Patient Safety and Vendor Risk: The Hidden Threats Healthcare Organizations Must Address
Post Summary
Healthcare organizations rely on third-party vendors for critical services like EHR systems and medical devices. But when vendors face cybersecurity breaches or failures, patient safety is directly at risk. These issues can delay care, disrupt emergency operations, and lead to poor clinical decisions. Current vendor risk management approaches often fall short, focusing on compliance rather than protecting patients.
Key Insights:
- Vendor Incidents Impact Patient Safety: Breaches can compromise patient records and delay treatments, with severe consequences.
- Flaws in Risk Management: Outdated, reactive strategies and limited oversight leave gaps in addressing evolving threats.
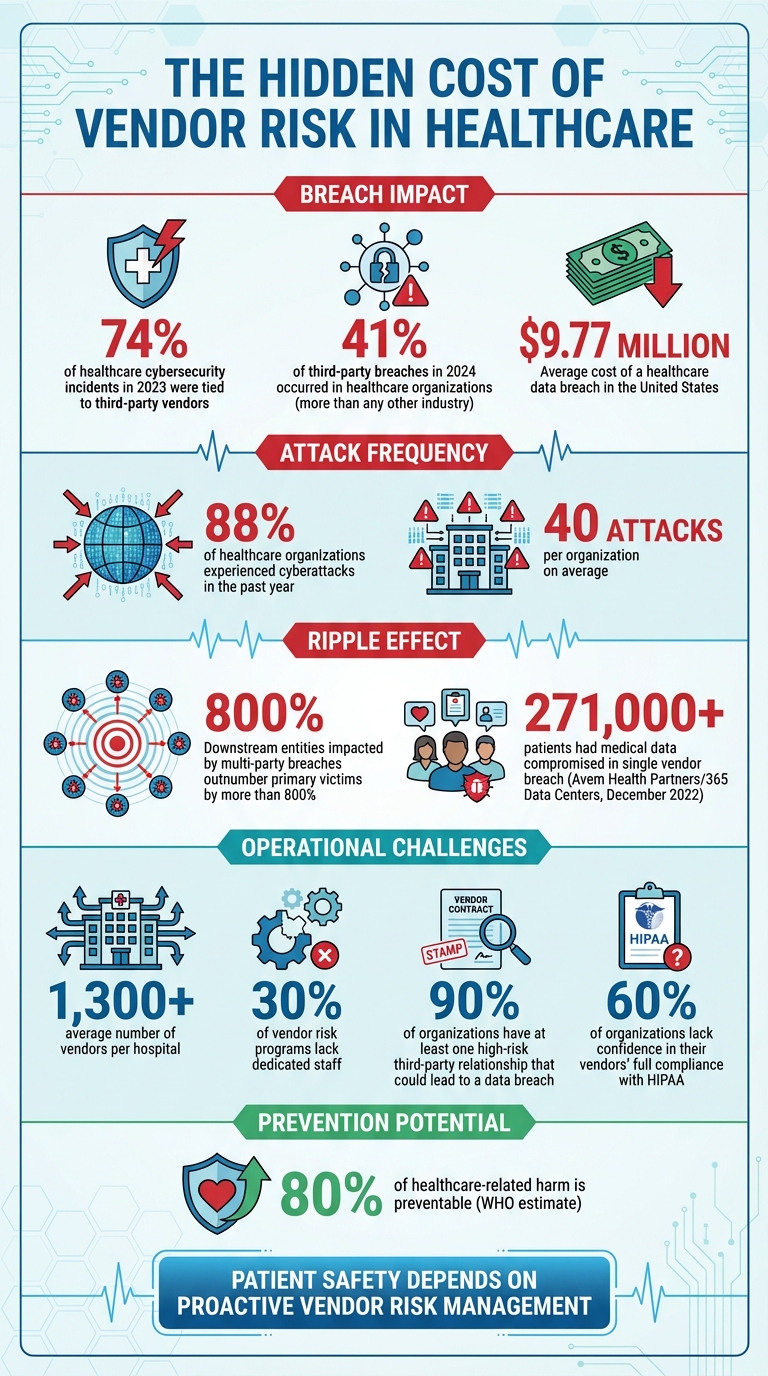
- Critical Statistics: 74% of healthcare cybersecurity incidents in 2023 were tied to third-party vendors. The average cost of a breach is $9.77 million.
- Solutions: Continuous monitoring, standardized assessments, and clear incident response plans are essential. Tools like Censinet RiskOps™ streamline management through automation and real-time oversight.
Healthcare providers must shift from compliance-focused strategies to patient-centered approaches to safeguard care and reduce risks.
Healthcare Vendor Risk Statistics: Impact on Patient Safety and Cybersecurity
Threats from Vendor Ecosystems
What Drives Risk in Vendor Ecosystems
Relying on static, one-time assessments isn't enough to manage vendor risks effectively. Limited visibility into vendor security practices leaves critical threats unchecked. Many organizations depend on self-reported questionnaires, where vendors essentially evaluate their own security measures. This method offers minimal assurance that vendors are actually implementing the practices they claim to follow.
Adding to this challenge, risk ownership is often fragmented across IT, procurement, compliance, and clinical teams. This lack of coordination makes it difficult to get a clear picture of vendor risks. While nearly 80% of organizations have vendor risk programs, 30% of them lack dedicated staff to manage these risks, allowing vulnerabilities to go unnoticed until an incident occurs [2]. These hidden risks can lead to vendor-related incidents that directly jeopardize patient safety.
Patient Safety Impacts from Vendor Incidents
When vendor incidents occur, the consequences for patient care can be immediate and severe. For example, in December 2022, over 271,000 patients of Avem Health Partners had their medical data compromised after a breach at Avem's vendor, 365 Data Centers [2]. The ripple effects of such incidents are staggering - downstream entities impacted by multi-party breaches outnumber primary victims by more than 800% [2]. A single vendor breach can affect hundreds of healthcare organizations and millions of patients.
Beyond cyberattacks, vendor-related issues with Electronic Health Records (EHRs) can also harm patients. According to The Pew Charitable Trusts, "EHR usability - their layout, design, customizations, and how they fit into different workflows - can impact patient safety" [1]. Poor usability in EHR systems can lead to errors that directly affect patient outcomes.
Compliance-Focused vs. Patient-Safety-Focused Vendor Risk
The difference between a compliance-driven approach and one centered on patient safety is stark. Compliance programs primarily aim to avoid fines and penalties, while patient-safety-focused strategies assess how vendor risks affect patient outcomes. The financial stakes are immense - the average cost of a healthcare breach in the United States is $9.77 million [4]. But the human cost is even higher: 88% of healthcare organizations experienced cyberattacks in the past year, averaging 40 attacks per organization [4]. These breaches result in care delays, longer hospital stays, more complications, and even higher mortality rates [4].
| Feature | Regulatory-Driven | Patient-Centric |
|---|---|---|
| Visibility | Limited to regulatory requirements; relies on self-reported questionnaires and periodic audits. | Requires real-time insight into vendor security, operational risks, and impact on clinical workflows. |
| Speed | Reactive to regulatory changes; audit cycles are slow and infrequent. | Focuses on rapid identification, assessment, and mitigation of risks to prevent patient harm. |
| Clinical Impact | Aims to avoid fines and legal penalties; patient outcomes are an indirect concern. | Prioritizes preventing adverse events, care delays, complications, and mortality. |
The World Health Organization estimates that up to 80% of healthcare-related harm is preventable [3]. This highlights the urgent need for healthcare organizations to move beyond regulatory checklists and develop vendor risk programs that actively prevent harm. A patient-safety-focused approach is the only way to address these hidden and evolving threats effectively.
Gaps in Vendor Risk Management Programs
Program Gaps and Their Consequences
Healthcare organizations often struggle with significant weaknesses in how they track and monitor vendors. On average, a hospital works with over 1,300 vendors[6][7], yet many fail to maintain effective oversight of these relationships. Without proper tracking systems, organizations leave themselves vulnerable - not just to security threats but also to risks that directly impact patient safety.
Ongoing vendor monitoring is essential to catch and address emerging threats. In 2023, third-party vendors were linked to 74% of cybersecurity incidents or unauthorized access cases in healthcare[5]. These gaps in oversight lead to compliance issues and operational disruptions that can compromise the quality of care. For example, when systems go offline or supply chains are interrupted, patient safety is often at risk.
Another issue lies in the lack of enforceable cybersecurity standards within business associate agreements[6]. When breaches occur, this weak accountability leaves healthcare providers scrambling to respond. Additionally, many organizations fail to include vendors in their incident response plans or disaster recovery tests, making it difficult to coordinate during emergencies that affect patient care[6]. A culture that penalizes incident reporting further complicates the ability to address vulnerabilities, as it discourages timely and transparent communication about breaches[5].
Failure to Meet Regulatory Standards
These operational gaps also put organizations at odds with regulatory requirements. Many vendor risk management programs fail to meet the standards outlined by HIPAA, NIST, and HHS for managing third-party and supply chain risks. Alarmingly, healthcare organizations accounted for 41% of third-party breaches in 2024, more than any other industry[6]. This statistic highlights the failure of current practices to effectively mitigate vendor-related risks.
A common misconception is that HIPAA compliance alone is sufficient. However, patient safety risks extend beyond data privacy. Non-IT vendors - such as medical equipment suppliers, medication distributors, and health and safety system providers - play a critical role in care delivery[5][7]. When these vendors face disruptions, the ripple effect on patient care is immediate and severe. Yet, many risk management programs fail to address these operational dependencies, leaving patients exposed to preventable safety risks and organizations vulnerable to regulatory penalties.
Building a Patient-Safety-Focused Vendor Risk Framework
Steps for Managing Vendor Risk
For healthcare organizations, managing vendor risk isn't just about meeting compliance requirements - it’s about safeguarding patient safety. A robust framework starts with creating a detailed vendor inventory that outlines each vendor's specific role in supporting patient care.
It’s crucial to perform standardized assessments throughout the vendor lifecycle. This means evaluating vendors before signing contracts, periodically during their tenure, and when the partnership ends. These assessments should examine key areas like security credentials, history of breaches, data protection practices, and their potential impact on patient safety. Additionally, strong Business Associate Agreements (BAAs) are essential. These agreements should clearly spell out security requirements, breach notification protocols, and data-handling procedures for the end of the contract term [5][8].
Annual reviews are no longer enough. Continuous monitoring is now the gold standard, especially for high-risk vendors. Using certifications like HITRUST, SOC 2 Type 2, or ISO 27001 can provide real-time assurance of compliance [9]. Organizations should also adopt network segmentation to limit vendor access to only the necessary systems. To prepare for potential disruptions, regular testing of incident response and recovery plans - complete with simulations of vendor-related failures - ensures that clinical teams can continue delivering care without interruption.
Using Censinet RiskOps™ and Censinet AI
Managing thousands of vendor relationships can feel overwhelming, but Censinet RiskOps™ simplifies the process through automation. The platform allows vendors to complete security questionnaires in seconds instead of weeks. Meanwhile, Censinet AI steps in to summarize vendor evidence, document integration details, identify fourth-party risks, and generate risk summary reports from all relevant assessment data.
What sets this system apart is its human-in-the-loop approach. While automation handles the heavy lifting, experienced risk teams make the critical decisions. Advanced routing features act like "air traffic control", ensuring that important findings reach the right stakeholders, including members of the AI governance committee. A centralized dashboard ties it all together, offering a real-time, unified view of risks across all vendor relationships. This streamlined approach enables healthcare organizations to embed vendor risk management seamlessly into their daily clinical operations, keeping patient care and safety at the forefront.
sbb-itb-535baee
Integrating Vendor Risk into Healthcare Operations
Making Risk Management Part of Daily Operations
In healthcare, managing vendor risk shouldn't be an afterthought - it needs to be woven into everyday operations. One effective way to do this is by embedding vendor risk assessments directly into procurement workflows. This ensures that risk and security teams evaluate potential impacts on patient safety - like vendor access to clinical systems or risks of service delays - before contracts are signed.
Another key step is creating clear, collaborative incident response plans with vendors. These plans should outline protocols, escalation procedures, and recovery timelines. Regular simulations, such as ransomware attack drills or system outage scenarios, can help clinical teams practice maintaining care continuity under pressure. Aligning these efforts with broader disaster recovery strategies ensures that vendor-related risks are seamlessly incorporated into overall business continuity planning. This way, patient care can continue uninterrupted, even if a critical vendor faces disruption.
This integrated, proactive approach lays the groundwork for accurately measuring how vendor risks affect operations and, ultimately, patient safety.
Measuring Vendor Risk Impact on Patient Safety
To understand how vendor risks impact patient safety, healthcare organizations need to track the right metrics. A key indicator is system downtime - how many minutes or hours were clinical systems unavailable due to vendor issues? Another critical metric is remediation time, which measures how quickly identified security gaps are resolved after vendor assessments. Financial consequences tied to system downtime and remediation delays should also be monitored.
Other valuable metrics include vendor tier distribution, exposure to risks from fourth-party vendors, and trends in SLA breaches. Continuous monitoring and detailed recordkeeping are essential here. For example, nearly 90% of organizations report having at least one high-risk third-party relationship that could lead to a data breach, illustrating why ongoing visibility is so crucial [10][11]. Additionally, a survey revealed that 60% of organizations lack confidence in their vendors' full compliance with HIPAA. This highlights the need for compliance scorecards as a measurable way to track vendor performance [11].
By focusing on these metrics, healthcare organizations can better connect vendor risk to operational tools, enabling continuous risk management.
How Censinet Supports Daily Risk Management
Censinet RiskOps™ offers a centralized solution for managing vendor risks, keeping patient safety at the forefront. Its dashboard aggregates real-time data, acting like a command center for risk management. With advanced routing capabilities, critical findings and tasks are automatically sent to the right teams - whether it's procurement, clinical leadership, or even an AI governance committee. It’s like having air traffic control for vendor risk.
The platform also ensures continuous oversight by automating workflows that track remediation efforts and trigger reassessments when needed. Expert validation adds an extra layer of assurance to automated processes. By bringing together vendor risk data, task management, and stakeholder collaboration into one streamlined system, Censinet enables healthcare organizations to respond more quickly to threats while keeping patient safety at the heart of every decision.
Conclusion
Healthcare organizations must view vendor risk management as a responsibility tied directly to patient safety. In this industry, the stakes are far too high - lives depend on it. Protecting patients should always take precedence over simply satisfying regulatory requirements like HIPAA [12]. Cybersecurity and third-party risks are not just about compliance; they are integral to safeguarding care [5]. When vendors face breaches or disruptions, the consequences ripple directly to patient well-being.
This reality calls for a shift in mindset - from focusing solely on compliance to adopting proactive, patient-centered risk strategies. Traditional risk management approaches often fall short, leaving critical gaps unaddressed. A framework that prioritizes patient safety is the natural next step in healthcare cybersecurity. This approach demands real-time monitoring, automated processes, and scalable solutions to manage thousands of vendor relationships effectively. Enter Censinet. With its RiskOps™ platform powered by integrated AI, Censinet redefines the process, slashing assessment times and centralizing vendor data on a large scale [13][14].
Ed Gaudet, CEO and founder of Censinet, emphasizes this shift:
"Our collaboration with AWS enables us to deliver Censinet AI to streamline risk management while ensuring responsible, secure AI deployment and use. With Censinet RiskOps, we're enabling healthcare leaders to manage cyber risks at scale to ensure safe, uninterrupted care" [13].
By combining automation with human oversight, healthcare organizations can expand their operational capabilities without sacrificing control.
The way forward is straightforward. Healthcare providers must adopt centralized platforms that integrate real-time data, direct critical findings to the appropriate teams, and maintain continuous vendor risk oversight. When vendor risk management is aligned with patient safety, healthcare leaders can ensure uninterrupted, high-quality care delivery.
FAQs
What steps can healthcare organizations take to manage vendor risks and protect patient safety?
Healthcare organizations can strengthen their approach to vendor risk management by conducting thorough risk assessments before bringing vendors on board and continuously monitoring their security measures. Setting specific security requirements in contracts and developing strong incident response plans are key steps in this process.
Focusing on vendors based on the sensitivity of the data they manage and their involvement in critical operations is equally important. Keeping a clear view of all third-party relationships and working closely with vendors to ensure compliance and implement timely security updates can go a long way in reducing risks and safeguarding patient safety.
What’s the difference between compliance-focused and patient-safety-focused vendor risk strategies?
When it comes to vendor risk management, compliance-focused strategies aim to ensure that vendors align with key regulatory standards such as HIPAA, HITRUST, and SOC 2. These strategies prioritize thorough due diligence during the onboarding process and ongoing compliance checks to maintain adherence to legal and industry-specific requirements.
On the other hand, strategies centered on patient safety go beyond compliance. They actively assess risks that could directly impact the quality of patient care. This includes identifying potential issues like operational disruptions or cybersecurity threats that might jeopardize care delivery or endanger patient safety.
Why is it important to continuously monitor vendors to prevent cybersecurity risks in healthcare?
Continuous vendor monitoring plays a crucial role in helping healthcare organizations stay ahead of cybersecurity risks. It allows them to spot vulnerabilities, implement strict access controls, and identify unusual activity at every stage of the vendor relationship - whether during onboarding, active collaboration, or offboarding.
With real-time monitoring in place, healthcare organizations can act swiftly to address potential threats. This not only reduces the chances of data breaches and operational interruptions but also safeguards patient safety. Ultimately, it strengthens the healthcare system’s defenses, protects sensitive information, and helps maintain the trust of patients and stakeholders.


