
To get started, create a cross-functional inventory that involves leaders from IT security, compliance, privacy, supply chain, and clinical departments. Use data from procurement, accounts payable, and EHR integration lists to identify all vendors connected to PHI. This should include specialized cloud applications and device manufacturers. For each vendor, list the primary communication channels they use, such as email, secure file transfers, APIs, messaging platforms, VoIP, telehealth systems, or encrypted data carriers. Clearly document which party controls each channel.
Once you have this list, classify each vendor-channel pair based on data sensitivity and business importance. Note whether the channel handles ePHI, de-identified data, other personally identifiable information, financial data, or administrative content. Assess the volume of PHI being transferred (low, medium, or high) and assign a criticality score. For example, channels supporting clinical care or life-safety functions - like real-time EHR integrations or telehealth platforms managing hundreds of visits daily - should be marked as high priority. This classification helps you focus on where stronger encryption and tighter controls are needed. By completing this detailed inventory, you’ll have the foundation for creating a comprehensive communication register.
Creating a Communication and Data Flow Register
With the vendor channels identified, consolidate this information into a communication and data flow register. This register is essential for making informed encryption decisions and maintaining HIPAA compliance. For each vendor and communication channel, include the following details:
- Vendor name and business owner
- Data exchange volume and frequency (e.g., daily batch files, periodic emails)
- Systems and locations involved (source systems, middleware, vendor systems, and hosting locations)
Also, document the encryption methods used for data in transit (e.g., TLS, HTTPS, VPN, or SRTP) and at rest (e.g., database encryption, disk encryption, or encrypted backups). Include authentication and access controls like SAML, MFA, or role-based access, as well as audit logging capabilities, retention periods, and links to contracts or Business Associate Agreements. Make sure to note the date of the last security or risk assessment for each channel.
Organize the register so each data flow aligns with HIPAA Security Rule safeguards for transmission security and access control. Add fields for compliance with NIST guidelines and include a last-review date with the reviewer’s name to ensure regular updates. If encryption isn’t in place for a specific channel, document any compensating controls and any formal risk acceptance according to HIPAA’s "addressable" encryption standard. This level of detail will not only support audits but also help refine your encryption strategy and quickly identify unencrypted segments needing attention.
To streamline this process, platforms like Censinet RiskOps™ can centralize vendor inventories, data flow records, and risk assessments into a single cloud-based system. As Matt Christensen, Sr. Director GRC at Intermountain Health, explains:
"Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare" [1].
Choosing and Implementing Encryption Standards
Encryption Standards for Healthcare
Once communication channels are mapped, the next priority is to establish standardized encryption protocols. Under HIPAA, encryption is considered "addressable", meaning it should be implemented when a risk analysis deems it necessary, or an equivalent alternative must be documented. That said, encrypting all electronic protected health information (ePHI) - whether in transit or at rest - has become a widely accepted practice. While HIPAA doesn’t mandate specific algorithms, healthcare organizations often rely on NIST cryptographic guidance to meet compliance requirements and avoid penalties for breaches.
For data at rest, such as databases, file servers, backups, or email archives, encryption using AES-256 is recommended, with AES-128 as the minimum standard. As noted by SecurityMetrics, "industry best practice would be to use AES-128, AES-256, or better" to safeguard medical data, with AES-256 offering the highest level of protection. Similarly, when securing data in transit, robust protocols are essential. Adopt TLS 1.2 or 1.3 with modern cipher suites for all web portals, APIs, and email connections, and ensure older protocols like SSL and TLS 1.0/1.1 are fully disabled.
When it comes to email encryption, a layered approach is often necessary. For lower-risk communications between managed email systems, TLS-only encryption between mail servers may suffice. However, for emails containing PHI, enforce end-to-end encryption using S/MIME or PGP. Most email platforms already utilize AES for storage and TLS for transmission. For voice and telehealth communications involving PHI, choose vendors that support VoIP encryption through SRTP over TLS and maintain detailed audit logs. Secure messaging solutions designed for HIPAA compliance typically include end-to-end encryption, role-based access controls, and built-in logging.
Developing a Risk-Based Encryption Strategy
To ensure encryption efforts are aligned with organizational needs, create risk tiers - such as low, medium, high, and critical - based on factors like PHI sensitivity, data volume, and potential business impact. Then assign encryption controls accordingly.
- Low-risk scenarios, such as scheduling notifications sent to a vendor’s managed system, can be secured with TLS 1.2+ for email and HTTPS with AES encryption for data at rest.
- Medium-risk scenarios, like claims data shared with billing vendors via secure portals, require stronger measures, including TLS 1.2/1.3, robust authentication, AES-256 for data at rest, and periodic security reviews.
For high-risk communications - such as clinical notes, imaging files, lab results, or large-scale PHI exchanges - heightened controls are essential. Use SSH-based SFTP for file transfers, enforce AES-256 encryption at rest, implement IP restrictions, require multi-factor authentication (MFA), and adopt end-to-end encryption for emails.
In critical scenarios - like real-time clinical integrations or life-safety functions - additional layers of security are necessary. These include mutual TLS authentication, hardware security modules for managing encryption keys, continuous monitoring, and pre-established incident response plans. Clearly document these requirements in a written policy to ensure encryption practices are consistent and auditable across all vendor relationships.
To meet HIPAA requirements, combine encryption measures with access controls, MFA, audit logs, and vendor business associate agreements (BAAs). Update vendor contracts to specify minimum standards, such as AES-256 and TLS 1.2+, for any vendor handling ePHI. Regularly test vendor endpoints with TLS scanning tools and maintain a compatibility matrix to track which vendors support TLS 1.3 or stronger cipher suites. This risk-based approach ensures appropriate protection for each communication channel, balancing the need for robust security with practical implementation for lower-risk scenarios. These measures set the stage for securely managing vendor communications, as outlined in the next section.
Step-by-Step Guide to Encrypt Vendor Communications
Once you've established your encryption standards and identified risk tiers, it's time to implement these measures across all vendor communication channels. This guide builds on your earlier groundwork, showing how to secure systems and ensure compliance in every interaction with vendors.
Configuring Encrypted Email Communication
Start by aligning your email setup with your risk-based strategy. For vendors handling sensitive data like PHI (Protected Health Information), configure your email gateway or cloud email service to require TLS 1.2 or higher for all inbound and outbound connections. Use opportunistic TLS as a baseline, but enforce forced TLS for high-risk vendors such as billing companies, clearinghouses, or cloud EHR providers. Forced TLS ensures that emails are rejected if the vendor's mail server can't establish a secure connection, eliminating the risk of unencrypted PHI transmission.
For highly sensitive data - think clinical notes, mental health records, or financial information - implement S/MIME or PGP encryption. This provides end-to-end encryption, securing both messages and attachments beyond just server-to-server communication. To further strengthen your email policies, align encryption rules with HIPAA risk assessments. Use content-based policies and data loss prevention (DLP) rules to automatically trigger encryption for emails containing PHI indicators. You can also set up manual triggers for encryption by using specific keywords or labels like "Secure: Vendor PHI."
Staff training is key. Educate your team to avoid sending PHI through unencrypted channels. For vendors with limited email capabilities, consider using secure email portals. These portals store content safely in an encrypted web interface while notifying recipients via standard email. Additionally, ensure that email data at rest - whether on servers, backups, or mobile devices - is encrypted using methods like full-disk encryption. Regularly audit and log encryption events, such as unencrypted transmissions or TLS downgrade attempts, to identify and address gaps.
With email secured, apply the same level of attention to your web portals, APIs, and file transfer systems.
Securing Web Portals, APIs, and File Transfers
All patient- and vendor-facing web portals should exclusively use HTTPS with TLS 1.2 or 1.3. Disable weak protocols and ciphers, use certificates from trusted authorities, and enable automated renewals. To prevent security risks like downgrade attacks or man-in-the-middle threats, enforce HTTP Strict Transport Security (HSTS) and redirect all HTTP traffic to HTTPS.
For vendor APIs, such as those used in EHR integrations or scheduling tools, require TLS and strong authentication methods like OAuth 2.0 with scoped access tokens, mutual TLS (mTLS), or signed JSON Web Tokens (JWTs). Document API data contracts to clearly define the PHI elements transmitted, encryption requirements, and logging expectations. Conduct integration testing and periodic reviews to ensure vendor compliance.
When transferring files containing PHI, abandon outdated methods like plain FTP or unsecured email attachments. Instead, use secure file transfer protocols like SFTP (SSH File Transfer Protocol) or FTPS (FTP over TLS). Strengthen these systems with AES-256 encryption, key-based authentication, or multi-factor authentication. To further secure file transfers, place managed file transfer (MFT) servers in isolated network segments protected by strict firewall rules. Limit vendor access to specific directories or IP ranges, and automate workflows to encrypt files at rest and during transfer. For additional security, consider encrypting files individually (e.g., using encrypted zip archives) before transfer. For ad hoc file sharing, standardize on HIPAA-compliant platforms that provide end-to-end encryption, expiration dates, download limits, and detailed audit trails.
Encrypting Voice, Messaging, and Telehealth Channels
Voice and telehealth communications also require robust encryption. For VoIP and SIP trunking with vendors like outsourced contact centers or telehealth providers, configure SIP signaling over TLS and media streams over SRTP (Secure Real-Time Transport Protocol). This protects both call setup and audio from interception. Use session border controllers (SBCs) to inspect external SIP connections, enforce encryption policies, and block unencrypted RTP traffic. Ensure telehealth platforms support encrypted video and audio using TLS for signaling and SRTP for media. Additionally, secure business associate agreements to address PHI shared during calls or video sessions. Validate encryption settings through test calls and vendor security assessments.
For messaging and collaboration, choose platforms that are HIPAA-compliant and offer end-to-end encryption, role-based access controls, and audit trails. Avoid standard SMS or consumer messaging apps for PHI-related conversations. If SMS must be used, document and mitigate the risks - such as limiting the data shared and obtaining patient consent for notifications. Messaging platforms should encrypt data both in transit and at rest. Enforce device-level security measures like PINs, biometrics, remote wipe capabilities, and auto-lock features on mobile devices used for communication. Integrate these tools with directory services like single sign-on (SSO) to streamline access control and ensure prompt deprovisioning when vendor contracts end or staff roles change.
sbb-itb-535baee
Governance and Continuous Improvement of Encryption Practices
Setting up encryption is just the first step. For healthcare organizations, maintaining effective encryption practices requires a structured governance framework. This framework ensures that vendor encryption practices stay compliant, effective, and resilient against new threats. To achieve this, organizations should define clear ownership - typically assigning responsibility to the CISO or Security Officer - and outline roles for creating, implementing, and overseeing encryption policies. This governance should explicitly cover all communications involving ePHI or regulated data, such as email, secure messaging, APIs, telehealth, and file transfers. Without a formal structure, encryption practices can degrade over time. This governance effort also ties in seamlessly with vendor risk assessments, which are discussed later.
Establishing Policies and Standards
Building on previously defined encryption risk tiers, formal policies help ensure consistent application across vendors. These policies should integrate HIPAA and NIST requirements into actionable technical guidelines that vendors can follow and your team can enforce. For example, the HIPAA Security Rule includes "addressable" encryption specifications for access control and transmission security, while NIST SP 800-53 and SP 800-52/57 provide standards for encryption algorithms, key management, and TLS configurations. Policies should clearly outline when encryption is mandatory - like for external emails containing PHI, vendor portals handling ePHI, and file transfers - and define standards such as certificate validation, encryption protocols, and endpoint security measures like multi-factor authentication (MFA) and role-based access.
To make these policies practical, include real-world examples of how to implement them. For instance, provide instructions for configuring email DLP and encryption rules, VPN requirements for SFTP, and approved secure messaging platforms. Map each requirement to specific HIPAA and NIST clauses so vendors understand the regulatory basis. For cases where vendors cannot fully meet the standards, establish a process for documenting exceptions and compensating controls, with leadership approval required. Administrative standards should also specify controls like MFA, audit logs, and automatic logoff for systems handling PHI, ensuring these requirements are embedded in contracts and Business Associate Agreements (BAAs). Keep in mind that HIPAA treats encryption as "addressable", meaning you must either implement it or document a valid alternative. For vendor communications involving PHI, unencrypted data is a major risk that has led to civil monetary penalties from HHS in the past.
Monitoring and Auditing Encrypted Communications
Once encryption is in place, continuous monitoring is essential to maintain compliance and detect issues before they lead to breaches. This involves both technical monitoring and compliance reviews. Key metrics to track include the percentage of vendor traffic using approved encryption protocols (e.g., TLS 1.2+), failure rates for secure connections, the number of emails auto-encrypted by policy, exceptions granted, and unresolved findings from audits. Logs should capture authentication events, transmissions, file transfers, and API calls to detail who accessed PHI and when - aligning with HIPAA's audit control requirements.
To support monitoring, use tools like secure email gateways with DLP, API gateways, log aggregation or SIEM platforms, and secure messaging systems with built-in audit trails. Review metrics monthly or quarterly, setting thresholds for alerts - such as detecting unencrypted PHI in emails or downgrades in TLS strength. Common issues uncovered during monitoring might include vendors using outdated protocols like TLS 1.0/1.1, email systems relying on basic TLS without enforced encryption for PHI, incomplete audit logs for secure messaging, inconsistent MFA usage, or unencrypted file transfers via ad hoc methods like email attachments instead of approved SFTP.
Your audit program should combine scheduled, risk-based reviews with event-driven assessments. Onboarding audits verify that vendors meet encryption requirements, such as AES for stored PHI, TLS for data in transit, end-to-end encryption, MFA, and role-based access. Periodic audits (annually for high-risk vendors) should examine technical evidence like configuration screenshots, penetration test results, SOC 2 or HITRUST reports, and logs showing encrypted sessions. Process audits should check that BAAs reflect encryption obligations, staff training is current, and incident response plans cover breaches involving encrypted channels. If gaps are found - like weak ciphers or missing audit logs - issue formal findings with risk ratings and deadlines for remediation, followed by verification to close the loop. Audit outcomes should feed into vendor risk scores and influence contract renewal, tiering, and compensating measures.
Using Censinet RiskOps™ for Vendor Risk Management

Bringing vendor risk assessments into your governance framework ensures a unified approach to encryption. Censinet RiskOps™ simplifies this process by centralizing third-party risk assessments with standardized questionnaires and workflows that capture vendors' encryption practices across email, messaging, APIs, storage, and backups. Healthcare organizations can tailor assessments to align with HIPAA and NIST guidelines, asking about algorithms (e.g., AES-256, TLS versions), key management, audit logs, and incident response for encrypted data. The platform allows risk owners to review vendor responses, attach evidence like SOC reports or penetration tests, and generate risk scores that factor in encryption maturity. This helps quickly identify vendors with weak or missing encryption controls, prioritizing them for remediation instead of relying on scattered spreadsheets or emails.
When encryption gaps are found - such as outdated TLS configurations or missing end-to-end encryption - Censinet RiskOps™ creates remediation tasks tied to specific findings and tracks their resolution through a centralized dashboard. This ensures healthcare organizations can enforce corrective actions within set timelines and monitor progress across their vendor portfolio. As vendors address issues, updated documentation and evidence can be uploaded and reviewed within the platform, improving their risk profile over time. Aggregated analytics from Censinet can also reveal systemic challenges, like frequent issues with secure messaging or file transfers, guiding leadership to make targeted investments or policy adjustments that strengthen encryption practices across all vendors.
"Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required." - Terry Grogan, CISO, Tower Health
"Not only did we get rid of spreadsheets, but we have that larger community [of hospitals] to partner and work with." - James Case, VP & CISO, Baptist Health
Continuous improvement relies on using operational data to refine governance. Trends from monitoring - such as recurring encryption misconfigurations or frequent use of unencrypted channels - and audit findings can inform updates to policies and minimum requirements. For example, you might mandate TLS 1.2+ across all vendors, clarify expectations in BAAs, or enhance onboarding checklists. Insights from Censinet RiskOps™, like common control failures or average time-to-remediate, can help prioritize automation, training, or standard configurations. Regular risk analyses should assess encryption across all major communication channels (email, messaging, telehealth, file transfer, APIs, voice/SMS). A change management process should evaluate new vendors, tools, and integrations for encryption compliance before they go live. Additionally, encryption policies should be reviewed and updated annually or as regulations, NIST guidance, or threats evolve. Ongoing workforce training is also crucial to ensure staff know how to use encrypted channels, avoid non-compliant tools, and report potential lapses effectively.
Conclusion
Encrypting vendor communications isn't just a good practice - it's a requirement under HIPAA to safeguard Protected Health Information (PHI). Since 2009, over 100 breaches reported to the Department of Health and Human Services (HHS) have stemmed from inadequate email encryption [2]. With healthcare data being highly valuable on the dark web, any unencrypted email, file transfer, or messaging platform becomes a potential vulnerability for attackers.
Encryption not only protects PHI but also fosters vendor trust and simplifies onboarding. By using robust encryption protocols like AES-256 and TLS 1.2/1.3, and ensuring all access is logged and audited, organizations can collaborate securely with vendors. This reduces the likelihood of PHI exposure, minimizes emergency exceptions, and builds stronger, more productive partnerships over time. A secure foundation like this paves the way for smoother vendor operations.
From an operational perspective, embedding encryption into daily workflows reduces the need for manual workarounds and eliminates reliance on insecure tools like personal email accounts or consumer messaging apps. Solutions such as Censinet RiskOps™ help streamline risk management by verifying encryption practices across the vendor network, ensuring secure and compliant communication channels.
The strategies discussed earlier emphasize that encryption should be treated as an ongoing effort, not a one-time fix. As threats and technologies change, healthcare organizations must remain proactive. Regular risk assessments, updated policies aligned with NIST guidelines, continuous monitoring, and comprehensive workforce training are essential to keeping encryption effective. With strong technical controls and sound governance in place, organizations can protect PHI, maintain regulatory compliance, and ensure operational stability in an ever-evolving threat landscape.
FAQs
What are the best practices for securing vendor communication channels in healthcare?
To protect communication channels with vendors in healthcare, start by pinpointing all the ways you exchange information - this includes email, phone calls, messaging apps, and online portals. Once identified, organize these channels by their purpose and the sensitivity of the data they handle. From there, evaluate the security risks tied to each channel and take steps to address vulnerabilities. For instance, encryption should be a priority to safeguard sensitive details like patient records and to stay aligned with healthcare regulations.
Tools like Censinet RiskOps™ can make risk assessments easier and help establish secure communication workflows designed specifically for healthcare needs. It's also important to regularly revisit and update your communication framework to account for new tools, evolving threats, or changes in your vendor partnerships.
What steps can healthcare organizations take to meet HIPAA and NIST encryption standards?
Healthcare organizations can align with HIPAA and NIST encryption standards by using encryption tools tailored for healthcare compliance, conducting frequent risk assessments, and keeping thorough records of all encryption practices. Equally important is educating staff on encryption policies and staying informed about updates to these regulations.
Platforms like Censinet RiskOps™ can simplify risk management, help enforce encryption protocols, and monitor compliance effectively. By integrating the right technology, structured processes, and comprehensive training, organizations can safeguard sensitive patient information while meeting regulatory requirements.
How can healthcare organizations ensure secure and up-to-date encryption practices with vendors?
Healthcare organizations must take an active role in ensuring their encryption practices with vendors remain secure and current. This means consistently reviewing and updating encryption protocols to match the latest industry standards and address new threats. Incorporating regular vulnerability assessments and real-time monitoring tools can help spot risks before they become serious issues.
Building strong partnerships with vendors is equally important. Work closely with them to ensure they meet your security requirements. Offer ongoing training and maintain open communication to keep them informed about changes in encryption practices and compliance needs. Creating an environment of continuous improvement not only strengthens data protection but also enhances vendor relationships over time.


