How Multi-Factor Authentication Prevents Healthcare Breaches
Post Summary
Healthcare data breaches are on the rise, with weak password-only systems being a major culprit. Multi-factor authentication (MFA) adds extra security by requiring users to verify their identity using two or more methods, such as a password, a smartphone notification, or biometrics like fingerprints. This approach blocks 99.9% of account compromise attempts, according to Microsoft.
Key takeaways:
- 86% of healthcare breaches involve stolen credentials.
- MFA protects critical systems like EHRs, billing platforms, and remote access tools.
- Phishing-resistant methods (e.g., hardware keys) are more secure than SMS codes.
Cyber Threats That Exploit Weak Access Controls
Healthcare organizations frequently deal with attacks that take advantage of password-only systems, leaving sensitive data and operations vulnerable.
Credential Theft and Phishing Attacks
Attackers often rely on phishing emails and deceptive phone calls, pretending to be IT support or vendors, to trick employees into revealing their login credentials. These scams direct staff to fake login pages, where their credentials are stolen. Once attackers gain access, they can infiltrate critical systems like web-based EHRs, cloud email platforms, and billing portals. This access allows them to steal PHI, redirect insurance claims, or launch ransomware attacks. According to the HHS Cybersecurity Coordination Center, common entry points for such breaches include EHR systems, patient portals, and remote access services [2]. Beyond phishing, attackers also use direct password-based methods to compromise systems.
Password-Based Attacks
Weak or short passwords are a prime target for brute-force attacks, where automated tools repeatedly attempt login combinations. Remote access portals and externally exposed admin interfaces are especially vulnerable to this method [1]. Credential stuffing is another tactic, where attackers use stolen username and password pairs from unrelated data breaches. This becomes a bigger issue when healthcare staff reuse passwords across multiple systems [4]. Shared accounts with simple, rarely updated passwords further complicate security. These accounts can allow attackers to move undetected between systems like EHRs, imaging platforms, and medication dispensing systems, making incident response and HIPAA reporting much more challenging [7].
Remote Access and Privileged Account Risks
Internet-facing VPNs, RDP, and remote support portals without MFA are essentially open doors for attackers to infiltrate hospital networks [6]. Once inside, they can access file shares, domain controllers, and clinical systems to deploy ransomware or steal PHI on a large scale. This often leads to serious operational disruptions, such as canceled procedures, delayed care, and shutdowns of billing or scheduling systems [2].
Privileged accounts, such as those held by domain admins, EHR super-users, or cloud administrators, pose an even greater risk. These accounts have elevated permissions, granting access to configure systems and manage extensive databases [6]. Attackers often begin by compromising a low-level user through phishing and then escalate privileges by exploiting misconfigured permissions or scanning Active Directory. With control over a privileged account, they can disable security tools, create backdoor accounts, and spread ransomware across multiple facilities [2]. These scenarios highlight the urgent need for MFA to strengthen access controls in healthcare environments.
How MFA Prevents Healthcare Breaches
How MFA Blocks Common Healthcare Cyber Threats
Multi-factor authentication (MFA) acts as a critical defense against credential-based attacks by requiring an additional, independent verification step. Even if a password is compromised, MFA ensures that access is denied without a secondary factor - such as a one-time code, push notification, hardware token, or biometric verification - that only the legitimate user can provide.
Blocking Common Attack Methods
MFA is highly effective at neutralizing common attack techniques by introducing a barrier that attackers cannot easily overcome. For example, in phishing attacks, when a healthcare employee unknowingly enters stolen credentials into a fake login page, the attacker may capture the username and password but will still face the MFA prompt. Push notifications further enhance security by alerting users to unauthorized login attempts, enabling them to report the activity and reset their credentials immediately [1][3].
Credential stuffing, where attackers use stolen username-password pairs from other breaches to gain access, is thwarted by MFA. The additional requirement for a time-sensitive or device-specific factor prevents automated login attempts from succeeding [1][5]. Similarly, brute-force attacks, which rely on guessing passwords, are rendered ineffective because even a successfully guessed password is useless without the second factor [1][3]. These safeguards align with broader Zero Trust security principles.
Supporting Zero Trust and Least-Privilege Access
Federal guidelines emphasize MFA as a foundational element of Zero Trust security for critical infrastructure, including healthcare [1]. Zero Trust operates on the philosophy of "never trust, always verify", requiring continuous validation of identity for every login attempt, whether it involves electronic health records (EHRs), patient portals, or administrative systems [1][6]. Unlike traditional perimeter defenses, MFA offers ongoing identity verification, making it much harder for attackers to bypass security.
Healthcare organizations often enhance MFA with context-aware policies, such as requiring stronger authentication for logins from unfamiliar devices, unmanaged endpoints, or unusual geographic locations. This dynamic approach ensures trust is continually reassessed [6]. MFA also bolsters internal security by controlling access to sensitive patient health information (PHI) across multiple entry points.
Additionally, MFA strengthens least-privilege access by requiring extra verification for elevated permissions. For example, routine access to EHRs may only need basic credentials, but accessing sensitive behavioral health records, prescribing controlled substances, or exporting large datasets would require step-up authentication [2][6]. Time-limited privileged access tools can also integrate with MFA, granting temporary administrative rights only after fresh authentication and revoking them automatically, minimizing opportunities for credential misuse [6].
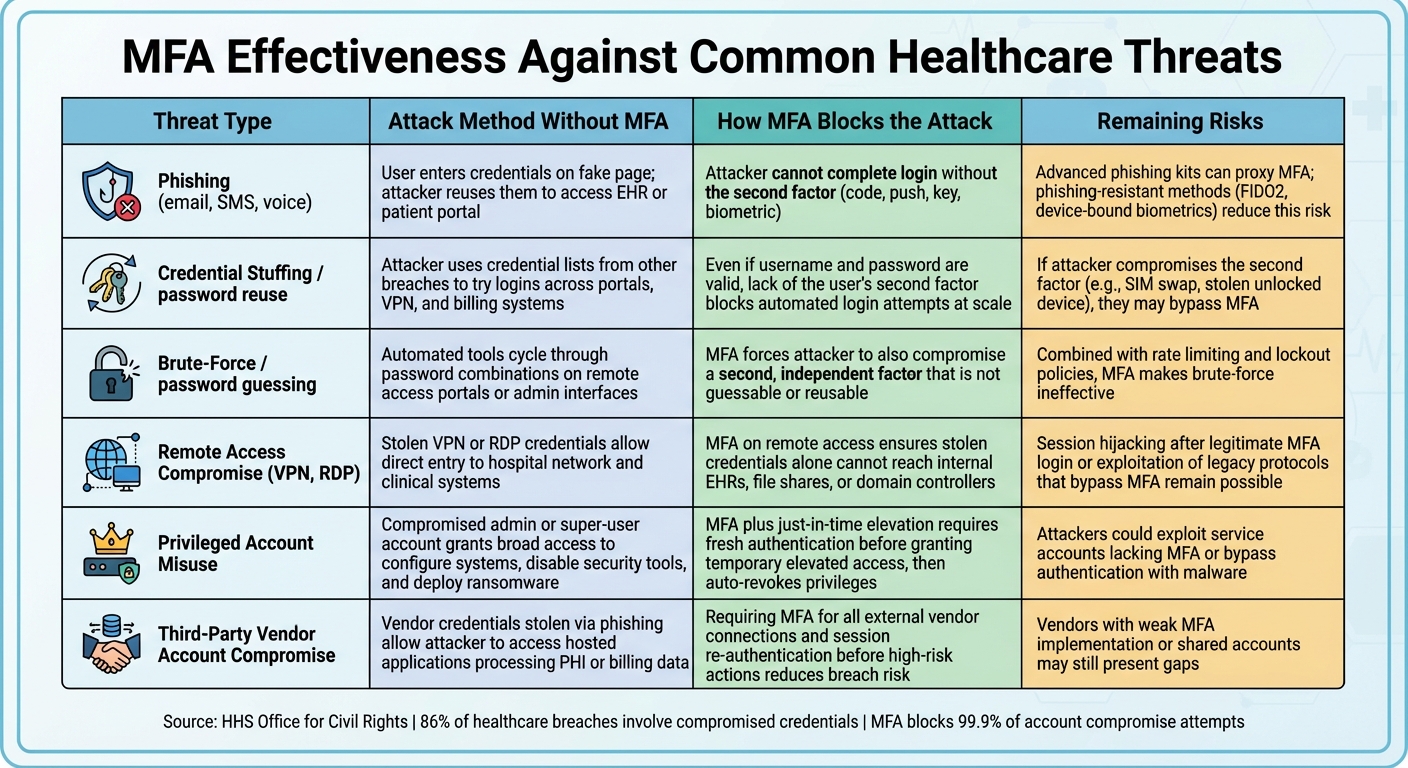
MFA Effectiveness Against Common Threats
| Threat Type | Attack Method Without MFA | How MFA Blocks the Attack | Remaining Risks |
|---|---|---|---|
| Phishing (email, SMS, voice) | User enters credentials on fake page; attacker reuses them to access EHR or patient portal | Attacker cannot complete login without the second factor (code, push, key, biometric) [1][5][3] | Advanced phishing kits can proxy MFA; phishing-resistant methods (FIDO2, device-bound biometrics) reduce this risk [5][7] |
| Credential stuffing / password reuse | Attacker uses credential lists from other breaches to try logins across portals, VPN, and billing systems | Even if username and password are valid, lack of the user's second factor blocks automated login attempts at scale [1][5][7] | If attacker compromises the second factor (e.g., SIM swap, stolen unlocked device), they may bypass MFA |
| Brute-force / password guessing | Automated tools cycle through password combinations on remote access portals or admin interfaces | MFA forces attacker to also compromise a second, independent factor that is not guessable or reusable [1][3] | Combined with rate limiting and lockout policies, MFA makes brute-force ineffective [5][4] |
| Remote access compromise (VPN, RDP) | Stolen VPN or RDP credentials allow direct entry to hospital network and clinical systems | MFA on remote access ensures stolen credentials alone cannot reach internal EHRs, file shares, or domain controllers [2][6] | Session hijacking after legitimate MFA login or exploitation of legacy protocols that bypass MFA remain possible [1][6] |
| Privileged account misuse | Compromised admin or super-user account grants broad access to configure systems, disable security tools, and deploy ransomware | MFA plus just-in-time elevation requires fresh authentication before granting temporary elevated access, then auto-revokes privileges [6] | Attackers could exploit service accounts lacking MFA or bypass authentication with malware [4] |
| Third-party vendor account compromise | Vendor credentials stolen via phishing allow attacker to access hosted applications processing PHI or billing data | Requiring MFA for all external vendor connections and session re-authentication before high-risk actions reduces breach risk [2][4] | Vendors with weak MFA implementation or shared accounts may still present gaps |
This table highlights how MFA mitigates a range of threats, illustrating its value in healthcare environments.
The HHS Office for Civil Rights has identified weak authentication measures as a major factor in recent healthcare data breaches [1]. A study by the Center for Cybersecurity Policy reveals that compromised credentials account for approximately 86% of breaches, many of which could have been prevented with even basic MFA [7]. However, while MFA significantly enhances security, it is not foolproof. Attackers may exploit legacy protocols that bypass MFA, intercept SMS codes through SIM swapping, or use methods like prompt-bombing to trick users into approving fraudulent requests [1][6].
To address these challenges, healthcare organizations should adopt phishing-resistant MFA solutions such as hardware security keys or FIDO2/WebAuthn, implement number-matching push notifications to combat prompt fatigue, and combine MFA with endpoint protection, network segmentation, and continuous monitoring [1][6]. These measures collectively enhance cybersecurity and safeguard PHI from unauthorized access.
Implementing MFA in Healthcare Organizations
Critical Systems That Require MFA
To safeguard sensitive data and maintain compliance, healthcare organizations must prioritize multi-factor authentication (MFA) for systems that handle electronic protected health information (ePHI), financial records, or those critical to care delivery. Weak authentication has been a leading cause of healthcare data breaches, making MFA a necessity for both covered entities and business associates.
Start by securing core systems, including electronic health record (EHR) and electronic medical record (EMR) platforms, patient portals, telehealth and remote monitoring systems, and e-prescribing applications. Additionally, extend MFA to email and messaging tools that process PHI, VPNs and remote access gateways, identity and access management portals, cloud collaboration software, billing systems, and privileged administrative consoles for servers, databases, and medical devices.
To ensure no gaps, conduct a workflow inventory to identify every point where PHI is accessed. This involves tracking how different roles - clinicians, schedulers, IT staff, and third-party vendors - interact with PHI during their daily tasks. For instance, a telehealth session might require logging into a patient portal, accessing a video platform, viewing the EHR, and using e-prescribing tools - all of which must be secured with MFA. As Matt Christensen, Sr. Director GRC at Intermountain Health, highlights, healthcare demands specialized tools to address its unique challenges:
"Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare" [8].
After mapping access points, the next step is to determine the most appropriate MFA methods for each clinical environment.
Selecting MFA Methods for Clinical Workflows
Choosing the right MFA method requires balancing security with the practical needs of healthcare workflows. Common MFA options include SMS or voice codes, authenticator apps generating one-time passcodes, push notifications, biometrics, and hardware-based tools like smart cards or FIDO2 security keys. However, SMS and voice codes are increasingly seen as less secure due to vulnerabilities like SIM-swapping.
Push notifications with number-matching - where a code displayed on the login screen must be entered into the app - offer stronger protection against push-bombing attacks. Biometrics, such as fingerprint or facial recognition on managed devices, provide quick and secure authentication but require solid device security policies. For high-risk access, hardware tokens and FIDO2 security keys deliver phishing-resistant MFA, though scaling their deployment can be challenging.
Different clinical settings require tailored MFA solutions. In inpatient units and emergency departments, where shared workstations are common, badge-tap plus PIN, desktop single sign-on integrated with biometric MFA, or proximity-based reauthentication can help minimize disruptions. Ambulatory clinics may rely on push notifications or time-based one-time passcode (TOTP) apps on mobile devices, with extended session lifetimes to reduce login prompts. For telehealth staff or remote coders, enforcing MFA at the VPN or zero-trust network edge - while requiring additional verification for logins from unfamiliar devices, new locations, or non-U.S. IP addresses - ensures strong security without hindering productivity.
Configuring MFA for Security and Usability
Once you’ve selected the right MFA methods, the key is seamless integration into clinical workflows. Pairing MFA with single sign-on (SSO) reduces the need for repeated logins across systems like EHRs, PACS, e-prescribing platforms, and lab portals. Context-aware policies can further enhance usability by limiting re-authentication to situations where risk changes, such as logins from a new device or location.
Introduce step-up MFA for high-risk actions, such as exporting PHI, modifying permissions, e-prescribing controlled substances, accessing systems after hours, or logging in from unmanaged devices. This adaptive approach ensures added security only when necessary, maintaining workflow efficiency for routine tasks.
For shared workstations, use fast reauthentication methods like badge-tap or biometrics to prevent repeated logins. Disable "remember me" settings, enforce MFA at the start of each session, and implement strict session lock and logout protocols to prevent unauthorized access.
MFA should also work hand-in-hand with device management policies. For managed devices, require screen locks and encryption. On shared workstations, enforce logout protocols and disable persistent login settings. For bring-your-own-device (BYOD) scenarios, specify approved MFA apps and enable remote wiping capabilities. Additionally, third-party vendors accessing PHI or managed systems should adhere to the organization’s MFA standards, with compliance monitored through tools like Censinet RiskOps™.
sbb-itb-535baee
MFA and Healthcare Risk Management
Phased MFA Rollout Based on Risk Levels
When rolling out multi-factor authentication (MFA) in healthcare, a targeted, risk-based approach is far more effective than trying to apply the same strategy across the board. Start by securing high-risk assets like identity infrastructure (Active Directory, Azure AD/Entra, privileged access management), administrative consoles (hypervisors, backup systems), and remote access points (VPN, remote desktop gateways, webmail). These are critical because their compromise can lead to lateral attacks and widespread ransomware incidents [6]. At the same time, prioritize core clinical and billing platforms - such as EHR/EMR systems, e-prescribing tools, PACS/RIS, pharmacy systems, and revenue cycle applications - because breaches in these areas incur some of the highest costs per record in the U.S. [5].
In the next phase, expand MFA to cover all clinical systems, patient portals, and high-risk third-party access. This includes telehealth platforms, cloud-hosted EHR modules, and vendors with access to protected health information (PHI), like billing services and medical device providers. Vendor-related breaches and supply-chain attacks are on the rise, making it essential to enforce MFA for these parties [2][4]. Finally, implement MFA for all staff and vendor connections that interact with PHI, including SSO integrations and shared workstation access.
Keep track of adoption metrics, such as the percentage of users and systems with MFA enabled, as part of your ongoing risk assessments. Include MFA in your risk registers to address threats like credential theft, phishing, ransomware, and compromised remote access [1][2][5]. This phased rollout not only reduces risks effectively but also supports regulatory compliance efforts.
Meeting HIPAA and Regulatory Requirements with MFA
Under the HIPAA Security Rule, healthcare organizations and their business associates must implement technical safeguards for unique user identification, entity authentication, and encryption/authentication of ePHI in transit [2][5]. MFA strengthens these safeguards by requiring multiple factors to verify user identity, significantly reducing the chances of stolen credentials being misused. The U.S. Department of Health and Human Services Office for Civil Rights (OCR) has frequently highlighted weak authentication measures as a major contributor to healthcare data breaches. They expect organizations to adopt "reasonable and appropriate" measures like MFA, especially for remote access, administrative accounts, and cloud-based systems [1][2].
To ensure compliance, document your MFA policies, configurations, and procedures. This documentation should outline which systems require MFA, approved authentication methods, and how exceptions are justified and monitored. Logs should also be reviewed as part of audit controls [1][2][5]. Federal guidance increasingly positions MFA as a key element of Zero Trust architectures, which focus on protecting sensitive data and continuously verifying user identities [1]. By aligning with these principles, your organization not only meets HIPAA requirements but also prepares for evolving regulations and cyber insurance demands. These steps are crucial for preventing unauthorized access and safeguarding patient data.
Using Censinet for MFA Assessment and Monitoring
Effective risk management requires reliable tools, and Censinet provides a strong solution. Its RiskOps platform is specifically designed for healthcare cybersecurity, helping organizations catalog systems, identify where ePHI is stored, and assess MFA implementation on each asset [2][4]. By using standardized questionnaires tailored to healthcare workflows, you can evaluate whether vendors enforce MFA for user and admin access, remote connections, and privileged functions. It also helps you identify risks when MFA is absent or relies on outdated methods like SMS [2][4]. The platform offers centralized visibility into MFA adoption across your ecosystem, enabling risk managers to prioritize fixes in areas like billing platforms, telehealth solutions, and medical device portals.
Censinet supports continuous or periodic reassessments, ensuring that changes - like stronger MFA methods or new applications - are reflected in your risk evaluations [2][4]. Dashboards provide insights into gaps, overdue remediation tasks, and areas of high residual risk, allowing teams to focus their efforts. Terry Grogan, CISO at Tower Health, shared:
"Censinet RiskOps allowed us to increase assessment capacity while reducing resource requirements" [8].
The platform also tracks remediation plans, assigns accountability, and creates an auditable trail for compliance, addressing HIPAA requirements, OCR inquiries, and board-level oversight [2][4]. For critical systems, this ensures MFA remains intact during upgrades or vendor changes, and that exceptions are justified and time-limited. Additionally, Censinet's cybersecurity benchmarking feature lets you compare your MFA implementation with peer organizations, helping secure resources and guide investment decisions. As Brian Sterud, CIO at Faith Regional Health, noted:
"Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters" [8].
Conclusion
Multi-factor authentication (MFA) addresses critical weaknesses in healthcare authentication systems - like weak passwords, credential theft, phishing attacks, and unsecured remote access - that are often exploited in breaches. According to the HHS Office for Civil Rights, weak authentication measures are a leading cause of healthcare data breaches [1]. MFA, by requiring at least two verification factors, ensures that stolen credentials alone cannot grant access to sensitive systems, such as electronic health records or billing platforms containing protected health information. In fact, MFA can block 99.9% of account compromise attempts [5].
But MFA does more than just prevent breaches - it supports operational stability. By reducing the risk of ransomware and other attacks, it helps protect critical clinical systems, such as EHRs, imaging platforms, and medication management tools, which are essential for consistent and safe patient care [2]. As healthcare increasingly relies on digital systems, maintaining the availability and integrity of data is vital for delivering reliable and secure care.
To be effective, MFA must be implemented thoughtfully and monitored continuously. Organizations should prioritize phishing-resistant methods that integrate seamlessly into clinical workflows and cover all potential access points, including VPNs, cloud applications, privileged accounts, and third-party vendors [6]. MFA also plays a key role in Zero Trust security models, which emphasize ongoing identity verification rather than relying on one-time perimeter defenses [6].
Maintaining MFA’s effectiveness requires constant vigilance. This includes tracking adoption rates, monitoring for suspicious login activity, and regularly reevaluating risks across systems and vendors [6]. Tools like Censinet RiskOps™ can assist healthcare organizations by assessing MFA maturity, pinpointing vulnerabilities, and benchmarking controls against industry standards. These measures ensure that MFA remains aligned with both regulatory requirements and organizational goals over time.
Healthcare organizations should start by securing high-risk areas - such as administrative accounts, remote access points, and core clinical systems - and then expand MFA coverage throughout the organization. Combining MFA with other security measures like least-privilege access, device verification, and network segmentation creates a multi-layered defense. Purpose-built risk management and continuous monitoring are essential to ensuring that MFA remains a reliable safeguard for patient data in the long run.
FAQs
How does multi-factor authentication help secure healthcare data?
Multi-factor authentication (MFA) strengthens the security of healthcare data by requiring users to confirm their identity through multiple verification steps. These steps often involve a combination of factors: something the user knows (like a password), something they have (such as a one-time code sent to their phone), or something they are (like a fingerprint or facial recognition).
These added layers of protection make it significantly harder for unauthorized individuals to access sensitive systems, even if login details are stolen or exposed. This is especially important in healthcare, where protecting sensitive patient records and other protected health information (PHI) is crucial for preventing breaches and maintaining trust in the system.
What are the most effective MFA methods for securing healthcare data?
The most reliable multi-factor authentication (MFA) options for securing healthcare data include biometric authentication (like fingerprint or facial recognition), hardware security tokens (such as physical security keys), and authenticator apps that create time-based one-time passwords (TOTP). These methods strengthen security by adding extra layers that block unauthorized access.
Biometric authentication stands out because it uses unique physical characteristics, making it difficult to bypass. Hardware tokens add a tangible layer of security, requiring physical possession to gain access. Meanwhile, authenticator apps are popular for their ease of use and ability to generate secure, time-sensitive codes. By combining these MFA tools, healthcare organizations can better protect sensitive patient information and meet strict security requirements.
How can healthcare providers adopt MFA without interrupting clinical workflows?
Healthcare providers can introduce multi-factor authentication (MFA) without causing significant disruptions by embedding it into their current systems and workflows. Tools like single sign-on (SSO) and adaptive authentication help simplify the process by adjusting security prompts based on the level of risk involved.
Opting for user-friendly options like biometrics or push notifications allows clinicians to access systems quickly and efficiently, even in high-stress situations. Additionally, automating MFA for high-risk activities strengthens security while maintaining the speed and efficiency critical in clinical environments.


