How ISO 27001 Secures Patient Data
Post Summary
ISO 27001 is a globally recognized standard that helps healthcare organizations protect patient data by managing information security risks. It aligns with HIPAA requirements and strengthens safeguards for electronic health information (ePHI). By using ISO 27001, healthcare providers can:
- Identify and manage risks to patient data, including cyber threats like ransomware and phishing.
- Implement controls such as encryption, access restrictions, and secure cloud services.
- Continuously improve security through regular audits and updates to address new threats.
- Manage third-party risks by assessing vendor security practices.
This framework ensures patient data remains secure, supports compliance, and reduces breach risks, making it a key tool for healthcare cybersecurity.
How ISO 27001 Protects Patient Data
ISO 27001 and HIPAA Alignment: Technical, Administrative, and Physical Safeguards for Healthcare
ISO 27001 Scope in Healthcare Settings
When healthcare organizations implement an Information Security Management System (ISMS) under ISO 27001, they must clearly define what falls within its scope. This typically includes systems, data, and processes such as electronic health records (EHRs), patient portals, telehealth platforms, medical devices (like infusion pumps and wearable monitors), billing systems, and clinical research databases. The scope also extends to physical locations where patient data is stored or accessed, including hospitals, clinics, data centers, cloud environments, and even remote workstations used by clinicians during telehealth sessions.
This defined scope ensures that all systems interacting with patient data are appropriately secured. For example, real-time cardiac monitoring devices require robust measures like device authentication, data encryption, and secure cloud storage. ISO 27001's structured approach translates these needs into actionable controls, which are explored next.
Key Clauses and Annex A Controls
ISO 27001:2022 consists of ten main clauses and an Annex A, which outlines 93 security controls grouped into four categories: organizational, people, physical, and technological. This framework guides healthcare organizations through assessing their environment, demonstrating leadership commitment, planning risk treatments, managing the ISMS, monitoring performance, and driving continuous improvement.
Annex A is where high-level requirements turn into specific actions. For instance:
- A.5.15 (Access Control) ensures that only authorized personnel, such as clinicians and staff, can access or modify protected health information (PHI) within EHR systems.
- A.8.24 (Use of Cryptography) mandates encryption of patient data during storage and transmission.
- A.5.23 (Information Security for Use of Cloud Services) addresses the security of cloud-hosted clinical applications, which is increasingly critical as telehealth and analytics platforms grow.
- A.8.10 (Information Deletion) requires the secure disposal of PHI when devices are decommissioned or records are no longer needed, reducing the risk of data leaks from discarded media.
These controls align seamlessly with HIPAA requirements, supporting a secure and compliant healthcare environment.
How ISO 27001 Supports HIPAA Requirements
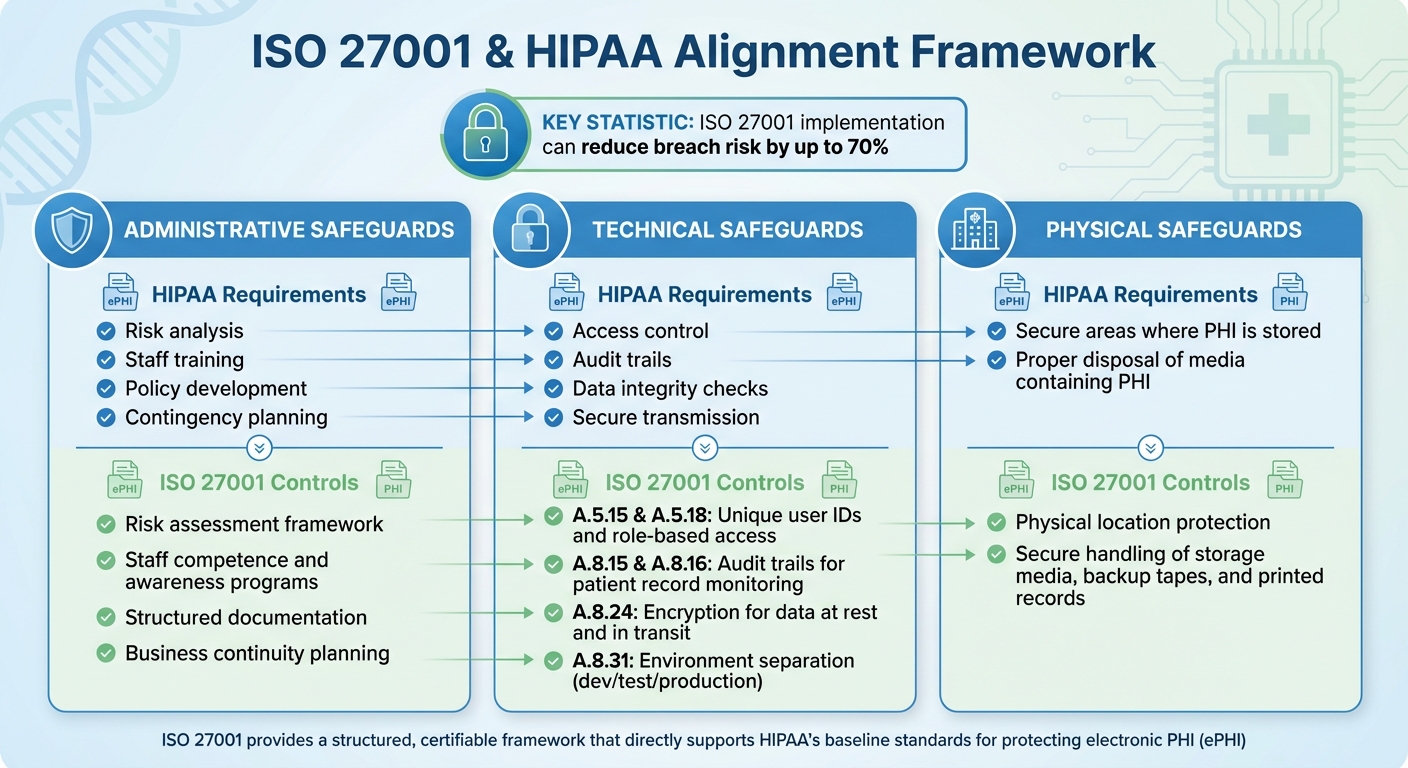
ISO 27001's risk management and control framework directly supports HIPAA's safeguards for electronic PHI (ePHI). While HIPAA establishes the baseline standards for protecting ePHI, ISO 27001 provides a structured and certifiable way to implement these safeguards.
Administrative safeguards under HIPAA include risk analysis, staff training, policy development, and contingency planning. ISO 27001 complements these with its focus on risk assessment, staff competence and awareness, and structured documentation, ensuring policies are enforced and training is consistent.
For technical safeguards, HIPAA requires measures like access control, audit trails, data integrity checks, and secure transmission. ISO 27001's Annex A provides corresponding controls:
- A.5.15 and A.5.18 enforce unique user IDs and role-based access to ePHI.
- A.8.15 and A.8.16 establish audit trails to monitor access to patient records.
- A.8.24 ensures encryption for data at rest and in transit.
- A.8.31 separates development, test, and production environments to prevent unauthorized changes to clinical systems.
On the physical safeguards side, HIPAA emphasizes securing areas where PHI is stored and proper disposal of media containing PHI. ISO 27001 addresses these through controls that protect physical locations and ensure secure handling of storage media, backup tapes, and printed records, minimizing the risk of data breaches.
Healthcare Cybersecurity Risks Addressed by ISO 27001
Common Cybersecurity Threats in Healthcare
Healthcare organizations in the U.S. face a wide array of cyber threats that jeopardize both patient data and operational continuity. Ransomware attacks are a major concern, often targeting hospitals where any disruption can directly impact patient care [5]. Insider threats add another layer of vulnerability - whether it's unauthorized access to sensitive records or mishandling data through emails, lost devices, or misconfigured cloud storage [1][2]. Phishing campaigns frequently aim at clinical staff, seeking to steal credentials for electronic health record (EHR) systems. Meanwhile, outdated software and weak network segmentation leave legacy medical devices and other networked equipment exposed [5].
Third-party vendors, such as billing services, telehealth platforms, and cloud EHR providers, also process protected health information (PHI). Weak security measures or insufficient contractual safeguards on their part can widen the breach surface [4][1]. Business email compromise schemes, where attackers impersonate executives or clinicians, further compound these challenges [2]. This diverse threat landscape highlights the need for a strong framework like ISO 27001, which supports organizations through layered security measures.
"Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare." - Matt Christensen, Sr. Director GRC, Intermountain Health [8]
ISO 27001 Controls That Reduce These Risks
To tackle these challenges, ISO 27001 offers a comprehensive set of controls designed to manage and mitigate cybersecurity risks. This internationally recognized standard provides a structured framework for identifying, prioritizing, and addressing threats. When fully implemented, ISO 27001:2022 can lower breach risks by up to 70% [6].
The standard emphasizes building multi-layered defenses, such as implementing robust anti-malware tools, secure data backup protocols, and effective incident response plans to counter ransomware and other malware threats. It also enforces strict access control measures, ensuring that only authorized personnel can access patient data. Encryption, secure system configurations, and detailed business continuity planning are further key components, reducing the impact of potential cyber incidents and protecting critical healthcare operations.
Managing Third-Party and Supply Chain Risks
With the extensive use of external vendors, managing third-party risks is a critical focus area for healthcare organizations. Vendors like cloud providers, billing services, and telehealth platforms often handle sensitive PHI, making their security practices a direct concern. ISO 27001 addresses these risks by requiring organizations to evaluate and monitor the security controls of their suppliers continuously. This includes setting clear security expectations in contracts, conducting regular vendor risk assessments, and managing changes in service delivery.
For vendors involved in creating or maintaining clinical applications, secure coding practices and proper data handling are essential. Tools like Censinet RiskOps™ simplify third-party risk evaluations and support compliance efforts, further strengthening an organization’s overall security framework.
Implementing ISO 27001 in U.S. Healthcare Organizations
Steps to Build an ISMS
Start by securing executive sponsorship and establishing a clear governance structure. Appoint a Chief Information Security Officer (CISO) or an ISMS owner, and assemble a steering committee that includes key stakeholders like the CIO, Chief Compliance Officer, privacy officer, clinical leadership, IT, HR, legal, and vendor management. This team will oversee critical tasks such as managing the risk register, approving security policies, and supervising audits and reviews.
Define the scope of your ISMS carefully. Decide whether it will cover specific facilities, business units, or the entire organization. Regardless of the scope, ensure that essential patient-care services - like electronic health record systems, clinical applications, and connected medical devices - are included. Conduct a thorough risk assessment to identify threats to patient data and vulnerabilities unique to healthcare. Use these findings to select appropriate controls from ISO 27001's Annex A, helping you prioritize resource allocation.
Document governance processes using RACI matrices (Responsible, Accountable, Consulted, Informed). These tools clarify roles and responsibilities, streamline operations, and align with auditor expectations, ensuring everyone involved understands their part in safeguarding patient data.
Once the ISMS framework is established, align it with existing HIPAA policies to strengthen security controls.
Integrating ISO 27001 with Existing Healthcare Policies
Healthcare organizations in the U.S. already adhering to HIPAA can use their current policies and controls as a foundation for ISO 27001 compliance. Both frameworks share a focus on protecting the confidentiality, integrity, and availability of electronic protected health information (ePHI). By aligning HIPAA Security Rule safeguards with ISO 27001 requirements and Annex A controls, organizations can simplify the adoption process.
For example, HIPAA risk analyses, access control policies, workforce training programs, and enforcement procedures can be adapted to meet ISO 27001's requirements for risk assessment, risk treatment, and information security policy development. Similarly, incident response and breach notification procedures required under HIPAA align closely with ISO 27001's controls for event logging, incident management, and communication. This alignment ensures consistency in detection, escalation, and regulatory reporting processes.
Disaster recovery and business continuity plans should also be updated to meet ISO 27001 standards, particularly for critical clinical systems where downtime could directly impact patient care. Maintaining a crosswalk document that maps HIPAA requirements to ISO 27001 controls can help demonstrate compliance to auditors, regulators, and leadership. This approach not only simplifies audits but also reinforces patient data protection by integrating both standards into a single, cohesive program.
Using integrated tools can further streamline the alignment process.
Using Censinet RiskOps™ to Streamline Implementation

Censinet RiskOps™ is specifically designed for healthcare cybersecurity and risk management, offering workflows and tools tailored to protect PHI, clinical applications, medical devices, and manage supply chain risks. The platform centralizes and automates enterprise and third-party risk assessments using standardized questionnaires aligned with ISO 27001 and HIPAA. This reduces manual effort and accelerates vendor onboarding and reassessment processes.
Censinet allows organizations to aggregate risk data, score vendors, and track remediation efforts. This makes it easier to document risk assessments, treatment plans, and supplier monitoring activities. Since the platform is focused exclusively on healthcare, it incorporates clinical impact and patient safety considerations into risk management. For instance, it can identify vendors whose failures might disrupt critical care workflows or expose large amounts of ePHI. By aligning ISO 27001 controls with real-world healthcare operations, Censinet helps organizations meet regulatory requirements with less friction.
"Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required." - Terry Grogan, CISO, Tower Health [8]
The platform also supports secure collaboration with third-party vendors by enabling organizations to share cybersecurity and risk data more efficiently. Additionally, Censinet's benchmarking features allow healthcare organizations to measure and improve their cybersecurity maturity against industry standards. This supports the continuous improvement cycle required by ISO 27001 and strengthens patient data protection across the healthcare ecosystem.
sbb-itb-535baee
Measuring ISO 27001 Control Effectiveness
Key Performance Metrics for ISO 27001
Healthcare organizations implementing ISO 27001 must monitor, measure, analyze, and evaluate their Information Security Management System (ISMS) and its controls, as outlined in Clause 9.1–9.3 [1][7]. To do this effectively, organizations need a detailed measurement plan that specifies what to measure, where the data will come from (e.g., SIEM logs, GRC tools), when measurements will occur, who will oversee them, and how results will be evaluated [1][7].
Metrics should focus on safeguarding patient data. For incident management, key indicators include the number of security incidents per quarter and per 1,000 employees, along with metrics like Mean Time to Detect (MTTD) and Mean Time to Respond/Recover (MTTR). Access control metrics track unauthorized access attempts, misuse of privileges, or inappropriate access to PHI (Protected Health Information), along with the time it takes to revoke access after staff departures. In vulnerability management, organizations should measure the percentage of critical vulnerabilities resolved within agreed timelines, such as 7 or 30 days. Training and awareness metrics include the percentage of employees completing security training on time and passing phishing simulations. Audit results focus on the number and severity of nonconformities identified during internal and external audits. Lastly, third-party risk metrics monitor the percentage of vendors with completed risk assessments and risk treatment plans.
| Measurement Area | Example Metric (KPI/KRI) | ISO 27001 / Healthcare Relevance |
|---|---|---|
| Incident Management | Average incident response time and recovery time (MTTR) | Highlights the effectiveness of Annex A incident management controls; essential for protecting PHI [6][1]. |
| Access Control / PHI Privacy | Number of unauthorized PHI access events per month; time to revoke access after termination | Reflects compliance with HIPAA and ISO 27001 access control standards [1][2][5]. |
| Audit & Compliance | Number and severity of nonconformities in audits | Indicates ISMS maturity and control effectiveness [1][7]. |
| Overall Security Outcomes | Number of reportable breaches per year; estimated breach-related costs avoided | Measures the overall impact of ISO 27001 on healthcare security [6][2][3]. |
Tools like Censinet RiskOps™ can simplify this process by centralizing risk data, automating third-party assessments, and maintaining evidence libraries mapped to ISO 27001 controls and HIPAA safeguards. These platforms also support benchmarking against industry standards, helping organizations continuously improve [6][8].
"Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters." - Brian Sterud, CIO, Faith Regional Health [8]
These metrics provide actionable insights for management reviews, ensuring that security measures adapt to emerging threats.
Management Review and Continuous Improvement
ISO 27001 requires organizations to regularly review and adjust their controls to address new threats, technologies, and regulatory changes like HIPAA [1][2][7]. While annual reviews are mandatory, many healthcare organizations conduct quarterly reviews to keep pace with the rapidly changing environment. These reviews, aligned with the PDCA (Plan-Do-Check-Act) cycle, should examine ISMS performance metrics, incident trends, audit findings, shifts in technology (e.g., telehealth platforms), and resource needs [1][2][7].
To avoid fragmented reporting, integrate ISO 27001 monitoring with other governance structures, such as HIPAA security committees and enterprise risk management programs. This ensures board-level visibility into patient data risks and promotes a unified approach. Metrics are often reported monthly or quarterly, tied to fiscal quarters, and translated into business terms - such as breach costs avoided or reduced overtime from fewer incidents - to resonate with executives and board members [6][2][3]. Regular reviews keep patient data protected as new challenges arise.
AI-powered platforms tailored for healthcare can further streamline risk management and reduce vulnerabilities. Collaborative risk networks allow organizations to share cybersecurity insights, fostering a collective approach to addressing threats and adopting best practices [8].
Impact of ISO 27001 on Healthcare Security
The benefits of ISO 27001 implementation are tangible for healthcare organizations. Studies show it can reduce breach risk by up to 70% [6]. Before adopting ISO 27001, many healthcare providers rely on spreadsheets for risk management, which limits visibility into critical areas like third-party risks. With ISO 27001, organizations gain structured governance, improved incident response capabilities, centralized risk registers, and more efficient vendor assessments.
"Not only did we get rid of spreadsheets, but we have that larger community [of hospitals] to partner and work with." - James Case, VP & CISO, Baptist Health [8]
ISO 27001 strengthens governance and accountability by clearly defining roles for protecting PHI and ePHI. It enhances risk visibility through systematic assessments and continuous monitoring. Incident response becomes faster and more effective, thanks to well-defined procedures and communication protocols. The framework also helps organizations allocate resources more strategically, with metrics and benchmarking data providing a solid foundation to justify security investments. In an industry where breach costs are among the highest, ISO 27001 offers a structured approach to minimizing financial and reputational harm [6][2][3]. By reinforcing governance, improving response times, and optimizing resources, ISO 27001 plays a critical role in safeguarding patient data.
Conclusion and Key Takeaways
ISO 27001 provides a structured, risk-based framework designed to safeguard patient data effectively. By implementing a formal Information Security Management System (ISMS), healthcare providers weave security practices into their daily operations, ensuring the confidentiality, integrity, and availability of electronic Protected Health Information (ePHI) and other sensitive records. Its ongoing improvement process allows organizations to adjust to new threats, emerging telehealth technologies, and changes in clinical workflows.
While complementing HIPAA's requirements, ISO 27001 strengthens administrative, physical, and technical safeguards. This framework addresses regulatory, operational, and vendor-related challenges, offering a practical, risk-based approach to data protection. Achieving ISO 27001 certification signals a commitment to protecting patient information, enhancing third-party risk assessments and business associate agreements. Organizations that adopt ISO 27001 often see fewer security incidents, reduced breach-related costs, and stronger operational stability.
ISO 27001 also emphasizes the importance of managing third-party and supply chain risks. Tools like Censinet RiskOps™ simplify this process by streamlining risk assessments, cybersecurity benchmarking, and collaborative management across PHI, clinical systems, medical devices, and supply chains. For healthcare providers, these platforms are instrumental in operationalizing ISO 27001 requirements.
Beyond its technical benefits, ISO 27001 brings together IT, security, compliance, and clinical teams in a unified effort to protect patient data. It establishes clear guidelines for creating policies, conducting risk assessments, managing access controls, and implementing audit logging and incident response measures. This integrated approach ensures due diligence while enabling strategic resource allocation. Its flexibility makes it well-suited to meet U.S. regulatory needs, payment models, and care delivery systems.
To begin, healthcare organizations should conduct a baseline risk and gap analysis, assign a cross-functional sponsor, and start with pilot projects in high-risk areas before scaling across the enterprise. By embedding ISO 27001 into their security strategies, healthcare providers create a strong foundation for safeguarding patient data and ensuring resilience in the face of evolving challenges.
FAQs
How does ISO 27001 help healthcare organizations comply with HIPAA regulations?
ISO 27001 plays a critical role in supporting HIPAA compliance by offering a well-defined framework to manage information security risks. This framework ensures that patient data is protected and handled securely. At its core, ISO 27001 establishes an information security management system (ISMS) that aligns seamlessly with HIPAA's Privacy and Security Rules, covering essential aspects like access controls, risk assessments, and data protection strategies.
When healthcare organizations implement ISO 27001, they can take a proactive stance against cybersecurity risks, minimize vulnerabilities, and show regulators that they meet compliance standards. Beyond safeguarding protected health information (PHI), this approach also helps organizations stay prepared for audits and strengthens trust with both patients and stakeholders.
How does ISO 27001 protect healthcare organizations from cybersecurity threats?
ISO 27001 plays a key role in helping healthcare organizations protect patient data from major cybersecurity threats like data breaches, unauthorized access, malware, phishing, ransomware, and insider threats.
By providing a clear framework for managing information security, ISO 27001 helps healthcare providers spot vulnerabilities, reduce risks, and stay aligned with privacy regulations. This is especially critical for safeguarding sensitive patient details, such as Protected Health Information (PHI), and maintaining trust in healthcare systems.
What are the first steps healthcare organizations should take to implement ISO 27001?
To get started with ISO 27001, healthcare organizations should begin with a thorough risk assessment. This process helps pinpoint vulnerabilities and potential threats to patient data. From there, it's crucial to establish a solid management framework and develop policies that align with ISO 27001 standards.
Leveraging tools designed for the healthcare sector, such as Censinet RiskOps™, can make a big difference. These tools simplify risk assessments, automate compliance tasks, and enhance overall cybersecurity preparedness. Additionally, involving leadership early on, training staff on security best practices, and maintaining ongoing monitoring and updates to security protocols are key steps to ensuring lasting success.


