HIPAA Compliance for API Integration in Healthcare
Post Summary
A HIPAA-compliant API securely handles Protected Health Information (PHI) by adhering to HIPAA’s Privacy, Security, and Breach Notification Rules.
API integration enables secure, real-time data exchange between healthcare systems, improving patient care and operational efficiency.
Safeguards include encryption, access controls, audit logging, and adherence to the "minimum necessary" data principle.
Challenges include ensuring interoperability, managing legacy systems, and maintaining compliance with strict security standards.
Benefits include enhanced data security, streamlined workflows, improved patient outcomes, and regulatory compliance.
By implementing secure API gateways, encrypting PHI, conducting regular audits, and signing Business Associate Agreements (BAAs).
Protecting health data is non-negotiable. If your API handles electronic protected health information (ePHI), compliance with HIPAA is mandatory. This involves meeting strict rules for privacy, security, and breach notification. APIs are essential in healthcare for tasks like telehealth, EHR integrations, and billing, but they also introduce risks if not properly secured.
Here’s what you need to know:
- Who must comply? Covered entities (e.g., hospitals, insurers) and business associates (e.g., API developers, cloud vendors) handling ePHI.
- Key safeguards: Encrypt data in transit and at rest, enforce strict access controls, and maintain detailed audit logs.
- Common challenges: Balancing security with usability, managing third-party risks, and ensuring interoperability with standards like HL7 FHIR.
- Deployment options: On-premises, cloud, or hybrid setups, all requiring HIPAA-aligned configurations.
- Best practices: Use OAuth 2.0 for authentication, limit data exposure, and conduct regular risk assessments.
Non-compliance can result in hefty fines - up to $1.5 million per violation annually - and loss of trust. Whether you’re a developer or a healthcare provider, securing APIs is critical to protecting patient data and meeting regulatory requirements.
HIPAA Security Rule Requirements for APIs
The HIPAA Security Rule establishes national guidelines to protect electronic protected health information (ePHI) [7]. While it includes administrative, physical, and technical safeguards, APIs primarily fall under the technical safeguards, which cover access control, audit controls, integrity, authentication, and transmission security. Let’s explore how these safeguards apply to API design and deployment.
According to the Office for Civil Rights (OCR), hacking and IT incidents now account for the majority of large healthcare data breaches. Many of these breaches involve network servers, web applications, or APIs [7]. This highlights the critical need for strong technical controls. Organizations that fail to implement HIPAA-compliant APIs or proper encryption face civil monetary penalties of up to $1.5 million per violation category per year [7].
Access Control and Authorization
HIPAA requires unique user identification and measures to ensure only the necessary access to ePHI is granted. For APIs, this means issuing unique credentials for every user and integration. For instance, a telehealth API should assign separate OAuth 2.0 client IDs to each third-party app instead of using a shared API key.
Protocols like OAuth 2.0 and OpenID Connect are commonly used to manage access control in healthcare APIs. OAuth 2.0 handles authentication and delegation, while scoped permissions restrict access to only what's needed. For example, a patient-facing app might receive a token with scopes such as patient/*.read, allowing read-only access to that individual’s records. Meanwhile, a clinician portal might use tokens with scopes like user/*.read and user/*.write, granting controlled access to patient data. Internally, role-based or attribute-based access control can further limit API resources based on user roles. Additional safeguards such as multi-factor authentication, strict credential management, and binding agreements with external partners ensure compliance with HIPAA’s stringent standards.
Data Integrity and Transmission Security
HIPAA requires that ePHI remains protected against unauthorized changes and that mechanisms verify data integrity. APIs can achieve this by using cryptographic hashes and checksums to detect tampering. For instance, a system might compute an SHA-256 hash of a FHIR bundle or claim file, include it in a header, and then have the receiving system verify the hash to confirm the data was not altered during transmission. Digital signatures for JSON Web Tokens or FHIR documents also help confirm the sender’s identity and ensure the content hasn’t been modified.
For transmission security, HIPAA mandates that ePHI be protected during electronic transfer. Healthcare APIs should enforce HTTPS with TLS 1.2 or higher, using modern cipher suites. Additional measures like HTTP Strict Transport Security (HSTS), secure cookie flags, and certificate pinning for mobile apps help guard against downgrade attacks and man-in-the-middle threats. Network-level protections, such as VPNs or private connections for cross-boundary integrations, and regular testing of TLS configurations should also be part of a broader HIPAA security risk management strategy. The ONC/HealthIT.gov guide on healthcare APIs provides practical recommendations to meet these requirements.
Audit Controls and Logging
After ensuring data integrity and secure transmission, robust audit controls are essential for monitoring API activity. HIPAA requires systems to record and review activity in environments handling ePHI. A compliant API should log critical details like timestamps, unique identifiers, source IPs, request methods, endpoints, and actions involving ePHI. It should also track security-relevant events, such as failed login attempts, permission denials, or rate-limiting actions.
To minimize risk, logs should avoid including raw ePHI, using resource identifiers instead. If ePHI must be logged for troubleshooting, access to these logs should be tightly controlled, and the data should be encrypted at rest. Logs should also be stored in systems that prevent tampering, such as append-only storage or cryptographically signed logs, ensuring their reliability for compliance reviews or investigations.
Centralizing logs in a Security Information and Event Management (SIEM) or similar platform can streamline compliance. These platforms enforce role-based access and manage changes, while real-time log transmission from API gateways ensures timely monitoring. Access to logs should be limited to authorized security and compliance teams, with all log access being monitored and reviewed regularly. Automated alerts in the SIEM can identify suspicious behavior, like repeated failed logins or unusual access patterns, enabling quick responses to potential threats.
For organizations managing numerous third-party services and API-based systems, platforms like Censinet RiskOps™ simplify risk assessments, evaluate API vendor security controls, and provide continuous monitoring of risks tied to PHI, clinical applications, and medical devices reliant on APIs.
Best Practices for Secure API Design in Healthcare
Creating a HIPAA-compliant API starts with building security into every step of the design process. From the very first line of code, ensure that each endpoint enforces strong authentication, implements role-based authorization, encrypts Protected Health Information (PHI) both in transit (using TLS 1.2 or higher) and at rest (with modern encryption methods), and validates all inputs and outputs to prevent injection attacks or data leaks. Detailed audit logging should also be baked into the system. Regular design reviews are essential to map API behaviors directly to HIPAA safeguards [2][6][8]. Below, we’ll dive into the key strategies for designing secure healthcare APIs.
Adopting FHIR and Other Healthcare Standards
Building APIs around established healthcare standards like HL7 FHIR, HL7 v2, or DICOMweb is critical for achieving both interoperability and security. FHIR, in particular, has become the go-to standard for modern healthcare APIs. It uses RESTful endpoints with JSON or XML over HTTPS to exchange clinical data [3][4][6]. Developers should structure APIs around FHIR resources like Patient, Observation, Encounter, and MedicationRequest. By leveraging FHIR’s built-in search parameters, resource structures, and error codes, you can simplify development and align with CMS interoperability rules. These rules require payers to support FHIR-based APIs for workflows like patient access, provider access, and prior authorization [3][4].
For imaging APIs, DICOMweb standards (like WADO-RS, QIDO-RS, and STOW-RS) provide consistent approaches to authentication, metadata management, and identifier handling [3]. While these standards don’t guarantee HIPAA compliance, they help centralize semantics and reduce errors, making it easier to implement security controls around PHI [2][3][4].
Once your API aligns with these standards, it’s time to dig deeper into security by conducting structured threat modeling.
Implementing Threat Modeling for PHI Protection
Threat modeling is a must for safeguarding PHI. Start by creating a data-flow diagram that maps out how PHI enters, moves through, and exits your system. This should include API gateways, backend services, storage locations, and third-party integrations [2][6]. Use the STRIDE framework to identify potential threats, such as weak authentication, broken object-level authorization (e.g., one patient accessing another’s records by tweaking an ID), injection attacks, insecure storage access, and data leaks via compromised third-party apps [2][6][9].
For each identified threat, outline specific mitigations. For example:
- Use parameterized queries and input validation to block injection attacks.
- Apply rate limiting and anomaly detection to catch suspicious activity.
- Protect data with network segmentation and robust encryption key management.
- Continuously scan for vulnerabilities to address new threats early [2][6][9].
Keep your threat model up to date, especially when adding new endpoints, integrating partners, or changing how PHI flows through your system. This proactive approach ensures that risks are identified and mitigated before they reach production [2][6].
With these protections in place, focus on limiting the exposure of sensitive data to comply with HIPAA’s "minimum necessary" standard.
Minimizing PHI Exposure in API Payloads
Under HIPAA’s "minimum necessary" standard, APIs should only expose the PHI needed for a specific purpose [2][5][6]. Implement field-level whitelisting to ensure endpoints return only approved attributes. For example, a scheduling API for a patient kiosk might provide just initials, appointment times, and anonymized IDs, while a clinician-facing app could access full demographics and clinical history [2][4][6].
Avoid exposing sensitive identifiers like Medical Record Numbers or Social Security Numbers in URLs, as they can leak through logs or proxies. Instead, use opaque, non-guessable identifiers in API paths, while keeping sensitive data in encrypted storage with strict access controls [2][6]. Free-text clinical notes pose a high risk due to incidental PHI. Separate these into dedicated resources with specific permissions, avoid bulk returns, and offer redacted or summarized versions when full text isn’t necessary [2][6][9]. For analytics or testing, de-identify data by removing direct identifiers, shifting dates, or aggregating information so that it no longer qualifies as PHI under HIPAA [1][2][6].
When working with third-party apps or vendors, treat them as business associates and require signed Business Associate Agreements (BAAs) before granting API access [2][8][9]. Conduct thorough security reviews of their architecture, authentication protocols, and data handling practices. Limit access to only the scopes and endpoints they need. Use monitoring tools like API analytics, rate limiting, and anomaly detection to spot misuse. Rotate keys or tokens immediately if risks are identified or contracts change [2][6][9].
For organizations managing many third-party integrations, platforms like Censinet RiskOps™ can streamline risk assessments, evaluate vendor security controls, and provide ongoing monitoring of risks tied to PHI, clinical applications, and medical devices that rely on APIs. This ensures a robust security posture across your API ecosystem.
Deployment Strategies for HIPAA-Compliant APIs
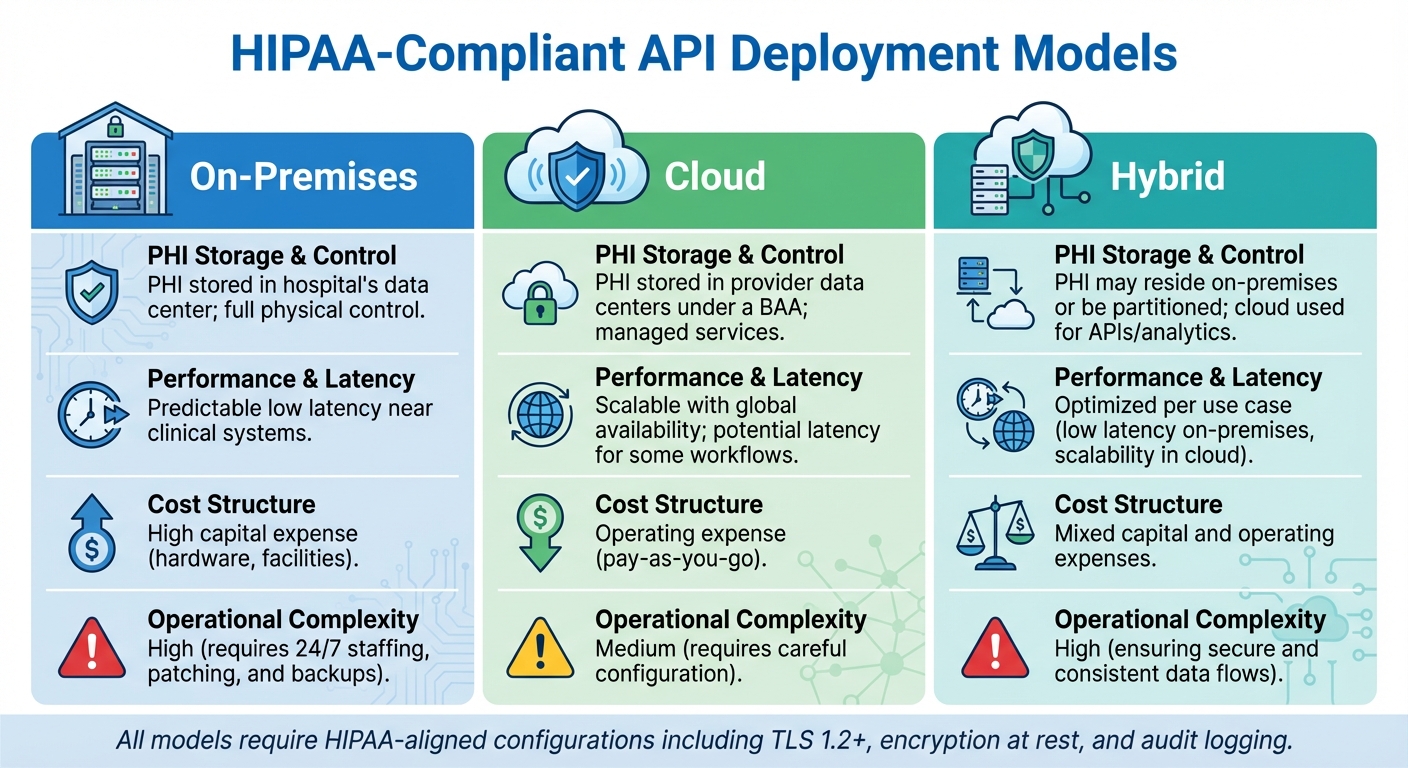
HIPAA-Compliant API Deployment Models: On-Premises vs Cloud vs Hybrid Comparison
Deciding where to host your healthcare APIs - whether on-premises, in the cloud, or through a hybrid setup - directly affects how you protect PHI, meet performance demands, and manage operational challenges. Each option comes with its own set of advantages and limitations regarding control, cost, scalability, and the effort needed to maintain HIPAA safeguards. By understanding these differences, you can align your deployment strategy with clinical needs and regulatory requirements. Below, we break down the key aspects of each deployment model.
Comparing On-Premises, Cloud, and Hybrid Architectures
On-premises deployments keep all API infrastructure and PHI within your organization’s data center. This model offers direct control over physical security and seamless integration with legacy EHR systems. Many hospitals favor this approach for handling highly sensitive data. However, it comes with high upfront costs and requires ongoing maintenance for hardware, security, and disaster recovery, making it resource-intensive.
Cloud deployments rely on HIPAA-eligible cloud services governed by a Business Associate Agreement (BAA). The Department of Health and Human Services (HHS) allows cloud hosting of ePHI as long as safeguards like encryption, access controls, and risk management are in place. Cloud platforms provide managed security controls and scalable performance, shifting costs from capital expenses to operating expenses. However, these deployments demand careful configuration to manage shared responsibility, ensure compliance with data residency rules, and prevent misconfigurations. When properly set up, cloud-hosted API gateways can simplify integration and enhance scalability.
Hybrid architectures combine the strengths of both on-premises and cloud models. Core clinical systems and primary EHR data often remain on-premises, while API gateways, analytics platforms, and patient-facing services run in HIPAA-compliant cloud environments. This setup allows low-latency processing for clinical workflows while leveraging cloud scalability for less critical tasks. However, hybrid models require secure connections - such as VPNs or private links - and consistent security practices across both environments.
| Deployment Model | PHI Storage & Control | Performance & Latency | Cost Structure | Operational Complexity |
|---|---|---|---|---|
| On-Premises | PHI stored in the hospital’s data center; full physical control | Predictable low latency near clinical systems | High capital expense (hardware, facilities) | High (requires 24/7 staffing, patching, and backups) |
| Cloud | PHI stored in provider data centers under a BAA; managed services | Scalable with global availability; potential latency for some workflows | Operating expense (pay-as-you-go) | Medium (requires careful configuration) |
| Hybrid | PHI may reside on-premises or be partitioned; cloud used for APIs/analytics | Optimized per use case (low latency on-premises, scalability in cloud) | Mixed capital and operating expenses | High (ensuring secure and consistent data flows) |
When selecting a deployment model, consider where PHI will be stored, the latency requirements of clinical workflows, integration with existing EHR systems, and your team’s security expertise. Each setup must be configured to meet HIPAA’s stringent PHI protection standards.
HIPAA-Aligned Configuration Practices
Regardless of the deployment model, your API infrastructure must adhere to the HIPAA Security Rule’s technical safeguards, including access control, audit controls, data integrity, authentication, and transmission security. Here’s how to meet these requirements:
- Secure communications: Use TLS 1.2 or higher for all endpoints, disable weak ciphers, and enable HTTP Strict Transport Security (HSTS) to prevent plaintext HTTP connections.
- Authentication and authorization: Implement strong authentication protocols like OAuth 2.0 or OpenID Connect with short-lived tokens. Enforce role-based or attribute-based access controls to ensure compliance with the "minimum necessary" principle.
- Abuse prevention: Apply rate limiting, request size limits, and IP allow/deny lists to administrative endpoints. Normalize error messages to avoid exposing sensitive information.
- Cloud-specific measures: Use native cloud gateway services with private networking (e.g., private endpoints or VPC integration) to avoid exposing APIs directly to the public internet.
For network security, restrict access to APIs using private networks, firewalls, and zero-trust principles. Place API servers and PHI-handling data stores in restricted subnets with default-deny firewall rules, opening only essential ports. In cloud setups, use private subnets controlled by load balancers or API gateways, along with security groups and network ACLs. For hybrid environments, secure on-premises-to-cloud connections with VPNs or private links, and adopt zero-trust practices such as mutual TLS and continuous authentication.
Encryption at rest is equally critical. Use strong algorithms like AES-256 for databases, file systems, and object storage containing PHI. In cloud environments, enable provider-managed encryption services and, where necessary, use customer-managed keys. On-premises setups should employ hardware security modules (HSMs) or enterprise key managers, with documented key rotation and recovery procedures. Consistent encryption practices across hybrid setups ensure PHI remains secure throughout its lifecycle.
Centralized logging and monitoring are vital for HIPAA compliance. APIs should generate structured logs that capture authentication events, authorization decisions, errors, and system changes. Ensure logs exclude unnecessary PHI, and use redaction or tokenization when minimal identifiers are needed. Consolidate logs into a secure platform or SIEM for continuous monitoring. Detect anomalies like failed logins or unusual access patterns to address potential threats quickly.
For organizations with multiple third-party integrations, tools like Censinet RiskOps can help assess vendor risks tied to API connections and flag high-risk integrations for remediation. Once secure configurations are in place, the focus shifts to maintaining continuity through disaster recovery and high availability.
Disaster Recovery and High Availability
APIs supporting critical clinical workflows - such as medication administration or imaging - must align with HIPAA’s contingency planning requirements. Start with a business impact analysis to define Recovery Time Objectives (RTOs) and Recovery Point Objectives (RPOs) for each API based on its role in clinical operations. Mission-critical APIs often require near-zero data loss and rapid failover.
Disaster recovery plans should include encrypted backups stored offsite, detailed recovery procedures, and defined roles and communication plans. Regular testing of these plans ensures readiness. In cloud environments, deploying across multiple availability zones - or even regions - can enhance resilience and maintain operational continuity.
sbb-itb-535baee
Governance, Risk, and Compliance for API Ecosystems
After designing robust APIs and ensuring secure deployment, the next challenge lies in maintaining their integrity over time. Deploying HIPAA-compliant APIs is only the beginning; ongoing governance and risk management are essential to ensure they remain secure and compliant. API ecosystems are dynamic, constantly adapting to new integrations and threats. Without structured governance, even well-crafted APIs can fall out of compliance or inadvertently expose Protected Health Information (PHI). To address this, organizations need to embed HIPAA safeguards into every phase of the API lifecycle - from design to deprecation - while staying vigilant about third-party integrations and emerging risks.
Continuous API Security Monitoring
Real-time monitoring plays a critical role in identifying and mitigating potential security breaches before they escalate. Centralizing API logs in a Security Information and Event Management (SIEM) system can help detect anomalies like unusual query patterns, repeated login failures, access from unexpected locations, or bulk data extractions from FHIR Patient resources. Behavioral analytics can establish a baseline for normal activity, such as typical access times, user roles, and device types. Alerts can then be triggered when deviations occur - for instance, if a patient-access app starts querying unrelated patient records or if a provider token is used to export large datasets outside of clinic hours.
Audit logs are another essential component, capturing details such as who accessed PHI, when, from where, and what actions were performed (read, create, update, delete). These logs should include timestamps (in U.S. time zones), user or system identities, patient record IDs, calling IPs, client/app IDs, API methods, endpoints, and request outcomes. Strict access controls and retention policies aligned with HIPAA guidelines are a must. Regular log reviews, particularly for high-risk APIs, should be part of the routine. Integrating monitoring into incident response plans enables security teams to act swiftly - revoking credentials, tightening gateway rules, or disabling compromised endpoints as needed. These practices are equally vital for overseeing third-party integrations.
Third-Party Risk Management for API Integrations
With over 60% of healthcare data breaches involving third parties or business associates, managing vendor risks is a cornerstone of API governance. Start by cataloging all third-party APIs and vendors that handle PHI, including cloud platforms, EHR integrations, telehealth providers, billing systems, analytics tools, and messaging services. Before exchanging any PHI, require Business Associate Agreements (BAAs) that outline security controls, breach notification timelines, and subcontractor obligations. Security questionnaires and evidence reviews - such as SOC 2 reports, penetration test results, and HIPAA program documentation - should focus on critical areas like encryption, access controls, logging, and incident response.
Vendors should be categorized based on the sensitivity of the data they handle and their critical role in operations. High-risk integrations warrant more frequent assessments and deeper scrutiny. Ongoing management practices should include periodic reassessments, tracking vendor security advisories, and implementing technical safeguards like IP allowlists, mutual TLS, and scoped API keys to minimize exposure in case of a breach. APIs should also enforce least-privilege access, granting each vendor only the PHI necessary for their role. For example, a billing vendor might access patient demographics and billing codes but not full clinical records.
Terry Grogan, CISO at Tower Health, highlighted the efficiency gains achieved through streamlined risk management tools:
"Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required." - Terry Grogan, CISO, Tower Health
This demonstrates how effective platforms can enhance resource allocation while improving the volume and quality of risk assessments.
Using Censinet for Cyber Risk Management
For healthcare organizations, tools like Censinet RiskOps™ offer a centralized approach to managing third-party risk assessments for vendors handling PHI through API integrations. By replacing manual processes with a digital platform, Censinet consolidates risk data and streamlines workflows. Its network, encompassing over 50,000 vendors and products across the healthcare sector, facilitates secure sharing of cybersecurity information. This centralized visibility helps organizations prioritize remediation efforts for high-risk integrations, particularly those tied to EHRs, clinical applications, or medical devices.
Integrating Censinet into procurement processes ensures that no API vendor handling PHI is approved without a completed risk assessment and mitigation plan. The platform supports ongoing reassessments, tracks remediation activities, and fosters collaboration between security teams, IT, clinical stakeholders, and vendors. This is especially critical when new APIs are added or existing ones undergo changes. By aggregating risk data and industry benchmarks, Censinet not only identifies systemic vulnerabilities - such as gaps in API logging or insufficient multi-factor authentication - but also feeds these insights back into internal API standards. In the event of a PHI-related incident, these practices demonstrate due diligence to regulators and auditors.
Brian Sterud, CIO at Faith Regional Health, emphasized the importance of benchmarking:
"Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters." - Brian Sterud, CIO, Faith Regional Health
Matt Christensen, Sr. Director GRC at Intermountain Health, highlighted the necessity of tailored solutions for healthcare's complexities:
"Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare." - Matt Christensen, Sr. Director GRC, Intermountain Health
Conclusion
For U.S. healthcare organizations, ensuring HIPAA-compliant API integration is not just a regulatory requirement - it’s the backbone of secure interoperability, patient access, and advancing digital care solutions. Beyond avoiding penalties, secure APIs play a crucial role in protecting patient trust, minimizing breach risks, and enabling new care models in a safe and controlled manner. By adopting security-first APIs, healthcare providers can safeguard critical workflows, medical devices, and supply chain connections.
To achieve this, organizations need a structured and phased approach to implementation. Within the first 30 days, identify all APIs that interact with PHI and address any immediate vulnerabilities. Over the next 90 days, update security protocols and governance frameworks. Within 12 months, focus on modernizing outdated interfaces and aligning software development practices with HIPAA and NIST standards. For vendors and startups classified as business associates, it’s vital to confirm your BA status, execute Business Associate Agreements (BAAs) with all clients and subcontractors, adopt secure development practices that include threat modeling, and comply with HIPAA Security Rule specifications and NIST guidance.
Maintaining compliance goes beyond technical safeguards - it requires ongoing governance and risk management. This includes real-time monitoring of API activity for suspicious behavior, conducting regular risk assessments after significant changes, maintaining centralized API catalogs with clear ownership, and having incident response plans specifically designed for API-related breaches. Equally important is continuous training for developers and clinical application managers on securely handling PHI. For third-party integrations, such as those with EHR systems, telehealth platforms, or billing providers, thorough due diligence is non-negotiable. Tools like Censinet RiskOps™ can simplify third-party and enterprise risk management by assisting healthcare organizations in assessing cybersecurity risks, benchmarking performance, and managing vendor oversight effectively across PHI-dependent ecosystems.
The transition to FHIR-based APIs is reshaping how healthcare data is exchanged. With CMS/ONC interoperability rules making API integration a central focus, the stakes are high. Considering that over 80% of reported HIPAA breach records stem from hacking and IT incidents [9], and healthcare remains one of the most targeted industries, prioritizing secure API design is no longer optional - it’s a strategic necessity. Achieving HIPAA compliance demands not only strong technical controls but also a commitment to robust organizational governance.
FAQs
What technical safeguards are essential for ensuring HIPAA compliance in APIs?
To ensure APIs meet HIPAA requirements, it's important to implement strong technical measures. Start by encrypting data both when stored and while being transmitted. This ensures sensitive information remains secure. Next, enforce strong authentication and access controls to limit access to only authorized users. Keeping detailed audit logs is also essential to monitor and track all access and activities related to the data.
APIs should also be built with security in mind. This includes using proper input validation and sanitization to block common vulnerabilities. Regular vulnerability assessments are equally important to spot and fix potential security issues before they become problems.
These steps are key to safeguarding patient data and meeting HIPAA's strict standards for confidentiality, integrity, and availability.
What’s the best way for healthcare organizations to manage third-party risks in API integrations?
Healthcare organizations can tackle third-party risks in API integrations by using advanced risk management platforms such as Censinet RiskOps™. These platforms offer automated tools for risk assessments, real-time monitoring, and detailed insights into potential vulnerabilities. This approach not only helps maintain HIPAA compliance but also protects sensitive patient information.
By simplifying cybersecurity evaluations and enabling proactive measures, healthcare providers can better secure clinical applications, medical devices, and other essential systems, all while staying aligned with regulatory requirements.
What are the best strategies to ensure HIPAA compliance when integrating APIs in healthcare systems?
When integrating APIs in healthcare, maintaining HIPAA compliance is all about keeping patient data secure. Start by implementing secure authentication, encryption, and access controls to ensure sensitive information stays protected. On top of that, conducting regular risk assessments and compliance audits is essential for spotting and addressing potential vulnerabilities.
To make compliance more manageable, consider using specialized risk management tools, like AI-driven platforms. These can help by continuously monitoring for risks and reinforcing data security measures. Partnering with vendors who understand healthcare regulations and using cybersecurity frameworks tailored to the industry can also play a big role in protecting protected health information (PHI).
Related Blog Posts
Key Points:
What is a HIPAA-compliant API?
- Definition: A HIPAA-compliant API is an Application Programming Interface designed to securely handle Protected Health Information (PHI) in compliance with HIPAA’s Privacy, Security, and Breach Notification Rules.
- Purpose: It ensures that healthcare applications, systems, and websites can exchange PHI securely without violating HIPAA regulations.
Why is API integration important in healthcare?
- Real-Time Data Exchange: APIs enable seamless communication between systems like EHRs, patient portals, and billing platforms, improving care coordination.
- Operational Efficiency: Automates workflows, reduces manual data entry, and minimizes errors.
- Patient Outcomes: Enhances patient engagement by providing secure access to health records and real-time updates.
What safeguards are required for HIPAA-compliant APIs?
- Encryption: PHI must be encrypted both in transit (e.g., TLS 1.2+) and at rest (e.g., AES-256).
- Access Controls: Implement role-based access and least-privilege principles to limit who can access PHI.
- Audit Logging: Maintain detailed logs of API interactions to track access and detect unauthorized activity.
- Data Minimization: Adhere to the "minimum necessary" principle, ensuring APIs only handle the data required for specific tasks.
What are the challenges of implementing HIPAA-compliant APIs?
- Interoperability: Ensuring APIs work seamlessly across different systems and standards like FHIR and HL7.
- Legacy Systems: Many healthcare organizations rely on outdated systems that lack modern API capabilities.
- Compliance Complexity: Balancing security, scalability, and compliance with HIPAA and other regulations.
- Authentication: Managing complex identity and access management across multiple systems.
What are the benefits of using HIPAA-compliant APIs?
- Enhanced Security: Protects sensitive patient data from breaches and unauthorized access.
- Regulatory Compliance: Ensures adherence to HIPAA, GDPR, and other data protection standards.
- Streamlined Workflows: Automates data exchange, reducing administrative burdens.
- Improved Patient Outcomes: Enables real-time data sharing for better care coordination.
How can organizations ensure API compliance with HIPAA?
- Secure API Gateways: Use gateways with OAuth 2.0 for authentication and centralized logging.
- Encryption: Encrypt all PHI in transit and at rest using strong encryption protocols.
- Regular Audits: Conduct periodic security assessments and penetration testing.
- Business Associate Agreements (BAAs): Ensure BAAs are in place with all vendors handling PHI.


