How SOC 2 Enhances Healthcare Data Security Policies
Post Summary
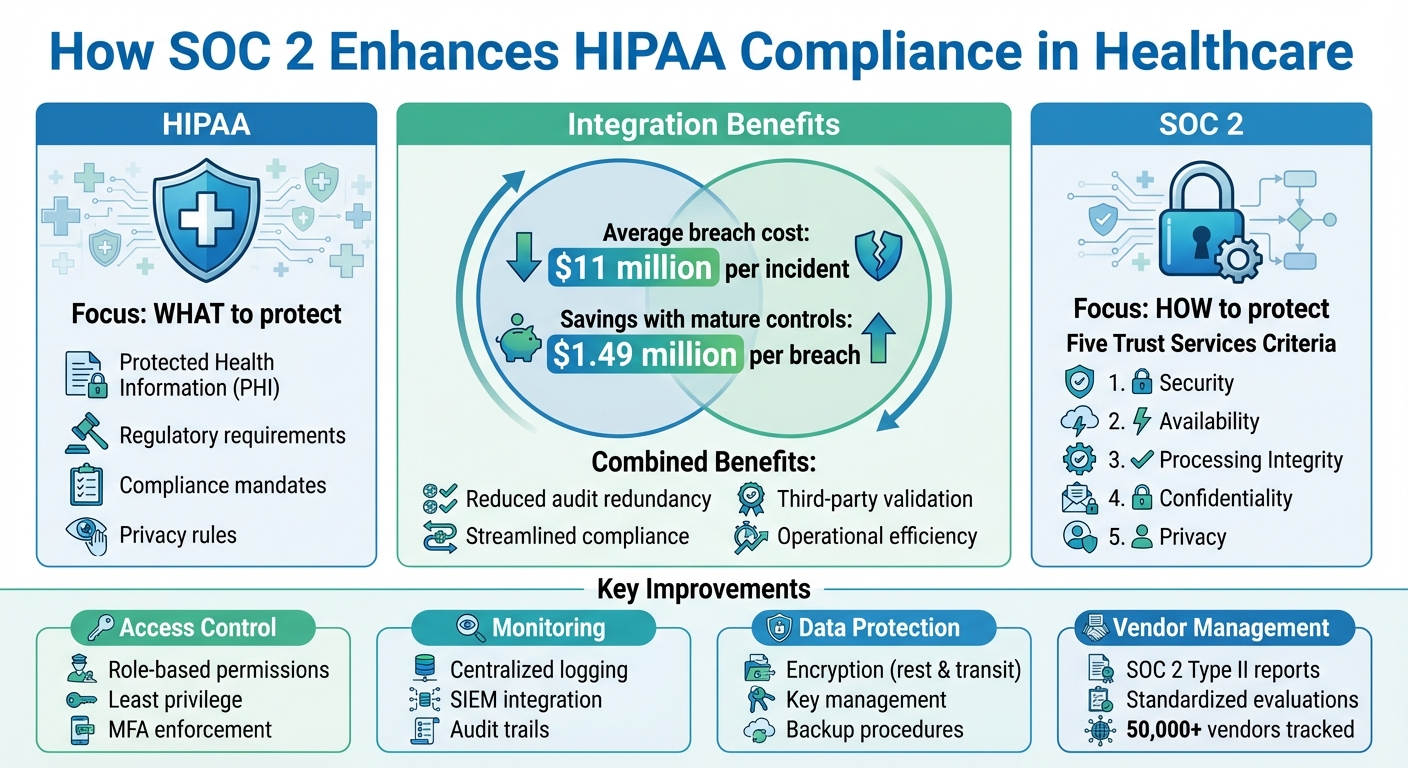
SOC 2 helps healthcare organizations strengthen data security by addressing critical challenges like breaches, outdated systems, and vendor risks. While HIPAA mandates what to protect, SOC 2 focuses on how to protect it through five Trust Services Criteria: Security, Availability, Processing Integrity, Confidentiality, and Privacy.
Key benefits include:
- Stronger Access Control: Role-based permissions, least privilege, and better identity management.
- Improved Monitoring: Centralized logging, audit trails, and faster incident response.
- Enhanced Data Protection: Encryption for sensitive data at rest and in transit.
- Better Vendor Oversight: Standardized evaluations and SOC 2 Type II reports for third-party risk management.
SOC 2 complements HIPAA, improves compliance readiness, and reduces the risk of breaches, which cost healthcare organizations an average of $11 million per incident. By integrating SOC 2 into governance, healthcare providers can protect patient data, meet regulatory demands, and build trust.
SOC 2 vs HIPAA: Complementary Healthcare Data Security Frameworks
Common Challenges in Healthcare Data Security Policies
Even with HIPAA's stringent requirements, many healthcare organizations struggle to implement effective security policies. The issue often lies in focusing on checkbox compliance rather than adopting a proactive, risk-based approach. This leaves protected health information (PHI) exposed to increasingly sophisticated cyber threats[4][6]. These challenges highlight why SOC 2 controls can play a critical role in strengthening healthcare data security.
Weak Technical Safeguards and Monitoring
Access control remains a major vulnerability in healthcare security. Many organizations still use shared accounts, outdated access controls, and grant excessive privileges, exposing sensitive patient data to unnecessary risks[4][6]. The problem worsens when access for employees who leave or change roles isn’t revoked promptly.
Adding to these risks, many healthcare providers lack proper monitoring systems. Without centralized logging tools like SIEM or comprehensive audit trails, organizations struggle to meet HIPAA’s requirements and respond effectively to incidents[4][5]. Legacy systems often fail to support modern security measures, such as encryption for data at rest and in transit, proper network segmentation, and timely software updates[4][6]. Moreover, outdated medical devices and clinical applications - often running on unsupported operating systems - create exploitable vulnerabilities that attackers actively target.
These gaps make a strong case for implementing SOC 2 controls to address these shortcomings.
Third-Party and Vendor Risk Management Problems
The healthcare supply chain adds another layer of complexity. A significant number of breaches stem from business associates and vendors, not the healthcare organizations themselves[6][3]. Yet, many providers fail to conduct thorough due diligence when onboarding new vendors, relying on outdated questionnaires and manual spreadsheets for tracking.
"Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required." – Terry Grogan, CISO, Tower Health
Healthcare organizations often lack visibility into their vendors' actual security practices. Contracts frequently omit key elements like security obligations, breach notification timelines, or audit rights[3][6]. When a vendor suffers a breach, the healthcare provider typically shoulders the regulatory and reputational fallout, even though the incident occurred outside their direct control.
With the healthcare industry relying on over 50,000 vendors and products, traditional risk management methods simply don’t scale[1]. Manual assessments consume significant resources and often fail to address smaller vendors that handle PHI but lack mature security measures.
Beyond vendor risks, fragmented policies further weaken overall security.
Disconnected Policies Across Systems and Supply Chains
In many healthcare organizations, security policies are scattered across different systems. For example, one set of rules might govern the EHR, while another applies to cloud applications, medical devices, or supply chain partners[4][6][7]. This siloed approach leads to inconsistent protection for PHI and makes enforcing uniform security standards nearly impossible. Managing these fragmented systems becomes even more challenging in complex healthcare environments.
The growing use of connected medical devices (IoMT), telehealth platforms, and cloud-based clinical tools has expanded the attack surface significantly[7]. Each new system introduces additional complexity, and without centralized policy management, maintaining consistent security across the entire technology ecosystem becomes a daunting task. Different departments often manage different systems, creating coordination issues and gaps in coverage.
Documentation issues compound the problem. Incomplete logs, risk assessments, and training records undermine compliance efforts and hinder incident response[4][6]. During audits or breach investigations, piecing together evidence from disconnected systems is not only time-consuming but also prone to errors, delaying responses and amplifying the damage.
Addressing these challenges requires the comprehensive framework that SOC 2 controls provide.
How SOC 2 Improves Healthcare Data Security Policies
SOC 2 provides healthcare organizations with a clear framework to strengthen their data security policies. While HIPAA outlines what needs to be protected, SOC 2 focuses on how to protect it. By using its five Trust Services Criteria - security, availability, processing integrity, confidentiality, and privacy - SOC 2 helps close the security gaps that healthcare organizations often face. It offers a structured approach to safeguarding system access, monitoring operations, and managing vendors, complementing HIPAA’s broader regulations[4][6][2].
Better Access Control and Identity Management
SOC 2 enforces strict access control measures, ensuring that only authorized individuals can access sensitive data. This includes principles like least privilege, role-based access, and regular reviews of access permissions[4][5][2]. Organizations must implement processes for provisioning and deprovisioning user access, monitor privileged accounts, and enforce multi-factor authentication (MFA) for remote access, privileged accounts, and any applications dealing with PHI. These measures ensure that access rights are tied to actual job responsibilities and are promptly revoked when employees leave or change roles.
Strong password policies and identity verification procedures also become mandatory, which significantly reduces the risk of breaches caused by compromised credentials. Since stolen credentials remain one of the leading causes of data breaches, these controls provide healthcare organizations with an effective way to mitigate this vulnerability[4][5][6].
Stronger Logging, Monitoring, and Incident Response
SOC 2 emphasizes the importance of centralized logging and continuous monitoring. Organizations are required to track user activity, system changes, security events, and access to sensitive data[4][5][6]. This often involves implementing tools like SIEM systems and maintaining detailed audit trails. Logs must be securely stored, retained for specified periods, and monitored for suspicious activity. This approach not only helps detect breaches faster but also supports thorough investigations.
Incident response is another critical area under SOC 2. Organizations must establish detailed incident response plans, outlining roles, escalation procedures, and testing protocols. Regular tabletop exercises and post-incident reviews are required to ensure that responses are well-coordinated and effective. This shift transforms incident management from a chaotic reaction to a structured process that minimizes downtime and damage[4][6].
Improved Data Protection and Encryption Standards
SOC 2 sets rigorous expectations for data protection, including encryption for data both in transit and at rest. For healthcare organizations, this means encrypting PHI across all platforms - such as EHR systems, telehealth applications, and third-party services - using modern encryption standards[4][5][7].
Key management also becomes a formalized process under SOC 2. Policies must cover key generation, secure storage (e.g., hardware security modules or cloud-based solutions), rotation schedules, and access controls[5][6]. Additionally, organizations are required to define robust backup and recovery procedures. This includes setting recovery time objectives, testing backups regularly, and storing them offsite. These measures ensure that even in the event of a breach or ransomware attack, patient data remains secure and systems can be restored quickly[4][5].
Better Vendor and Third-Party Risk Management
SOC 2 doesn’t stop at internal controls - it also addresses vendor and third-party risks. By using SOC 2 standards, healthcare organizations can evaluate vendors in a consistent and standardized way. SOC 2 Type II reports demonstrate not only that vendor controls are properly designed but also that they are effective over time, typically over a six- to twelve-month period[6][3][2].
Healthcare organizations can embed SOC 2 requirements into vendor contracts to ensure alignment with their own security policies. Tools like Censinet RiskOps™ make it easier to centralize SOC 2 reports, risk assessments, and remediation tracking, cutting down on manual effort and inconsistencies in vendor management. This approach ensures that the organization’s supply chain doesn’t become its weakest link, while also reducing friction during vendor onboarding[4][3].
Implementing SOC 2 for Healthcare Security Governance
Adding SOC 2 to Risk Management Frameworks
Incorporating SOC 2 into existing risk management frameworks - like NIST CSF, HITRUST, ISO 27001, or enterprise-wide ERM systems - can strengthen your security governance. Start by mapping SOC 2 Trust Services Criteria directly to your current frameworks. This process helps pinpoint policy gaps and assigns ownership to specific roles, ensuring accountability.
To make SOC 2 a key part of your governance strategy, include it as a recurring topic in security and risk committee meetings. Assign executive sponsors, such as the CIO, CISO, or Chief Privacy Officer, to oversee specific SOC 2 domains. Regularly report on risks, remediation efforts, and audit findings at the board level. This approach shifts SOC 2 from being just another compliance requirement to becoming a dynamic governance tool that drives accountability and continuous progress.
SOC 2 should also be integrated into operational workflows like access provisioning, change management, and incident response. Use ticketing systems to track remediation efforts, linking tickets to risk records to monitor trends and closure rates. This ensures SOC 2 controls are not just documented but actively implemented and monitored, creating a foundation for ongoing improvements across daily operations.
Using Censinet RiskOps™ for SOC 2 Compliance

Censinet RiskOps™ offers a centralized platform for managing SOC 2 compliance and vendor risk in the healthcare sector. It allows organizations to upload and review SOC 2 reports, track risks related to protected health information (PHI), maintain audit evidence, and provide executive-level dashboards - all within a system tailored to healthcare's regulatory and operational needs.
"Not only did we get rid of spreadsheets, but we have that larger community [of hospitals] to partner and work with." – James Case, VP & CISO, Baptist Health
This platform minimizes manual work while enabling organizations to scale their ability to manage SOC 2 requirements and vendor risks effectively.
Measuring Policy Maturity Before and After SOC 2
Embedding SOC 2 into daily operations allows organizations to measure the maturity of their policies over time. Start by establishing baseline maturity scores for key policy areas - such as access control, logging and monitoring, incident response, and vendor management - using a five-level scale: ad hoc, repeatable, defined, managed, and optimized.
After implementing SOC 2 and completing audit cycles, reassess these domains to track improvements. This provides clear, evidence-based insights into how your governance is evolving.
"Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters." – Brian Sterud, CIO, Faith Regional Health
Monitor key performance indicators like reductions in PHI-related security incidents, fewer emergency changes causing downtime, improved availability for critical clinical systems, and faster vendor onboarding. These measurable outcomes demonstrate how SOC 2 governance delivers value to both technical teams and business stakeholders.
sbb-itb-535baee
Measuring the Impact of SOC 2 on Healthcare Data Security
Better Risk and Security Outcomes
SOC 2 controls play a crucial role in improving security outcomes by cutting down quarterly critical security findings, speeding up incident response times, and enhancing vendor oversight. By emphasizing robust logging, monitoring, and incident response, SOC 2 reduces both the likelihood of breaches and their potential impact.
Consider this: healthcare data breaches in the U.S. come with an average price tag of $11 million per incident, making it the most expensive sector for breaches. Organizations that maintain mature security strategies and regularly test their incident response processes save approximately $1.49 million per breach compared to those lacking these measures. SOC 2’s structured approach to access control, encryption, and vulnerability management helps healthcare providers achieve these savings by methodically minimizing their exposure to threats.
Key performance indicators (KPIs) like the number of critical security findings per quarter, mean time to detect and respond to incidents, percentage of vendors with current SOC 2 reports, and monthly policy exceptions or access violations provide clear evidence of progress. These metrics not only highlight improvements in security posture but also make compliance and audit processes more straightforward.
Easier Compliance and Audit Readiness
SOC 2 simplifies the path to HIPAA compliance by operationalizing many overlapping security and privacy controls. Since SOC 2 and HIPAA share significant similarities, organizations can often leverage the same evidence for both audits, making it easier to demonstrate compliance. SOC 2’s emphasis on documented, testable controls over a defined period also helps organizations show regulators, payers, and health system partners that they’re taking security seriously.
Increasingly, large health systems require SOC 2 Type II reports from vendors during onboarding. What was once a "nice-to-have" credential has now become a baseline requirement for digital health companies, telehealth providers, and medical device vendors. Vendors with up-to-date SOC 2 reports benefit from quicker procurement processes and fewer repetitive security questionnaires, making compliance not just a necessity but a competitive advantage.
More Efficient Operations Through Standardized Processes
SOC 2 doesn’t just enhance security - it also boosts operational efficiency across the board. Its policies standardize processes like change management, incident response, and access reviews, making daily operations smoother and more predictable.
Tools like Censinet RiskOps™ help healthcare organizations align their risk management practices with SOC 2 standards. By centralizing vendor risk data and creating dashboards to track remediation efforts, these platforms make it easier to measure efficiency. For example, organizations can reduce the time it takes to grant or revoke access, cut down on manual security reviews, and speed up vendor onboarding. Consolidating risk management in this way minimizes manual work while enabling organizations to scale their SOC 2 requirements effectively. The result? A streamlined, scalable approach to managing risks that supports growth without requiring a proportional increase in staff.
Conclusion
SOC 2 provides healthcare organizations with a structured approach to tackling critical data security challenges. By implementing enhanced controls, ongoing monitoring, and better vendor oversight, organizations can address the rising costs associated with healthcare data breaches - averaging over $10 million per incident, the highest across all industries.
This framework goes beyond compliance. SOC 2 simplifies aligning with HIPAA by operationalizing overlapping controls, cutting down on redundant audit efforts, and offering the independent third-party validation increasingly demanded by health systems, payers, and regulators. As cyber threats grow more advanced and vendor expectations shift, SOC 2 becomes a cornerstone of healthcare security governance, not just a regulatory checkbox.
To make the most of SOC 2, healthcare organizations should weave it into their operational governance strategies. As outlined earlier, integrating SOC 2 into risk management can significantly enhance security practices. Start by mapping current controls to the Trust Services Criteria and embedding SOC 2 requirements into existing frameworks to create a unified control library. Leveraging tools like Censinet RiskOps™ can help centralize third-party risk assessments and manage SOC 2-aligned remediation efforts across sensitive areas like PHI, clinical systems, and medical devices. Partner with an independent auditor to complete a Type 1 assessment of control design, followed by a Type 2 report to validate long-term operational effectiveness.
Track progress with clear KPIs, such as the number of quarterly critical findings, incident response times, and the percentage of vendors maintaining up-to-date SOC 2 reports. By treating SOC 2 as a continuous governance tool rather than a one-time task, healthcare organizations can build stronger relationships with patients and partners while staying ahead in an ever-evolving threat landscape.
FAQs
What’s the difference between SOC 2 and HIPAA when it comes to protecting healthcare data?
SOC 2 offers a structured approach to managing operational controls and security across various industries, including healthcare. Its primary focus lies in data protection, risk management, and strengthening overall security measures. On the other hand, HIPAA is exclusively designed for the healthcare sector, enforcing strict legal standards to protect Protected Health Information (PHI). This includes rules for privacy and clear guidelines for breach notifications.
While HIPAA compliance is a legal obligation for healthcare organizations, SOC 2 serves as a valuable addition. It highlights advanced security practices and broader control measures that go beyond HIPAA’s baseline requirements. When combined, these frameworks help healthcare organizations achieve both legal compliance and a higher level of data security.
What are the key advantages of adopting SOC 2 for healthcare data security?
Adopting SOC 2 in healthcare plays a key role in bolstering data security policies, meeting industry regulations, and improving risk management practices. By implementing these standards, healthcare organizations can better protect sensitive information, such as patient data and protected health information (PHI), significantly lowering the chances of data breaches.
Beyond security, achieving SOC 2 compliance helps build trust and confidence with patients, partners, and stakeholders by showcasing a clear dedication to safeguarding critical information. It also streamlines audit procedures, saving both time and resources, all while maintaining adherence to rigorous security requirements.
How does SOC 2 help strengthen vendor risk management in healthcare?
SOC 2 plays a crucial role in improving vendor risk management within the healthcare sector. It establishes a set of standardized controls designed to address key areas such as data security, confidentiality, and privacy. These controls make it easier for healthcare organizations to assess and oversee third-party compliance, ensuring vendors adhere to stringent security protocols.
When healthcare organizations adopt SOC 2, they can better safeguard sensitive patient information, including PHI (Protected Health Information). This not only reduces the likelihood of vendor-related data breaches but also helps align operations with industry standards for cybersecurity and risk management.


