5 Key Premarket Cybersecurity Requirements for Devices
Post Summary
Requirements include a cybersecurity management plan, risk assessments, Software Bill of Materials (SBOM), and postmarket vulnerability monitoring.
The FDA provides guidance to ensure medical devices are secure, resilient, and maintainable throughout their lifecycle.
An SBOM is a detailed inventory of software components in a device, helping identify vulnerabilities and ensure timely updates.
Non-compliance can result in delayed approvals, increased cybersecurity risks, and potential harm to patients.
By submitting a comprehensive cybersecurity management plan, conducting threat modeling, and providing evidence of risk mitigation.
Tools like C2A Security’s EVSec platform automate SBOM management, vulnerability tracking, and compliance documentation.
Medical device cybersecurity is now a legal requirement. The FDA mandates that connected devices meet strict cybersecurity standards before approval. Here's what manufacturers need to know:
- Secure Product Development Framework (SPDF): Integrate cybersecurity at every stage of device design, from risk analysis to testing.
- Security Architecture & Technical Controls: Build strong safeguards like encryption, authentication, and secure updates into device design.
- Software Bill of Materials (SBOM): Provide a detailed, machine-readable inventory of all software components, including third-party and open-source elements.
- Premarket Documentation: Submit comprehensive cybersecurity plans, threat models, and risk assessments to the FDA.
- Postmarket Vulnerability Management: Set up systems to monitor, identify, and address cybersecurity risks after the device is launched.
These steps ensure that devices remain safe, functional, and secure throughout their lifecycle. Failure to comply can lead to denied approvals and legal consequences.
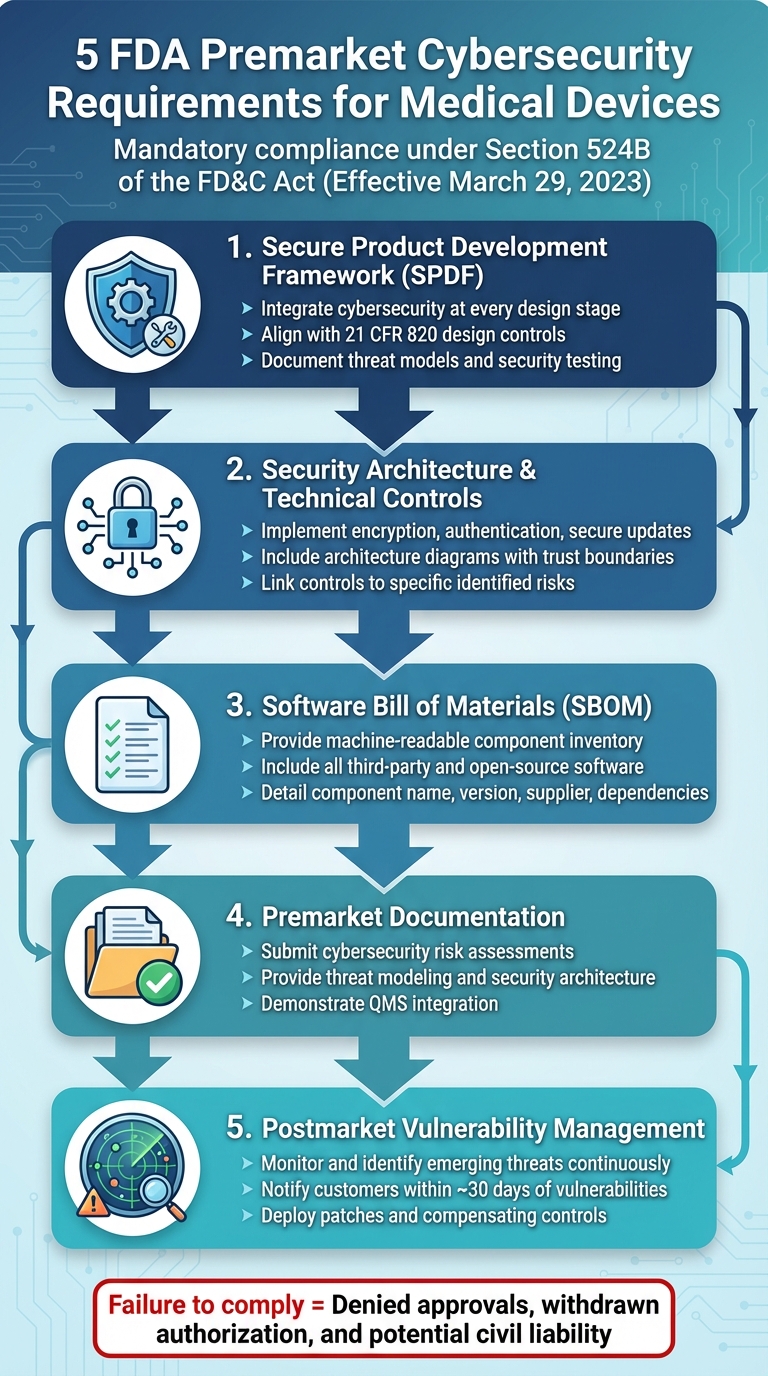
FDA's 5 Premarket Cybersecurity Requirements for Medical Devices
1. Secure Product Development Framework (SPDF)
FDA Compliance and Expectations
On June 27, 2025, the FDA issued guidance defining the Secure Product Development Framework (SPDF) as a structured process that weaves cybersecurity into every stage of medical device development [3]. The agency now mandates that manufacturers provide "reasonable assurance of cybersecurity" as part of ensuring device safety [1].
To meet these requirements, manufacturers must align their SPDF with 21 CFR 820 design controls and risk management [3]. In practice, this means treating cybersecurity as a core design input, incorporating security testing into verification and validation processes, and documenting both threat models and test reports in a traceable manner. The FDA expects manufacturers to provide objective evidence, which includes:
- A comprehensive risk analysis identifying potential threats and mitigation strategies.
- Design documentation detailing security architecture, such as access controls, encryption, logging, and update mechanisms.
- Security testing results that demonstrate critical vulnerabilities have been addressed.
- A Software Bill of Materials (SBOM) listing all third-party components.
These structured steps aim to improve both patient safety and device reliability.
Impact on Patient Safety and Device Effectiveness
A well-implemented SPDF plays a crucial role in protecting patients by minimizing the risk of cyber incidents that could disrupt essential clinical functions [9]. During the design phase, threat modeling can identify potential risks, such as unauthorized dose adjustments in infusion pumps, delayed alarms in monitoring systems, or data integrity attacks affecting diagnostic results. By integrating controls like strong authentication, integrity checks, least-privilege access, and secure communication protocols, manufacturers can help ensure that devices remain safe and operational, even under cyberattack conditions [9].
Integration with Quality Management Systems
Cybersecurity isn’t just a design-phase concern - it must be embedded throughout the device lifecycle via the Quality Management System (QMS). This involves integrating security into design inputs, verification processes, and change controls [3][12]. For example, document and change control systems should explicitly assess the cybersecurity impact of updates, architecture changes, new connectivity features, or modifications to cryptographic measures. Internal audits should track key cybersecurity metrics, such as patch deployment times and vulnerability resolution rates. Standards like IEC 81001-5-1 provide detailed guidance on incorporating cybersecurity into existing QMS frameworks [5].
Lifecycle Management of Cybersecurity Risks
The FDA emphasizes that cybersecurity is an ongoing responsibility, not just a premarket checkpoint. Section 524B of the FD&C Act underscores the need for lifecycle management of cybersecurity risks [1]. Building on the SPDF, this approach requires continuous monitoring and rapid response to emerging threats.
At the deployment stage, devices should come with secure default settings, hardening guidelines, and clear labeling to help healthcare organizations implement them securely in clinical environments [3]. Postmarket, manufacturers must stay vigilant by monitoring for new vulnerabilities through coordinated vulnerability disclosure programs, threat intelligence, and third-party advisories. They must assess these vulnerabilities' impacts and release timely patches or compensating controls as needed [4]. The FDA’s guidance reinforces the importance of having robust plans and procedures for monitoring, identifying, disclosing, and addressing vulnerabilities throughout the device lifecycle [4].
2. Security Architecture and Technical Controls
FDA Compliance and Expectations
Following the Secure Product Development Framework (SPDF), a strong security architecture is a critical component for premarket cybersecurity compliance. The FDA's final guidance from June 2025 emphasizes that security architecture and technical controls are essential to provide "reasonable assurance of cybersecurity." To meet these requirements, manufacturers must include architecture diagrams that outline communication paths, protocols, trust boundaries, and any third-party components. Additionally, the FDA expects a risk-based approach to security architecture, detailing how the device's design addresses threats across hardware, software, and connectivity layers. These requirements align closely with the SPDF principles discussed earlier.
Reviewers evaluate whether the architecture supports key objectives like authenticity (including integrity), authorization, availability, confidentiality, and secure, timely updates and patches. Each technical control must be directly linked to specific risks identified in the manufacturer's threat model. The FDA also advises that security architecture design requirements be built into the SPDF and integrated into broader quality system processes.
Impact on Patient Safety and Device Effectiveness
Cybersecurity plays a pivotal role in ensuring both patient safety and the effectiveness of medical devices. Strong security controls not only reduce cyber risks but also maintain device performance. Manufacturers must show how features like authentication, encryption, and network isolation protect against unauthorized access or tampering. These safeguards are essential to prevent scenarios that could endanger patients. Technologies such as secure boot and code signing add another layer of protection, ensuring that devices can recover from security issues while continuing to operate safely and effectively.
Integration with Quality Management Systems
Decisions about security architecture must be seamlessly incorporated into the manufacturer's Quality Management System (QMS). This involves managing security design through established processes like design planning, documentation of inputs and outputs, verification, validation, and formal design reviews. Threat modeling, secure coding practices, technical control verification, and configuration management should all be embedded within the QMS to ensure a comprehensive approach to security.
Lifecycle Management of Cybersecurity Risks
The FDA advocates for a lifecycle approach to managing cybersecurity risks, requiring manufacturers to maintain effective security measures throughout a device's operational life. This includes continuous monitoring, regular vulnerability assessments, and planning for the eventual end-of-life for devices and their supporting systems. Manufacturers must stay vigilant about emerging vulnerabilities in areas like operating systems, cryptographic libraries, and communication protocols, addressing them through secure updates or other mitigations.
Documentation should clearly identify third-party components and external services, detailing how they are secured over time. For example, devices must demonstrate safe operation on standard U.S. hospital networks, with controls that integrate smoothly with existing firewalls, authentication systems, and network segmentation. Platforms like Censinet RiskOps™ are often used by healthcare organizations to evaluate security postures and streamline third-party risk assessments. These technical measures not only support premarket documentation but also lay the groundwork for ongoing vulnerability management.
3. Software Bill of Materials (SBOM) and Third-Party Component Management
When it comes to secure device design, having a detailed SBOM and a structured approach to managing third-party components is essential for staying ahead of vulnerabilities.
FDA Compliance and Expectations
As outlined in Section 524B of the FD&C Act, manufacturers are required to include a machine-readable SBOM in premarket submissions to the FDA [10][11]. This mandate, effective since March 29, 2023, applies to 510(k), De Novo, PMA, HDE submissions, and related supplements [11]. According to the FDA's final guidance issued on June 27, 2025, failure to provide an adequate SBOM could result in Refuse to Accept (RTA) decisions or technical screening holds [1].
The FDA expects SBOMs to serve as comprehensive inventories of all software components in a device, including proprietary, open-source, third-party, and off-the-shelf software [3][6]. Each entry in the SBOM should detail the component name, version, supplier, dependencies, and licensing to support thorough vulnerability assessments [10]. Additionally, the SBOM must link components to specific device functions, especially those critical to safety or security, such as authentication, encryption, and update mechanisms [3][7].
Manufacturers are also required to establish a third-party component management process. This process should define how third-party and open-source components are selected, approved, and monitored. It must also include methods for tracking vulnerabilities through resources like the National Vulnerability Database (NVD) or vendor advisories [3][6]. This applies to all third-party elements, such as communication libraries, embedded operating systems, cryptographic modules, and cloud or mobile components [10][3].
Impact on Patient Safety and Device Effectiveness
An accurate SBOM plays a critical role in reducing risks and improving patient safety by enabling quick responses to vulnerabilities. The FDA emphasizes that SBOMs and third-party management are integral to ensuring the safety and effectiveness of medical devices. Undocumented or poorly managed components can create vulnerabilities that compromise device functionality or patient data [2][3].
Take, for example, a connected infusion pump using an open-source TCP/IP stack and TLS library. If a vulnerability is discovered, a detailed SBOM allows manufacturers to quickly identify affected devices, software versions, and deployment environments. This speeds up safety assessments and patch deployment, minimizing patient risk [2][9]. Without an SBOM, manufacturers may need to conduct time-consuming manual investigations across multiple product lines, delaying mitigation efforts [2][3].
Recent research highlights the urgency of these measures: 53% of connected medical and healthcare IoT devices have at least one unpatched critical vulnerability [10]. For instance, an unpatched third-party communication library could allow remote tampering with device settings, potentially impacting dosing, stimulation, or monitoring accuracy - leading to direct patient harm [2].
Integration with Quality Management Systems
The FDA's cybersecurity guidance integrates SBOM and third-party management into quality system controls [3][7]. SBOMs should be tied to design inputs, outputs, and verification artifacts, ensuring that every software component is supported by documented requirements, risk analyses, and verification evidence [3][12].
Third-party software must be managed through supplier controls, purchasing procedures, configuration management, and CAPA (Corrective and Preventive Action) processes [3][7]. Third-party software suppliers are treated as critical suppliers, with contracts outlining expectations for security support, vulnerability notifications, and update timelines. Additionally, change control procedures must ensure that any updates to third-party components trigger hazard re-analyses, regression testing, and evaluations for potential FDA submissions or notifications [3][7]. This approach supports ongoing risk management throughout the device’s lifecycle.
Lifecycle Management of Cybersecurity Risks
The FDA expects cybersecurity risk management to continue throughout the device’s lifecycle, and SBOMs are a key part of this ongoing effort [2][3]. A living SBOM enables continuous monitoring for new vulnerabilities, rapid impact analysis, and prioritization of fixes based on clinical risk and deployment context [2][3].
Manufacturers are required to update the SBOM with each release and inform customers through security bulletins or field safety notices [10][11][3]. Postmarket plans should incorporate SBOM data into vulnerability monitoring, incident response, and update programs, with clear timelines for assessing and mitigating vulnerabilities in critical components [3][4].
Healthcare organizations can also leverage SBOMs to cross-reference known vulnerabilities against their existing devices, prioritize fixes for high-risk systems, and make informed purchasing decisions [2][3]. Tools like Censinet RiskOps™ simplify third-party risk assessments by automating risk scoring, tracking remediation progress, and coordinating responses between manufacturers and healthcare providers [2][6].
sbb-itb-535baee
4. Premarket Documentation for Cybersecurity Assurance
FDA Compliance and Expectations
On June 27, 2025, the FDA released its final guidance titled "Cybersecurity in Medical Devices: Quality System Considerations and Content of Premarket Submissions." This document outlines the cybersecurity requirements for premarket submissions, including 510(k), PMA, De Novo, and HDE applications. As mandated by Section 524B of the FD&C Act, manufacturers of cyber devices must provide specific documentation, such as:
- A cybersecurity risk assessment
- Threat modeling
- Security architecture overview
- Risk-mapped security controls
- Secure Product Development Framework (SPDF) procedures
- Software Bill of Materials (SBOM)
- Postmarket vulnerability management plans [3]
This guidance builds upon previously discussed cybersecurity design and risk management practices, emphasizing the need for a unified compliance approach. The FDA ties the concept of "reasonable assurance of cybersecurity" directly to the statutory standards of safety and effectiveness. Failing to meet these documentation requirements can lead to denial of premarket authorization. To avoid this, manufacturers need to embed cybersecurity considerations into their quality systems and design controls, addressing not just the device itself but also its related systems [3].
Impact on Patient Safety and Device Effectiveness
Cybersecurity documentation isn't just a regulatory checkbox - it plays a critical role in ensuring patient safety and device reliability. Manufacturers must clearly demonstrate how identified threats and vulnerabilities could impact patient outcomes. For example, exploited vulnerabilities might lead to incorrect dosing, delayed treatments, or compromised clinical data. To address these risks, manufacturers must provide detailed analyses that connect specific threats to potential harms, such as overdose, underdose, therapy interruptions, or data privacy breaches.
Take a connected infusion pump, for instance. Its documentation might highlight risks like unauthorized dosage changes via network access. To mitigate these risks, the manufacturer could outline measures such as authentication protocols, encryption, network segmentation, and audit trails. These security controls should be directly linked to the vulnerabilities they address, ensuring a clear connection between risk and mitigation.
Integration with Quality Management Systems
The FDA considers cybersecurity a fundamental part of a device’s quality management system (QMS). This means manufacturers must align their cybersecurity documentation with QMS processes to demonstrate a robust and repeatable approach. Key elements include:
- Design controls that incorporate cybersecurity requirements
- Risk management procedures addressing both cybersecurity and traditional safety concerns
- Configuration management and coding standards
- Testing and vulnerability-handling processes
All submitted documentation must tie back to controlled QMS procedures to ensure consistency and auditability. Platforms like Censinet RiskOps™ can help streamline this process by enabling structured risk assessments, SBOM-based analysis, and coordinated mitigation planning.
Lifecycle Management of Cybersecurity Risks
Managing cybersecurity risks doesn’t stop once a device hits the market. Premarket documentation must explain how manufacturers will adapt to emerging threats and vulnerabilities. This includes detailing processes for updating threat models, conducting ongoing security monitoring, and evaluating vulnerabilities through sources like the National Vulnerability Database or vendor advisories.
Manufacturers also need to outline their strategies for versioning and configuration management. These strategies should specify how changes to a device are assessed for cybersecurity impact and when such modifications might require a new submission. Additionally, the vulnerability management plan should describe:
- Monitoring sources for new threats
- Internal workflows for triaging vulnerabilities
- Severity scoring methods
- Timelines for patch development and testing
- Contingency measures, such as compensating controls or customer notifications, when immediate updates aren’t feasible [3].
5. Postmarket Cybersecurity Planning and Vulnerability Management
FDA Compliance and Expectations
Once a medical device hits the market, the responsibility for its cybersecurity doesn’t end - it’s just the beginning. Section 524B of the FD&C Act has transformed how manufacturers handle cybersecurity after a device is released. Postmarket cybersecurity is now an ongoing responsibility, not a one-time task during premarket approval [10][13]. To meet FDA requirements, manufacturers must create and implement a plan to monitor, identify, and address cybersecurity vulnerabilities as they arise [11].
This means setting up robust monitoring systems that pull from threat intelligence feeds, vulnerability databases like the National Vulnerability Database, and vendor advisories. If a vulnerability is discovered, manufacturers are expected to notify customers within about 30 days and provide clear steps for mitigation, such as patches or temporary controls [10]. The FDA has made it clear: failing to manage these vulnerabilities could lead to the denial or withdrawal of a device’s authorization. Cybersecurity noncompliance isn’t just a regulatory issue anymore - it’s now classified as a "prohibited act" under federal law, which could result in penalties and even civil liability [13]. This structured approach builds on premarket efforts, ensuring devices remain safe and secure throughout their lifecycle.
Impact on Patient Safety and Device Effectiveness
Cybersecurity vulnerabilities are not just technical glitches - they can directly impact patient safety. For instance, a ransomware attack on an infusion pump could alter medication dosages, or a hack into a diagnostic imaging system could corrupt scan results. Even worse, compromised patient data could delay critical treatment decisions. These risks are far from hypothetical - they’re real and potentially life-threatening.
The FDA underscores that "reasonable assurance of cybersecurity" is essential for ensuring a device’s safety and effectiveness [13]. Without proper monitoring and mitigation of new threats, a device that was once considered safe may no longer perform as intended. That’s why the FDA treats postmarket cybersecurity as a safety-critical function, placing it on the same level as traditional reliability and quality controls [3][9]. Manufacturers are expected to implement risk-based processes to address vulnerabilities. Critical threats categorized as "uncontrolled" require immediate updates, while less urgent issues labeled as "controlled" can be addressed during scheduled maintenance [10][13].
Integration with Quality Management Systems
Postmarket cybersecurity isn’t a standalone effort - it must be woven into the broader Quality Management System (QMS) under 21 CFR Part 820. This includes integrating cybersecurity with design controls, complaint handling, CAPA (Corrective and Preventive Actions), and risk management processes [13][3]. For example, vulnerability reports from healthcare providers or security researchers should trigger CAPA investigations, updates to risk files, and patch releases, all managed through established change control procedures [3][5].
This approach ensures that cybersecurity is handled systematically and not treated as a series of isolated IT problems. It also demonstrates to the FDA that your organization is capable of managing cybersecurity risks throughout the device’s lifecycle. Maintaining an up-to-date Software Bill of Materials (SBOM) is particularly crucial in the postmarket phase. For example, when vulnerabilities like the log4j incident arise, an accurate SBOM helps manufacturers quickly identify affected devices and prioritize patches [10][3].
Lifecycle Management of Cybersecurity Risks
Cybersecurity risk management isn’t a one-and-done deal - it’s a continuous process that lasts throughout the device’s lifecycle. Even after a device is shipped or deployed in a hospital, manufacturers must regularly update threat assessments and plan for secure updates and patchability until the device’s end-of-support date [3][5][6].
The FDA stresses the importance of clearly communicating end-of-life and end-of-support timelines to healthcare organizations. This allows hospitals and clinics to plan for replacements or upgrades well in advance [10]. Additionally, lifecycle management should include steps for hardening devices and securely decommissioning them to avoid leaving behind outdated systems that could become targets for cyberattacks.
To support these efforts, many healthcare organizations are turning to cybersecurity platforms like Censinet RiskOps™. These platforms help operationalize ongoing risk assessments, track and address vulnerabilities, and benchmark cybersecurity performance across their medical device inventory. By partnering with such tools, manufacturers can scale their postmarket efforts and maintain a collaborative approach to device security.
Conclusion
The FDA's five premarket cybersecurity requirements - Secure Product Development Framework (SPDF), security architecture and technical controls, Software Bill of Materials (SBOM) and third‑party component management, premarket cybersecurity documentation, and postmarket vulnerability management - are essential for achieving "reasonable assurance of cybersecurity" for cyber devices under Section 524B of the FD&C Act [1][3][8]. Together, these elements form a robust framework that addresses cybersecurity from the initial design stages through to the device's retirement.
This framework not only satisfies regulatory demands but also ensures devices perform reliably and support patient care throughout their lifecycle. By reducing the risks of cyberattacks or vulnerabilities that could disrupt device operations, alter therapies or diagnostics, or compromise clinical data, these requirements directly enhance patient safety [2][3][14]. Incorporating cybersecurity measures across the device lifecycle demonstrates to the FDA and U.S. healthcare providers that medical devices can consistently deliver safe and effective therapy.
To streamline compliance with these requirements, manufacturers are increasingly leveraging advanced cybersecurity platforms. Censinet RiskOps™ provides tools for manufacturers and healthcare organizations to implement these requirements through structured workflows and standardized assessments. The platform centralizes cybersecurity documentation - such as risk analyses, test results, SBOM data, and policies - making it easier to compile and maintain the necessary evidence [1][2]. For healthcare organizations, Censinet RiskOps simplifies third-party and enterprise risk assessments across clinical applications, connected devices, and supply chains. It offers a unified view of cyber risks affecting patient data and protected health information (PHI) [2]. Shared workflows and collaborative risk registers enable manufacturers and healthcare delivery organizations (HDOs) to coordinate mitigation efforts, manage vulnerabilities, and document resolutions - especially critical when firmware or software updates are deployed across devices in U.S. hospitals [2].
FAQs
Why is the Software Bill of Materials (SBOM) important for medical device cybersecurity?
The Software Bill of Materials (SBOM) serves as an essential resource for strengthening the cybersecurity of medical devices. Essentially, it’s a detailed inventory of all the software components that make up a device. This level of transparency gives manufacturers and healthcare providers a clear view into the device's internal systems, making it easier to pinpoint and address potential vulnerabilities.
An accurate SBOM isn’t just about compliance - it’s about staying ahead of risks. By keeping this record up to date, organizations can better manage security threats, meet regulatory standards, and react quickly to new cybersecurity challenges. Ultimately, it’s a critical safeguard for protecting both patient safety and sensitive healthcare information.
How does the Secure Product Development Framework (SPDF) improve the safety of medical devices?
The Secure Product Development Framework (SPDF) enhances the safety of medical devices by integrating cybersecurity best practices into each phase of the development process. This forward-thinking method addresses potential vulnerabilities early, reinforces device security, and aligns with FDA premarket requirements.
Focusing on security from the design stage onward, SPDF enables manufacturers to develop dependable devices that safeguard sensitive patient information and reduce risks to patient safety. This approach ensures the creation of healthcare solutions that both patients and providers can rely on with confidence.
What does the FDA require for managing cybersecurity risks after a device is on the market?
The FDA mandates that manufacturers take proactive steps to handle cybersecurity risks during a device's entire lifecycle. This involves ongoing monitoring, performing regular risk evaluations, and rolling out timely updates to counter emerging threats.
Such measures are critical for keeping devices secure and functional, safeguarding both patient information and the device's performance against ever-changing cybersecurity threats.
Related Blog Posts
Key Points:
What are the key premarket cybersecurity requirements for medical devices?
- Cybersecurity Management Plan: Manufacturers must submit a plan detailing how they will monitor, identify, and address cybersecurity vulnerabilities throughout the device lifecycle.
- Risk Assessments: Conduct threat modeling and risk analysis to identify potential vulnerabilities and mitigation strategies.
- Software Bill of Materials (SBOM): Provide a detailed inventory of software components to facilitate vulnerability tracking and updates.
- Postmarket Monitoring: Include processes for ongoing vulnerability monitoring and coordinated vulnerability disclosure (CVD).
What is the FDA’s role in medical device cybersecurity?
- Guidance Provider: The FDA issues guidance documents to help manufacturers design secure devices and meet regulatory requirements.
- Regulatory Oversight: The FDA evaluates cybersecurity risks as part of its premarket review process, ensuring devices are safe and effective.
- Lifecycle Management: The FDA emphasizes cybersecurity throughout the Total Product Lifecycle (TPLC), including premarket and postmarket phases.
What is a Software Bill of Materials (SBOM), and why is it important?
- Definition: An SBOM is a detailed inventory of all software components used in a medical device.
- Purpose: It helps manufacturers identify vulnerabilities, track updates, and ensure compliance with cybersecurity standards.
- Regulatory Requirement: The FDA requires SBOMs as part of premarket submissions for cyber devices.
What are the consequences of non-compliance with FDA cybersecurity requirements?
- Delayed Approvals: Non-compliance can result in a refusal to accept premarket submissions or technical screening holds.
- Increased Risks: Devices with unresolved vulnerabilities may expose patients to safety risks and organizations to reputational damage.
- Regulatory Penalties: Failure to meet cybersecurity requirements can lead to enforcement actions by the FDA.
How can manufacturers demonstrate compliance with FDA cybersecurity requirements?
- Comprehensive Documentation: Submit a cybersecurity management plan, threat modeling results, and evidence of risk mitigation.
- Risk-Based Approach: Align documentation with the device’s risk level, as recommended by the FDA.
- Lifecycle Evidence: Provide proof of ongoing monitoring, vulnerability management, and secure design practices.
What tools can help manufacturers meet premarket cybersecurity requirements?
- C2A Security’s EVSec Platform: Automates SBOM management, vulnerability tracking, and compliance documentation.
- Threat Modeling Tools: Support risk assessments and mitigation planning.
- Compliance Platforms: Streamline evidence collection and submission for FDA premarket reviews.


