FDA Medical Device Vendor Compliance: Third-Party Risk Management Best Practices
Post Summary
<article>
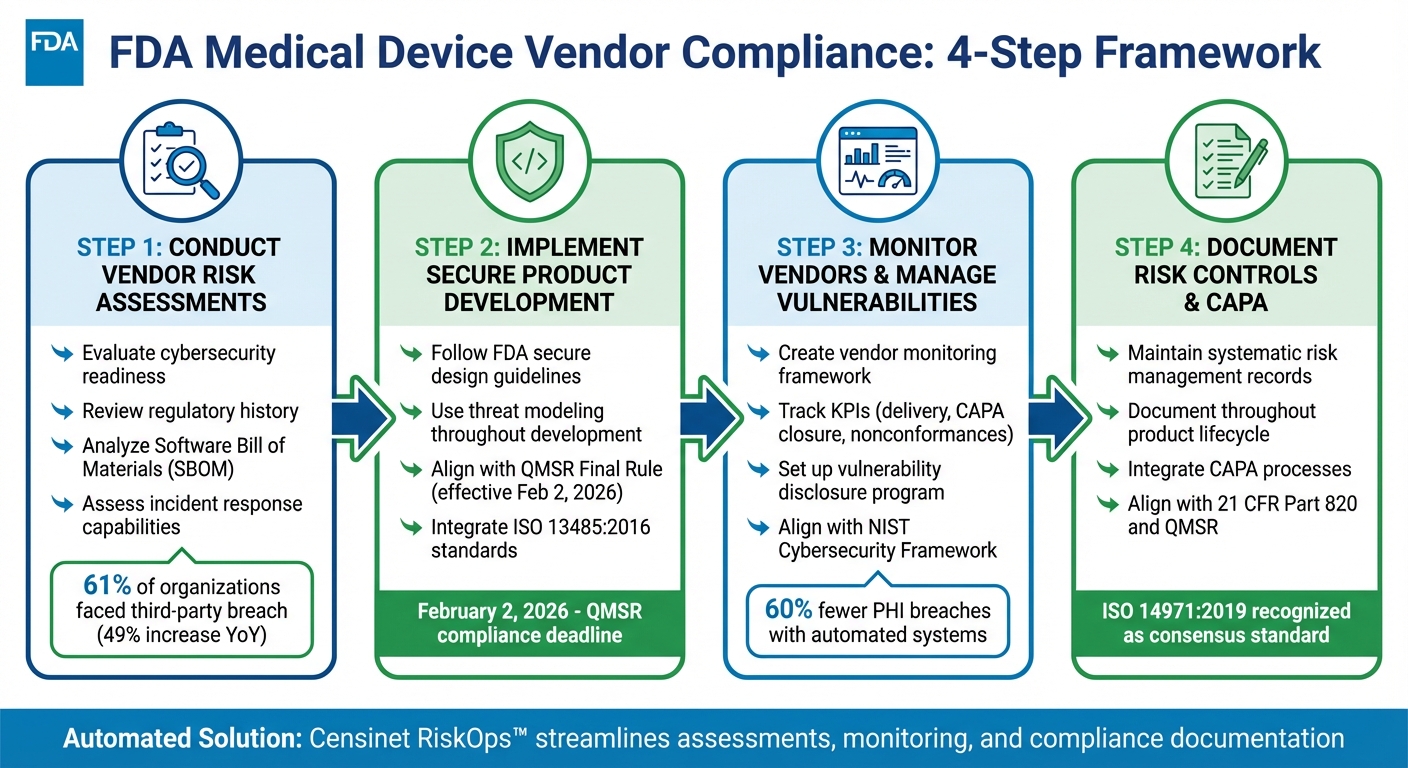
4-Step FDA Medical Device Vendor Compliance Framework
Managing Third-Party Vendors for FDA Compliance
To comply with FDA regulations, manufacturers working with third-party medical device vendors must prioritize risk management. With updates like the Quality Management System Regulation (QMSR) aligning with ISO 13485:2016 starting February 2, 2026, the focus on vendor oversight is increasing. Here's a quick breakdown of key practices:
- Vendor Risk Assessments: Evaluate vendors for cybersecurity readiness, regulatory history, and incident response. Use Software Bill of Materials (SBOMs) to identify vulnerabilities.
- Secure Development Practices: Ensure vendors follow secure product design frameworks and FDA guidelines for safety and security.
- Continuous Monitoring: Track vendor performance, compliance, and vulnerabilities throughout the product lifecycle.
- Risk Documentation: Maintain detailed records of risk controls and integrate corrective actions (CAPA) into vendor management.
Tools like Censinet RiskOps™ can automate assessments, monitoring, and compliance tracking, simplifying the process while reducing risks. </article>
Step 1: Conduct Vendor Risk Assessments
Create a well-organized process to evaluate FDA compliance and uncover security weaknesses before partnering with third-party vendors. This process should include technical reviews, such as analyzing Software Bill of Materials (SBOMs) to identify potential software vulnerabilities.
When conducting your assessment, focus on key risk areas like cybersecurity readiness, regulatory history, and incident response capabilities. A 2024 Third-Party Risk Management Study revealed that 61% of organizations faced a third-party data breach or cybersecurity incident, marking a 49% increase compared to the previous year [7]. These figures highlight the growing importance of thorough vendor evaluations, especially in healthcare.
Use Software Bill of Materials (SBOM) to Identify Risks
The FDA now mandates that manufacturers include a Software Bill of Materials (SBOM) in their premarket submissions. An SBOM provides a detailed inventory of all software components within a medical device. This level of transparency helps uncover vulnerabilities that could jeopardize patient safety.
"Software Bill of Materials (SBOM) is crucial for managing cybersecurity risks. It identifies device components and vulnerabilities, aiding risk management. Regularly updated SBOMs should be part of device configuration management and included in premarket submissions for FDA assessment and user transparency in labeling." - BioT-Medical [6]
When assessing vendors, request a machine-readable SBOM that includes information such as support levels, end-of-support dates, and known vulnerabilities. If a vendor cannot provide this document, require a clear explanation. Use the SBOM to evaluate identified vulnerabilities, their potential impact, and the risk controls the vendor has implemented. The document should also establish a clear connection between threat models, cybersecurity risk assessments, and testing documentation [6].
Key Criteria for Evaluating Vendor Risks
In addition to technical evaluations, assess vendor risks using a comprehensive set of criteria. Classify vendors based on factors like their access to protected health information (PHI), the criticality of the systems they support, and the regulatory requirements they must meet [8]. Vendors with direct access to patient data or those supplying essential medical devices require more stringent evaluations compared to those offering peripheral services.
Examine the vendor's security questionnaires and verify their certifications, such as ISO 13485:2016 compliance. Investigate their history for past breaches or FDA warning letters. Assess their operational resilience by reviewing their business continuity plans and disaster recovery strategies. Studies show that healthcare organizations using automated third-party risk management systems experience up to 60% fewer PHI breaches compared to those relying on manual processes [8].
Hold vendors accountable by requiring regular compliance attestations, conducting periodic audits, and ensuring they have a robust incident response plan [7]. Focus your risk assessments on vulnerabilities that could directly affect patient safety. These evaluations are essential for maintaining FDA compliance and safeguarding patient health.
Step 2: Implement Secure Product Development Practices
Encourage vendors to adopt secure development frameworks to minimize vulnerabilities that could jeopardize patient safety. The FDA's updated guidelines, released on September 27, 2023, outline key areas like cybersecurity risk assessments, interoperability, and documentation for premarket submissions [9].
Follow FDA Guidelines for Secure Product Design
After conducting vendor risk assessments, ensuring vendors follow secure development practices becomes essential. Vendors should align their processes with the FDA's recommendations to guarantee that medical devices meet both safety and security expectations. The FDA's Quality Management System Regulation (QMSR) Final Rule, which takes effect on February 2, 2026, incorporates ISO 13485:2016 and outlines detailed requirements for every stage of the product lifecycle - designing, purchasing, manufacturing, packaging, labeling, storing, installing, and servicing medical devices [1]. These guidelines establish the foundation for secure product development.
One critical step is verifying that vendors use threat modeling throughout the development process. The FDA’s "Playbook for Threat Modeling Medical Devices" offers practical guidance for identifying and addressing potential security flaws before they can be exploited [5]. Vendors should thoroughly document how they integrate threat modeling with cybersecurity testing and assessments.
Integrate Vendor Security Practices into Your Organization
Securing patient safety and device performance requires more than just design - it demands embedding vendor security into daily operations. Both healthcare organizations and manufacturers must take active steps to protect devices and ensure compliance [5]. Ultimately, your organization bears responsibility for maintaining these standards [12].
To achieve this, establish clear contractual agreements with vendors that cover regulatory compliance, data security, quality assurance, service level agreements, data privacy, access controls, encryption, and breach response protocols [10][11][12]. Vendors should also be required to notify your organization of any changes to their product or service that could impact the quality or safety of a medical device [12]. Include a right-to-audit clause in all vendor contracts, define consequences for non-compliance, and ensure vendors understand their obligations around incident reporting and compliance updates [10][11][12].
Step 3: Monitor Vendors and Manage Vulnerabilities
After completing vendor risk assessments and securing product development, the next critical step is continuous monitoring. This ensures compliance with FDA standards and helps address evolving threats. The FDA requires manufacturers to actively monitor supplier performance throughout the entire product lifecycle [2]. This ongoing vigilance is key to maintaining compliance and security.
Create a Vendor Monitoring Framework
Develop a structured framework to keep track of vendor performance, security updates, and compliance metrics. Incorporate risk management into your quality system to evaluate and respond to significant events [13]. The FDA's Q9(R1) Quality Risk Management Guidance for Industry, released in May 2023, underscores the importance of applying quality risk management principles to areas like "Assessment and Evaluation of Suppliers and Contract Manufacturers" as part of materials management [13].
To make your framework effective, prioritize resources based on risk levels. Vendors with higher risks should undergo more frequent reviews compared to those with lower risks [13][14]. Use key performance indicators (KPIs) to measure vendor reliability and security, such as on-time delivery rates, trends in nonconformances, corrective and preventive action (CAPA) closure times, and data from complaints or adverse events tied to supplier products [2]. Additionally, the Medical Device Single Audit Program (MDSAP), which becomes mandatory on December 22, 2023, requires participants to monitor the effectiveness of risk management actions, identify new risks, and provide regular feedback [14].
To streamline the process, standardize audits with digital checklists and automated CAPA workflows [2]. Keep centralized, searchable audit records that integrate with broader quality system functions like document control, training, and change management [2]. This interconnected approach ensures supplier risk management supports your entire quality management system rather than functioning as a standalone process.
Once monitoring is in place, the next focus should be on structured vulnerability reporting.
Set Up a Vulnerability Disclosure Program
Implement clear processes for vendors to report cybersecurity vulnerabilities and ensure prompt resolutions. Continuously monitor cybersecurity threats throughout a device's lifecycle [3][6]. Manufacturers must have systems in place to identify, respond to, and mitigate cybersecurity issues quickly and effectively [3].
Align your vulnerability disclosure program with established frameworks like the National Institute of Standards and Technology (NIST) Cybersecurity Framework, which is widely used in healthcare for managing medical device risks [4]. Require vendors to report on their cybersecurity controls, potential risks, and mitigation measures [5]. Maintain detailed documentation of all vulnerability reports, remediation actions, and patch deployment timelines. This ensures transparency and provides a clear record for regulatory audits [13][15]. Such documentation demonstrates your organization's commitment to managing postmarket cybersecurity vulnerabilities throughout the product lifecycle [5][4].
sbb-itb-535baee
Step 4: Document Risk Controls and CAPA Integration
To ensure compliance and maintain a clear audit trail, it's crucial to document your risk management and CAPA processes thoroughly. The FDA expects medical device manufacturers to establish and record a systematic risk management process that spans the entire product lifecycle - from the initial concept to the final phase of decommissioning [16]. This step ties together the earlier efforts in risk assessment, secure development practices, and continuous monitoring.
Your documentation should reflect the level of risk associated with each vendor [13][14]. For instance, high-risk vendors demand more detailed records compared to those with lower risk profiles.
Align Risk Controls with FDA QMSR Requirements
Historically, 21 CFR Part 820 has addressed risk management mainly in the context of design validation. However, the FDA now recognizes ISO 14971:2019 as a consensus standard, signaling a broader need for comprehensive risk management documentation [16]. The upcoming Quality Management System Regulation (QMSR) will further formalize these expectations, making it essential to align your practices sooner rather than later.
For each vendor, document the specific risk controls implemented, the reasoning behind them, and evidence of their effectiveness. Your records should clearly demonstrate how these controls meet FDA requirements and fit into your overall quality management system. Organize these records systematically to streamline internal audits and FDA inspections.
Once your risk controls are documented, take the next step by integrating CAPA processes into your vendor management system.
Integrate CAPA Processes with Vendor Operations
Building on your risk control documentation, incorporate CAPA processes to address vendor-related issues effectively. Regulatory frameworks like ISO 13485, FDA 21 CFR Part 11/820, and EU MDR require stringent oversight of suppliers [2].
Define clear procedures for initiating CAPA actions when vendor issues arise. Outline how vendors should report problems, what details they need to include, and the expected timelines for resolving these issues. Every CAPA action - whether it involves root cause analysis, corrective measures, or verification of effectiveness - should be documented in detail.
Supplier risk management is an integral part of your quality system, demanding the same level of rigor as your internal processes. Vendors should adhere to strict CAPA protocols, with clear reporting requirements and resolution deadlines to ensure seamless integration with your quality management system [2].
Use Censinet RiskOps™ for Automated Third-Party Risk Management

As your vendor network grows, manually managing third-party risks can quickly become overwhelming. Fragmented processes not only slow things down but also leave gaps that audits can expose. That’s where Censinet RiskOps™ steps in. By automating vendor assessments, ongoing monitoring, and compliance documentation, it simplifies the entire process and reduces vulnerabilities.
Automate Risk Assessments with Censinet RiskOps™
With Censinet AI™, the days of drawn-out risk evaluations are over. The platform collects evidence and tracks compliance automatically, cutting evaluation times from weeks to just seconds. It summarizes vendor evidence, highlights key product integration details, and identifies fourth-party risks. From there, it generates detailed risk summary reports based on the data it gathers.
Censinet RiskOps™ also ensures workflows align with regulations like 21 CFR Part 820 and QMSR. High-risk vendors are flagged for closer scrutiny, and documentation is enhanced to meet compliance standards.
The platform combines automation with human oversight. Evidence validation, policy drafting, and risk mitigation are guided by configurable rules, giving risk teams the ability to maintain control while speeding up processes.
View Risk Data Through Censinet's Command Center
The Command Center offers a centralized dashboard that provides real-time insights into vendor risks and compliance gaps. It produces audit-ready reports [17] and consolidates data from across your vendor ecosystem. This makes it easier to identify critical cybersecurity risks and unresolved CAPA (Corrective and Preventive Actions).
Key findings are routed to the right stakeholders, ensuring swift action when it matters most. By integrating seamlessly with your existing risk management practices, this system helps maintain FDA compliance while keeping your vendor network secure and efficient.
Managing Uncontrolled vs. Controlled Security Risks
Understanding the difference between uncontrolled and controlled security risks is crucial for meeting FDA compliance standards. Uncontrolled risks arise from unpredictable factors like emerging threats, hidden vulnerabilities in third-party components, or improper device use. These risks can result in serious issues such as patient harm, data breaches, or device failures, and they are inherently harder to predict and measure [3][4][5].
On the other hand, controlled risks are those that have been identified, evaluated, and addressed through structured processes. The FDA highlights that cybersecurity is a shared responsibility, involving manufacturers, healthcare facilities, patients, and providers [4][5]. The key objective is to shift risks from uncontrolled to controlled by improving visibility, designing secure systems, and implementing continuous monitoring [5][19].
Recent statistics highlight the growing urgency of addressing these risks. The 2025 Verizon Data Breach Investigations Report revealed that third-party involvement in breaches has doubled, now accounting for 30% of incidents compared to 15% previously [18]. Additionally, supply chain-related attacks have surged, averaging 26 incidents per month as of April 2025 [18]. A notable example is the July 19, 2024, CrowdStrike incident, where a flawed security software update caused global outages and resulted in $5 billion in direct losses over just four days [19].
Below is a summary table comparing uncontrolled and controlled security risks, along with FDA requirements, mitigation strategies, and vendor responsibilities.
Comparison Table: Uncontrolled vs. Controlled Security Risks
| Risk Type | Characteristics | FDA Requirements | Mitigation Strategies | Vendor Responsibilities |
|---|---|---|---|---|
| Uncontrolled | Evolving threats, unknown vulnerabilities in third-party components, unexpected misuse, limited supply chain visibility [3][4][5][18] | Report cybersecurity issues via MedWatch (health professionals/patients) or Medical Device Reporting (manufacturers/importers) [5] | Use SBOMs for all software components, maintain a comprehensive OT device inventory, and map system traffic before deployment [18][19] | Provide complete SBOMs, promptly disclose vulnerabilities, and maintain transparent communication channels |
| Controlled | Risks are identified, assessed, and actively monitored; documented in risk management records [4][19] | Follow a Secure Product Development Framework (SPDF); comply with 21 CFR Part 820, QMSR, NIST FIPS 140-2/140-3, NIST SP 800-82, and IEC 62443 [3][4][5][19] | Segment networks into zones and conduits, adopt a three-tier architecture, configure COTS products for security, and establish continuous monitoring plans [19] | Integrate security from the design phase, conduct rigorous multi-environment testing, and ensure ongoing security training for personnel [19] |
The FDA's updated guidance, titled "Cybersecurity in Medical Devices: Quality System Considerations and Content of Premarket Submissions," issued on June 27, 2025, emphasizes these requirements [5]. By adopting a Secure Product Development Framework (SPDF), manufacturers can reduce vulnerabilities throughout the device lifecycle, making it a cornerstone of effective cybersecurity risk management [3][4].
Conclusion: Maintain FDA Compliance with Censinet
Key Points for Meeting FDA Standards
To stay in line with FDA cybersecurity requirements, it’s important to manage third-party risks thoughtfully. This includes conducting vendor risk assessments with tools like SBOMs, implementing secure product development practices, and ensuring ongoing monitoring. Clear vulnerability disclosures and proper documentation are also crucial to meet FDA standards for corrective actions.
How Censinet Simplifies Compliance
Censinet’s platform brings risk management under one roof, simplifying vendor assessments and making it easier for risk teams to uphold FDA compliance. This streamlined approach strengthens your organization’s overall efforts in meeting FDA requirements while bolstering cybersecurity defenses.
FAQs
How does a Software Bill of Materials (SBOM) help manage third-party vendor risks?
A Software Bill of Materials (SBOM) is essentially a detailed list of all the software components, including third-party libraries, that make up a device. This level of transparency allows organizations to pinpoint potential vulnerabilities, evaluate risks, and stay aligned with FDA regulations.
Knowing precisely what software is in use enables healthcare organizations to tackle cybersecurity threats head-on, keep track of necessary updates or patches, and strengthen their overall approach to risk management. An SBOM serves as an essential resource for protecting the healthcare supply chain and meeting regulatory requirements.
What steps can manufacturers take to continuously monitor vendor compliance with FDA regulations?
Manufacturers can stay on top of vendor compliance with FDA regulations by using automated risk management tools, performing regular risk assessments at every stage of the product lifecycle, and leveraging real-time analytics to monitor vendor performance closely.
Keeping thorough records of vendor activities is equally important. This includes documenting cybersecurity measures and compliance efforts to promote transparency and accountability. Taking these proactive steps helps manufacturers minimize risks and stay aligned with FDA standards.
What are the essential practices for secure product development to meet FDA compliance?
To align with FDA requirements in secure product development, start with detailed risk assessments using tools like FMEA (Failure Modes and Effects Analysis), FTA (Fault Tree Analysis), or threat modeling. Make sure to comply with essential standards such as ISO 14971 and follow FDA regulations, including 21 CFR Part 820 and Part 11. Incorporate risk management strategies at every stage of the product lifecycle, from initial design to post-market surveillance.
Set clear and measurable criteria for assessing and accepting risks. Keep comprehensive records and continuously monitor for new threats to ensure timely responses. By taking these steps, you not only meet regulatory expectations but also prioritize patient safety and strengthen confidence in your medical device.


