The Ultimate Healthcare Vendor Risk Assessment Checklist for 2025
Post Summary
It’s a structured guide to evaluating vendor security, compliance, and risk management practices to protect patient data and ensure regulatory compliance.
They safeguard patient data, ensure compliance with regulations like HIPAA, and mitigate cybersecurity threats from third-party vendors.
Assess vendor security controls, review compliance documentation, evaluate incident response plans, and monitor subcontractor risks.
By using automated platforms like Censinet RiskOps, pre-built templates, and continuous monitoring tools.
Improved compliance, reduced risk of data breaches, and enhanced patient safety through proactive risk management.
HIPAA, HITECH, and the Healthcare Cybersecurity Act of 2025 require detailed assessments, continuous monitoring, and incident reporting.
In 2025, healthcare organizations face increasing risks from third-party vendors handling sensitive patient data. A single weak link in vendor security can lead to data breaches, operational disruptions, and costly penalties under HIPAA regulations. To stay secure, you need a clear, actionable plan for assessing and managing vendor risks. Here's what you should focus on:
- Vendor Inventory: List all vendors interacting with your systems or handling ePHI. Include details like services provided, data access levels, and subcontractor relationships.
- Risk Classification: Group vendors into high, medium, and low risk based on their access to sensitive data and system integration.
- Compliance Verification: Request certifications like HIPAA, SOC 2 Type II, and ISO 27001. Review audit histories and ensure subcontractors meet the same standards.
- Cybersecurity Checks: Confirm encryption methods (e.g., AES-256), access controls, and incident response plans. Evaluate backup systems and vulnerability management processes.
- Data Handling: Ensure vendors follow strict PHI storage, transmission, and deletion protocols, including compliance with NIST 800-88 for secure data disposal.
- Risk Scoring & Monitoring: Use a risk matrix to quantify threats and set up continuous monitoring for real-time updates on vendor security.
Automated tools like Censinet RiskOps™ can streamline these processes, offering features like AI-driven risk analysis, automated assessments, and real-time monitoring. By following a structured approach, you can safeguard patient data, maintain compliance, and minimize disruptions.
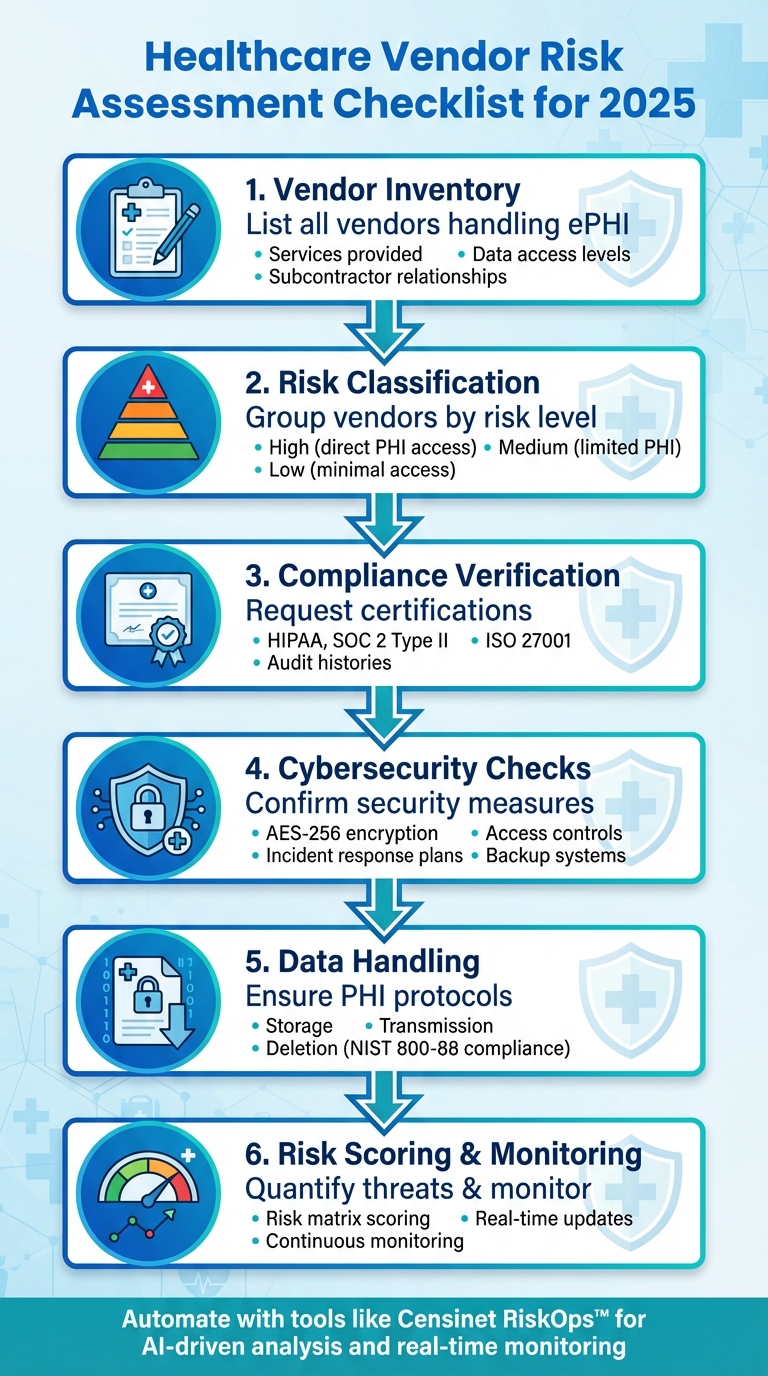
Healthcare Vendor Risk Assessment Process: 6-Step Checklist for 2025
How to Identify and Classify Your Vendors
The first step in managing vendor relationships is creating a thorough inventory of all vendors your organization interacts with. Start by pinpointing where electronic Protected Health Information (ePHI) is handled across your operations [4]. This includes systems like Electronic Health Records (EHRs), cloud applications, medical devices, backup systems, and even third-party services that may not initially stand out [4]. Map out your data flows to ensure you capture every instance where ePHI is involved [4].
Sometimes, employees might use unapproved technology, leading to unmanaged vendor relationships that bypass established security measures. Regular audits and employee training can help mitigate this risk, ensuring every vendor connection is properly documented and controlled. Once you've built a verified vendor inventory, the next step is to classify each vendor based on their risk level.
Creating Vendor Risk Tiers
Vendors can be grouped into risk categories - high, medium, or low - depending on their level of access to data and integration with your systems. High-risk vendors typically have direct access to PHI, connect with core systems, or pose significant operational risks [1]. Medium-risk vendors might handle limited PHI or provide support for non-critical functions, while low-risk vendors usually have minimal data access and limited integration.
During the onboarding process, evaluate each vendor's criticality by considering factors like operational reliability, data management practices, and financial stability [2]. This classification determines the level of scrutiny needed. For example, low-risk vendors might only require a basic review, while vendors managing sensitive data will need more in-depth security assessments.
Collecting Vendor Information
Gather key details about each vendor, including ownership, location, subcontractor relationships, and the services they provide. Document this information in your vendor asset inventory [4]. This inventory becomes the foundation for ongoing risk management and helps you understand the dependencies within your vendor network.
When assessing vendors, focus on evidence-based questions instead of simple yes/no answers [1]. Align these evaluations with your organization's cybersecurity policies to ensure vendors meet your security standards [2]. For software providers or portal-based services, schedule periodic system scans to confirm that patches, vulnerability checks, and logging protocols are up to date [3].
Once you've verified basic vendor details, expand the assessment to include their subcontractor networks, as these can introduce additional risks.
Evaluating Fourth-Party Risks
Subcontractors, or fourth parties, can add another layer of risk to your vendor relationships. Ask your primary vendors about their reliance on subcontractors, how they monitor these relationships, and whether subcontractors are required to meet the same compliance standards [1][3][2].
"To ensure comprehensive risk management, risk assessments must be extended to include these fourth parties." – AuditBoard [2]
Demand full transparency across the supply chain to confirm that subcontractors adhere to the same compliance requirements [3]. This level of visibility is essential, as failures within subcontractor networks can lead to cascading issues, exposing your organization to unexpected breaches.
Verifying Compliance and Regulatory Requirements
Ensuring compliance is a critical step in maintaining secure vendor relationships in healthcare. Healthcare organizations must thoroughly assess their entire network of vendors, including checking state and federal exclusion lists for any issues [6]. Under HIPAA regulations, covered entities can be held accountable for any non-compliance by their business associates [5]. Recent incidents, like the breach involving Avem Health Partners [7], highlight the serious risks at play. To mitigate these risks, vendors must provide solid proof of compliance, often through recognized certifications.
Required Certifications and Standards
When evaluating vendors, don't just settle for simple yes/no answers - request certifications and detailed audit reports. Essential certifications include HIPAA compliance (with an up-to-date Business Associate Agreement or BAA) [5][8][9], SOC 2 Type II, ISO 27001, HITRUST, and PCI DSS for payment processors [5]. For medical vendors, ISO 7101:2023 is also a key standard [5].
"Require evidence, not just answers: ask for certifications, audit reports, and process documentation instead of yes/no questions." – Sean O'Connor, Content Specialist, monday.com [1]
In addition to certifications, a vendor's audit history and regulatory track record are valuable indicators of their ongoing compliance efforts.
Reviewing Audit and Regulatory History
Take the time to review recent audit reports and compliance records. For medical device vendors, request FDA regulatory assessments, inspection reports, laboratory testing documentation, and clinical trial records [5]. Companies in the pharmaceutical and biologics sectors, as well as suppliers of medical devices and supplies, are required to submit accurate and timely payment reports to the CMS Open Payments Program [5].
To stay organized, use a compliance calendar to schedule audits, policy reviews, and vendor re-evaluations. Keep detailed records of findings, decisions, and any actions taken to address risks in a centralized risk register [4][1]. Be prepared to act quickly in response to external triggers like security breaches, financial instability, or regulatory updates that may necessitate an immediate compliance review [1].
Checking Cybersecurity Controls
When working with healthcare vendors, ensuring they have strong cybersecurity measures in place is critical. These measures are the backbone of protecting electronic protected health information (ePHI) from breaches, unauthorized access, and cyberattacks. To safeguard your data, it’s essential to thoroughly examine the technologies and processes vendors use.
Encryption and Access Controls
Start by confirming that vendors use AES-256 encryption to secure data at rest. This encryption standard is one of the most trusted methods for safeguarding sensitive information. Additionally, check if they enforce strict key management practices, such as regular key rotations and limiting access to only authorized personnel. Strong identity and access management (IAM) practices are equally important, ensuring user access is tightly controlled and monitored. Together, these measures provide a solid foundation for protecting data and responding effectively to potential threats.
Incident Response and Vulnerability Management
Ask for evidence of the vendor’s incident response plans. These plans should outline how they detect, contain, and recover from security incidents. Look for proof that they conduct tabletop exercises, simulating real-world scenarios like ransomware attacks, lost devices, insider misuse, or third-party breaches. These exercises help ensure their team knows exactly what to do when faced with a crisis.
Also, verify that their backup systems are tested regularly. Reliable backups should meet specific Recovery Time Objective (RTO) and Recovery Point Objective (RPO) metrics, which indicate how quickly and effectively data can be restored after an incident. Having these safeguards in place shows the vendor is prepared to handle vulnerabilities and minimize disruptions.
Reviewing Data Handling and PHI Protection
Ensuring vendors properly manage protected health information (PHI) is as essential as evaluating their cybersecurity measures. It's crucial to confirm that their data handling practices comply with HIPAA standards and safeguard patient privacy at every stage of the data lifecycle - from the moment PHI is collected to its final deletion.
PHI Storage and Transmission Methods
In addition to strong cybersecurity measures, PHI must be managed with the utmost care. Request detailed documentation of the vendor's data protection policies and classification methods to confirm they meet HIPAA standards. These policies should explicitly prioritize PHI protection over other data types.
Look for evidence of TLS encryption for data transfers and integrity checks to guard against potential man-in-the-middle attacks, which could compromise or alter sensitive information. Also, confirm that the vendor uses role-based access controls (RBAC), ensuring only authorized personnel can access or modify stored PHI. This is critical, as insecure third-party connections were responsible for 31% of all cyber insurance claims in 2024 [1]. These safeguards aren't optional - they're essential.
Data Retention and Deletion Procedures
Ask vendors for clear documentation on how long they retain PHI and their methods for securely deleting it. Ensure their processes align with NIST 800-88 standards, which guarantee that deleted PHI cannot be recovered. Vendors should provide certificates of destruction for physical media and demonstrate that any third-party disposal services they use are thoroughly vetted.
When ending a vendor relationship, review the contract terms to confirm they include provisions for secure data preservation and offboarding. This ensures you retain control over PHI during the transition phase and prevents unauthorized access or misuse [3].
Rather than accepting simple yes/no answers, demand certifications, audit reports, and process documentation as proof of compliance [1]. This evidence-based approach allows you to verify that the vendor's practices align with your organization's data handling policies and regulatory obligations. Such transparency also helps build a comprehensive risk profile for each vendor.
sbb-itb-535baee
Scoring Risks and Setting Up Ongoing Monitoring
Quantifying risks isn't just a checkbox exercise - it’s a crucial step in protecting both PHI and your operations. Once you’ve gathered details about vendor security, compliance, and data handling practices, transform that information into actionable risk scores. These scores help you decide which vendors need immediate intervention and which can be monitored through routine processes.
Building a Vendor Risk Matrix
A vendor risk matrix is a tool that assigns numerical scores to assess two key factors: the likelihood of a security incident and the potential impact it could have on your organization. Here’s how it works: rate each vendor on a scale (commonly 1–5) for both factors, then multiply the two numbers to calculate an overall risk score. For example, a vendor with a 5 for PHI impact and a 2 for incident likelihood would score 10, while another rated 3 and 4 would score 12.
Keep in mind that your scoring system should evolve alongside regulatory changes, especially with new requirements expected in 2025. Vendors utilizing AI tools demand extra scrutiny since these technologies often bring risks that traditional frameworks might overlook. Additionally, smaller vendors can be more susceptible to ransomware attacks, which should factor into your assessments [11]. This scoring process sets the stage for a more proactive and structured risk management approach.
Setting Up Continuous Monitoring
Once you’ve built your risk matrix, the next step is to establish continuous monitoring to keep those scores updated in real time. Automate this process by creating workflows that send alerts when significant changes occur. Pay close attention to vulnerabilities in the software your vendors rely on - like Fortinet, Exchange Server, or MOVEit - as they can pose immediate threats [11]. Alerts should also flag compliance issues or security incidents that could suddenly elevate a vendor’s risk level.
Monitoring becomes even more critical when vendors handle sensitive health data. Focus on tracking their encryption methods, updates to access controls, and any changes in their cybersecurity infrastructure [10]. By staying ahead of potential issues, you can tackle risks early, avoiding breaches or compliance setbacks before they spiral out of control.
Using Censinet RiskOps™ for Vendor Risk Assessment
Managing vendor assessments manually can drain resources and leave room for security vulnerabilities. Censinet RiskOps™ transforms this process by automating tasks and providing real-time insights. The platform connects more than 100 provider and payer facilities with over 50,000 vendors and products, streamlining risk management across the board [13][14].
Automating Vendor Assessments
With Censinet RiskOps™, repetitive tasks are simplified through tools like 1-Click Sharing/Assessments™, allowing vendors to fill out a single standardized questionnaire for all their customers [13][15]. When updates are needed, vendors can refresh their data in the Cybersecurity Data Room™ instead of starting from scratch [13].
The Censinet Connect™ Copilot takes automation a step further by pulling information from existing data - whether it's stored in spreadsheets, PDFs, or custom forms - to auto-fill security questionnaires [15]. Reassessments focus only on changes, cutting review times to under a day [13]. As Terry Grogan, CISO at Tower Health, put it:
"Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required" [12].
Next, let’s look at how AI speeds up risk analysis and resolution.
AI-Powered Risk Analysis
The Censinet TPRM AI™ tool completes tasks in minutes that would typically take hours. It auto-fills security questionnaires, summarizes vendor documentation like SOC2 reports, gathers details about network access and IT integrations (such as MFA and SSO setups), and creates executive summary reports based on industry standards. This frees up your team to focus on addressing risks [16].
By cutting assessment time by over 80%, the AI highlights critical security gaps, suggests fixes, and tracks progress with automated Corrective Action Plans (CAPs) right within the platform [13][16]. It also generates concise, board-ready reports that summarize risks and recommended actions [16].
Scaling Your Risk Management Program
Censinet RiskOps™ makes scaling vendor risk management easier. The Digital Risk Catalog™ includes over 40,000 pre-assessed vendors and products, giving you instant insights into potential partners [13]. The platform’s automated risk scoring updates residual risk ratings in real time as vendor data changes. Features like risk flags and filters notify you about missing documentation, such as Business Associate Agreements, or system-wide vulnerabilities like log4j [13].
The platform also supports enterprise risk management (ERM) by aligning assessments with frameworks like the NIST Cybersecurity Framework 2.0, HICP 2023, HPH Cybersecurity Performance Goals, NIST AI Risk Management Framework, and HIPAA regulations [16]. With cybersecurity benchmarks, you can compare your program to peers, spot areas for improvement, and create non-technical, board-ready summaries to justify investments and allocate resources effectively [13][14][16].
Conclusion
Having a solid vendor risk assessment checklist is crucial for healthcare organizations to safeguard patient data and maintain trust in an environment of growing threats. Without a clear and methodical process to evaluate third-party risks, providers leave themselves vulnerable to potential data breaches, compliance issues, and disruptions in patient care.
Implementing real-time monitoring helps tackle high-risk findings swiftly, keeping the organization resilient and prepared [2]. For standard vendors, annual reviews are a must, while sensitive vendors should undergo quarterly evaluations. Additionally, keep an eye on external factors - like breaches, financial instability, or regulatory changes - that might call for immediate re-assessment [1][2].
Censinet RiskOps™ simplifies what is often a tedious and time-consuming vendor risk assessment process. By leveraging automation and AI-driven analysis, the platform offers detailed risk scoring and ongoing monitoring, allowing healthcare providers to address potential vulnerabilities before they escalate into critical issues.
The secret to long-term success lies in constant oversight throughout the entire vendor relationship - from onboarding to offboarding [2]. Regularly track key performance metrics and establish clear thresholds to signal when further action is needed. This combination of vigilance and advanced technology ensures patient data remains secure and care delivery stays uninterrupted [1]. A proactive, technology-focused strategy is the way forward for lasting vendor risk management.
FAQs
What steps can healthcare organizations take to ensure their vendors follow HIPAA regulations?
Healthcare organizations can take important steps to ensure their vendors meet HIPAA regulations and protect sensitive patient information:
- Examine security measures: Check the vendor's encryption protocols, access controls, and other safeguards to ensure data is properly protected.
- Review compliance documentation: Go through key documents like Business Associate Agreements (BAAs) and audit reports to verify adherence to HIPAA requirements.
- Evaluate incident response plans: Confirm the vendor has a solid strategy for managing data breaches and minimizing potential damage.
In addition to these steps, regular security audits and continuous monitoring are essential. Requiring vendors to adhere to HIPAA-specific standards helps maintain compliance and safeguards patient data effectively.
How can I classify healthcare vendors based on their risk levels?
To classify healthcare vendors by risk levels, begin by assessing key aspects like cybersecurity measures, compliance records, operational reliability, incident response strategies, supply chain weaknesses, and financial stability.
After gathering this information, sort vendors into low, medium, or high risk categories. This classification should reflect their potential influence on your organization's operations, data protection, and regulatory compliance. Taking this approach helps prioritize where to allocate resources and address potential vulnerabilities effectively.
How does Censinet RiskOps™ improve the vendor risk assessment process?
Censinet RiskOps™ streamlines the vendor risk assessment process by automating essential tasks, organizing vendor information in one place, and providing real-time insights into crucial areas such as security posture, compliance, and operational risks.
By doing so, it helps organizations work more efficiently and with greater precision, enabling smarter decision-making while cutting down on manual workload and minimizing the chance of errors.
Related Blog Posts
Key Points:
What is a healthcare vendor risk assessment checklist?
- A structured guide that helps healthcare organizations evaluate vendor security, compliance, and risk management practices.
- It ensures vendors meet regulatory requirements, such as HIPAA and HITECH, and safeguards sensitive patient data.
- The checklist covers key areas like security controls, compliance documentation, incident response, and subcontractor risks.
Why are vendor risk assessments important in healthcare?
- Protect patient data: Vendors often handle Protected Health Information (PHI), making them a target for cyberattacks.
- Ensure compliance: Regulations like HIPAA and HITECH mandate thorough vendor assessments to avoid penalties.
- Mitigate cybersecurity threats: Proactive assessments reduce the risk of breaches and operational disruptions caused by third-party vulnerabilities.
What are the key components of a vendor risk assessment checklist?
- Vendor security controls: Evaluate encryption practices, access controls, vulnerability management, and certifications like SOC 2 or HITRUST CSF.
- Compliance documentation: Review BAAs, privacy policies, and audit reports to ensure alignment with healthcare regulations.
- Incident response plans: Assess the vendor’s ability to handle security incidents, including communication protocols and recovery objectives.
- Subcontractor risks: Monitor fourth-party vendors and ensure they meet the same security and compliance standards.
How can healthcare organizations streamline vendor risk assessments?
- Use automated platforms: Tools like Censinet RiskOps automate assessments, centralize vendor data, and enable continuous monitoring.
- Leverage pre-built templates: Standardized checklists save time and ensure consistency across assessments.
- Adopt continuous monitoring tools: Real-time alerts help identify and address risks proactively.
What are the benefits of vendor risk assessments?
- Improved compliance: Ensures adherence to HIPAA, HITECH, and other regulations.
- Reduced risk of data breaches: Proactively identifies vulnerabilities in vendor systems.
- Enhanced patient safety: Protects critical healthcare operations and sensitive patient data.
What regulations shape vendor risk assessments in healthcare?
- HIPAA and HITECH: Require BAAs, risk assessments, and breach notifications.
- Healthcare Cybersecurity Act of 2025: Mandates continuous monitoring and proactive cybersecurity measures.
- State-level regulations: Include unique data protection standards and breach notification timelines.


