Questions to Ask Vendors During Risk Assessments
Post Summary
Healthcare organizations rely on vendors for critical services like electronic health records (EHR), medical devices, and cloud hosting. But these partnerships come with risks - data breaches, compliance failures, and operational disruptions. To protect patient safety and organizational stability, vendor risk assessments are essential.
Here’s what you should focus on when evaluating vendors:
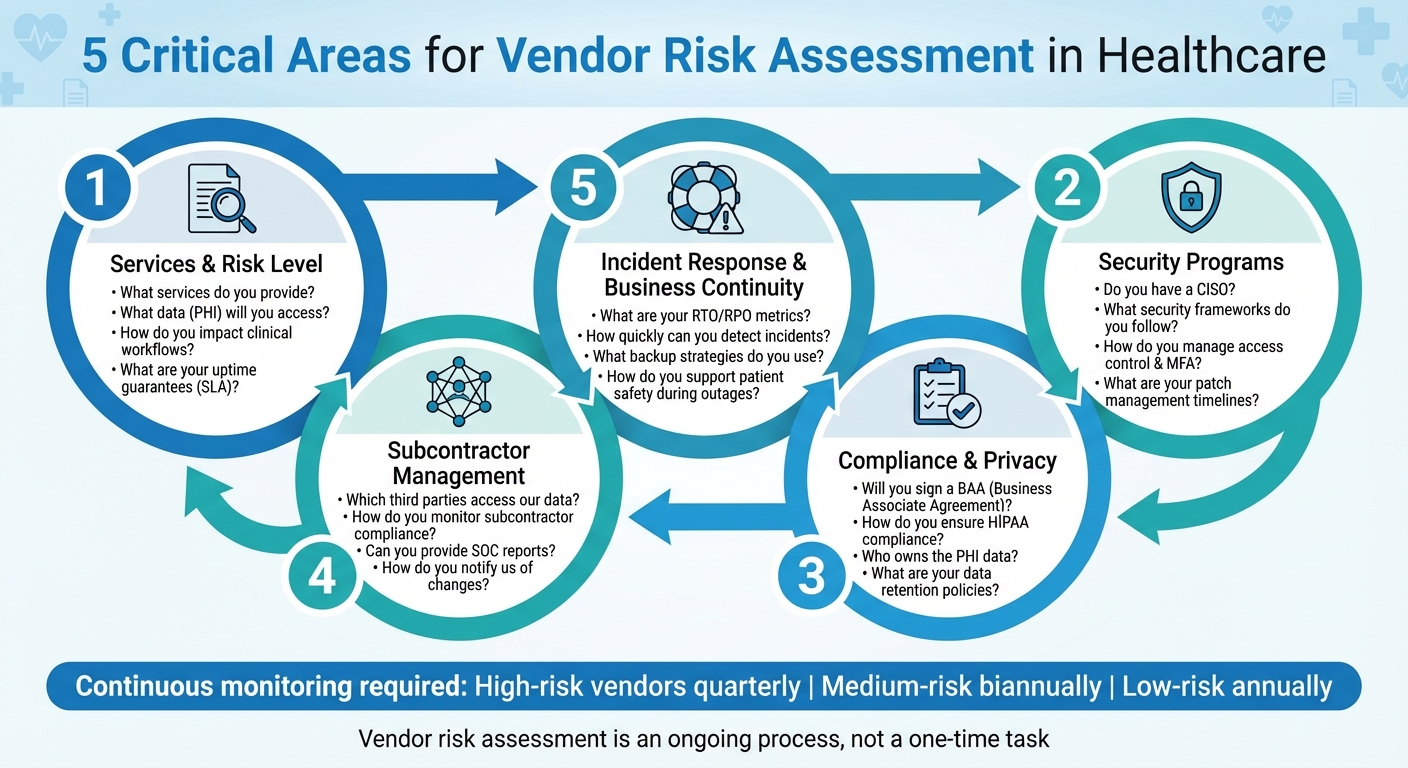
- Understand Services and Risks: Clarify what services vendors provide, their access to sensitive data, and how they impact clinical workflows. For example, ask about data encryption, uptime guarantees, and recovery plans.
- Evaluate Security: Review their security policies, leadership, access controls, and vulnerability management. Questions about encryption methods, patching timelines, and penetration testing are key.
- Check Compliance: Confirm HIPAA compliance, data ownership policies, and subcontractor management. Ensure they’ll sign a Business Associate Agreement (BAA) and meet regulatory standards.
- Assess Incident Response: Examine their plans for detecting and responding to incidents. Ask about breach notifications, disaster recovery objectives, and how they support patient safety during outages.
- Monitor Subcontractors: Vendors often rely on third parties. Verify their oversight processes and request documentation like SOC reports.
Vendor risk management isn’t a one-time task. Use tools like Censinet RiskOps™ to streamline assessments and monitor risks continuously. By asking the right questions, you reduce vulnerabilities and ensure uninterrupted patient care.
5 Key Areas for Healthcare Vendor Risk Assessment
Questions About the Vendor's Services and Risk Level
Before diving into technical controls and compliance measures, it’s important to first understand the vendor’s services, their access to data, and how they might impact your operations. These initial questions set the stage for how thorough and detailed your assessment needs to be. For example, evaluating a vendor handling marketing services is a completely different ballgame compared to assessing one managing your EHR system or medical device data. Below, we outline key questions to help you identify service types and assess their operational impact.
Questions to Identify Services and Data Access
Start by clarifying the vendor’s service category and whether they fall under HIPAA’s classification. A good opening question is: “What specific services do you provide, and how do they interact with our clinical or operational systems?” This helps determine if the vendor qualifies as a HIPAA business associate, which comes with specific contractual and security requirements. Don’t rely on the vendor’s self-classification - verify it yourself.
Next, dig into data flows. Ask: “What types of data, including PHI or other sensitive information, will you access, store, or process as part of your services?” Follow up with: “How and where do you store and transmit healthcare data? Can you provide details about encryption methods and data segregation practices?” For instance, a billing vendor might initially claim they only handle payment data. However, further questioning could reveal they also access patient names, birth dates, and diagnosis codes. Whether data is encrypted both at rest and in transit, and whether it’s segregated from other customers’ data, plays a major role in determining your risk exposure.
Questions to Determine Clinical and Operational Impact
Understanding the clinical and operational impact of a vendor’s potential failure is critical. Ask: “How do your systems and services affect our clinical operations or patient care workflows in the event of downtime or disruptions?” Another essential question is: “What level of uptime do you guarantee (e.g., a 99.9% SLA), and what are your Recovery Time Objective (RTO) and Recovery Point Objective (RPO) for our environment?” For context, a 99.9% uptime SLA allows for over 8 hours of downtime annually - something that may be unacceptable for critical clinical systems.
Beyond uptime, it’s also important to ask about contingency plans. For example: “What manual procedures are in place to mitigate the impact of system downtime?” Lastly, identify any hidden dependencies by asking: “Which third or fourth parties do you rely on (e.g., hosting providers, subcontractors, call centers), and do any of these parties have access to our data?” A vendor’s security is only as strong as the weakest link in their chain of dependencies.
Leveraging tools like Censinet RiskOps™ can simplify and streamline this evaluation process.
Questions About Security Programs and Technical Controls
Once you've evaluated a vendor's services and how they impact your operations, it's time to dig into their technical defenses. This means asking pointed questions about their security governance, access controls, and vulnerability management to gauge the strength of their safeguards.
Questions About Security Leadership and Policies
Start with leadership: "Do you have a Chief Information Security Officer (CISO) or an equivalent security leader, and what are their responsibilities?" A lack of a dedicated security leader could be a warning sign. Follow up with: "What security policies and governance frameworks do you have in place to protect sensitive healthcare data, including PHI?" This will help you determine whether the vendor aligns with established standards.
Another critical question: "How often are your security policies reviewed and updated, and who oversees these reviews?" Outdated policies can indicate a lack of attention to security. Additionally, ask: "Can you provide documentation of your security program and recent audit reports?" If they hesitate or refuse, it could signal underlying problems.
From there, shift your focus to how they control access and use encryption to protect your data.
Questions About Access Control and Encryption
Ask: "How do you manage access control to ensure that only authorized personnel can access critical systems and data? Do you use multi-factor authentication (MFA)?" It's also important to know: "What is your process for provisioning and deprovisioning user access, especially when employees leave or change roles?" Poorly managed access can leave systems vulnerable.
When it comes to encryption, get specific. For data in transit, ask about protocols like TLS 1.2 or 1.3. Then dig deeper with: "How are encryption keys generated, stored (e.g., in HSMs or secure key vaults), rotated, and who has access to them?" Storing encryption keys alongside encrypted data can render the encryption ineffective.
Questions About Vulnerability and Patch Management
Ask about their approach to vulnerabilities: "Can you describe your vulnerability management processes, including how often scans are conducted, patching timelines, and your response to zero-day threats?" You should also ask: "What is your Service Level Agreement (SLA) for applying critical security patches, and can you share examples from recent patch cycles?"
To validate their processes, inquire about penetration testing. "Are these tests conducted by independent third parties? How often do they occur, and can we review the findings?" Finally, ask: "What tools and processes do you use to track and address identified vulnerabilities?" These answers will give you insight into how proactive and thorough their security measures really are.
Questions About Compliance, Privacy, and Contracts
After reviewing a vendor's technical controls, the next step is to confirm that they align with healthcare's strict regulatory and contractual requirements. This involves asking clear, targeted questions about HIPAA compliance, data ownership, and how they handle subcontractors who may access patient information.
Questions About HIPAA and Regulatory Requirements
Start with the essentials: "Do you qualify as a Business Associate under HIPAA, and will you sign our Business Associate Agreement (BAA)?" Vendors handling PHI (Protected Health Information) must sign a BAA, which outlines their responsibilities, including permitted uses, security measures, reporting obligations, and conditions for contract termination. Follow up with: "How do you ensure compliance with the HIPAA Security Rule? Specifically, describe your approach to access control, audit controls, integrity controls, transmission security, and workforce training."
Dive deeper into their risk management practices by asking: "Do you conduct formal risk analyses on systems that store or process PHI? How frequently? Can you provide a summary of findings and remediation efforts?" This helps gauge their commitment to identifying and addressing vulnerabilities. Another critical question is: "Have you ever experienced HIPAA violations or been part of an OCR (Office for Civil Rights) investigation? If so, what were the causes, and what corrective actions did you implement?"
Once regulatory compliance is addressed, shift the focus to data ownership and retention policies.
Questions About Data Ownership and Retention
Understanding who owns PHI is crucial. Ask: "Who owns the PHI and any derived data? Can you confirm that our organization retains ownership, with your role limited to acting as a custodian?" Then, clarify how they handle secondary uses of data: "Do you use our data - including de-identified or aggregated data - for purposes beyond the contracted services, such as analytics, AI training, or product development?" If they do, request details about their de-identification process and whether they adhere to HIPAA standards like Safe Harbor or expert determination.
Retention policies are another key area. Ask: "What are your standard retention periods for PHI, logs, backups, and metadata? Can these be customized to meet contractual or regulatory requirements?" Additionally, inquire about their approach to supporting audits: "How long do you retain system and security logs to facilitate investigations and compliance reviews?" At the end of the contract, ensure clarity with: "What formats can data be exported in (e.g., CSV, HL7, FHIR, DICOM), and are there fees for bulk exports? Does any data remain in logs, analytics platforms, or third-party systems after termination?"
Finally, ensure subcontractor management is thoroughly addressed to minimize risks.
Questions About Subcontractors and Fourth-Party Risk
Begin by asking for transparency: "Can you provide a list of all subcontractors or hosting providers who will access or store our PHI, along with their locations?" Then, confirm how they handle changes: "How will you notify us about material updates involving subcontractors, such as the addition of a new hosting provider?" To assess third-party security, ask: "Can you share assessment artifacts for key subcontractors, such as security questionnaires or SOC reports, under an NDA?"
Lastly, evaluate their ongoing oversight: "How do you monitor subcontractor compliance with security and privacy standards? What actions do you take if a subcontractor fails to meet these standards?" These questions provide insight into how the vendor actively manages potential risks from subcontractors and fourth parties.
Using a comprehensive risk management platform like Censinet RiskOps™ can simplify the process of gathering and analyzing these critical compliance, privacy, and contractual details. This ensures a streamlined and transparent approach to vendor risk management.
sbb-itb-535baee
Questions About Incident Response and Business Continuity
After completing technical and compliance reviews, it's essential to evaluate how well a vendor can handle disruptions through their incident and disaster management processes. Even the most secure vendors can experience incidents. The key to minimizing impact lies in rapid detection, effective response, and ensuring business continuity to protect patient care.
Questions About Incident Detection and Response
"Do you have a documented incident response plan, and when was it last reviewed and tested?" A solid incident response plan should be regularly updated and tested to ensure it's effective. "Which tools (SIEM, IDS/IPS, EDR, log monitoring) do you use, and how quickly can you detect and contain incidents?" Knowing their detection tools and response times can help you understand how long your data might be at risk during an incident.
"Who is responsible for incident response within your organization (titles, teams), and how are incidents escalated to our organization, including after-hours contacts?" Clear escalation procedures and points of contact are critical for timely communication. "Describe a significant incident in the last 24 months that impacted availability, confidentiality, or integrity of customer data. What was the root cause, and what corrective actions were taken?" This question gives insight into the vendor’s transparency and ability to learn from past events. Repeated incidents with similar causes may indicate weak controls. "How do you notify customers of security incidents and breaches? What timelines do you follow to meet HIPAA's 60-day breach notification requirement?"
Questions About Disaster Recovery and Backup Plans
"What are your RTO (Recovery Time Objective) and RPO (Recovery Point Objective), and how do they align with our clinical uptime needs and SLAs?" These metrics are vital for understanding how quickly services can be restored and how much data might be lost. "How often do you back up our data, where are backups stored (geographic region, cloud/on-premises), and are they encrypted?"
"What backup strategy do you use (e.g., immutable storage, offline copies, geographically diverse replicas)?" This is particularly important for ransomware protection, as attackers often target backups. "Can you provide examples of successful restores after ransomware attacks or accidental deletions, including the time it took to restore core functions and any data loss?" "Do you have redundant data centers or availability zones, and what is your failover strategy in case of a data center or cloud region failure?"
"How often do you test your Business Continuity/Disaster Recovery (BC/DR) plans, what types of tests do you conduct, and what corrective actions were implemented after the last test?" Vendors who regularly test their plans and improve based on findings demonstrate operational readiness.
Questions About Patient Safety During Outages
Ensuring patient safety during system outages is just as important as restoring technical functionality. Downtime impacts clinical workflows, so effective communication and preparation are essential. "How will you communicate planned and unplanned downtime, including expected duration and impact on clinical workflows?" Accurate, timely updates allow clinical teams to implement downtime procedures and manage patient risks effectively. "What degraded or read-only modes, offline access options, or manual fallback processes do you offer so clinicians can continue providing safe care during outages?"
"How do you coordinate with our clinical engineering, IT, and patient safety teams during extended outages or cyber incidents to prioritize restoring life-critical services?" "Do you support integration with our downtime procedures, such as printing downtime reports, offline medication administration records, or order entry workarounds?" These questions ensure vendors are prepared to support clinical operations even under challenging circumstances.
Platforms like Censinet RiskOps™ enable healthcare organizations to systematically evaluate vendor incident response and business continuity capabilities. They ensure that critical questions are addressed, documented, and monitored throughout the vendor lifecycle.
Conclusion
Carrying out comprehensive vendor risk assessments means asking the right questions in five key areas: understanding the vendor's services and associated risks, evaluating their security programs and technical safeguards, verifying compliance and contractual protections, examining subcontractor relationships, and ensuring their incident response and business continuity plans are solid. Each of these areas is vital for safeguarding PHI (Protected Health Information) and staying compliant with HIPAA's 60-day breach notification rule.
Relying on spreadsheets to manage risks across thousands of vendors, devices, and supply chain partners just doesn’t cut it anymore. Healthcare organizations that adopt specialized platforms for vendor risk assessments see noticeable improvements in efficiency. For example, Terry Grogan, CISO at Tower Health, shared: "Censinet RiskOps allowed us to perform more risk assessments with one less FTE." Similarly, James Case, VP & CISO at Baptist Health, remarked: "Not only did we get rid of spreadsheets, but we have that larger community [of hospitals] to partner and work with."
Vendor risk assessment isn’t a one-and-done task - it’s a continuous process. High-risk vendors should be reviewed quarterly, medium-risk vendors biannually, and even low-risk vendors should undergo annual automated scans. Additionally, risks from subcontractors (fourth-party risks) need ongoing monitoring. Platforms like Censinet RiskOps™ enable this continuous monitoring through a collaborative network of healthcare organizations and over 50,000 vendors, offering automated, ongoing risk assessments. This approach ensures that proactive measures stay in place, strengthening the organization's overall risk management strategy.
FAQs
What should I ask a vendor about their data encryption practices?
When reviewing a vendor's data encryption practices, it's important to ask the right questions to ensure they meet security and compliance standards. Here are some key points to address:
- What encryption algorithms are used to secure both stored data and data in transit?
- How are encryption keys managed and safeguarded to prevent unauthorized access?
- Are the encryption methods aligned with healthcare regulations like HIPAA?
- How frequently are encryption protocols evaluated and updated to counter new threats?
- Is end-to-end encryption provided for all patient data, including data shared with third parties?
These questions can help you assess whether the vendor's encryption measures are robust enough to protect sensitive healthcare information effectively.
What steps can healthcare organizations take to confirm a vendor complies with HIPAA regulations?
Healthcare organizations can ensure a vendor complies with HIPAA by following a few critical steps:
- Review the vendor’s documented policies and procedures to confirm they meet HIPAA standards.
- Perform a detailed risk assessment to evaluate the vendor’s security measures and uncover any potential weaknesses.
- Examine the vendor’s security controls to ensure they effectively protect sensitive data, including patient information and PHI.
- Secure a signed Business Associate Agreement (BAA) to legally define the vendor’s obligations in safeguarding protected health information.
Tools like Censinet RiskOps™ can simplify the risk assessment process and provide continuous monitoring of vendor compliance, helping your organization uphold strict security and regulatory standards.
Why is it important to continuously monitor vendor risks in healthcare?
Continuous monitoring of vendor risks plays a crucial role in healthcare, ensuring that new threats or vulnerabilities are identified and addressed promptly. This vigilant approach helps protect sensitive patient information, such as PHI, while keeping organizations aligned with regulatory standards.
By keeping a close eye on vendor activities in real time, healthcare providers can minimize the chances of data breaches, safeguard their operations, and respond quickly to shifting risks. Tools powered by AI make this process more efficient, allowing organizations to manage risks effectively without losing focus on what matters most - delivering quality patient care.


