Why Session Monitoring Matters for HIPAA Compliance
Post Summary
Session monitoring is a critical component for meeting HIPAA compliance, ensuring patient data remains secure in healthcare systems. It tracks user activity, detects suspicious behavior, and provides detailed logs for audits. Without it, healthcare organizations risk data breaches, compliance failures, and hefty fines. Here's why it matters:
- Tracks Activity: Monitors who accessed systems, what actions they performed, and when.
- Prevents Data Breaches: Identifies unusual behavior like after-hours access or large data downloads.
- Supports HIPAA Requirements: Meets standards for audit controls, authentication, and secure transmissions.
- Addresses Risks: Mitigates issues with shared devices, remote access, and fragmented logs across platforms.
- Improves Response: Enables faster breach investigations and compliance proof during audits.
Healthcare organizations must implement detailed logging, automatic logoffs, and real-time alerts to safeguard electronic protected health information (ePHI). Centralized tools, like Censinet RiskOps™, simplify this process by unifying logs and enhancing visibility across systems.
What Session Monitoring Means for HIPAA Compliance
HIPAA Security Rule Safeguards and Session Monitoring Requirements
Session Monitoring Defined
Session monitoring involves tracking user activity from the moment they log in to when they log out within systems handling electronic protected health information (ePHI). This process captures every action, access, and change, all tied to a unique session ID [1][2].
Unlike standard access logs that only record logins and logouts, session monitoring provides a detailed view of user behavior. It tracks activities like idle periods, switching between applications, after-hours access, downloading data, copying and pasting information, and making configuration changes - all in a chronological sequence [1][2]. For example, it can identify when a nurse accesses patient records late at night from an unusual location [1][2][3].
This level of detail plays a crucial role in meeting HIPAA compliance standards.
HIPAA Security Requirements That Apply to Session Monitoring
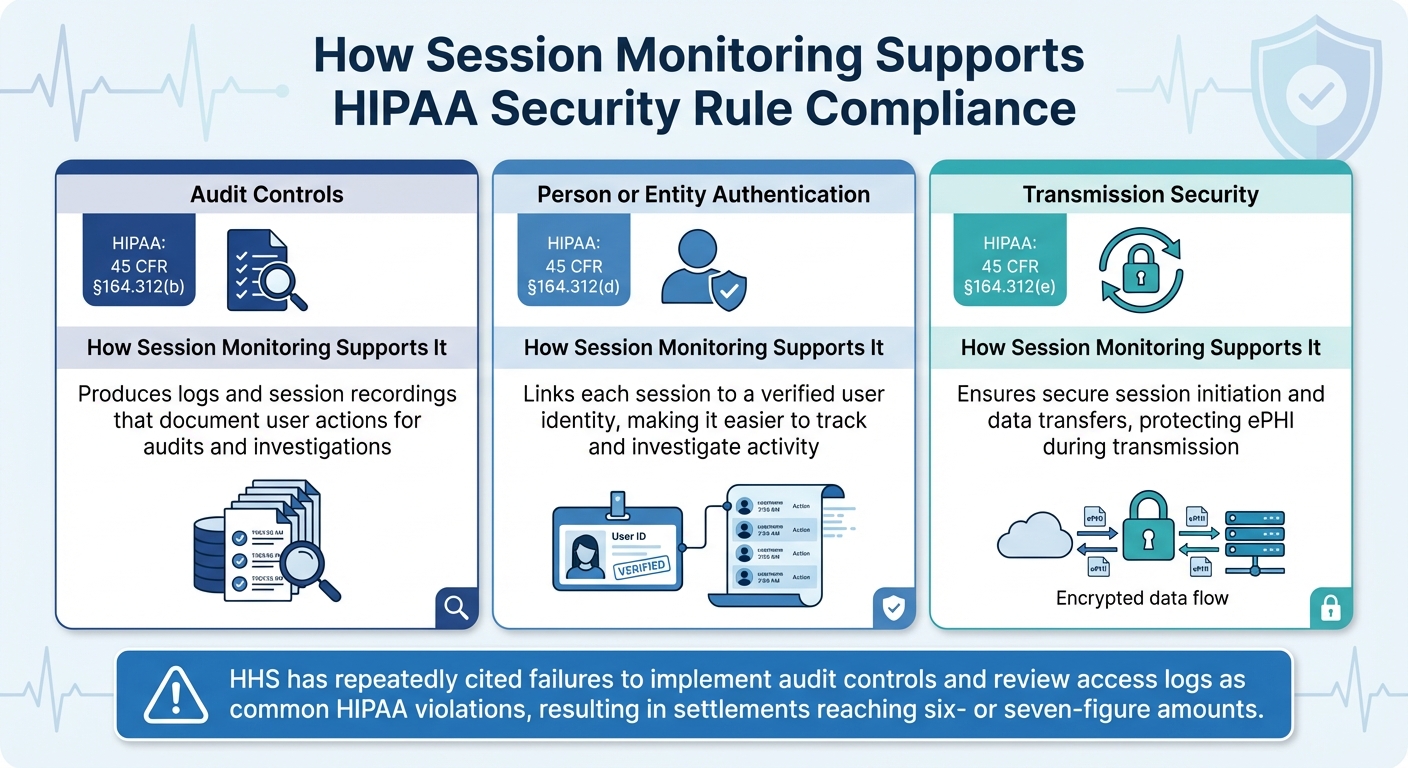
Session monitoring aligns with several key HIPAA Security Rule safeguards by creating a reliable record of user activities. These safeguards are essential for covered entities to maintain compliance [4]:
| HIPAA Safeguard | Citation | How Session Monitoring Supports It |
|---|---|---|
| Audit Controls | 45 CFR §164.312(b) | Produces logs and session recordings that document user actions for audits and investigations. |
| Person or Entity Authentication | 45 CFR §164.312(d) | Links each session to a verified user identity, making it easier to track and investigate activity. |
| Transmission Security | 45 CFR §164.312(e) | Ensures secure session initiation and data transfers, protecting ePHI during transmission. |
The Department of Health and Human Services (HHS) has repeatedly cited failures to implement audit controls and review access logs as common HIPAA violations. These lapses have resulted in multiple settlements, often reaching six- or seven-figure amounts, underscoring the importance of robust session monitoring on systems containing ePHI [4].
Where Healthcare Organizations Fall Short on Session Monitoring
Even though HIPAA clearly outlines the need for effective session monitoring, many healthcare organizations still struggle to implement basic practices. These gaps not only expose them to compliance risks but also make it harder to detect or investigate potential breaches. This lack of oversight weakens their ability to manage risks effectively.
Shared Workstations and Unattended Sessions
In busy healthcare settings, clinicians often leave electronic health record (EHR) sessions open on shared devices. This creates opportunities for unauthorized individuals - whether staff, patients, or visitors - to access protected health information (PHI). Such incidents may lead to reportable privacy violations [1].
The problem worsens when shared credentials are used. With everyone logging in under the same account, it becomes nearly impossible for security teams to identify who accessed specific records. Shared accounts render audit logs useless for attributing actions to individual users, making breach investigations much harder. HIPAA requires organizations to track who accessed what information, when, and why - something that’s unachievable without strong session controls [1][4].
Poor Visibility into Remote and Vendor Access
Session monitoring challenges aren’t limited to on-site activities. Remote employees and third-party vendors accessing EHR systems, medical devices, or telehealth platforms often do so without adequate oversight. Many organizations only log basic actions like login attempts, failing to track what users actually do during their sessions [2][3].
Vendors supporting systems such as revenue cycle management, imaging platforms, or clinical applications often have their activity logged separately. This fragmented approach makes it difficult to piece together what happened during support sessions. Without a unified view, unauthorized actions can go unnoticed, and organizations may struggle to prove they’ve managed business associate access responsibly [2][3][4].
Fragmented Logs Across Multiple Cloud Systems
To make matters worse, many healthcare providers operate across a patchwork of cloud systems - EHRs, telehealth apps, patient portals, medical device clouds, and more. Each system typically has its own logging format, retention policy, and access method [3][5][1]. This siloed approach creates significant challenges for security teams trying to track a user’s activity across platforms.
Inconsistent user IDs, mismatched timestamps, and varying log retention policies further complicate the process. Some systems even limit the ability to export logs, making it difficult to centralize data. Without a unified, HIPAA-compliant log management system, even large organizations can face delays of days or weeks when investigating breaches. This lack of efficiency undermines their ability to meet the Office for Civil Rights’ expectations for timely responses [3][4].
What Session Monitoring Must Do to Meet HIPAA Standards
HIPAA regulations demand that session monitoring captures detailed activity and detects suspicious behavior in real time. According to HIPAA, covered entities must implement audit controls to "record and examine activity in information systems that contain or use ePHI" [6][7]. These requirements are essential for building a session management framework that aligns with HIPAA's rigorous standards.
Complete Logging and Data Correlation
Effective session monitoring involves logging every detail of user, application, system, and network activity across systems handling ePHI [6][3]. Each log should include critical details such as user ID, role, patient records accessed, actions taken (view, edit, export), system used, IP address or device, date and time, session start and end times, and whether the action succeeded or failed. This level of detail allows security teams to reconstruct sessions with precision.
Logs from various systems must be correlated to form a unified timeline of related events. For example, a centralized platform should link events like a VPN login, subsequent access to an EHR system, and any unusual data export activity into one cohesive timeline [6][3]. Without this correlation, security teams may struggle to piece together breach timelines, leading to delays in response. Additionally, logs must be safeguarded against tampering, stored in immutable formats, and made searchable, enabling Security and Privacy Officers to respond quickly to incidents like repeated failed logins or unusual access patterns [6][3].
Automatic Logoff and Session Timeout Settings
Automatic session termination is a critical safeguard against unauthorized access to ePHI, especially on shared or unattended devices. By enforcing automatic logoff, organizations can significantly reduce the risk of accidental or malicious access.
Session timeout settings should be uniformly applied across all systems handling ePHI, including EHRs, patient portals, telehealth platforms, cloud applications, and third-party tools [3][5]. Governance practices must ensure these settings are not disabled or bypassed. For cloud-based and third-party environments, Business Associate Agreements should clearly outline logging responsibilities and enforce session timeout configurations to maintain comprehensive security [3][5].
Real-Time Monitoring and Alert Systems
Real-time alerts are a cornerstone of HIPAA-compliant session monitoring. These alerts rely on advanced analytics to detect behaviors that may indicate unauthorized access or misuse of ePHI. Examples include repeated failed login attempts, anomalies like impossible travel or unusual access hours, excessive PHI record views by a single user, access to restricted records without proper authorization, or irregular remote or vendor access patterns [6][2][3].
When paired with automatic session terminations, real-time alerts enable swift responses to potential threats. Alert thresholds should be tailored to each role's baseline behavior, regulatory requirements for minimum necessary access, and the organization's incident history [2][3]. For instance, an alert might trigger if a receptionist account views an unusually high number of records in a short period or if an account logs in from an unexpected foreign IP address [2][3]. These alerts should integrate seamlessly with incident response workflows, allowing Security Officers to investigate promptly, document findings, and initiate breach analysis in compliance with HIPAA's Breach Notification Rule [6][3].
sbb-itb-535baee
How to Add Session Monitoring to Your Healthcare Risk Program
To enhance your healthcare risk program, start by evaluating your current session monitoring processes, particularly for cloud services, vendor access points, and remote workstations.
Review Your Current Session Monitoring Setup
Take stock of all systems that handle electronic Protected Health Information (ePHI). This includes EHR platforms, telehealth tools, VPNs, cloud applications, remote access systems, billing software, and imaging platforms. For each system, document key session log details, such as login/logout events, failed attempts, IP addresses, device identifiers, and user actions. Then, ensure these logs align with HIPAA's requirements for audits, access control, and authentication.
Next, examine where these logs are stored, how long they're kept, and who reviews them. Look for gaps - like shared workstations without monitoring, unmanaged SaaS tools, or disconnected logs across systems. Determine if centralized tools, such as Security Information and Event Management (SIEM) systems or log management software, are being used to connect activity across platforms and identify anomalies. Since these logs often include sensitive patient information, make sure they are protected with encryption, access restrictions, and integrity controls.
This detailed review sets the stage for creating standardized policies to address any weaknesses.
Create Standard Policies and Controls
Develop clear policies requiring logs to capture essential details: user ID, timestamps, source devices, access types, and success statuses. Ensure log retention aligns with HIPAA’s six-year minimum requirement.
Establish procedures for regular log reviews and incident responses. These should include measures like forced logoffs, account lockout thresholds, and reporting protocols for security incidents. For higher-risk activities - such as privileged administrative access or remote vendor sessions - implement enhanced monitoring, such as detailed activity logs or session recordings, with well-defined retention policies.
Once internal policies are solidified, consider adopting a dedicated risk management platform to streamline and centralize session monitoring.
Use Risk Management Platforms Like Censinet
Platforms like Censinet RiskOps™ can simplify session monitoring across complex healthcare environments. Censinet RiskOps™ integrates risk data, correlates fragmented logs, and provides visibility into areas like remote and vendor access - gaps that traditional EHR logging might overlook.
As Matt Christensen, Sr. Director GRC at Intermountain Health, puts it: "Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare."
Censinet also supports benchmarking against industry standards, helping organizations measure their performance and advocate for necessary resources.
Brian Sterud, CIO at Faith Regional Health, emphasizes, "Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters."
The platform’s automation features and risk visualization tools allow security teams to shift from manual data collection to proactive monitoring and response. For instance, Tower Health reported that adopting Censinet RiskOps allowed three full-time employees to return to their primary roles, reducing the risk team size from five to two. By offering centralized oversight and real-time insights, platforms like Censinet strengthen HIPAA compliance and enhance session monitoring efforts across healthcare systems.
Conclusion
Session monitoring plays a crucial role in meeting HIPAA compliance requirements. By tracking who accessed electronic protected health information (ePHI), when and where they accessed it, and what actions were performed, healthcare organizations can comply with the HIPAA Security Rule's mandates for audit controls, access controls, and person/entity authentication. These logs provide an auditable record that regulators expect during reviews or investigations. Beyond compliance, this detailed logging also enables quicker identification of potential threats.
Effective session monitoring does more than fulfill regulatory obligations - it actively reduces security risks. By correlating logs from electronic health records (EHRs), cloud platforms, telehealth tools, and remote access systems, security teams can detect unusual activities like off-hours access, large data downloads, or repeated failed login attempts in mere hours rather than days. This is especially critical given the alarming rise in health data breaches. In 2023, over 133 million individuals were impacted by large-scale health data breaches (affecting 500+ records), more than doubling the numbers from 2018 [3][4]. Early detection and swift response can help prevent incidents from escalating into full-blown reportable breaches.
The modern U.S. healthcare ecosystem relies on a mix of cloud-based systems, specialty applications, and remote access points. Fragmented logging across these systems often complicates efforts to prove HIPAA compliance or investigate potential security incidents. Unified session data addresses this challenge, improving the speed and accuracy of threat detection, incident containment, and audit documentation.
Beyond compliance and security, session monitoring safeguards patient trust and safety. Patients expect their health data - whether stored in EHRs, telemedicine platforms, or patient portals - to be as secure as their financial information. Clear and auditable controls not only meet these expectations but also protect the confidentiality that is fundamental to the patient–provider relationship. This ensures data integrity and availability, both of which are critical for clinical decision-making. Strengthening these safeguards reinforces an organization’s overall security posture and commitment to compliance.
To make session monitoring a cornerstone of your HIPAA risk management strategy, ensure comprehensive logging across all systems handling ePHI. Centralize log management to correlate events effectively and integrate monitoring into your broader risk management framework. Platforms like Censinet RiskOps™ can help streamline this process by consolidating risk data, validating vendor controls, and providing enterprise-wide visibility, enabling healthcare organizations to transition from manual checks to proactive monitoring.
FAQs
How does session monitoring help ensure HIPAA compliance?
Session monitoring is essential for upholding HIPAA compliance, as it keeps a close watch on access and activity within healthcare systems. This ongoing oversight is key to spotting unauthorized access or suspicious behavior that might jeopardize protected health information (PHI).
With detailed audit trails, session monitoring bolsters accountability and equips healthcare organizations to respond swiftly to potential security threats. Beyond meeting HIPAA's strict standards, it also adds an extra layer of defense for safeguarding sensitive patient data.
What challenges do healthcare organizations face when monitoring user sessions?
Healthcare organizations face a variety of hurdles when it comes to monitoring user sessions. One big challenge is achieving real-time visibility into user activities while keeping up with the demand for detailed audit trails. Add to that the task of handling large data volumes without slowing down performance, and it’s clear how complex this balancing act can get. On top of it all, ensuring strong security measures while maintaining a smooth user experience is no small feat - especially in clinical settings where workflows must remain uninterrupted to provide quality care.
Another sticking point is the integration of session monitoring tools into existing systems while adhering to strict HIPAA regulations. Protecting sensitive patient data without disrupting daily operations calls for thoughtful planning and precise execution. It’s a delicate process that requires careful attention to both compliance and functionality.
Why is centralized log management important for session monitoring and HIPAA compliance?
Centralized log management is crucial for effective session monitoring, especially in healthcare settings. By consolidating all system activity data into a single platform, it becomes much easier to identify unusual or non-compliant behavior. This is essential for protecting sensitive patient information, such as protected health information (PHI), and ensuring compliance with HIPAA regulations.
With centralized access to logs, healthcare organizations can stay prepared for audits and respond swiftly to potential security threats. This approach not only supports compliance but also bolsters the protection of patient data, creating a more secure environment overall.


