HIPAA Compliance for Vendor Onboarding
Post Summary
Managing vendors who handle Protected Health Information (PHI) is a critical responsibility under HIPAA regulations. Without proper safeguards, healthcare organizations risk data breaches, fines, and reputational harm. Here's what you need to know:
- Business Associate Agreements (BAAs) are mandatory for any vendor accessing PHI. Missing or incomplete BAAs are a leading cause of HIPAA violations.
- Vendors must comply with HIPAA's Privacy Rule, Security Rule, and Breach Notification Rule, ensuring PHI is protected at every level.
- A structured onboarding process involves vendor classification, documentation review, risk assessments, and training before granting access to PHI.
- Using centralized tools like Censinet RiskOps™ can simplify compliance tracking and reduce manual errors.
Key takeaway: A well-documented, step-by-step onboarding process ensures vendors meet HIPAA requirements before accessing sensitive data, minimizing risks and supporting regulatory compliance.
HIPAA Requirements for Vendors
HIPAA Rules That Apply to Vendors
HIPAA has three key regulations that guide how vendors must handle Protected Health Information (PHI). First, the Privacy Rule restricts the use of PHI to the purposes outlined in the vendor’s contract. Second, the Security Rule requires vendors to implement administrative, physical, and technical safeguards to protect electronic PHI (ePHI). Finally, the Breach Notification Rule obligates vendors to notify the covered entity of any breach within 60 days so that impacted individuals and the HHS Office for Civil Rights can be informed.
Additionally, any staff members who handle PHI must undergo HIPAA and security awareness training. Maintaining records of this training is critical for audits and compliance reviews. Unfortunately, this step is often overlooked during onboarding, but it plays a vital role in meeting regulatory requirements [2][3].
The next step is determining whether the vendor qualifies as a business associate under HIPAA.
Determining Business Associate Status
A vendor is considered a business associate if it creates, receives, maintains, or transmits PHI on behalf of a covered entity. Common examples include billing companies, cloud storage providers, IT consultants, shredding services, and legal firms. The defining factor is whether the vendor has access to PHI, regardless of its format.
Subcontractors working for a business associate are also bound by HIPAA if they handle PHI. For instance, if a billing company uses a cloud hosting provider to store patient data, that hosting provider must also comply with HIPAA requirements. During onboarding, it’s crucial to ensure vendors have appropriate agreements in place with their subcontractors, ensuring HIPAA obligations extend throughout the supply chain.
Once a vendor’s business associate status is confirmed, onboarding must include detailed documentation of their HIPAA safeguards.
How HIPAA Affects Onboarding
HIPAA introduces specific checkpoints into the vendor onboarding process to ensure compliance before granting access to PHI. It’s not enough to take a vendor’s word that they are "HIPAA compliant." Instead, you need documented proof of their safeguards. This includes collecting and reviewing security questionnaires, policies, and procedures, validating encryption practices, and confirming their incident response plans.
A fully executed Business Associate Agreement (BAA) is a non-negotiable requirement before allowing any access to PHI. Missing or incomplete BAAs significantly increase compliance risks. The onboarding process should also include a thorough risk assessment to verify that the vendor’s controls meet the standards outlined in the Security Rule. Any gaps identified must be documented and addressed before the vendor is activated.
Building a HIPAA-Compliant Onboarding Framework
With HIPAA regulations in place, having a structured onboarding process ensures vendors consistently meet compliance requirements.
Stages of the Onboarding Process
A HIPAA-compliant onboarding framework typically includes these key steps: vendor classification, documentation review, contracting with HIPAA clauses, technical access setup, and training before go-live.
- Vendor Classification: Determine if the vendor qualifies as a business associate and assess their potential exposure to protected health information (PHI).
- Documentation Review: Collect necessary materials such as security questionnaires and policies to evaluate the vendor's compliance posture.
- Contracting: Execute Business Associate Agreements (BAAs) and include HIPAA-specific clauses like breach notification timelines, audit rights, subcontractor oversight, and training obligations.
- Technical Access Setup: Establish access controls and verify the use of encryption to protect PHI.
- Training and Go-Live: Require vendors to complete HIPAA training and confirm adherence to policies before granting access to PHI.
To ensure nothing falls through the cracks, it's crucial to establish clear handoffs between compliance, security, legal, procurement, and business teams. Without clearly defined roles, critical steps - like executing a BAA - can be missed. Document each stage carefully and maintain an audit trail for accountability.
Using Centralized Systems to Track Compliance
Once the onboarding stages are defined, using a centralized system can simplify compliance tracking. Relying on manual spreadsheets often leads to gaps in documentation and reduced visibility across multiple vendors. A centralized solution addresses these issues by consolidating vendor information, compliance documentation, and assessment results in one place.
For example, Censinet RiskOps™ is a cloud-based platform designed specifically for healthcare organizations to manage third-party risk. It enables secure sharing of cybersecurity and risk data within a collaborative network of healthcare providers and over 50,000 vendors.
"Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required." - Terry Grogan, CISO at Tower Health
"Not only did we get rid of spreadsheets, but we have that larger community [of hospitals] to partner and work with." - James Case, VP & CISO at Baptist Health
Standardizing Risk Assessments and Workflows
Centralized tracking becomes even more effective when paired with standardized risk assessments. Using consistent questionnaires, risk scoring methods, and approval workflows helps ensure thorough and uniform evaluations, reducing the risk of compliance gaps.
Platforms like Censinet RiskOps™ streamline this process by automating workflows. Vendors can submit completed security questionnaires and supporting documentation early, cutting down on unnecessary back-and-forth. The platform also allows organizations to benchmark their controls against industry standards, helping identify areas for improvement.
"Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters." - Brian Sterud, CIO at Faith Regional Health
HIPAA Compliance Documentation Checklist
When setting up a HIPAA onboarding framework, having the right documentation is critical. This checklist outlines the key documents needed to ensure compliance, minimize risks, and streamline vendor onboarding.
Business and Legal Documents
Start with the basics: gather the vendor's corporate charter, W-9 form, and an organizational chart identifying key contacts for security, privacy, and legal matters. These documents establish the vendor's legitimacy and provide a foundation for further evaluations.
Risk and Security Documents
To assess a vendor's security measures, request third-party assurance reports like SOC 2 Type II and HITRUST CSF certification. Additionally, secure their information security policies, which should cover areas such as data classification, access controls, and incident response protocols. Ask for recent security risk assessments, penetration testing results, and vulnerability scans (completed within the past 12 months). Once these are in place, shift your attention to HIPAA-specific documentation to address compliance requirements.
HIPAA-Specific Evidence
The Business Associate Agreement (BAA) is a cornerstone of HIPAA compliance. Ensure the BAA outlines the permitted uses of PHI, safeguards for its protection, breach notification processes, and subcontractor obligations. Also, collect HIPAA training documentation, which should include the training curriculum, records of completed sessions, and the frequency of training (typically during onboarding and annually). Additionally, request written breach notification procedures that detail how breaches are detected, assessed, and reported - ensuring the timeline aligns with the 60-day requirement. Finally, obtain a subcontractor inventory listing all downstream vendors with access to PHI and proof that they’ve signed their own BAAs.
Technical and Privacy Controls
Secure technical documentation to confirm the vendor's ability to handle PHI securely. This should include details on encryption standards for data at rest (e.g., AES-256) and in transit (e.g., TLS 1.2 or higher). Request information about access control mechanisms, such as role-based access controls (RBAC), unique user IDs, multi-factor authentication, and automatic session timeouts. Ensure they provide documentation for audit logging and monitoring, capturing access to ePHI, administrative changes, and failed login attempts, with logs retained for at least six years. Additionally, gather their data backup and recovery procedures, specifying backup frequency, storage locations (preferably within the U.S.), retention periods, and tested recovery objectives. Finally, request the vendor’s incident response plan, which should outline steps for detecting, containing, investigating, and addressing security incidents effectively.
sbb-itb-535baee
Step-by-Step HIPAA Onboarding Workflow
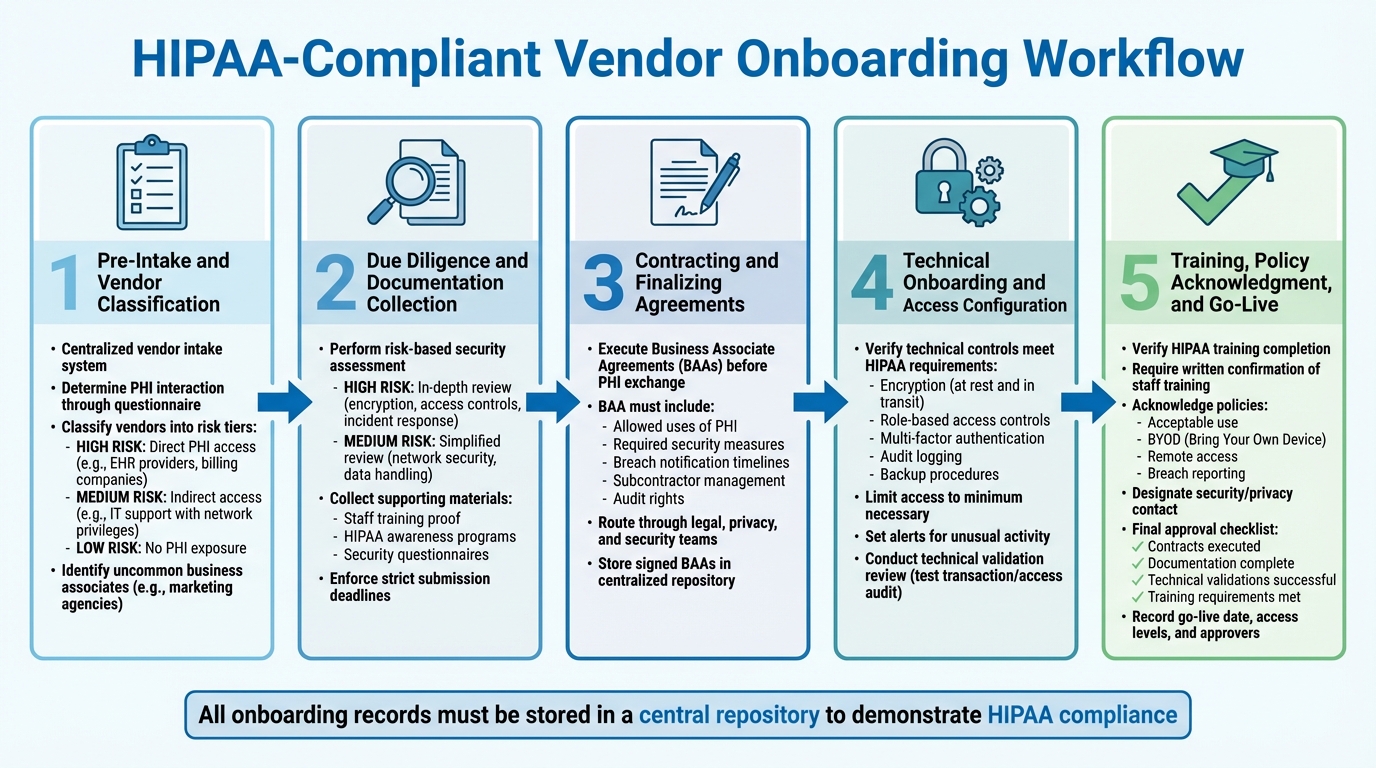
5-Step HIPAA-Compliant Vendor Onboarding Workflow for Healthcare Organizations
This process ensures vendors comply with HIPAA regulations before they gain access to Protected Health Information (PHI). Every step is documented to meet audit requirements.
Pre-Intake and Vendor Classification
Start with a centralized vendor intake system to log and route new engagements for PHI and HIPAA review before any purchases or access to systems occur. Use a detailed questionnaire to determine whether a vendor will interact with PHI. Based on their responses, classify vendors into risk tiers:
- High Risk: Vendors with direct PHI access, like electronic health record (EHR) providers or billing companies.
- Medium Risk: Vendors with indirect access, such as IT support teams with network privileges.
- Low Risk: Vendors with no PHI exposure.
Additionally, identify uncommon business associates, like marketing agencies managing patient testimonials, and ensure proper Business Associate Agreements (BAAs) and risk reviews are in place.
Due Diligence and Documentation Collection
After classification, perform due diligence tailored to the vendor's risk level. For high-risk vendors, conduct an in-depth security assessment covering encryption, access controls, and incident response protocols. Medium-risk vendors may require a simplified review focused on network security and data handling. Collect supporting materials, such as proof of staff training and HIPAA awareness programs.
Platforms like Censinet RiskOps™ make this process more efficient by enabling healthcare organizations to securely share cybersecurity and risk data with over 50,000 vendors. Centralize all documentation and enforce strict deadlines for submission.
"Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required." - Terry Grogan, CISO, Tower Health [1][2]
Contracting and Finalizing Agreements
Before any PHI is exchanged, execute BAAs and review existing contracts to ensure they align with HIPAA standards. These agreements should clearly outline:
- Allowed uses of PHI
- Required security measures
- Breach notification timelines
- Subcontractor management responsibilities
- Audit rights
Incorporate security obligations into the contracts, and route them through legal, privacy, and security teams for approval. Store all signed BAAs in a centralized repository linked to the vendor record. Once contracts are finalized, proceed to technical onboarding.
Technical Onboarding and Access Configuration
Before granting access, confirm the vendor's technical controls meet HIPAA requirements. This includes verifying encryption, role-based access, multi-factor authentication, audit logging, and backup procedures. Ensure access is limited to the minimum necessary and set alerts for unusual activity. Conduct a technical validation review - such as a test transaction or access audit - before allowing live access to PHI. These steps act as the final checkpoint to ensure compliance.
Training, Policy Acknowledgment, and Go-Live
Before granting live access, verify that the vendor has completed all necessary HIPAA training and policy acknowledgments. Require vendors to:
- Provide written confirmation that relevant staff have completed HIPAA training.
- Acknowledge policies on acceptable use, BYOD (Bring Your Own Device), remote access, and breach reporting.
- Designate a security or privacy contact for escalations.
Final production access and go-live approval should only occur after confirming that contracts are executed, documentation is complete, technical validations are successful, and training requirements are met. Record the go-live date, approved access levels, and the names of approvers, and store all onboarding records in a central repository to demonstrate compliance with HIPAA's training and documentation standards.
Maintaining HIPAA Compliance Over Time
Once you've set up a solid onboarding process, the next challenge is ensuring vendors stay compliant as situations change. Vendors might update their infrastructure, merge with other companies, experience breaches, or expand their services - each of these changes can impact HIPAA compliance. Without continuous oversight, these risks might only come to light during audits or after incidents occur. Regular monitoring builds on the onboarding foundation to help address potential problems before they escalate.
Regular Reviews and Documentation Updates
Set up a review schedule for vendors based on their risk level. For instance, vendors that directly handle protected health information (PHI) - like EHR platforms or billing services - should have a full reassessment every year, along with lighter quarterly check-ins. Medium-risk vendors might only need reviews every one to two years. When contracts are renewed, update security questionnaires, reassess risks from any new services or incidents, and revise Business Associate Agreements (BAAs) to reflect these changes [4].
Keep a centralized inventory of all vendors, detailing their classification (such as whether they’re a business associate), involvement with PHI, contact and contract information, dates of the last risk assessment, scheduled review dates, and their current residual risk level [4][5]. Using automated tools to manage this inventory can improve real-time tracking and support ongoing oversight.
Once these periodic reviews are in place, adding real-time monitoring ensures that incidents are addressed as they happen.
Continuous Monitoring of Vendor Risks
Require vendors to notify you immediately of any incidents involving PHI, in line with HIPAA's breach notification rules. Trigger a reassessment whenever a vendor experiences a breach, changes its hosting infrastructure or EHR integration, expands its PHI exposure, or undergoes a merger or acquisition. When offboarding a vendor, use a formal checklist to revoke access, ensure PHI is either returned or destroyed, verify data disposition, and document the entire process [4][5].
Using Tools for Automation and Evidence Management
Platforms like Censinet RiskOps™ can streamline the process by moving beyond static questionnaires to a more dynamic risk management approach. This tool automates the distribution of questionnaires and reassessments, centralizes vendor-related documents (such as BAAs, SOC 2 reports, penetration tests, and security policies), and offers dashboards for audits and board-level reporting. Its collaborative risk network securely shares cybersecurity and risk data with over 50,000 vendors, making it easier to collect and update evidence [1].
Conclusion
Ensuring HIPAA compliance during vendor onboarding is a critical step in protecting patient data and strengthening overall security. By following a structured process, healthcare organizations can verify that every vendor handling protected health information (PHI) meets the necessary safeguards before gaining access. This involves setting up clear workflows for categorizing vendors, gathering essential documentation, signing Business Associate Agreements (BAAs), and conducting risk-based assessments tailored to the level of PHI exposure each vendor has.
But onboarding is just the beginning. Maintaining compliance requires ongoing effort. Regular monitoring, periodic reassessments, and keeping documentation up to date are vital to address changes in vendor systems, respond to potential breaches, and stay aligned with evolving HIPAA regulations. Healthcare organizations often juggle unique challenges, like limited resources, large vendor networks, and the complexities of managing risks across clinical tools, medical devices, and supply chains. Without proper systems in place, these demands can quickly overwhelm compliance and security teams.
Platforms like Censinet RiskOps™ offer a practical solution. By automating and centralizing vendor risk management, such tools help streamline oversight and reduce manual work. Censinet’s collaborative risk network, which includes over 50,000 vendors, allows healthcare organizations to securely share and access cybersecurity data, boosting efficiency and simplifying vendor management.
Whether you're a compliance leader, security expert, procurement officer, or business owner, starting with a risk-based framework is key. Focus on high-risk vendors, standardize your documentation process, and use automation to scale your efforts. Even small steps - like maintaining a centralized vendor inventory or scheduling annual reassessments - can significantly reduce the risk of HIPAA violations and data breaches.
Ultimately, safeguarding PHI while embracing innovation is essential. A disciplined and well-documented onboarding process not only ensures compliance with HIPAA standards but also fosters patient trust, prepares your organization for audits, and strengthens your ability to manage third-party risks in an ever-changing healthcare environment.
FAQs
Why is a Business Associate Agreement (BAA) essential for HIPAA compliance?
A Business Associate Agreement (BAA) plays a crucial role in ensuring HIPAA compliance. It’s a legal contract that obligates vendors to protect protected health information (PHI), detailing their responsibilities to uphold privacy and security standards as required by HIPAA.
With a BAA in place, healthcare organizations can better safeguard patient data, minimize the risk of breaches, and hold vendors accountable for their actions. It also serves as a key document to show compliance with regulations, fostering trust in partnerships within the healthcare sector.
What steps can healthcare organizations take to ensure vendors comply with HIPAA's Security Rule?
To make sure vendors align with HIPAA's Security Rule, healthcare organizations need to conduct thorough risk assessments and outline clear security measures. Regular checks for system vulnerabilities and enforcing strict data protection standards are key steps in this process.
Platforms like Censinet RiskOps™ can make this task easier. They offer tools for efficient risk assessments, cybersecurity comparisons, and collaborative risk management. These features help healthcare organizations stay ahead of potential risks tied to patient data, clinical tools, and other vital systems, ensuring compliance while protecting sensitive information.
What should a vendor do if they experience a PHI data breach?
If a vendor faces a breach involving Protected Health Information (PHI), quick action is crucial to limit damage and meet HIPAA requirements. The first step is to contain the breach immediately, stopping any further exposure of sensitive data. It’s also essential to notify the impacted healthcare organization and, if required, inform the Department of Health and Human Services (HHS) as outlined by HIPAA regulations.
After containment, evaluate the breach to determine the extent of the compromised information. Document every detail, including how the breach happened, the steps taken to address it, and any measures put in place to prevent it from happening again. Additionally, notify affected individuals without delay, providing them with clear guidance on how to protect themselves.
To prevent future incidents, conduct a root cause analysis to uncover vulnerabilities. Use these findings to update security protocols and implement corrective measures. HIPAA compliance also requires reporting all breaches to the appropriate regulatory bodies, ensuring accountability and transparency.


