Telehealth Security: Identity Proofing vs. Authentication
Post Summary
Telehealth relies on two key security processes to protect patient data and ensure compliance: identity proofing and authentication.
- Identity proofing confirms a person’s identity during account setup by verifying documents like IDs, insurance cards, or biometrics. It prevents fake accounts and fraud.
- Authentication ensures that the same verified individual accesses the system during future logins, using methods like passwords, multi-factor authentication (MFA), or biometrics.
Together, these processes reduce risks such as medical identity theft, account takeovers, and data breaches while meeting HIPAA regulations. Identity proofing happens once (e.g., during registration), while authentication is ongoing every time a user logs in.
| Aspect | Identity Proofing | Authentication |
|---|---|---|
| Purpose | Verify identity during onboarding | Confirm identity during logins |
| Frequency | One-time or event-driven | Ongoing |
| Methods | IDs, biometrics, database checks | Passwords, MFA, biometrics |
| Focus | Prevent fake accounts and fraud | Protect access to sensitive information |
A strong combination of these methods ensures telehealth platforms remain secure, patient-focused, and compliant.
Identity Proofing vs Authentication in Telehealth: Key Differences
What Is Identity Proofing in Telehealth?
Identity proofing is the process of confirming a person's true identity during critical moments like account setup or when requesting high-risk privileges, such as e-prescribing controlled substances. Unlike authentication, which validates identity at each login, identity proofing lays the groundwork for all future authentication steps[1].
This process involves more than simply checking a username and password. It requires gathering and verifying multiple pieces of evidence - such as a government-issued ID, insurance card, or biometric data like a facial scan - against trusted sources. For example, a patient registering for a telehealth appointment might upload a picture of their driver's license, take a live selfie to match against the ID, and have their insurance details verified with payer records. These layers of verification make it much harder for fraudsters to create fake accounts using stolen or fabricated identities[2].
In telehealth, robust identity proofing is essential for preventing medical identity theft, safeguarding patient records, and ensuring compliance with HIPAA by confirming that only authorized individuals access sensitive electronic health information[1].
Main Goals and Regulatory Requirements
The key objectives of identity proofing in telehealth include:
- Blocking medical identity theft and fraud to prevent unauthorized access to treatments, prescriptions, or sensitive health data.
- Ensuring accurate patient–provider matching so that test results, diagnoses, and treatment plans are correctly linked to the right individual.
- Establishing a reliable identity record that supports secure access to electronic health information.
Identity proofing is also critical for the safe electronic prescribing of controlled substances (EPCS). Federal DEA regulations, along with many state laws, mandate strong identity verification and multifactor authentication for clinicians prescribing controlled substances electronically. This often involves validating government IDs, checking state licensing, and linking the clinician’s identity to hardware tokens. Regulatory frameworks like the HIPAA Privacy and Security Rules, DEA requirements, and the NIST Digital Identity Guidelines (SP 800-63 series) shape these protocols.
Common Identity Proofing Methods
Telehealth platforms typically use a combination of methods to verify the identities of patients and providers, aiming to achieve higher levels of security:
- Government ID validation: Patients submit a photo of their government-issued ID, which is checked against trusted databases for authenticity and matching details.
- Insurance card verification: Scanning or uploading an insurance card confirms coverage and ties the account to a verified individual.
- Biometric verification: A live selfie or facial scan with liveness detection is compared to the photo on the government ID, ensuring the person is real and present.
- Knowledge-based checks: Platforms may ask questions derived from public or credit bureau data to further verify identity.
- Out-of-band verification: Sending a code to a verified email or phone number provides an additional layer of security, though at a lower assurance level.
For clinicians and staff, identity proofing often involves stricter measures. This can include in-person or supervised remote verification, where HR or credentialing teams review government IDs, medical licenses, and employment documents. In fully digital workflows, combining document validation with biometric matching enhances security, and clinicians may also use hardware tokens for high-risk tasks like EPCS.
How Identity Proofing Fits Into Telehealth Workflows
Identity proofing is typically required during onboarding or when enabling high-risk functions such as e-prescribing controlled substances or granting proxy access. Re-proofing may be necessary in cases like legal name changes, updated identity documents, or when risk indicators emerge. These targeted checks integrate seamlessly into broader identity assurance systems, ensuring smooth transitions from initial verification to ongoing access.
Healthcare organizations often conduct risk assessments to determine the appropriate identity proofing methods for different scenarios. For lower-risk activities, basic document and contact verification might be sufficient. However, higher-risk situations - like EPCS or access to sensitive medical specialties - usually require more advanced measures such as government ID validation, biometric checks, and database verification. By combining thorough initial proofing with multifactor authentication or passwordless access for routine use, telehealth platforms can maintain strong security without overwhelming users.
Platforms like Censinet RiskOps™ can further support identity proofing efforts by helping healthcare organizations evaluate and manage the security and privacy risks associated with telehealth vendors and technologies. This integrated strategy ensures a secure and compliant foundation for virtual care, setting the stage for ongoing authentication protocols, which will be discussed in the next section.
What Is Authentication in Telehealth?
Authentication is all about confirming that a returning user is who they claim to be by verifying them against their previously established identity. After the initial identity proofing - done during onboarding to confirm someone’s identity - authentication kicks in every time they log into a telehealth system. Essentially, it’s a repeated check to ensure the same person is accessing the system each time. While identity proofing lays the groundwork, authentication keeps things secure on an ongoing basis.
In the world of telehealth, authentication plays a crucial role in safeguarding digital platforms like patient portals, video consultation tools, remote monitoring systems, e-prescribing modules, and administrative dashboards. These systems often contain sensitive electronic protected health information (ePHI), making strong authentication essential to prevent unauthorized access and protect against data breaches.
Main Goals and Regulatory Requirements
The primary goal of authentication in telehealth is to ensure that only authorized individuals can access ePHI. This helps maintain confidentiality, link users to their actions for accountability, and enforce role-based access control (so users only access what they’re authorized to). Under HIPAA’s Security Rule, organizations are required to implement technical safeguards like unique user IDs, emergency access procedures, automatic logoff, and encryption. They also need systems that verify a user’s identity.
To meet these standards, authentication systems often issue unique credentials and add extra verification steps for sensitive actions, such as e-prescribing. This is especially important given the rising threat of hacking incidents involving stolen credentials. In fact, compromised credentials were a leading cause of major healthcare data breaches in 2022, with the average cost of a U.S. healthcare breach hitting around $10 million per incident [3]. As a result, many organizations are turning to stronger authentication methods.
Common Authentication Methods
Telehealth systems rely on a mix of authentication methods, including single-factor, multi-factor, and biometric approaches:
- Single-factor authentication: This is the most basic method, typically using passwords or numeric PINs linked to a user account. While simple and familiar, it’s also vulnerable to threats like phishing, password reuse, credential stuffing, and even shoulder-surfing. These risks are heightened when patients use personal devices and unsecured home networks.
- Multi-factor authentication (MFA): MFA steps up security by requiring two or more types of verification: something you know (like a password), something you have (such as a mobile device or hardware token), and something you are (like a fingerprint). Common MFA setups in telehealth include pairing passwords with SMS codes, app-generated one-time passcodes (OTPs), push notifications, or hardware tokens like FIDO2 keys for high-security roles.
- Biometric authentication: This method uses physical traits like fingerprints, facial recognition (e.g., Face ID), or voice recognition. Users enroll their biometric data on their device, which is then used for future logins. While biometrics can be more convenient and reduce the risk of password theft, they bring concerns about privacy, data security, and accessibility for some users.
Balancing Security and Ease of Use
While strong authentication is essential for protecting sensitive telehealth data, it can sometimes create hurdles for users. Patients may struggle with complex passwords or managing MFA codes, especially if they’re not tech-savvy. Clinicians, on the other hand, might find their workflows disrupted if authentication slows down access during critical moments. And for administrators, there’s the added burden of handling account recovery requests and MFA-related issues.
To address these challenges, telehealth providers can focus on user-friendly design. For example, offering clear, easy-to-follow instructions for login and MFA setup can make the process less intimidating. Features like “remember this device” (combined with reasonable session timeouts for low-risk activities) and push-based MFA or biometric logins can streamline access. Risk-based or adaptive authentication, which adjusts security requirements based on the context of the login, is another way to balance security with convenience. This approach ensures that routine access remains smooth while ramping up security only when necessary.
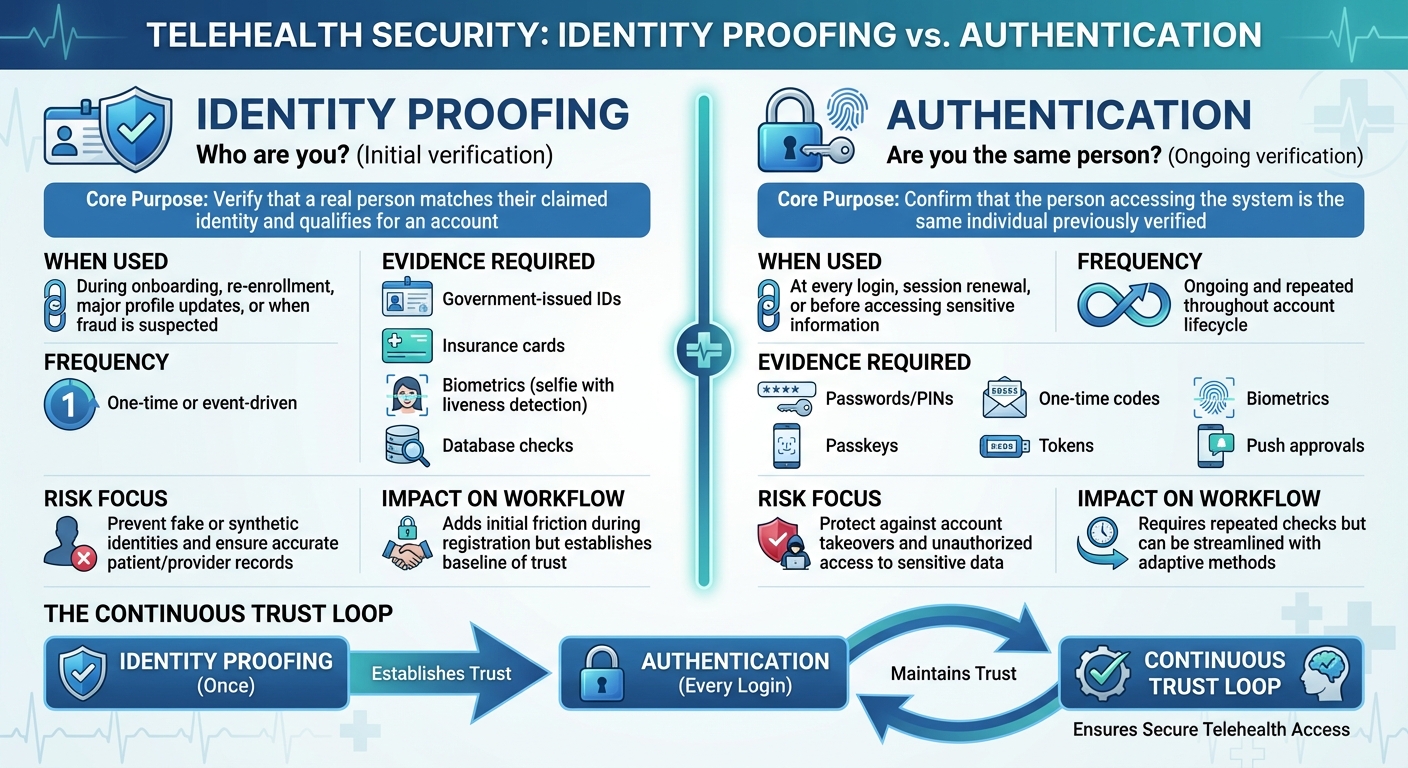
Identity Proofing vs. Authentication: Key Differences
How They Differ in Purpose and Function
When it comes to telehealth security, identity proofing and authentication play very different roles. Identity proofing is all about verifying that a person is who they claim to be - usually during account setup or other high-risk moments. This process ensures a trusted digital identity, preventing issues like fake accounts, synthetic identities, or impersonation from the very start.
On the other hand, authentication steps in after the account has been created. It confirms that the person trying to access the account is indeed the same individual who was verified earlier. While identity proofing works as a gatekeeper during the initial stages, authentication focuses on safeguarding access during future logins or sensitive activities. Together, these processes form a "continuous trust loop", combining rigorous upfront checks with reliable ongoing verification to protect the account over time.
Timing, Frequency, and Evidence Requirements
The timing and frequency of these processes are another key distinction. Identity proofing typically happens once - during patient registration, clinician onboarding, or when significant changes (like updated contact details or fraud alerts) require re-verification. In contrast, authentication is a regular occurrence. It’s required every time someone logs in, accesses test results, prescribes medications, or views sensitive health information.
The evidence needed for each process also differs. Identity proofing demands stronger proof, such as government-issued IDs, insurance details, demographic validation, or biometric data (like a selfie video with liveness detection). Authentication, however, relies on credentials tied to the verified account - these might include passwords, one-time passcodes, hardware tokens, biometrics, or passkeys.
Comparison Table
| Aspect | Identity Proofing | Authentication |
|---|---|---|
| Core Purpose | Verify that a real person matches their claimed identity and qualifies for an account | Confirm that the person accessing the system is the same individual previously verified |
| When Used | During onboarding, re-enrollment, major profile updates, or when fraud is suspected | At every login, session renewal, or before accessing sensitive information |
| Frequency | One-time or event-driven | Ongoing and repeated throughout the account’s lifecycle |
| Evidence Required | Government-issued IDs, insurance cards, biometrics (e.g., selfie with liveness detection), database checks | Passwords, PINs, passkeys, one-time codes, tokens, biometrics, or push approvals |
| Risk Focus | Prevent fake or synthetic identities and ensure accurate patient/provider records | Protect against account takeovers and unauthorized access to sensitive data |
| Impact on Workflow | Adds initial friction during registration but establishes a baseline of trust | Requires repeated checks but can be streamlined with adaptive methods |
These distinctions are critical for designing effective identity assurance strategies in telehealth platforms, ensuring both security and usability.
sbb-itb-535baee
Integrating Identity Assurance in Telehealth Platforms
Risk-Based Identity Workflows
Telehealth platforms need to tailor identity controls based on the level of risk associated with different actions. For instance, accessing general appointment details might only require basic device-based biometrics. However, more sensitive tasks - like e-prescribing Schedule II controlled substances - demand step-up authentication, which involves additional verifications such as re-entering a passkey or confirming identity through a biometric check. This approach aligns with the DEA's Electronic Prescriptions for Controlled Substances (EPCS) rule, which requires two-factor authentication for prescribing controlled substances, as well as HIPAA's mandate for safeguards proportional to the sensitivity of the data.
For example, if a user logs in from a familiar device and location, they may proceed with standard access. But if the system detects unusual activity - like logging in from an unfamiliar device or location - it triggers extra verification steps. This dynamic approach minimizes unnecessary friction during routine care while ramping up security when risk indicators arise. These adaptive identity controls naturally feed into broader governance and lifecycle management strategies.
Governance and Lifecycle Management
Effective identity assurance doesn’t stop at onboarding. Organizations should implement policies that assign assurance levels based on user roles and actions. Automating processes like credential updates, role adjustments, and access revocations ensures smoother operations and regulatory compliance. Additionally, logging all identity events is essential for audits and meeting compliance standards.
Policies should also outline when periodic re-proofing is necessary, such as after significant demographic updates, extended inactivity, or signs of account compromise. High-risk actions, like altering multi-factor authentication settings or accessing sensitive records, should always require step-up authentication.
For clinicians, digital identities must integrate directly with HR and credentialing systems. This ensures that updates to licenses, changes in privileges, or terminations automatically adjust access permissions. For patients, updates to contact or insurance information should trigger additional authentication steps, while major changes - like updating a legal name or Social Security number - should prompt targeted re-proofing measures.
How Censinet RiskOps™ Supports Telehealth Security
Censinet RiskOps™ builds on these identity assurance principles, offering tools specifically designed for healthcare cybersecurity and risk management. The platform helps organizations assess and manage identity-related risks across telehealth platforms, EHRs, patient engagement apps, and identity vendors. It simplifies third-party risk assessments, enabling security teams to evaluate identity proofing and authentication measures before onboarding vendors. Additionally, its risk registers, control catalogs, and industry-standard benchmarks let organizations compare their identity assurance practices with peers, identify gaps - like insufficient MFA coverage or weak account recovery protocols - and prioritize improvements.
"Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required." - Terry Grogan, CISO, Tower Health
Conclusion
A layered identity strategy plays a key role in securing telehealth systems. By combining identity proofing with authentication, healthcare providers create a continuous trust loop that protects telehealth interactions from the initial onboarding process through every patient encounter. Identity proofing confirms real-world identities during registration using tools like government IDs, biometrics, and database checks to prevent fraud. Authentication, on the other hand, ensures only verified users can access sensitive information, relying on methods like multi-factor authentication, biometrics, or passkeys to block unauthorized access to protected health information (PHI).
These two processes work hand in hand to meet specific regulatory standards. For instance, HIPAA requires technical safeguards to uniquely identify and authenticate users accessing electronic PHI. Similarly, NIST guidelines separate identity proofing from authentication and outline assurance levels for both. Strong proofing helps meet "know-your-patient" requirements and deters fraud, while robust authentication ensures compliance with HIPAA’s Security Rule by restricting PHI access to authorized individuals.
The benefits for healthcare organizations are substantial. Accurate identity verification reduces fraud, enhances patient safety, and simplifies operations through automated proofing and modern authentication methods. A risk-based approach - implementing stricter controls for sensitive actions like prescribing controlled substances while keeping routine logins simple - strikes a balance between security and user convenience for both patients and clinicians.
However, telehealth security extends well beyond proofing and authentication. It encompasses an ecosystem that includes electronic health records (EHRs), video platforms, and remote monitoring devices. Weak identity measures in any part of this system can introduce significant risks. To address these challenges, tools like Censinet RiskOps™ help organizations manage identity-related risks by streamlining assessments, benchmarking, and improving control management.
As telehealth continues to grow and regulations shift, healthcare leaders must treat identity assurance as a strategic priority. By building adaptable systems that incorporate continuous verification, behavioral insights, and passwordless authentication - aligned with HIPAA and NIST standards - they can safeguard patient data while supporting secure and compliant care delivery.
FAQs
What is the difference between identity proofing and authentication in telehealth?
In telehealth, identity proofing involves verifying a patient's identity during their initial access to the platform. This step ensures the individual is exactly who they claim to be, creating a secure foundation for future interactions.
Authentication takes place every time the patient logs in or uses the system. It verifies their identity through methods like passwords, biometrics, or multifactor authentication, helping maintain security during each session.
These two processes work together to safeguard patient data and ensure secure access to telehealth services, which is especially critical in the highly regulated healthcare industry.
Why is multi-factor authentication important for securing telehealth systems?
Multi-factor authentication (MFA) plays a key role in safeguarding telehealth systems by adding an extra layer of security. It requires users to confirm their identity using multiple methods - like a password paired with a unique code sent to their device. This added step makes it much harder for unauthorized individuals to gain access, significantly lowering the chances of breaches involving sensitive patient data or clinical systems.
In telehealth, where protecting personal health information (PHI) is absolutely critical, MFA ensures that only the right people can access confidential records. By combining different elements - something you know (like a password), something you have (like a smartphone), or something you are (like a fingerprint) - MFA creates a strong barrier against cyber threats.
How does biometric verification improve identity proofing in telehealth?
Biometric verification adds a layer of security to telehealth by using unique physical or behavioral traits - like fingerprints, facial recognition, or voice patterns - to confirm a patient’s identity. This approach offers more precision and security than traditional methods, reducing the risk of fraud and protecting sensitive patient data.
With biometrics, healthcare providers can simplify patient access while staying aligned with privacy laws and safeguarding vital information.


