How PHI De-Identification Prevents Data Breaches
Post Summary
De-identifying Protected Health Information (PHI) is one of the most effective ways to reduce the risks of data breaches in healthcare. By removing or modifying personal identifiers, organizations can safeguard sensitive data while still using it for research, analytics, and other purposes. Unlike identifiable PHI, de-identified data holds little value for attackers, minimizing its attractiveness as a target.
Key takeaways:
- What is PHI? PHI includes any health-related information linked to personal identifiers, such as names, birth dates, or Social Security numbers.
- Why are breaches increasing? The rise of telehealth, digital tools, and data sprawl has made PHI more vulnerable to cyberattacks.
- How does de-identification help? HIPAA-approved methods (Safe Harbor or Expert Determination) remove identifiable elements, turning PHI into low-risk data.
- Regulatory benefits: Properly de-identified data is exempt from HIPAA’s breach notification rules, reducing legal and financial liabilities.
- Common techniques: Suppression, generalization, pseudonymization, and hashing are some ways to de-identify data while preserving its usefulness.
Organizations should integrate de-identification into data workflows, vendor contracts, and risk management practices to protect patient privacy and reduce breach risks.
The Problem: Risks of Managing Identifiable PHI
PHI Spread Across Multiple Systems and Vendors
Identifiable PHI (Protected Health Information) flows through a maze of systems - ranging from EHRs and data warehouses to mobile apps and cloud services. This creates dozens, sometimes hundreds, of potential breach points [7]. For instance, staff often copy PHI into spreadsheets for quick analysis, move it into test environments for software development, or share full datasets with third-party analytics partners. Every duplicate increases the risk of a breach.
Then there’s the added challenge of third-party vendors. Billing companies, telehealth platforms, cloud service providers, and even medical device manufacturers all handle PHI. Alarmingly, many breaches now originate not from the healthcare providers themselves, but from these business associates [7][3].
Matt Christensen, Sr. Director GRC at Intermountain Health, emphasizes: "Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare" [1].
With over 50,000 vendors and products in use, ensuring consistent security measures - like access controls, encryption, and monitoring - across such a vast network is a monumental task [1][7]. This complexity not only makes securing PHI harder but also drives up financial and regulatory challenges.
Financial and Regulatory Costs of PHI Breaches
When PHI is compromised, the financial consequences can be staggering. HIPAA violations alone can cost anywhere from $100 to $50,000 per violation, with total penalties reaching into the millions [3][5]. But fines are just the beginning. Organizations must also cover forensic investigations, legal fees, breach notifications, and emergency security upgrades. Studies consistently show that healthcare breaches cost hundreds of dollars per compromised record. A breach involving hundreds of thousands of records can quickly snowball into a multi-million-dollar disaster.
HIPAA’s breach notification rules tie directly to the identifiability of the data. If unsecured, identifiable PHI is breached, organizations are required to notify affected individuals within 60 days of discovery [3][5]. For breaches involving 500 or more individuals in a single state, notifications must also go to prominent media outlets and the U.S. Department of Health and Human Services (HHS) immediately [3][5]. Even smaller breaches must be logged and reported to HHS annually.
Here’s the key: Data that’s properly de-identified and cannot reasonably be re-identified falls outside these breach notification requirements [3][5][8]. But if the data still qualifies as PHI, it’s subject to full regulatory obligations - making robust de-identification essential.
Dangers of Inadequate De-Identification
Some organizations mistakenly believe that stripping names and Social Security numbers is enough to safeguard patient privacy. It’s not. Details like ZIP codes, birth dates, gender, and specific medical information can still uniquely identify individuals when combined [2][4][5]. Research has shown that just three elements - date of birth, gender, and 5-digit ZIP code - can uniquely identify a significant portion of U.S. residents [2][4][5]. Attackers often link such datasets with public records, voter rolls, social media, or commercial data sources to re-identify individuals, even when obvious identifiers are removed.
Ad hoc methods that fall short of HIPAA’s Safe Harbor or Expert Determination standards leave the data classified as PHI, requiring the same rigorous safeguards [6][3]. If a breach occurs and regulators determine the data still qualifies as PHI, the organization faces full HIPAA obligations and potential penalties. Even pseudonymized or tokenized datasets - if reversible using a key or token vault - are still considered PHI under HIPAA, carrying the same breach notification and security requirements as raw identifiers [6].
The Solution: HIPAA-Compliant De-Identification Methods
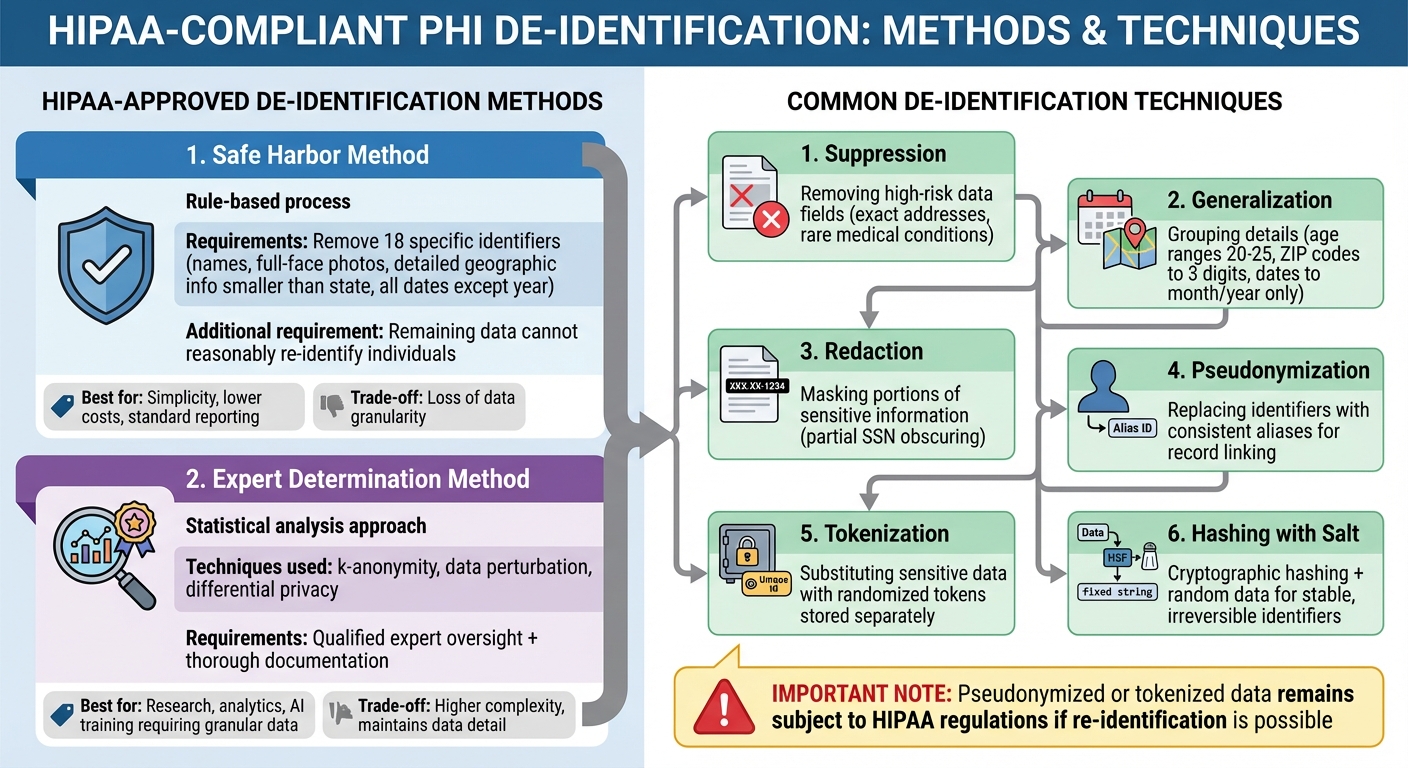
HIPAA-Compliant PHI De-Identification Methods and Techniques
Using HIPAA-compliant de-identification methods not only safeguards patient privacy but also plays a key role in minimizing the risk of data breaches.
HIPAA Safe Harbor and Expert Determination
The HIPAA Privacy Rule provides two official approaches for de-identifying Protected Health Information (PHI): Safe Harbor and Expert Determination. While both methods ensure that PHI is no longer subject to the Privacy Rule, they take different approaches to achieve this.
Safe Harbor is a rule-based process. It requires removing 18 specific identifiers, such as names, full-face photos, detailed geographic information (smaller than a state), and all date elements except the year. Additionally, it mandates that the remaining data cannot reasonably be used to re-identify an individual. This approach is relatively straightforward and often relies on checklists or automated tools. However, the trade-off is a loss of data granularity.
Expert Determination, on the other hand, uses advanced statistical techniques like k-anonymity, data perturbation, or differential privacy to minimize re-identification risks while maintaining more detailed data. This method requires oversight from a qualified expert, along with thorough documentation to validate compliance.
The choice between these methods depends on your organization's goals. Safe Harbor is ideal for situations where simplicity and lower costs are priorities, even if it means sacrificing some data detail. Expert Determination, however, is better suited for scenarios where retaining granular data is essential, such as for research, analytics, or training AI models.
Building on these foundational methods, organizations can apply specific techniques to customize de-identification for their needs.
Common De-Identification Techniques
Both Safe Harbor and Expert Determination rely on practical techniques to strike a balance between privacy and data usability:
- Suppression: Removing high-risk data fields, such as exact addresses or rare medical conditions in small populations.
- Generalization: Simplifying data by grouping details - for example, age ranges (e.g., 20–25), truncating ZIP codes to three digits, or recording only the month and year for dates.
- Redaction: Masking portions of sensitive information, such as partially obscuring Social Security numbers or other identifiers.
- Pseudonymization: Replacing direct identifiers with consistent aliases, allowing records to be linked over time without revealing actual identities. Securely managing the alias-to-identifier mapping is critical.
- Tokenization: Substituting sensitive data with randomized tokens stored separately in a secure system, ensuring referential integrity while protecting raw data.
- Hashing with Salt: Using cryptographic hashing and a salt (random data added to the hash process) to create stable, irreversible identifiers. This enables longitudinal analysis without exposing original data.
For more advanced needs, methods like differential privacy can be used. By adding controlled noise to datasets or generating synthetic data, these methods further reduce re-identification risks while preserving analytical value. However, keep in mind that pseudonymized or tokenized data remains subject to HIPAA regulations if re-identification is possible.
To effectively use these techniques, they need to be embedded into your organization's risk management workflows.
Adding De-Identification to Risk Management Workflows
Incorporating de-identification into your data processes begins with identifying datasets containing PHI and integrating Safe Harbor or Expert Determination into all data extraction workflows.
Make de-identification a standard part of change management. Before launching new projects, conduct a review to identify PHI and ensure proper de-identification measures are applied. When working with third-party vendors, establish clear protocols for data handling. Specify whether they will receive de-identified, limited, or full PHI, and include contractual clauses prohibiting re-identification or linking the data to external sources.
Additionally, include de-identification controls in your risk registers and control libraries alongside measures like encryption and access restrictions. Regularly auditing sample datasets helps verify that identifiers are correctly removed or transformed, ensuring compliance and reducing the chance of data breaches.
sbb-itb-535baee
Implementing PHI De-Identification in Healthcare Organizations
After understanding the de-identification methods, healthcare organizations must take the next step: integrating these practices into their workflows and external partnerships. This requires structured programs with clear policies, governance frameworks, and reliable technical controls.
Creating a De-Identification Program
To start, form a cross-functional governance team that includes privacy officers, compliance staff, IT security experts, clinical leaders, and researchers. This group will oversee de-identification policies, address high-risk situations, and approve exceptions when necessary. Develop a detailed policy document that outlines when PHI needs to be de-identified - such as for analytics, research, vendor collaboration, or quality improvement - and specify which HIPAA-compliant methods (Safe Harbor or Expert Determination) are permitted. Clarify who has the authority to grant exceptions.
Next, conduct a thorough PHI discovery across the organization using automated tools. Maintain updated data flow diagrams to track where PHI is transformed or shared. Standardize de-identification methods for structured data (e.g., masking, suppression, generalization, hashing, tokenization) and unstructured data (e.g., NLP-driven redaction). Automate these processes to ensure PHI is de-identified before leaving clinical systems.
Training is key. Educate clinicians, analysts, IT teams, and researchers on the approved tools and procedures. Regular training sessions and clear documentation will help ensure everyone understands that pseudonymized or tokenized data may still qualify as PHI under certain circumstances.
Once internal controls are established, extend these practices to your external collaborations.
Managing Vendor and Third-Party Risks
Managing external risks is just as important as internal controls. Whenever possible, de-identify PHI before sharing it with external parties. This reduces the risk of breaches, minimizes regulatory complications, and simplifies Business Associate Agreements (BAAs). For cases where identifiable PHI must be shared, classify vendors based on the data they handle (e.g., full PHI, limited datasets, or de-identified data) and tailor contract requirements accordingly.
Data use agreements should explicitly prohibit re-identification or external linking of de-identified data. Include provisions for strong access controls, audit logging, and breach reporting timelines. Contracts should also address sub-processor restrictions, data residency, retention periods, and deletion protocols. Require vendors to report any suspected identity disclosures and collaborate on remediation efforts.
To ensure compliance, use standardized security questionnaires and conduct evidence-based reviews. Regularly assess vendors to confirm they consistently meet security standards for both PHI and de-identified data.
Using Censinet for Risk Management

Censinet RiskOps™ simplifies the integration of de-identification into enterprise risk management. Through automated assessments, centralized dashboards, and collaborative workflows, the platform helps healthcare organizations manage risks tied to patient data, medical records, and third-party vendors in one place.
Tower Health's CISO Terry Grogan shared: "Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required."
Baptist Health's VP & CISO James Case added: "Not only did we get rid of spreadsheets, but we have that larger community [of hospitals] to partner and work with."
Censinet's collaborative risk network connects healthcare providers with over 50,000 vendors, enabling secure and efficient sharing of cybersecurity and risk data. Organizations can include de-identification controls in their risk registers alongside other safeguards like encryption and access restrictions. The platform also tracks metrics, such as the percentage of external data shares using de-identified data versus PHI.
For third-party risk assessments, Censinet AITM speeds up the process by allowing vendors to quickly complete security questionnaires. It automatically summarizes evidence, generates risk reports, and directs key findings to the appropriate stakeholders. Acting like "air traffic control" for governance and risk management, the platform keeps everything organized and efficient.
Conclusion: How De-Identification Reduces Breach Risk
Key Takeaways
De-identification, when done using HIPAA-approved methods, transforms how organizations protect data. By removing identifiable PHI, it eliminates the need for breach notifications and significantly lowers regulatory, legal, and financial risks. It also minimizes the attack surface, as vast amounts of sensitive information are no longer vulnerable. Even in the event of a system breach, the data exposed is not easily tied back to individual patients, reducing risks like identity theft, extortion, and reputational harm.
Beyond security, de-identification offers operational advantages. It enables organizations to use data for research, quality improvement, AI training, and partnerships without the heavy compliance burden tied to PHI. This allows for quicker advancements and innovation.
Each method has its strengths: Safe Harbor works well for routine data sharing and standard reporting, while Expert Determination supports more complex needs, like analytics or research, where richer datasets are required but with minimal re-identification risk. However, de-identification isn’t a one-and-done solution - it’s an ongoing process that must adapt as new data linkage methods and external data sources emerge.
Next Steps for Healthcare Leaders
To fully realize the benefits of de-identification, healthcare leaders need to embed these practices into all aspects of their data management strategies. Start by conducting a thorough audit to map where PHI flows within your systems. Look for opportunities to substitute identifiable data with de-identified data, especially in areas like test environments, training datasets, and external collaborations. Form a cross-functional governance team to oversee de-identification practices, approve any necessary exceptions, and ensure compliance with HIPAA standards.
Review and tighten vendor contracts to include specific clauses that prohibit re-identification, restrict data use, and require audits. Consider tools like Censinet RiskOps™ to streamline risk management efforts. This platform helps enforce de-identification protocols and offers a secure way to share cybersecurity and risk data while maintaining oversight of patient data protection across your network.
Track your progress with measurable goals. For instance, monitor the percentage of external data shares using de-identified data instead of PHI, identify how many systems have transitioned away from PHI, and measure the time it takes to complete vendor risk assessments. Regularly evaluate and refine your de-identification processes to ensure they remain effective in safeguarding your data and reducing breach risks.
FAQs
What’s the difference between the Safe Harbor and Expert Determination methods for de-identifying PHI?
The Safe Harbor method focuses on removing or masking specific identifiers - like names or Social Security numbers - to comply with strict guidelines aimed at minimizing the risk of re-identifying individuals. It’s a straightforward process that follows a standardized checklist, making it relatively simple to implement.
In contrast, Expert Determination involves a qualified expert analyzing and adjusting the data based on its context and intended use. This approach provides a more tailored solution, balancing the need to reduce re-identification risks while maintaining the data’s usefulness for specific purposes.
While both methods are effective, they differ in their approach. Safe Harbor is more rigid and standardized, whereas Expert Determination offers greater flexibility and precision, particularly for more complex datasets.
How can healthcare organizations protect de-identified data from being re-identified?
Healthcare organizations can protect de-identified data by implementing techniques such as data masking, differential privacy, and encryption. These approaches help obscure sensitive details while keeping the data functional for analysis and other purposes.
To minimize the chances of re-identification, it's crucial to enforce strict access controls, perform regular risk assessments, and maintain ongoing monitoring to identify potential vulnerabilities. Following established privacy standards and using tools tailored for cybersecurity and risk management adds extra security layers, ensuring patient data remains well-protected.
How can healthcare organizations integrate PHI de-identification into their data management processes?
Healthcare organizations can weave PHI de-identification seamlessly into their operations by focusing on a few practical steps:
- Pinpoint vulnerabilities: Start by thoroughly assessing where sensitive data exists and identifying weak points that could lead to exposure.
- Leverage automation: Rely on advanced tools to anonymize data quickly and consistently, minimizing the chance of human error.
- Integrate throughout processes: Make de-identification a core part of every stage of data handling - whether during collection, storage, or sharing.
- Educate your team: Equip staff with the knowledge of privacy regulations and best practices to ensure compliance and protect sensitive information.
- Stay proactive: Regularly review and adjust de-identification methods to keep up with changing threats and regulatory requirements.
By embedding these strategies into their workflows, healthcare organizations can better safeguard patient information and remain aligned with privacy standards.


