Insurance and Benefits Administration Vendor Risk for Healthcare Organizations
Post Summary
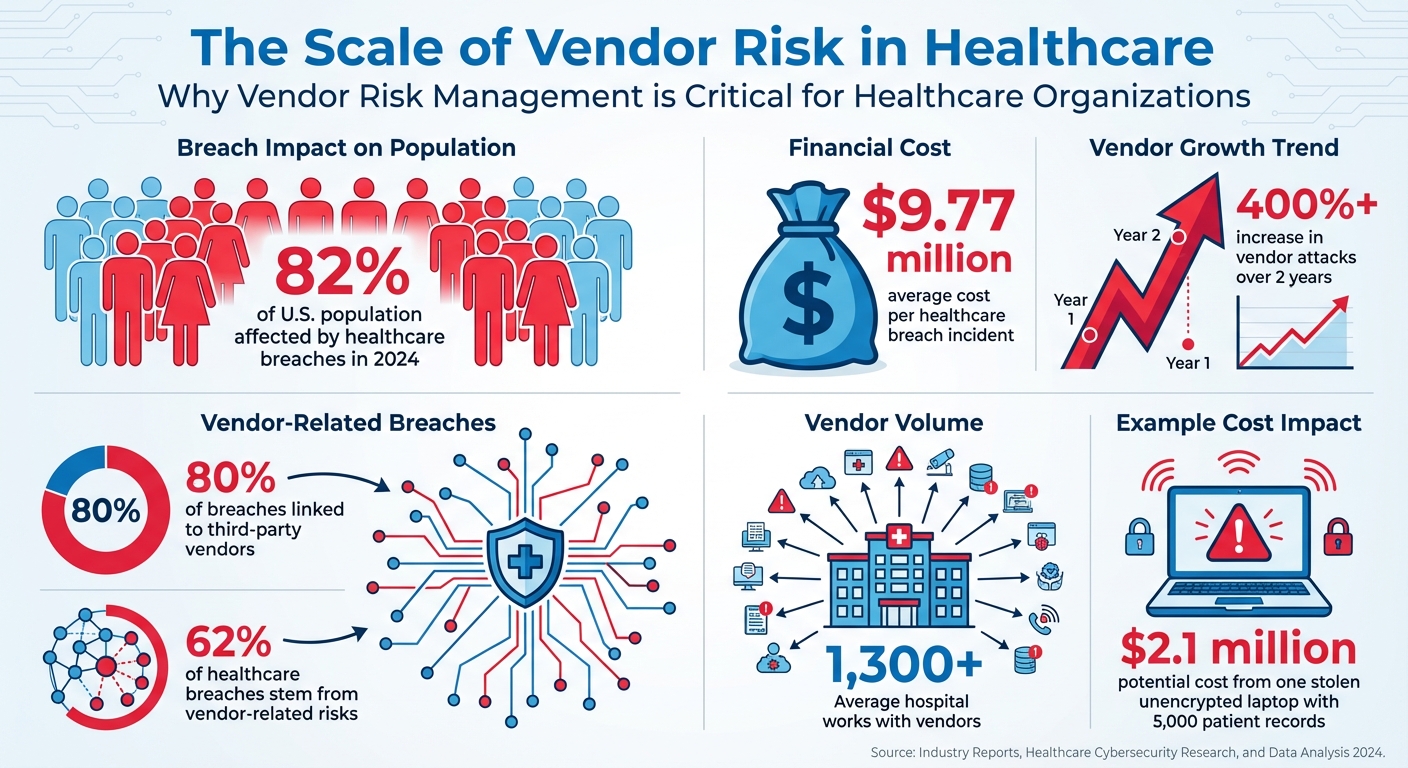
Healthcare organizations depend on vendors for critical operations like claims processing, billing, and electronic prescribing. However, these partnerships expose sensitive patient data - like PHI, Social Security numbers, and medical records - to significant cybersecurity risks. In 2024 alone, healthcare breaches affected 82% of the U.S. population, costing $9.77 million per incident on average. With 80% of breaches linked to third-party vendors, managing vendor risk is no longer optional.
Key Takeaways:
- Third-party vulnerabilities: 62% of healthcare breaches stem from vendor-related risks.
- Compliance challenges: Vendors must meet HIPAA and HITECH requirements to avoid penalties and data breaches.
- High-profile breaches: Incidents like the Change Healthcare attack in 2024 highlight the scale of vendor-related threats.
- Risk management essentials: Regular assessments, strong legal agreements (BAAs), and continuous monitoring are critical for protecting patient data.
To address these risks, healthcare organizations must implement structured vendor risk management programs, leveraging tools like Censinet RiskOps™ for automation, real-time monitoring, and centralized oversight. Without these measures, patient data and healthcare operations remain exposed to growing threats.
Healthcare Vendor Risk Statistics: Third-Party Breach Impact and Costs
Cybersecurity and Compliance Risks from Vendor Relationships
Vendors play a critical role in healthcare operations, but they can also introduce serious vulnerabilities if not properly managed. In fact, a staggering 80% of healthcare breaches stem from business associates[1]. This makes vendor relationships a key risk area for the industry. Even the most secure internal systems cannot fully shield an organization from weaknesses in third-party systems. Let’s dive into some of the common technical and regulatory challenges these partnerships can bring.
Common Security Weaknesses in Vendor Systems
Vendors involved in insurance and benefits administration often have technical flaws that attackers can exploit. One major issue is misconfigured cloud storage, which can leave sensitive patient data exposed. Another common problem is poor access controls, where users are given excessive permissions, unnecessarily increasing the risk of data breaches.
Unsecured network connections between healthcare organizations and their vendors can also act as a weak link, allowing data to be intercepted. Meanwhile, systems that lack timely updates or patches remain vulnerable to known exploits. Encryption issues - whether it’s poorly configured encryption or none at all - further amplify the risk, leaving data in transit or at rest susceptible to theft.
Navigating HIPAA, HITECH, and Other Compliance Standards
Beyond technical flaws, compliance failures with regulations like HIPAA and HITECH can have serious consequences. Vendor risk management isn’t just a best practice - it’s a legal requirement. Under HIPAA, both healthcare organizations and their business associates must implement specific safeguards. When a vendor experiences a breach or neglects these requirements, the healthcare organization could face penalties, mandatory breach notifications, and damage to its reputation.
To avoid these pitfalls, healthcare organizations need to ensure that vendors meet the administrative, physical, and technical safeguards outlined in the HIPAA Security Rule. This means verifying that vendors perform regular risk assessments, maintain detailed audit logs, train their staff on security protocols, and have solid incident response plans in place. Without these checks, compliance gaps can go unnoticed, leading to costly violations.
The combination of technical vulnerabilities and compliance risks highlights why a thorough vendor risk assessment process is essential. The following sections will explore how to structure an effective approach to managing these challenges.
How to Assess Vendor Risk
Evaluating vendor risk isn’t a one-and-done task - it’s an ongoing process that starts well before signing the contract and continues throughout the partnership. With 62% of healthcare breaches tied to third-party vulnerabilities[5], getting this right is non-negotiable. The aim? Spot security weaknesses early and ensure your vendors not only meet your technical standards but also comply with regulatory requirements.
Vendor Risk Assessment Checklist
Start by mapping out every point where the vendor interacts with PHI - whether it’s through EHR systems, medical devices, or older platforms. This helps you identify potential weak spots[5].
Your checklist should address several critical areas, including:
- Conducting regular risk assessments
- Keeping detailed audit logs
- Encrypting data both in transit and at rest
- Enforcing strict access controls
- Applying patches consistently
- Planning for incidents and providing security training
When assessing vendors, ask open-ended questions to dig deeper into potential risks. Avoid simple yes-or-no answers - they can mask underlying issues. For instance, a stolen, unencrypted laptop with just 5,000 patient records could cost you $2.1 million[5]. That’s a hefty price for missing a red flag.
Once you’ve identified technical risks, it’s time to solidify your expectations through legal agreements.
Using Business Associate Agreements to Define Responsibilities
Technical evaluations are just one piece of the puzzle - legal agreements ensure vendors are held accountable. Business Associate Agreements (BAAs) form the backbone of this accountability. These contracts must clearly outline the services the vendor will provide and their HIPAA compliance responsibilities[4]. Remember, it’s your organization’s job to ensure vendors stick to these terms[4], and vague wording won’t cut it.
Your BAA should include:
- Explicit cybersecurity requirements
- Clear consequences for non-compliance, using "if-then" statements to leave no room for misinterpretation[3]
- Specific instructions for securely destroying or returning PHI when the contract ends or during offboarding, to eliminate data retention risks[4]
Reviewing and updating your BAAs regularly is equally important[4]. As regulations evolve and new threats emerge, your agreements need to stay current. This ongoing effort ensures your legal protections remain strong throughout the vendor relationship.
Managing Vendor Risk with Censinet RiskOps™

Trying to manage vendor risk manually - especially with outdated processes - can eat up a lot of time. For context, the average hospital works with more than 1,300 vendors[3]. Keeping track of every insurance and benefits partner without the right tools is nearly impossible. That’s where Censinet RiskOps™ steps in, offering a smarter way to handle vendor risk through automation and centralized management.
By building on solid vendor risk assessments, Censinet RiskOps™ shifts your process from manual oversight to a streamlined, automated system.
Speeding Up Vendor Assessments with Censinet Connect™
Censinet Connect™ takes the hassle out of vendor evaluations by automating compliance workflows and simplifying the entire process. Instead of waiting weeks for vendors to finish long questionnaires, the platform offers guided assessments that quickly pinpoint gaps and generate actionable remediation plans. This means you can onboard insurance and benefits vendors faster while still upholding strict security standards - no compromises needed.
But speeding up assessments is just part of the equation. Keeping an eye on vendors in real time is equally important.
Real-Time Monitoring with Censinet AITM
Censinet AITM makes vendor assessments faster than ever. This AI-powered tool allows vendors to complete security questionnaires almost instantly by summarizing evidence and capturing key details about product integrations and potential fourth-party risks. It even generates risk summary reports based on all collected data. With this level of automation, your team can address risks efficiently while staying informed about critical decisions.
Centralized Risk Tracking with Censinet Command Center
The Censinet Command Center provides a comprehensive, single-screen view of your entire vendor risk landscape. From assessment statuses and training progress to open incidents, everything is consolidated in one place. This centralized system makes it easy to share updates on regulatory changes, vendor issues, and emerging threats across your organization. It’s a crucial tool for coordinating responses to risks that could impact sensitive PHI across departments.
sbb-itb-535baee
Building a Long-Term Vendor Risk Management Program
Managing vendor risk is not a one-and-done task - it’s an ongoing process that evolves alongside your organization and the ever-changing threat landscape. With vendor attacks skyrocketing by over 400% in just two years [4], healthcare organizations need a structured, adaptable approach to stay ahead of these risks.
Setting Up Continuous Risk Monitoring
To effectively address emerging threats, continuous monitoring is a must.
What sets effective programs apart is their commitment to real-time monitoring. Once a high-risk vendor is onboarded, they should agree to continuous scanning and network monitoring. This includes flagging unusual activity, such as suspicious logins or unexpected traffic patterns, that could signal a potential breach. Take Adobe as an example: the company requires medium- and high-risk vendors to undergo continuous scanning and annual security reviews in addition to initial assessments and certifications like SOC 2 Type II and ISO 27001 [4].
It’s also important to rely on compliance reports that reflect ongoing performance. Certifications like HITRUST, SOC 2 Type II, and ISO 27001 provide insights into whether a vendor is maintaining its security standards over time - not just at the point of their initial evaluation.
Coordinating Vendor Risk Management Across Departments
Continuous monitoring works best when paired with strong collaboration across departments.
Vendor risk management isn’t just an IT issue - it’s a shared responsibility that involves compliance, legal, procurement, and clinical teams. Cross-department coordination ensures that everyone understands their role in keeping patient data safe and responding to potential incidents. Regular training sessions can help align teams on policies, emerging threats, and response strategies.
A centralized system can streamline this process by giving all stakeholders a shared view of vendor statuses, open incidents, and assessment progress. When an issue arises, the relevant teams can act quickly and efficiently - without wasting time sifting through scattered spreadsheets or email chains.
Conclusion
Insurance and benefits administration vendors are essential to healthcare operations, but they also represent a significant cybersecurity risk. With third-party vendors accounting for 80% of healthcare breaches and incidents like the Change Healthcare breach impacting 192.7 million Americans [7], the scale of the problem is hard to ignore. These numbers highlight the pressing need for effective vendor risk management strategies.
As Mike Levin, General Counsel and Chief Information Security Officer at Solera Health, states: "Ultimately, protecting patient data isn't something that happens by accident. It's the result of deliberate decisions to build resilience across your people, processes, and technology." [2]
Levin’s point emphasizes the importance of proactive and continuous risk management. Establishing thorough assessment frameworks and monitoring systems is critical to identifying vulnerabilities before they become active threats [7]. The reality is that your cybersecurity is only as strong as its weakest link, which is often a third-party vendor [6]. Relying solely on periodic assessments or contractual assurances is no longer sufficient in a landscape where modern threat actors exploit weaknesses in healthcare supply chains [7]. To address this, adopting specialized risk management platforms is no longer optional - it’s essential.
Censinet RiskOps™ offers healthcare organizations the ability to stay ahead of these challenges. With tools like Censinet Connect™ for quicker assessments, Censinet AITM for automated risk analysis, and a centralized Command Center for comprehensive oversight, organizations can confidently manage vendor risks. These tools not only safeguard patient data but also ensure compliance, maintain trust, and prioritize patient safety.
FAQs
What steps can healthcare organizations take to manage vendor risks and protect patient data?
Healthcare organizations can tackle vendor risks effectively by employing a proactive and well-organized strategy. Begin by categorizing vendors according to the level of risk they pose to your organization and the security of patient data. Conduct detailed risk assessments to pinpoint potential weaknesses and confirm that vendors align with your cybersecurity and compliance expectations.
To protect sensitive information, enforce strict contract terms that address data protection and privacy. Maintain ongoing oversight by regularly monitoring vendor performance, conducting audits, and setting up clear protocols for incident response and vendor termination. These steps are essential for keeping patient data secure and consistently meeting regulatory obligations.
What are the essential elements of an effective vendor risk management program for healthcare organizations?
An effective vendor risk management program in healthcare is all about protecting sensitive patient information while staying aligned with regulatory requirements. To achieve this, organizations should focus on a few key practices: conducting detailed risk assessments, keeping tabs on vendor compliance with industry standards, and regularly evaluating vendor performance.
On top of that, having a well-defined incident response plan and using continuous monitoring tools can make a big difference. These tools help identify and address vulnerabilities quickly, ensuring data security stays intact. By following these steps, healthcare organizations can not only safeguard patient data but also build trustworthy, reliable relationships with their vendors.
Why is continuous monitoring important for managing vendor risks in healthcare organizations?
Continuous monitoring plays a crucial role in spotting new vulnerabilities, identifying active threats, and maintaining compliance over time. In the healthcare sector, where data sensitivity is paramount, this process provides real-time insights into vendor performance and potential risks, helping to minimize the chances of data breaches and security incidents.
By tackling issues as they emerge, healthcare organizations can protect patient data more effectively, stay compliant with regulations, and establish more secure and reliable partnerships with their vendors.


