Technology Convergence: How AI, Cloud, and Automation Reshape Business Risk
Post Summary
AI, cloud computing, and automation are transforming healthcare - but they also introduce new risks. Here's what you need to know:
- AI Risks: Vulnerabilities like adversarial attacks, "black box" algorithms, and inaccurate outputs can compromise patient safety and trust in medical decisions.
- Cloud Risks: Distributed data and reliance on third-party vendors expand attack surfaces, making consistent security a challenge.
- Automation Risks: Connected medical devices (IoMT) and automated workflows can be exploited, leading to disruptions in care or dangerous system failures.
Healthcare data is highly valuable, with breaches costing organizations millions annually. To address these challenges, solutions like Censinet RiskOps™ streamline risk management by automating vendor assessments, combining human oversight with AI, and offering real-time monitoring dashboards. By integrating these practices, healthcare providers can better protect sensitive data, maintain compliance, and ensure patient safety while leveraging modern technologies.
Risks from AI, Cloud, and Automation
AI, cloud computing, and automation bring transformative potential to healthcare, but they also introduce a web of vulnerabilities. Each technology carries its own risks, and when combined, these threats can amplify across interconnected systems. Let’s break down the specific challenges tied to each.
AI Risks: Adversarial Attacks and Trust Challenges
AI in healthcare comes with risks that extend beyond the typical cybersecurity concerns. Key threats include data breaches, opaque algorithms, and vulnerabilities in AI-driven medical devices - all of which can jeopardize patient safety and organizational security [1].
One major issue is the "black box" nature of many AI models, such as large language models and deep learning systems. These models often lack transparency, making it hard to explain how they arrive at decisions. This lack of clarity complicates informed consent and can erode trust in critical care decisions [1]. For example, healthcare providers and patients may struggle to understand why a specific diagnosis or treatment recommendation is made, creating uncertainty in high-stakes scenarios.
Generative AI brings another layer of risk. It can produce inaccurate or "hallucinated" data - false information presented with an air of confidence [1]. In healthcare, such errors could lead to misdiagnoses or flawed treatment plans if recommendations aren’t carefully verified.
Adversarial attacks pose yet another threat. These deliberate attempts to manipulate training data can disrupt AI systems, leading to unsafe predictions or outputs that undermine patient care.
While AI presents these unique challenges, cloud computing introduces its own set of vulnerabilities.
Cloud Risks: Broader Attack Surfaces and Vendor Dependencies
Cloud computing has revolutionized how healthcare organizations manage data, but it has also expanded the potential for cyberattacks. Moving to cloud-based systems creates larger, interconnected environments that are more susceptible to breaches [1].
One significant concern is the reliance on third-party vendors. These partnerships often require vendors to have extensive access to hospital systems, creating additional entry points for attackers [1]. Unfortunately, healthcare organizations may have limited visibility into how these vendors secure their systems, leaving potential blind spots in their defenses.
Another challenge is maintaining consistent security across distributed cloud infrastructures. With data spread across multiple locations, monitoring for anomalies and ensuring uniform security controls becomes increasingly complex.
Automation Risks: IoMT Weaknesses and Workflow Disruptions
The Internet of Medical Things (IoMT) connects devices like pacemakers, insulin pumps, imaging systems, and patient monitors. While this connectivity improves care coordination and enables real-time monitoring, it also exposes these devices to cyber threats. Many IoMT devices have outdated security measures, lacking basic protections like encryption or strong authentication, which makes them prime targets for ransomware and denial-of-service (DoS) attacks [1][2].
Automated workflows and AI-controlled medical devices introduce additional risks. Unauthorized alterations to these systems could lead to dangerous changes, such as incorrect medication dosages or tampered pacemaker settings [1][2]. Attackers may exploit these vulnerabilities to disrupt critical care processes, putting patients at serious risk.
The interconnected nature of automation also means that a failure in one system can ripple across others, disrupting workflows and potentially compromising patient safety on a larger scale.
Managing Technology Risks with Censinet RiskOps™
Healthcare organizations face increasing challenges as technology convergence reshapes their operational landscape. To tackle these risks effectively, they need a unified approach to cybersecurity and risk management. Censinet RiskOps™ steps in as a centralized platform designed specifically to address these needs, offering a streamlined solution for managing healthcare technology risks.
This platform covers everything from third-party vendor assessments to enterprise risk management, providing comprehensive visibility into an organization’s risk environment. By replacing fragmented processes, it enables security teams to oversee risks tied to patient data, clinical applications, medical devices, and supply chains - all from a single, cohesive system. Here's how it simplifies risk management across key areas.
Accelerating Third-Party Risk Management with Censinet AITM
Third-party vendors often introduce vulnerabilities, especially when they require extensive access to hospital systems. Traditional risk assessments can take weeks - or even months - leaving organizations exposed during the evaluation process.
Censinet AITM changes the game by automating and expediting third-party risk assessments. Vendors can complete security questionnaires in seconds, while the platform automatically processes their evidence, documentation, and product integration details. It also identifies potential fourth-party risks and generates comprehensive summary reports based on all collected data. For healthcare organizations, this means addressing vulnerabilities more quickly and reducing risk before issues escalate into critical threats.
Human-in-the-Loop AI: Merging Automation with Expertise
While automation can streamline processes, relying solely on it in healthcare risk management can pose safety concerns. That’s why Censinet AI employs a human-in-the-loop approach, blending automation with human oversight to ensure decisions are both efficient and thoughtful.
The platform supports tasks like evidence validation, policy creation, and risk mitigation through human-guided automation. Configurable rules and review processes allow risk teams to maintain control, ensuring that automation enhances rather than replaces human judgment. This approach helps healthcare organizations scale their risk management efforts without compromising the nuanced expertise required for complex scenarios.
In practice, Censinet RiskOps™ operates like "air traffic control" for managing AI-related risks. Key findings and tasks are automatically assigned to the appropriate teams for review and approval, ensuring that the right stakeholders address the right issues at the right time.
Real-Time Monitoring with Risk Dashboards
When managing converged technology risks, visibility is non-negotiable. Censinet RiskOps™ offers intuitive dashboards that consolidate real-time data into a single, easy-to-navigate interface.
These dashboards give security teams a clear view of risks across third-party vendors, enterprise systems, and AI deployments. By visualizing emerging threats, teams can prioritize remediation efforts effectively. For AI-related risks, the platform centralizes all policies, tasks, and risks, ensuring continuous oversight and accountability. This real-time monitoring shifts organizations from a reactive stance to a proactive approach, enabling them to address risks before they escalate into larger issues.
sbb-itb-535baee
Applying Risk Management Frameworks in Healthcare
The integration of AI, cloud technologies, and automation in healthcare requires careful coordination. These interconnected systems demand a structured approach that balances operational efficiency with regulatory compliance. The focus is shifting from reactive risk management - where threats are addressed after they occur - to proactive strategies that anticipate and mitigate risks before they arise. This proactive mindset helps weave regulatory compliance into the daily operations of healthcare organizations.
Today’s healthcare risk management relies on multidisciplinary frameworks that incorporate cybersecurity at every stage of technology adoption - starting from vendor selection and continuing through monitoring and compliance checks.
Meeting HIPAA and Regulatory Requirements
AI and automation add layers of complexity to HIPAA compliance. These technologies bring new challenges, such as adversarial attacks, reliance on cloud infrastructure, and vulnerabilities in the Internet of Medical Things (IoMT). To address these risks, the guiding principle remains clear: treat workflows involving AI just as rigorously as those handling Protected Health Information (PHI). This means ensuring compliance from the earliest design stages through deployment and ongoing operations.
Healthcare organizations need to implement comprehensive governance frameworks for AI usage. This involves creating clear policies for AI implementation, thoroughly vetting vendors, and training staff to avoid introducing unauthorized AI tools that haven’t undergone proper security reviews. For vendors managing PHI through cloud platforms or automated systems, organizations must require documented proof of HIPAA-compliant security measures. This includes regular risk assessments, transparent reporting, and evidence of robust security controls.
Beyond HIPAA, healthcare providers must also navigate state-specific privacy laws, FDA regulations for AI-powered medical devices, and emerging legislation targeting AI technologies. Tools like Censinet RiskOps™ simplify this process by centralizing compliance tracking, enabling organizations to manage multiple regulatory requirements through unified documentation and audit trails.
Building Integrated Cybersecurity Strategies
Managing the convergence of AI, cloud, and automation requires a cohesive strategy. Healthcare providers should avoid treating these areas as separate initiatives and instead build a unified framework that connects AI governance, cloud security, and automation oversight.
One effective step is forming an AI governance committee that includes representatives from clinical operations, IT security, legal, compliance, and risk management. This cross-functional team can evaluate AI implementations, assess their impact on workflows, and ensure they align with the organization’s risk tolerance. The committee should also have access to real-time data that shows how AI systems interact with cloud infrastructure and automated processes, helping to identify vulnerabilities before they escalate into major issues.
Enterprise Risk Management (ERM) frameworks offer a strong foundation for this integrated approach. By applying ERM principles, organizations can assess risks comprehensively - for example, understanding how an AI system’s reliance on cloud services might impact the security of medical devices, or how failures in automation could disrupt interconnected clinical workflows. This broader perspective enables teams to prioritize risk mitigation based on overall business impact rather than isolated concerns.
Continuous monitoring is critical. Healthcare organizations must regularly evaluate the combined risk profile of their technologies, test AI-driven automation during cloud disruptions, verify scalable security measures, and ensure that third-party vendors consistently meet high security standards across all touchpoints. This ongoing vigilance helps maintain a secure and compliant operational environment.
Conclusion: Using Technology Convergence to Build Resilience
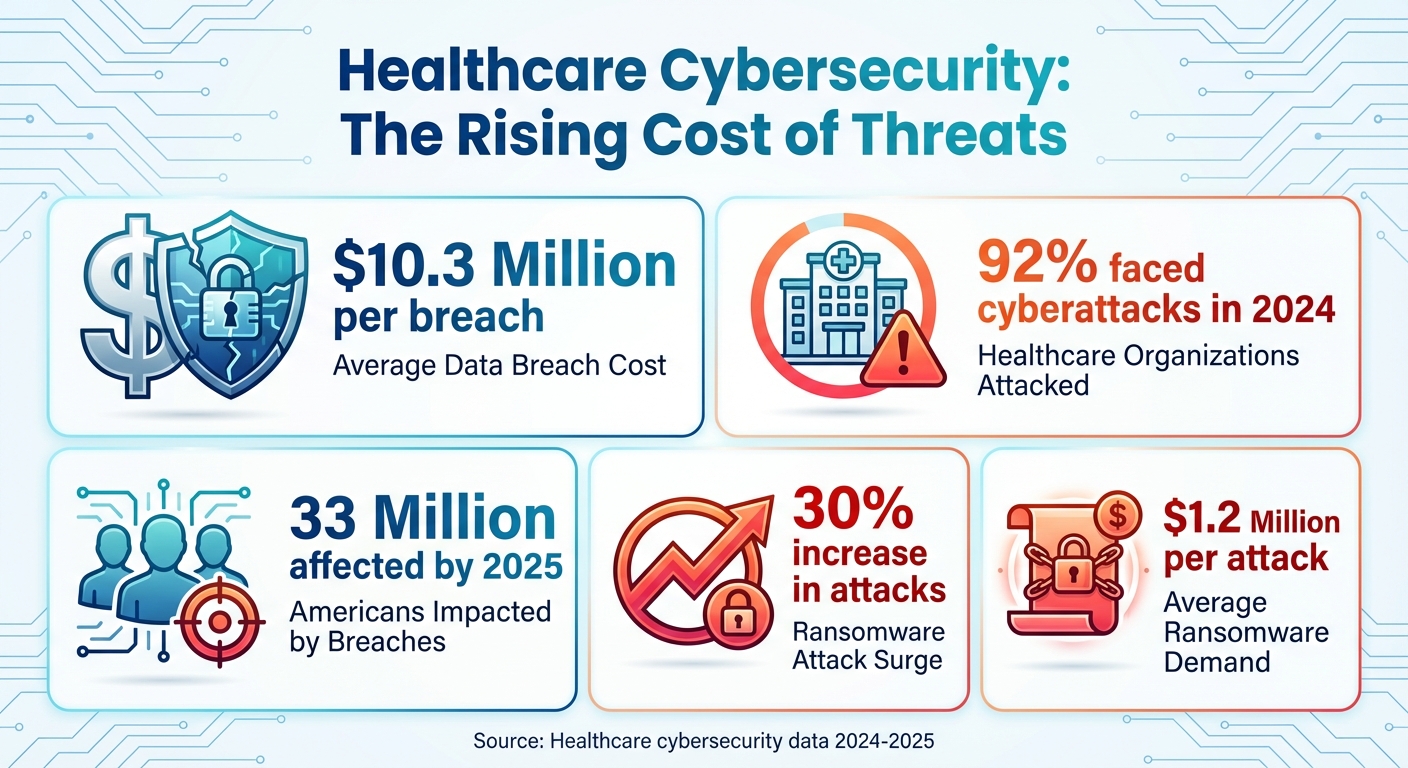
Healthcare Cybersecurity Statistics: Data Breach Costs and Attack Frequency 2024-2025
The blending of AI, cloud computing, and automation offers healthcare organizations a chance to improve patient care, streamline processes, and cut costs. But these advancements come with serious challenges. For instance, the average cost of a data breach in healthcare has reached $10.3 million. In 2024 alone, 92% of healthcare organizations faced cyberattacks, and by 2025, data breaches impacted 33 million Americans [3].
To build resilience, healthcare providers must integrate AI, cloud, and automation into unified systems. This approach goes beyond simply meeting compliance standards - it transforms risk management into a strategic tool that drives innovation while protecting patient safety. By adopting this mindset, organizations can stay ahead of the curve in combating increasingly sophisticated cyber threats.
The rise in cybercrime underscores the urgency of this shift. Ransomware attacks have surged by 30%, with demands averaging $1.2 million [3]. Healthcare organizations can no longer afford to rely on reactive measures. Instead, they need to implement continuous monitoring and use risk management platforms that offer real-time insights. Crucially, this must include human oversight to ensure automation supports, rather than replaces, critical decision-making.
As technology continues to evolve, securely adopting these innovations is no longer optional - it’s essential. By investing in robust risk management frameworks and maintaining constant vigilance, healthcare organizations can embrace innovation while protecting what matters most: patient safety and uninterrupted care.
FAQs
What steps can healthcare organizations take to reduce risks when using AI in medical decision-making?
Healthcare organizations can better manage AI-related risks by taking a forward-thinking approach to risk management. This involves frequent audits of AI systems to uncover weaknesses, enforcing rigorous access controls to protect sensitive information, and leveraging secure solutions like blockchain for safe data sharing.
Using established guidelines, such as the NIST AI Risk Management Framework (NIST AI RMF), can promote transparency, accountability, and adherence to regulations. It's also essential to provide ongoing training for staff on AI best practices and to keep a close watch on systems to catch unintended biases or errors. These steps are key to maintaining trust and ensuring accurate medical decisions.
What are the main security risks of using cloud computing in healthcare?
Cloud computing has brought immense opportunities to healthcare, but it also comes with security challenges that demand attention. Among the biggest concerns are protecting sensitive patient information, ensuring compliance with regulations like HIPAA, and dealing with potential service disruptions or downtime. Another pressing issue is the limited control healthcare providers have over how third-party cloud providers manage their data, which can open the door to breaches or unauthorized access.
To tackle these challenges, healthcare organizations should prioritize strong encryption methods, perform regular security audits, and set up clear data management agreements with their cloud providers. These measures are essential for keeping patient data safe while making the most of cloud technology.
What impact does automation have on the security of connected medical devices?
Automation plays a key role in securing connected medical devices by enabling real-time threat detection, swift responses to cyber incidents, and automatic firmware updates to patch vulnerabilities. These features help healthcare organizations stay proactive against new threats while also reducing the likelihood of human error.
That said, automation isn’t without its challenges. It can create system-wide vulnerabilities if processes aren’t well-secured, and attackers might exploit these systems for malicious purposes. To strike the right balance, healthcare organizations need to implement strong security measures, perform regular audits, and closely monitor and update automated systems to ensure they remain secure.


