HIPAA Rules for Cloud PHI Retention Policies
Post Summary
Healthcare organizations storing Protected Health Information (PHI) in the cloud must comply with HIPAA's strict retention rules. Here's what you need to know:
- HIPAA requires a minimum six-year retention period for documentation like policies, procedures, risk assessments, and Business Associate Agreements (BAAs).
- State laws may require longer retention periods for medical records, especially for minors or specific cases.
- Cloud storage adds complexity, as both healthcare entities and cloud providers share responsibility for securing PHI.
- Key safeguards include encryption, access controls, audit logs, and secure disposal of data once retention periods expire.
- Non-compliance risks include breaches, fines, and legal consequences.
To stay compliant, organizations must document retention policies, configure cloud systems to enforce rules, and ensure secure deletion of expired data. Regular audits and updated BAAs with cloud providers are essential for managing risks effectively.
HIPAA Rules That Impact Retention Policies
HIPAA Cloud PHI Retention Requirements and Implementation Guide
HIPAA retention policies are shaped by three key rules: the Privacy Rule, the Security Rule, and the Breach Notification Rule. These rules lay out specific requirements for managing cloud-based PHI (Protected Health Information). From retention timelines to security protocols, these guidelines should be reflected in your retention strategy to ensure compliance and safeguard sensitive data.
Retention and Documentation Requirements
HIPAA mandates that certain documentation be retained for six years. According to the Privacy Rule (45 C.F.R. § 164.530(j)) and the Security Rule (45 C.F.R. § 164.316(b)(2)), covered entities and business associates must keep records like policies, procedures, risk analyses, Business Associate Agreements (BAAs), audit logs, breach records, training documentation, patient authorizations, and sanctions records for six years from the date they were created or last in effect - whichever is later.
In cloud environments, it’s essential to configure retention settings to ensure these records remain accessible for the entire six-year period, even if platforms or systems change. Features like storage tiers, legal holds, and archival policies can help prevent premature deletion and keep records available for audits or investigations.
Medical records, however, fall under different rules. Their retention periods are often determined by state laws and federal programs like CMS, requiring storage for five to ten years or more. Your cloud retention strategy should clearly separate HIPAA documentation, which has a six-year baseline, from clinical records that may demand longer retention.
As you define retention periods, it’s equally important to integrate robust security measures to protect stored PHI.
Security Rule Standards for Retained PHI
The Security Rule outlines safeguards for electronic PHI (ePHI), including data stored in long-term cloud backups and archives. The following standards are critical when designing a compliant cloud retention strategy:
- Access Controls: Use unique user IDs, role-based permissions, and least-privilege access principles. Multi-factor authentication and strict identity and access management (IAM) ensure only authorized personnel can view or retrieve retained PHI.
- Audit Controls: All access to PHI, configuration changes, and administrative actions must be logged. Cloud systems should generate detailed audit logs and retain them for at least six years, even if operational logs are deleted sooner.
- Encryption and Integrity Controls: Encrypt ePHI during transit (TLS 1.2 or higher) and at rest (AES-256 or equivalent). Use reliable key management with periodic rotation. Employ checksums, versioning, and immutable storage to prevent unauthorized changes to archived data.
- Contingency Planning: A reliable disaster recovery plan is crucial. Maintain encrypted, geo-redundant backups of ePHI for six years, and test these backups regularly to ensure they can be restored when needed.
These safeguards should be documented, included in BAAs with cloud providers, and reviewed annually as part of your risk analysis.
Breach Notification and Privacy Rules
Retention policies also play a role in breach management. The Breach Notification Rule requires organizations to detect, investigate, and document breaches, as well as notify affected individuals, the Department of Health and Human Services (HHS), and - when applicable - the media. To support breach investigations, systems must retain access logs, system logs, and security event data for at least six years.
The Privacy Rule also impacts retention by enforcing the "minimum necessary" standard. This means PHI should only be retained for as long as required to meet legal, regulatory, or business needs. Once retention periods expire, PHI must be securely disposed of. In cloud environments, secure disposal methods include cryptographic erasure (destroying encryption keys), verified deletion from backups, and maintaining detailed destruction procedures. Collaborate with your cloud providers to ensure these methods are clearly outlined in your BAAs.
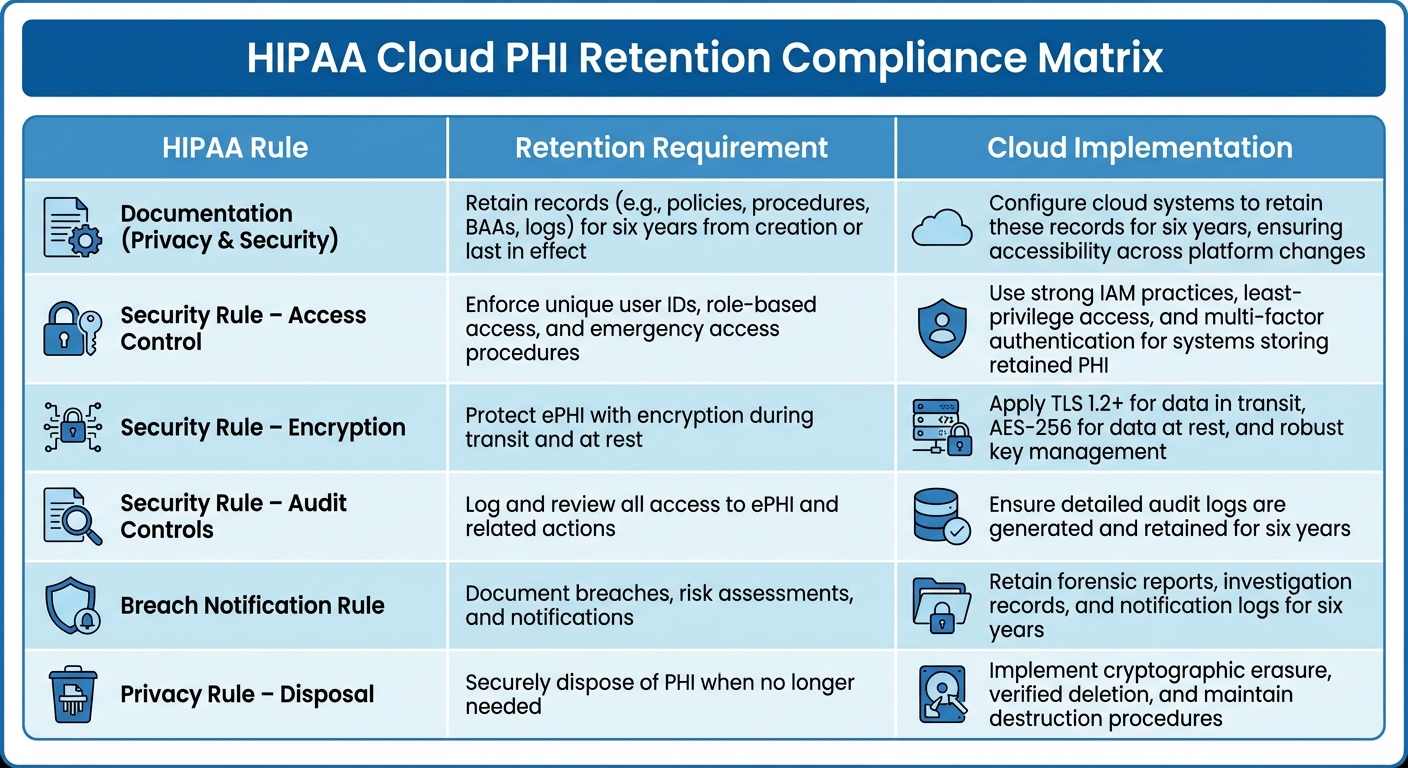
| HIPAA Rule | Retention Requirement | Cloud Implementation |
|---|---|---|
| Documentation (Privacy & Security) | Retain records (e.g., policies, procedures, BAAs, logs) for six years from creation or last in effect | Configure cloud systems to retain these records for six years, ensuring accessibility across platform changes |
| Security Rule – Access Control | Enforce unique user IDs, role-based access, and emergency access procedures | Use strong IAM practices, least-privilege access, and multi-factor authentication for systems storing retained PHI |
| Security Rule – Encryption | Protect ePHI with encryption during transit and at rest | Apply TLS 1.2+ for data in transit, AES-256 for data at rest, and robust key management |
| Security Rule – Audit Controls | Log and review all access to ePHI and related actions | Ensure detailed audit logs are generated and retained for six years |
| Breach Notification Rule | Document breaches, risk assessments, and notifications | Retain forensic reports, investigation records, and notification logs for six years |
| Privacy Rule – Disposal | Securely dispose of PHI when no longer needed | Implement cryptographic erasure, verified deletion, and maintain destruction procedures |
How to Design HIPAA-Compliant Cloud Retention Policies
Creating a retention policy that meets HIPAA requirements involves more than just knowing the rules. It demands a structured plan to translate those legal mandates into secure, practical cloud setups. Start by pinpointing where your PHI (Protected Health Information) is stored, set retention timelines that comply with the law, and ensure secure storage and disposal practices throughout the data's lifecycle.
Building a Cloud PHI Inventory
Begin by cataloging every cloud system that holds PHI. This includes not only clinical tools like electronic health records (EHRs) and practice management software but also SaaS platforms, collaboration tools, email systems, file-sharing services, backup solutions, data warehouses, log archives, ticketing systems, CRM platforms, analytics tools, and even marketing software that handles patient communications.
For each system, document these critical details:
- PHI type: Examples include clinical notes, imaging, claims data, demographics, and behavioral health records.
- Cloud deployment model: Whether it's SaaS, PaaS, or IaaS, and the geographic region where data is stored.
- Ownership status: Identify whether the system is managed by your organization or a business associate.
- BAA status: Confirm any Business Associate Agreements in place and identify subcontractors.
- Retention settings: Include existing backup practices, legal holds, and retention configurations.
Don't forget about metadata and logs - HIPAA's six-year retention rule specifically applies to access logs, audit trails, and configuration records. Use tools like questionnaires or automated discovery software to validate your inventory and uncover any "shadow IT" systems. Platforms like Censinet RiskOps™ can assist in evaluating third-party vendors and cloud services that handle PHI, ensuring nothing is missed.
Once your inventory is complete, you can establish retention timelines tailored to each category of data.
Setting Retention Periods and Triggers
HIPAA mandates a six-year minimum retention period, but the timeline for each PHI category often depends on specific legal triggers. Develop a matrix that maps each record type to its longest applicable retention period when multiple regulations overlap. For example, differentiate between:
- Primary clinical records: EHR data, imaging, and diagnostic results.
- Administrative PHI: Claims, remittances, and authorizations.
- Communications containing PHI: Emails or secure messages.
Ensure communications with PHI are retained for at least six years to meet documentation requirements. Clearly define the start and end points for each retention rule - whether it’s the date of service, discharge, contract termination, last patient interaction, or when a minor reaches adulthood plus the retention period. For policies and procedures, the timeline starts from the date they were last active.
Be sure to document exceptions. Situations like litigation holds, ongoing investigations, or research under IRB or FDA oversight may require overriding standard destruction schedules.
Secure Storage and Disposal Practices
Implement your retention rules directly within the cloud systems you use. Use features like storage lifecycle policies, retention labels, and legal holds to automate the transition of data from active storage to archival tiers once retention periods are met. Consider using write-once-read-many (WORM) or immutable storage to lock records for the required retention period. When data reaches the end of its retention period, configure systems to automatically delete or anonymize PHI, keeping detailed logs of these actions.
Store backups as exact, retrievable copies in secure locations that are geographically separated. Maintain documented restore procedures and test them regularly. When data reaches its expiration or a contract ends, ensure providers either return or destroy the PHI securely. Use certified methods like cryptographic erasure or verified deletion, following guidelines from HHS and NIST.
Make sure your BAAs with cloud providers explicitly outline these retention and disposal requirements to align with your broader risk management strategy. Finally, include retention configuration and testing as part of your organization's HIPAA Security Rule risk analysis to maintain compliance.
Implementing Cloud PHI Retention Compliance
To ensure compliance with retention policies in cloud environments, it's crucial to align people, processes, and technology. The following steps build on your retention policy design to maintain compliance across all cloud systems.
Governance and Policy Development
Strong governance ensures that your retention strategy translates into actionable controls. Establish a governance structure led by an executive sponsor, such as the CIO or CISO, and involve key stakeholders like HIPAA Privacy and Security Officers, compliance teams, legal advisors, HIM, and IT/cloud operations teams.[3][8] Each participant should have clearly defined responsibilities, such as approving retention schedules, monitoring compliance, and addressing issues as they arise.[3][7]
Your governance charter should explicitly cover PHI stored in cloud environments, including SaaS EHRs, backups, archives, and logs. These documents should be reviewed annually to address changes in regulations or technology.[3][7] HIPAA mandates maintaining written policies and procedures for protecting PHI and retaining those documents for at least six years from their creation or last effective date.[1][5][7]
A well-written retention policy should include:
- A defined scope covering all systems and cloud services where PHI is stored
- Retention periods for different PHI categories based on state and federal laws
- Procedures for legal holds and secure destruction (e.g., cryptographic erasure)
- Backup and archive management practices
- Roles authorized to adjust retention settings
- Documentation of deletion events, including certificates and logs[1][3][8]
Additionally, Business Associate Agreements (BAAs) should outline retention and destruction responsibilities clearly.[4][7]
Technical Implementation in Cloud Environments
Once governance is established, configure technical controls to enforce retention policies. Use lifecycle management rules to automatically transition PHI from primary storage to archive tiers after a specified period, and delete it once the retention period ends.[4] Archive tiers, often referred to as cold storage, offer cost-effective long-term storage for PHI, provided encryption at rest and strict access controls are maintained.[3][4]
Ensure encryption is enforced both in transit and at rest for all PHI, including backups and archives.[3][4] Centralize key management using tools like Key Management Services (KMS) or Hardware Security Modules (HSM), and align key-rotation schedules with your policy review cycles. Implement least-privilege access, restrict administrative rights, and enforce Single Sign-On (SSO) with Multi-Factor Authentication (MFA) for PHI storage.[3][4]
Automate deletion or cryptographic erasure of PHI once retention periods expire, and keep verifiable logs or deletion reports.[1][2][4] Your BAAs with cloud vendors should require them to support these capabilities and securely destroy or return PHI at the end of the contract.[1][2][4]
Risk Analysis and Monitoring
To complete your compliance framework, integrate risk analysis and monitoring to strengthen retention measures. The HIPAA Security Rule requires covered entities to conduct thorough risk analyses to identify vulnerabilities affecting the confidentiality, integrity, and availability of ePHI, and implement appropriate risk management strategies.[3][6][8] For cloud PHI retention, focus on:
- Identifying all cloud locations where PHI and related HIPAA documentation are stored
- Assessing risks tied to long-term storage, such as misconfigured access, expanded breach surfaces, vendor lock-in, or incomplete deletion from backups
- Evaluating the effectiveness of encryption, access controls, logging, and destruction processes for retained PHI
- Prioritizing remediation tasks, like adding lifecycle rules or tightening access controls[1][3][4]
Regularly monitor and audit cloud configurations to ensure lifecycle rules, archive settings, and deletion policies comply with your retention schedules.[3][4] Track access to retained PHI using audit logs and security tools, keeping those logs for at least six years.[1][3][5] Periodically test data restores from backups and archives to confirm data integrity and availability, as required by HIPAA.[3][4] Document destruction events, like scheduled deletions or contract terminations, with reports from cloud providers confirming secure erasure or media destruction.[1][2] Conduct internal compliance audits annually, or more frequently for high-risk systems, and retain findings, corrective actions, and sign-offs as part of your HIPAA documentation.[1][3][8]
Tools like Censinet RiskOps™ can streamline this process by standardizing risk assessments, vendor oversight, and PHI retention policies across multiple cloud vendors. These platforms help track BAAs, questionnaire responses, and remediation tasks, while centralized evidence repositories simplify compliance reporting for auditors and regulators.[3][4]
sbb-itb-535baee
Using Cybersecurity Platforms for Retention Compliance
Managing HIPAA-compliant cloud PHI (Protected Health Information) retention across various systems, vendors, and jurisdictions can be a logistical challenge. Healthcare organizations must not only track where PHI is stored but also align retention periods, ensure secure disposal, and maintain six years of documentation for policies, risk assessments, and logs. Cybersecurity and risk management platforms simplify this process, automating evidence collection, standardizing vendor evaluations, and creating audit-ready documentation that aligns with HIPAA requirements. Let’s explore how these platforms integrate into your retention strategy to streamline compliance.
Risk Assessments with Censinet RiskOps™

Censinet RiskOps™ helps healthcare organizations conduct structured risk assessments tailored to HIPAA’s Security Rule and retention requirements. The platform standardizes risk questionnaires, gathering vendor evidence on critical areas like storage, encryption, backups, access controls, secure disposal, and incident response. It scores vendors and internal services based on factors like the volume and sensitivity of PHI they handle, as well as their control maturity. This process highlights potential gaps such as insufficient log retention or unclear backup policies.
Organizations use Censinet RiskOps™ to catalog all cloud services handling PHI - such as EHR systems, data lakes, backup providers, and SaaS applications. It tracks what types of PHI each system holds and links them to retention schedules that meet HIPAA’s six-year documentation requirement, alongside any longer state or CMS rules. The platform’s dashboards identify systems lacking documented retention policies, PHI stored in unapproved locations, and vendors who haven’t confirmed secure disposal controls.
All documentation is maintained in compliance with six-year retention rules. When audits or investigations arise, compliance teams can quickly export reports that detail historical assessments, retention decisions, and monitoring activities for cloud environments storing PHI.
Policy Automation with Censinet AI

Censinet AI simplifies the creation of retention policies by analyzing regulatory requirements, internal policies, and contracts. It proposes standardized retention schedules by PHI type and system, auto-generating or editing policy language, BAAs (Business Associate Agreements), and vendor requirements for encryption, backup retention, and secure disposal. Additionally, it recommends technical enforcement rules - such as object lifecycle settings or purge workflows - that cloud and DevOps teams can implement.
The platform automates workflows to detect new cloud services or vendors, triggering PHI and retention risk assessments. It suggests default retention periods and disposal controls based on PHI classification and jurisdiction, while also tracking expiring contracts to ensure PHI is either returned or securely destroyed per HIPAA and BAA requirements. Censinet AI flags discrepancies, such as log retention or backup policies that deviate from approved schedules, helping avoid both over-retention (which increases breach risks) and under-retention (which risks non-compliance).
While physical deletion takes place within the cloud or application, Censinet ensures governance by documenting system-specific disposal requirements in line with HIPAA and state guidelines. It tracks when PHI is eligible for destruction, ensures vendors adhere to secure deletion methods, and stores critical evidence like destruction certificates and purge logs. These features provide the robust documentation needed to meet HIPAA’s stringent retention and disposal standards.
Collaborative Risk Management for PHI Retention
Effective PHI retention compliance requires seamless collaboration across multiple teams, including privacy, compliance, IT, legal, and HIM. Censinet RiskOps™ fosters this collaboration with shared dashboards, workflows, and centralized documentation repositories. These tools allow all stakeholders to access the same PHI system inventory, risk assessments, and retention decisions, reducing silos and minimizing conflicting interpretations of requirements.
Teams can work together to review vendor responses, assign tasks such as updating S3 lifecycle rules or revising BAAs, and finalize retention and disposal standards. This creates a unified record of HIPAA retention practices. Additionally, the platform acts as a cloud-based risk exchange, enabling healthcare organizations to securely share cybersecurity and risk data with a network of over 50,000 vendors. This collaborative approach helps reduce risk more efficiently than isolated methods.
As state laws evolve or HIPAA guidance changes, compliance teams can update retention rules centrally. Censinet AI can push updated policies to vendors and track metrics like the percentage of PHI systems aligned with current retention standards.
Brian Sterud, CIO at Faith Regional Health, shared: "Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters."
Metrics such as the percentage of cloud systems with documented retention schedules, the proportion of vendors completing HIPAA-aligned risk assessments, and the time required to address critical findings provide valuable insights into compliance efforts.
Conclusion and Key Takeaways
Summary of Best Practices
To ensure compliance with HIPAA and related regulations, it's crucial to maintain a thorough inventory of all cloud systems, vendors, and repositories that handle Protected Health Information (PHI). Establish retention schedules that align with HIPAA's six-year documentation rule and any stricter state or federal requirements. Safeguard PHI during its retention period by implementing technical measures like encryption, access controls, audit logs, and reliable backup systems. When the retention period ends, use secure destruction methods to dispose of PHI properly. Document these practices in formal policies, assign clear roles across compliance, IT, privacy, and records teams, and regularly conduct risk analyses to identify and address potential gaps. This checklist can serve as a guide to evaluate and refine your current retention practices.
Next Steps for Compliance
Start by mapping your current cloud PHI footprint and comparing your retention practices to your policies and legal requirements. Update retention policies based on the type of records and jurisdiction, and configure your cloud platforms with lifecycle rules and access controls to enforce these policies. Clearly define responsibilities for retention, backup, and secure destruction in every Business Associate Agreement (BAA). Ensure these updates align with your governance structure, IT controls, and BAAs for a cohesive compliance strategy. Revise your HIPAA risk analysis to address long-term risks associated with cloud storage, train your team on any policy changes, and schedule regular audits to monitor compliance.
Tools like Censinet RiskOps™ can simplify this process by centralizing risk assessments for cloud vendors handling PHI, automating evidence collection for retention and destruction controls, and offering dashboards to monitor compliance metrics. As Terry Grogan, CISO at Tower Health, shared:
Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required.
Stay proactive by assigning someone to monitor updates in HIPAA, CMS, and state record laws. Subscribe to regulatory updates and review your policies annually. Document all decisions, controls, and audit findings for at least six years to create an audit-ready evidence base. This demonstrates a consistent, risk-based approach to managing cloud PHI retention. With effective governance, robust technical controls, and specialized tools, you can navigate the complexities of cloud environments while maintaining HIPAA compliance.
FAQs
What steps should healthcare organizations take to securely delete PHI stored in the cloud after the retention period?
Healthcare organizations must adopt HIPAA-compliant data destruction practices to securely erase PHI stored in the cloud once the retention period ends. This involves setting up clear data deletion policies, encrypting data to make it unreadable prior to deletion, and performing rigorous checks to confirm the data has been permanently erased.
It's also crucial to keep detailed audit trails that document and validate every step of the deletion process, ensuring adherence to regulatory standards. Using advanced risk management tools can simplify these procedures, helping organizations monitor compliance and minimize the chances of data breaches.
How do HIPAA retention rules for medical records differ from state laws?
Healthcare providers are required by HIPAA to keep medical records and related documents for at least 6 years from the date they were created or last used. However, state laws often extend these timelines - sometimes to 10 years or more - especially for cases involving minors or particular medical conditions.
While HIPAA emphasizes protecting protected health information (PHI) and ensuring patients have timely access to their records, state laws may layer on additional rules. These might include longer retention periods, specific formatting requirements for records, or detailed guidelines for how records should be securely destroyed. For healthcare organizations, staying compliant with both HIPAA and state regulations is not just about avoiding penalties - it's about maintaining proper and responsible record management.
Why are Business Associate Agreements important for securing and managing cloud-based PHI retention?
Business Associate Agreements (BAAs) are a key part of staying HIPAA-compliant, especially when storing Protected Health Information (PHI) in the cloud. These agreements clearly define the roles and responsibilities of covered entities and their business associates in protecting sensitive health data and adhering to HIPAA's strict regulations.
BAAs set clear guidelines for safeguarding PHI, including security protocols, privacy standards, and breach notification processes. They also outline how PHI should be managed, stored, and protected, helping to minimize risks and ensure that cloud-based storage solutions meet the necessary compliance requirements.


